Initiating the Active Directory Odyssey: Unveiling Key Concepts and Building the Foundations
5 min read
January 6, 2023

Table of contents
Introduction to the series
Embark on a journey through the first post of this blog, where we unravel the intricacies of Active Directory. This topic, a personal favorite and a recurrent element in offensive security projects, takes center stage in our exploration. A year ago, I initiated the Igris project—a Python tool crafted to test Active Directory security. Currently paused for re-engineering in the nim programming language, it serves as a potential foundation for those keen on creating offensive security tools. The development of Igris not only provided valuable insights into these environments but also fueled my desire to fortify and expand my knowledge.
In this series, I will share a collection of articles covering various Active Directory topics as I encounter and learn them. For programming enthusiasts, I'll delve into the application of key Python libraries, demonstrating their utility in crafting practical tools for diverse scenarios. The exploration extends to both the Cmd console and the PowerShell console, showcasing methods to collect information on the discussed concepts.
I trust you will find this series both informative and enjoyable. Thanks for embarking on this learning journey with me! 😊
Things to Keep in Mind: Guiding Your Learning Path
This series caters to individuals venturing into offensive security, with a specific focus on Active Directory. Our expedition will gradually venture into more technical terrain, starting with the fundamentals. Acknowledging my non-expert status, I believe this series can be particularly beneficial for those new to Active Directory, as the mistakes I encounter may resonate with others in the future.
For effective practice, consider setting up an Active Directory lab. I recommend The Cyber Mentor's video for lab creation. If you opt for a Proxmox server setup, refer to my blogs on this topic:

How to set up an active directory environment to practice in vmware
Regarding Python, we won't cover basic language concepts. Instead, the focus will be on aspects of key libraries used. If you lack basic Python knowledge, numerous online tutorials are available. With these considerations in mind, let's dive into the series!
What is Active Directory?: Simplifying Centralized Management
In essence, Active Directory is a system designed to centrally manage an organization's computers and users. To illustrate its advantages, consider the scenario of a new employee joining an organization and needing access to various computers. Without Active Directory, creating a user account on each computer becomes a laborious task. However, by connecting these computers to an Active Directory network, only one user account for the new employee needs creation in the centralized database. This streamlined process ensures access to all network-connected computers without individual account creation on each.
After this succinct overview, let's introduce key concepts essential for understanding Active Directory environments.
Key Concepts in Active Directory
Domains
In the realm of Active Directory, a domain is akin to the previously mentioned "Active Directory network." It constitutes a collection of computers sharing the same centralized database, housed in a "Domain Controller." Future posts will delve deeper into the intricacies of Domain Controllers. An essential concept is the domain name or DNS name, often identical to the organization's website. For example, a domain name might be kayssel.com, while an internal network domain could be shadow.local.
To determine the domain name to which a computer belongs, execute the following commands in the PowerShell console:
PS C:\Users\beruinsect> $env:USERDNSDOMAIN
SHADOW.LOCAL
PS C:\Users\beruinsect> (Get-ADDomain).DNSRoot
shadow.local
Computers
In Active Directory environments, a computer doubles as a user and must be connected to a Domain Controller to belong to it. Three types of computers exist:
- Domain Controllers (DCs): Central servers managing the domain, housing the centralized database. These servers run on Windows Server Machines.
- Workstations: Personal computers used daily, typically running on Windows 10 or Windows 11.
- Servers: Computers offering services like webs, files, or databases, usually running on Linux or Windows Server machines.
Users
One of the main advantages of Active Directory is user management. As explained earlier, creating and configuring a user in the centralized database ensures changes affect all domain computers. All user data, residing in the centralized database, can be accessed from any domain point with the necessary permissions. Active Directory hosts two main user types: local users, with access limited to the machines on which they are created, and domain users, by default having access to all domain computers.
WORKGROUP/iron #Local User
shadow.local/iron #Domain User
Lab Scheme: Navigating the Active Directory Learning Landscape
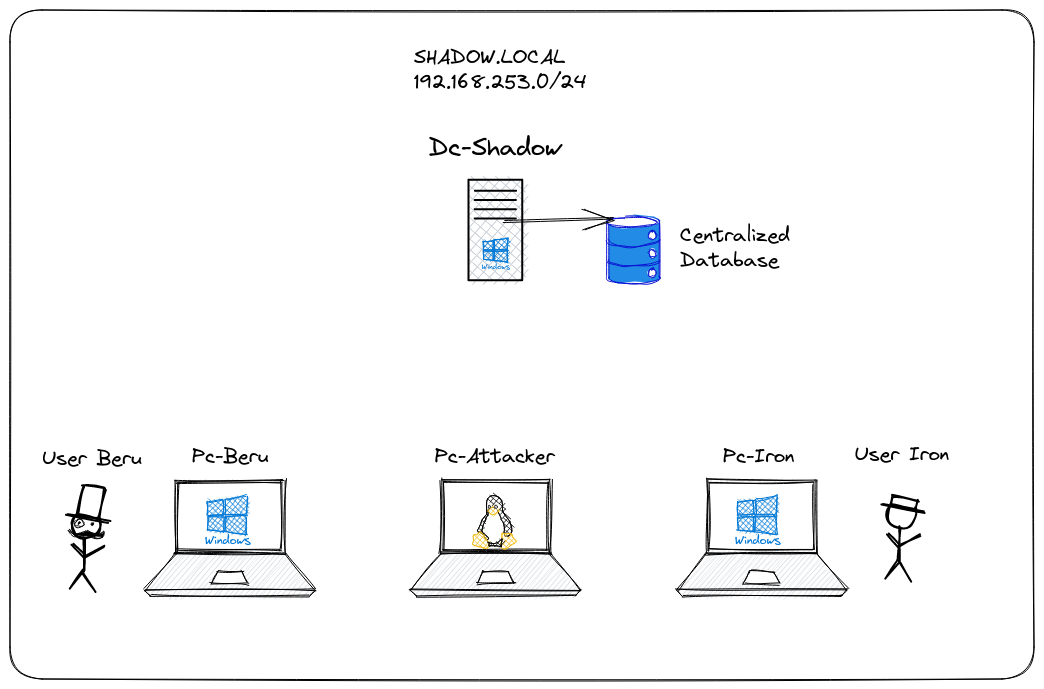
Concluding this inaugural chapter, let's introduce the main components of the lab instrumental in learning about Active Directory. The lab domain, named shadow.local, utilizes the IP range 192.168.253.0/24. Within the domain are two workstations, one for user Beru and one for user Iron—both operating on Windows 10 and connected to the Dc-Shadow Domain Controller, which runs Windows Server 2019. These components set the stage for further exploration in upcoming posts.
References
The main references that I have found to learn how to attack Active Directory environments are the following and will be the ones I will use as a guide to learn more about these environments :)


Feel free to explore and share your thoughts on specific sections you'd like to delve into further!
Chapters
Next chapter