Comprehensive Android Security Testing: Patching, Objection, and API Backend
7 min read
May 27, 2024

Introduction
In this second chapter, we will delve into advanced techniques and tools used in the penetration testing of Android applications. This chapter will focus on three key points:
- Patching an Application: Learn how to modify an application’s code to bypass security mechanisms, enabling deeper analysis and vulnerability detection.
- Using Objection: Get introduced to Objection, a powerful runtime mobile exploration tool that leverages Frida’s capabilities for real-time application inspection and modification. We’ll cover how to install and use Objection for various security analysis tasks.
- Configuring the Application Backend: Understand how to set up and configure the application’s backend using Docker Compose to facilitate interaction with the API, ensuring a complete environment for security testing.
By the end of this chapter, you’ll have a comprehensive understanding of these essential tools and methods, enhancing your ability to conduct thorough and effective security assessments of Android applications.
Patching an application
Patching in pentesting refers to modifying the application’s code to circumvent security measures that prevent in-depth analysis. This can involve disabling root detection, SSL pinning, or anti-debugging mechanisms. The goal is to allow the penetration tester to fully analyze the app’s behavior and identify vulnerabilities without being hindered by these protections.
To patch an application, we first need to follow the process outlined in the previous chapter to decompile the application and study the code.
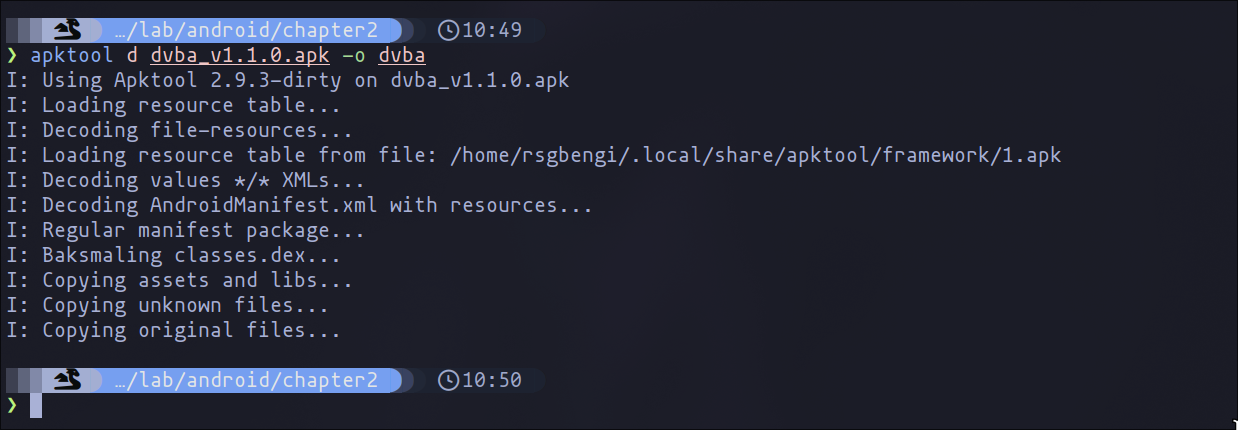
App Decompilation
The key difference now is that instead of decompiling to Java, we will use Smali, as it allows for easier recompilation of the application with the necessary changes. With the information we already have, we can locate the code that stops the execution of the program, in this case related to Frida detection.
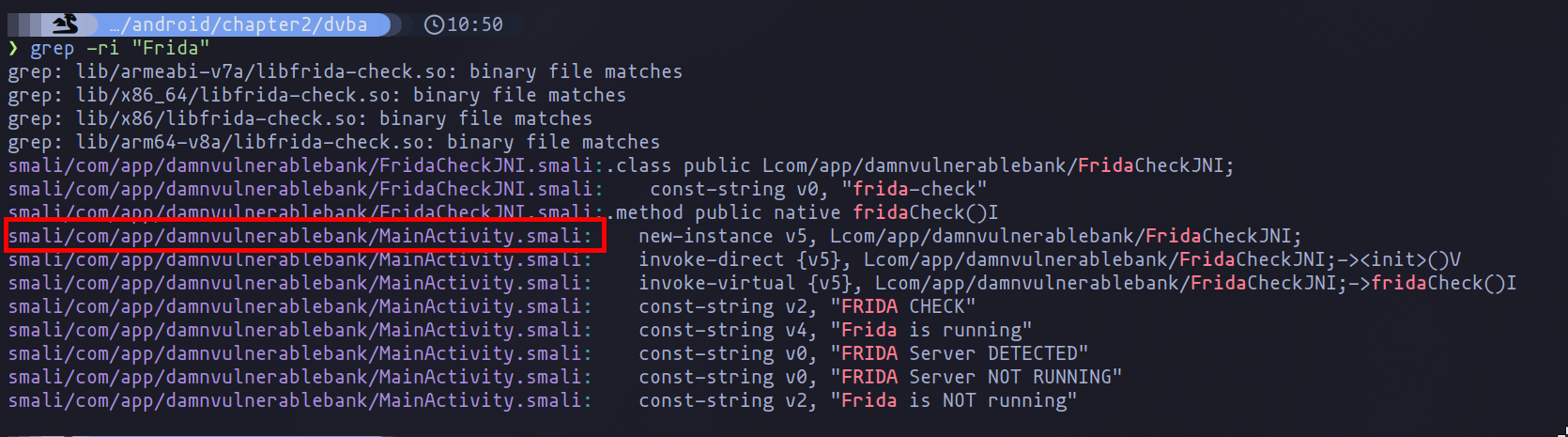
Detection of protection measures
As shown in the image above, the changes need to be made in the MainActivity.smali file, where the detection occurs. By examining the code, we find the finish function, which is responsible for closing the app when certain conditions are met. To solve the problem and prevent the program from breaking after detecting Frida/emulation, we simply need to comment out or eliminate these parts of the code.
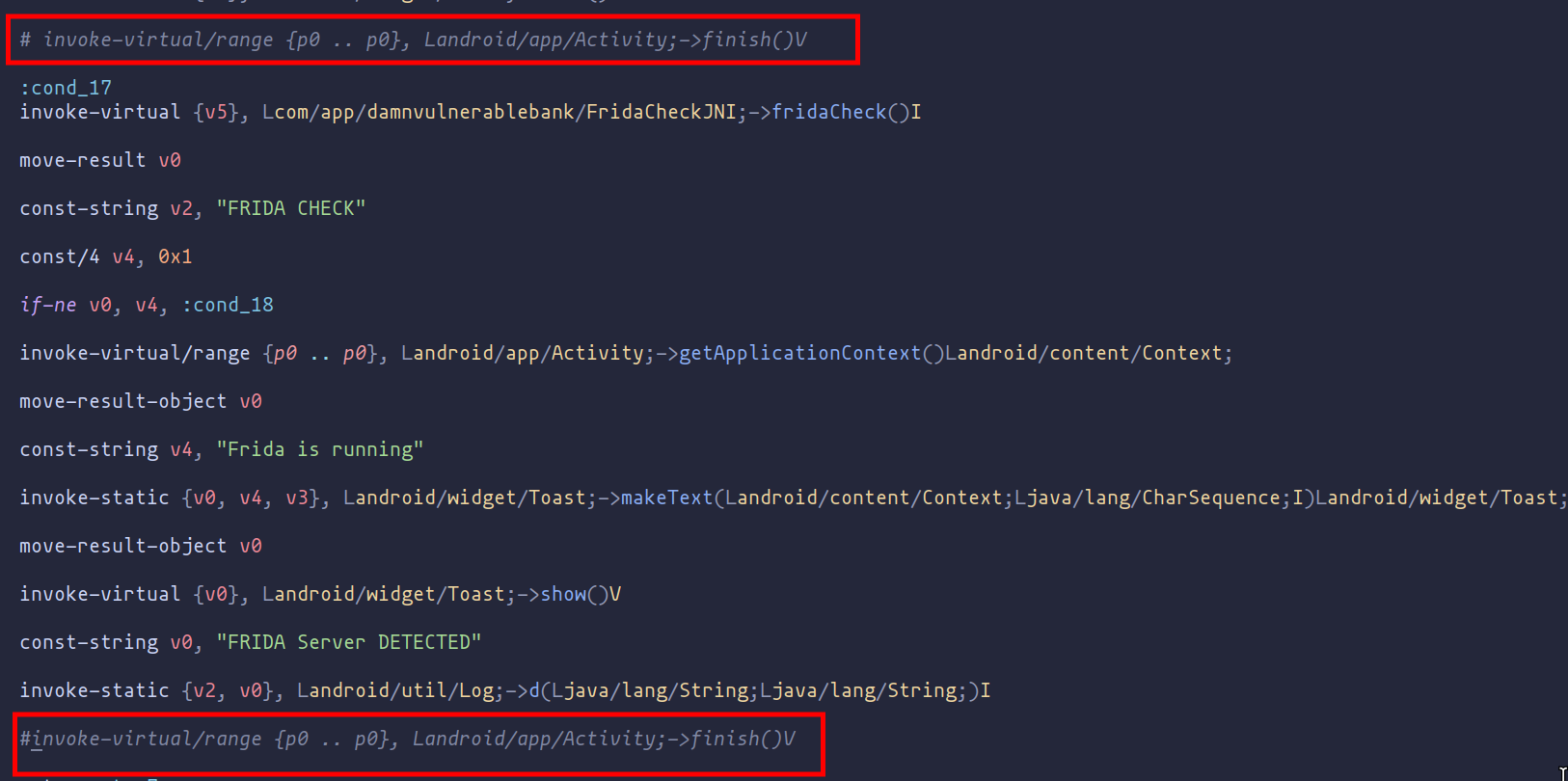
Comment code that terminates the application
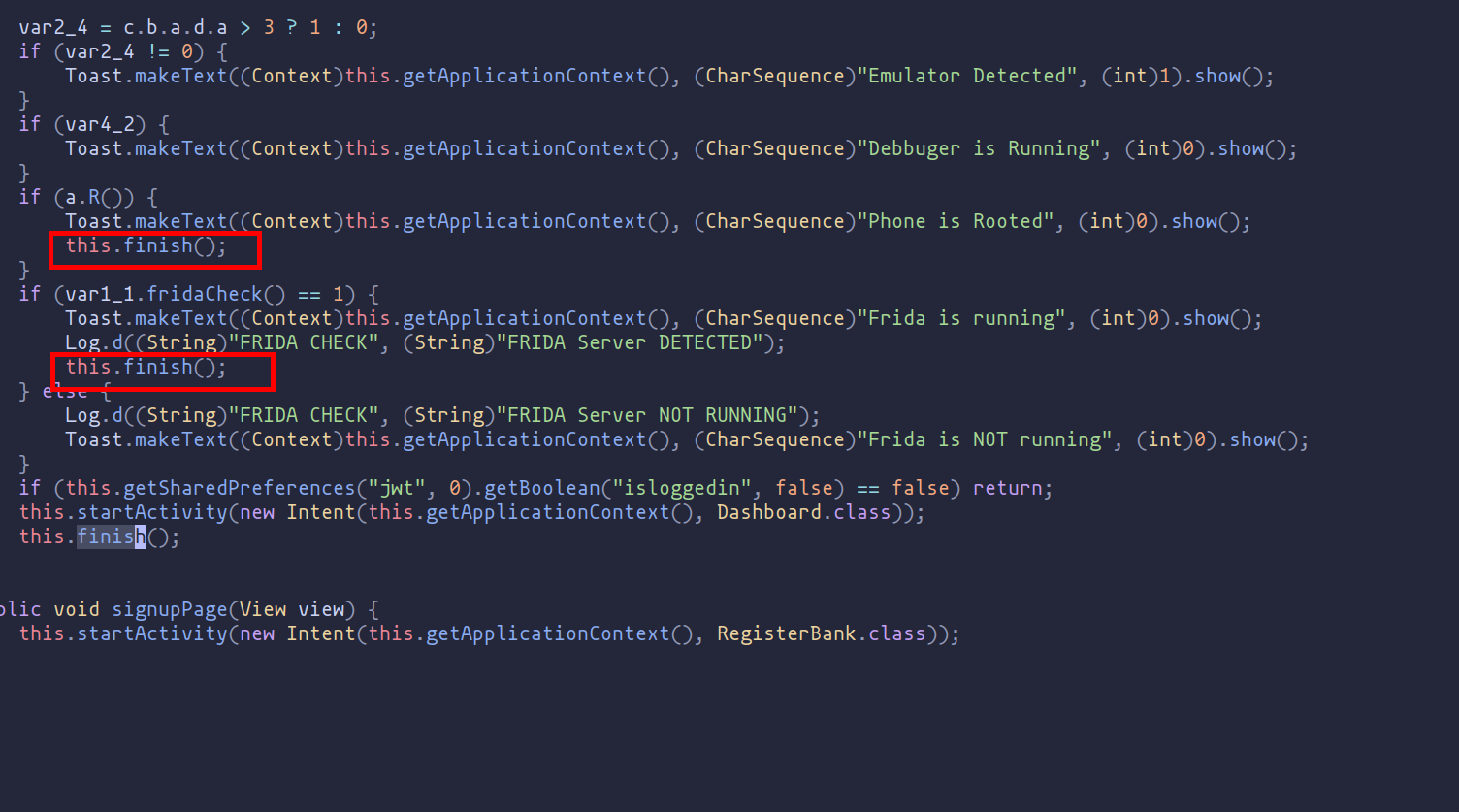
Correspondence with the code in Java
Once the changes have been made, we simply recompile the application and sign it as we did in the previous chapter.
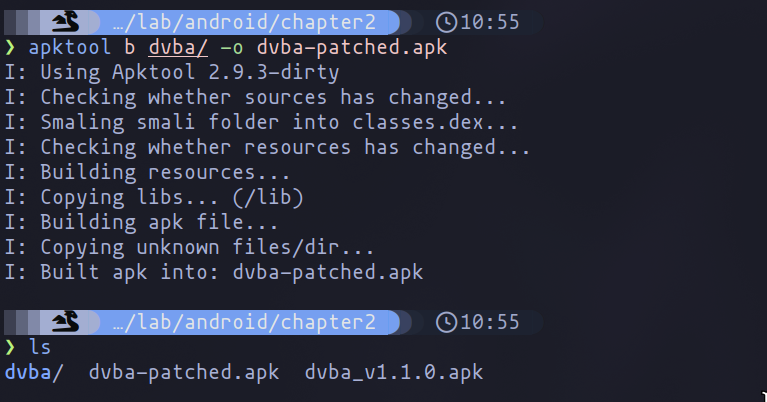
Compilation of the application
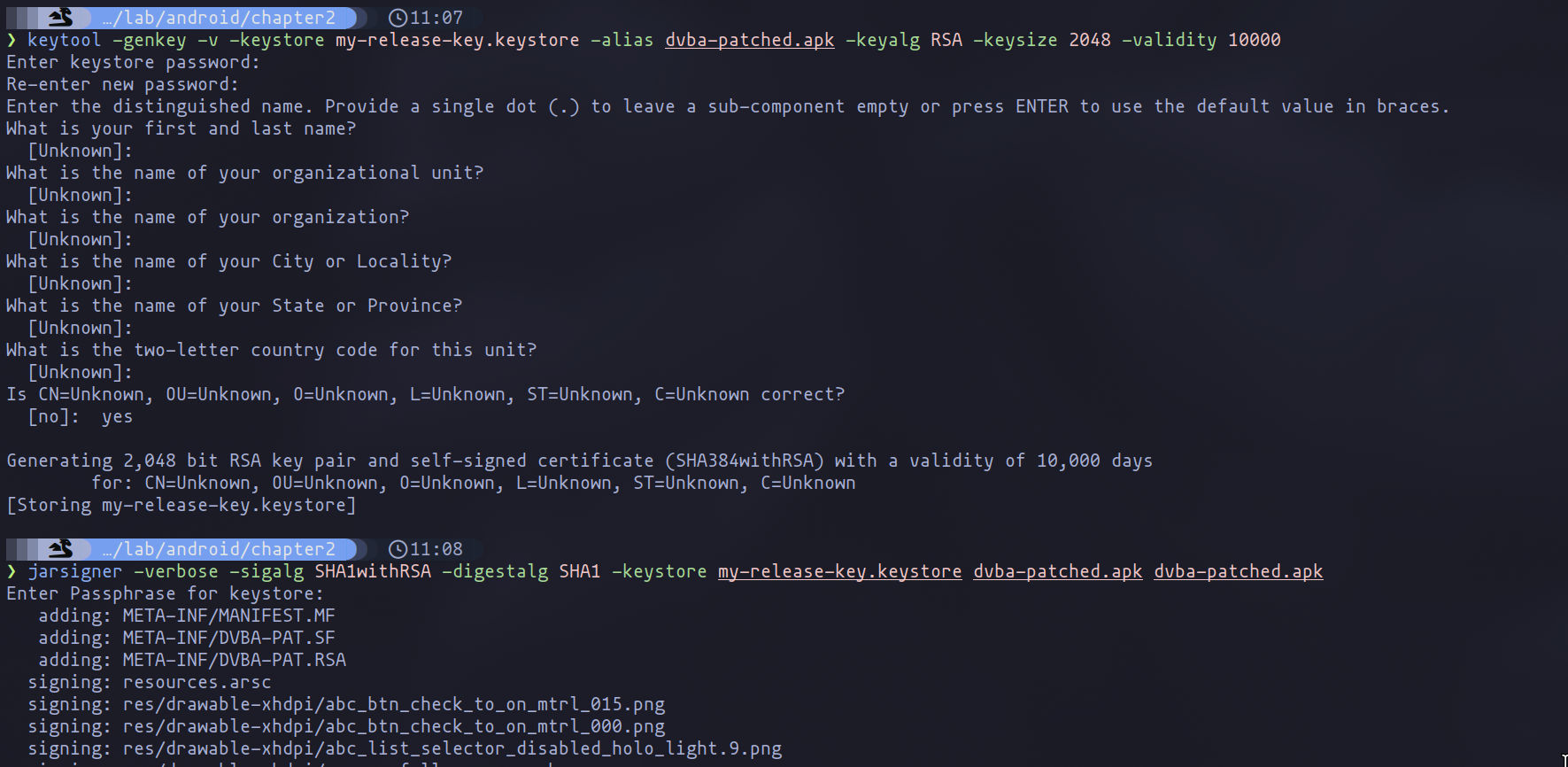
Application signature process
After this, we only need to install the patched application. Thanks to the patching, we will not need to launch it with Frida every time to interact with it.
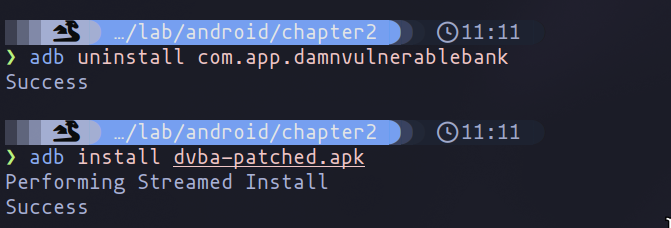
Application Installation
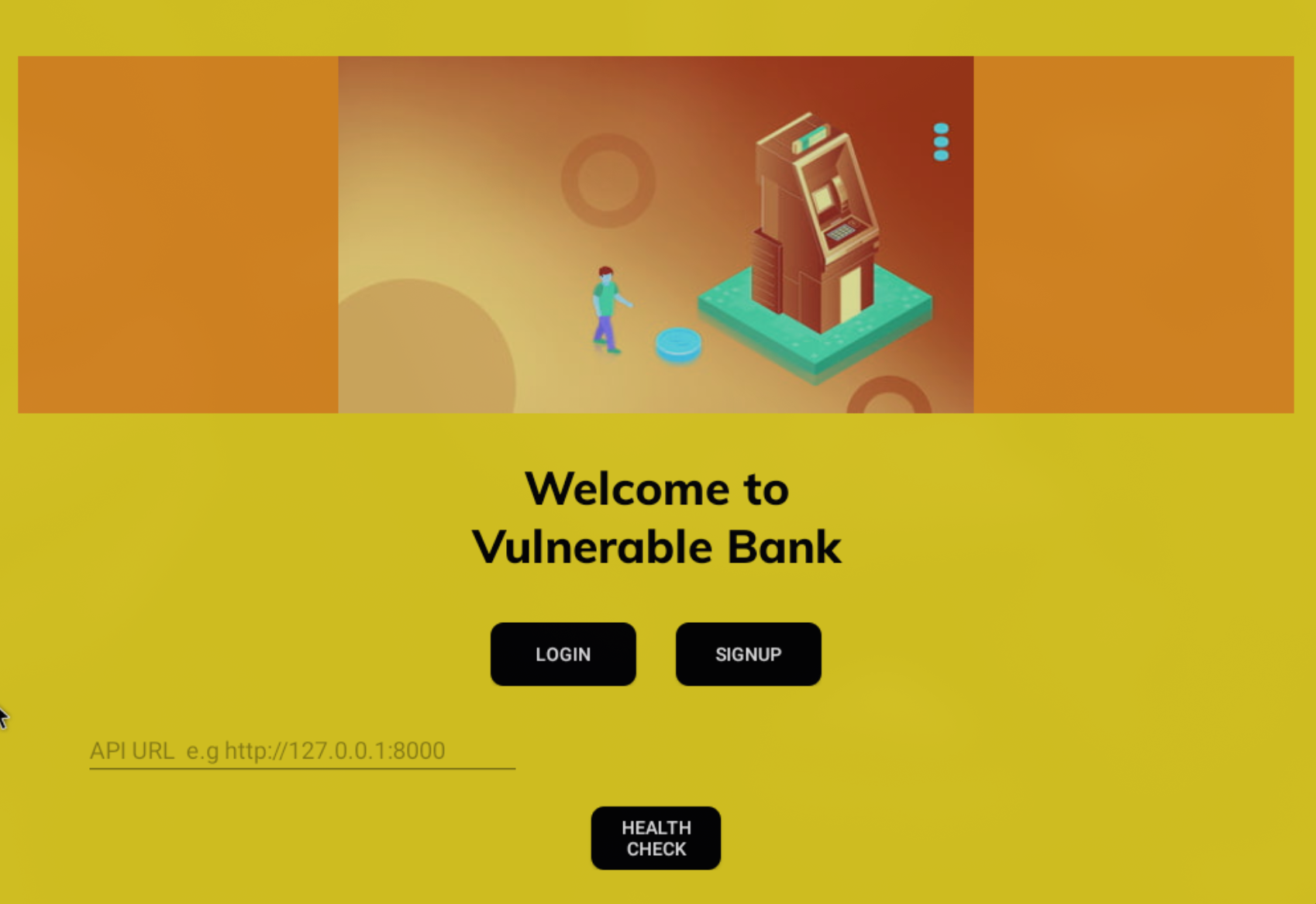
Access to the application
Objection
Objection is described as a “runtime mobile exploration” tool. Simply put, this means it allows users to interact with and modify applications while they are running. Leveraging the capabilities of Frida, Objection enables real-time inspection and modification of application behavior. It is often used instead of plain Frida because it provides a higher-level, user-friendly interface and pre-built functionalities that simplify common tasks, making it more accessible for security professionals who may not be as familiar with scripting or programming.
Objection offers a variety of functionalities crucial for mobile application security analysis:
- Object and Method Manipulation: Allows modification of objects and methods within the application, facilitating the detection of vulnerabilities and undesired behaviors. Today, we will focus on this functionality, but in the future, we will also use it for points 2 and 3.
- Application Structure Exploration: Provides tools to navigate and examine the internal structure of the application, including views, activities, and services.
- Security Bypass: Helps bypass security measures such as root detection, certificate pinning, and other protections that might hinder deeper analysis. We will cover this functionality in upcoming chapters.
Installation Process and Usage
To install the tool, using pip alone will suffice:
pip install objection
Additionally, we need to initialize the Frida server on the Android device and specify port “27042”; otherwise, the tool will not work:
data/local/tmp/frida-server-16.2.1-android-x86_64 -l 0.0.0.0:27042
Once this is done, we will need to locate the name of the application to launch it. This can be done using the following command:
frida-ps -U
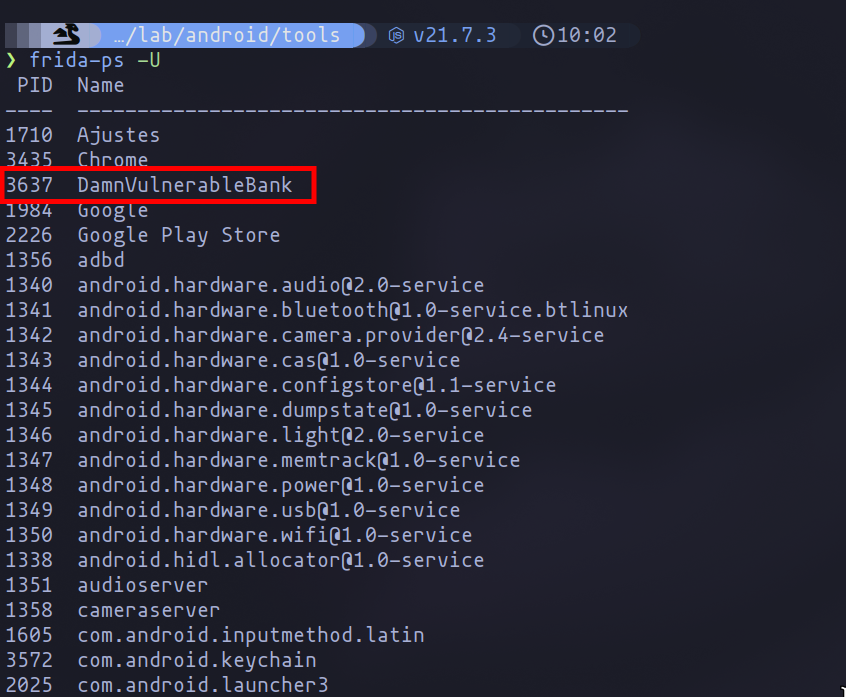
Process Dump
After identifying the application, we can launch Objection, and the application will also be launched on the device:
objection -N -h 192.168.20.143 --gadget "DamnVulnerableBank" explore
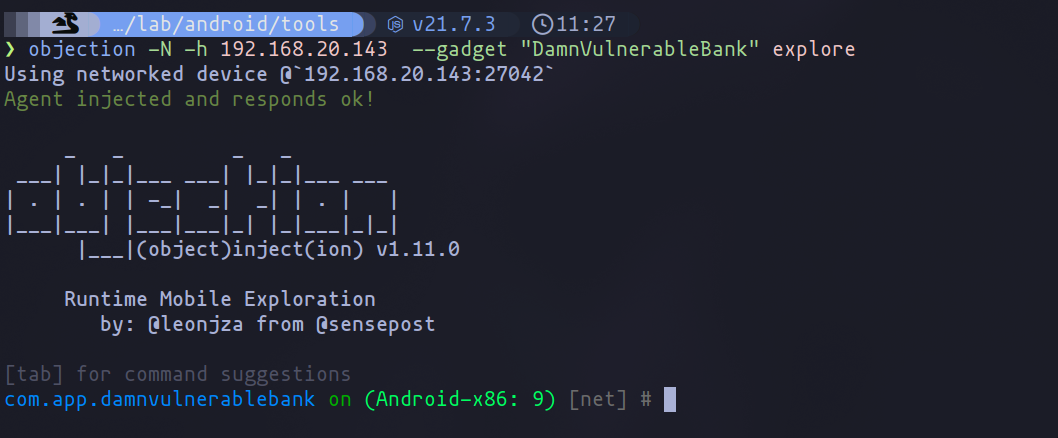
Objection startup
To detect protection measures, Objection allows you to display the different classes of the application. In this case, as shown in the following image, there are not many classes, making it easy to identify potential issues. However, in real-world scenarios, there may be many more classes, making it more challenging to find what you are looking for:
android hooking search classes com.app.damnvulnerablebank
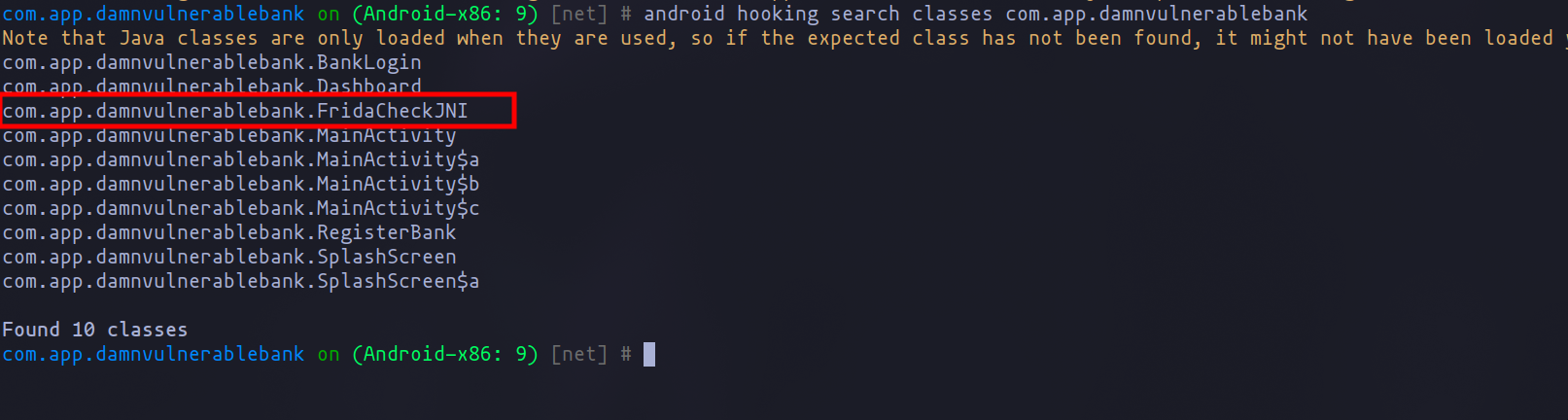
Detection of the FridaCheckIn class
Once we have identified an interesting class, we can filter by its methods:
android hooking list class_methods com.app.damnvulnerablebank.FridaCheckJNI
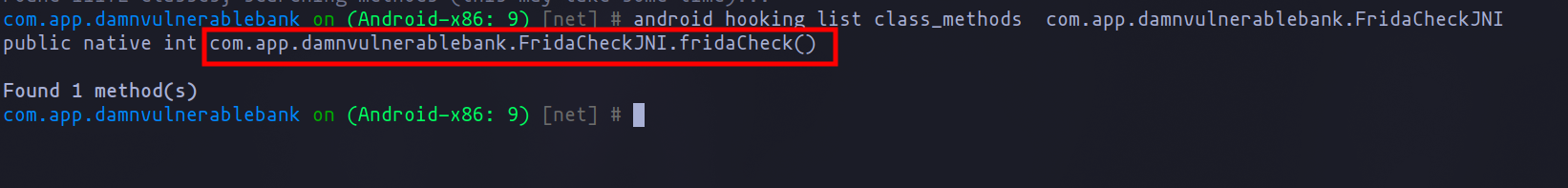
Search class methods
After identifying the class, we can use an agent to monitor the method and display its return value when it fails:
android hooking watch class_method com.app.damnvulnerablebank.FridaCheckJNI.fridaCheck --dump-return
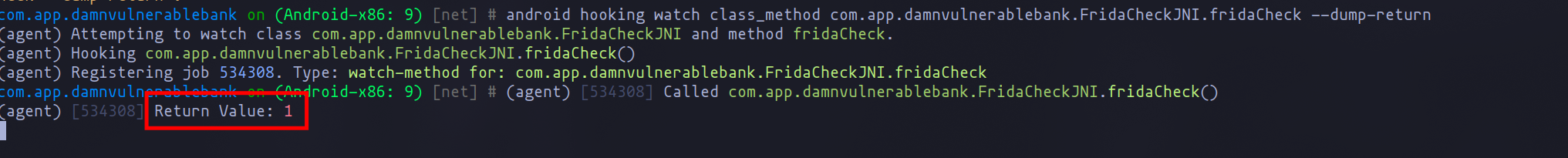
Monotoring to see what is returned by the method
Objection also allows us to load scripts from Frida and use them as needed. In the following image, you can see how I have loaded the script developed in the previous chapter to evade Frida detection:
Java.perform(function () {
console.log("looking for FridaCheckJNI.fridaCheck()");
try {
const FridaCheckJNI = Java.use('com.app.damnvulnerablebank.FridaCheckJNI');
FridaCheckJNI.fridaCheck.implementation = function() {
console.log("hooking fridaCheck().");
var value = this.fridaCheck.call(this);
console.log("fridaCheck() returned " + value);
console.log("switching fridaCheck() to 0");
return 0; // Always return 0 to bypass checks
};
} catch (e) {
console.log("Failed to hook fridaCheck: " + e.message);
}
});
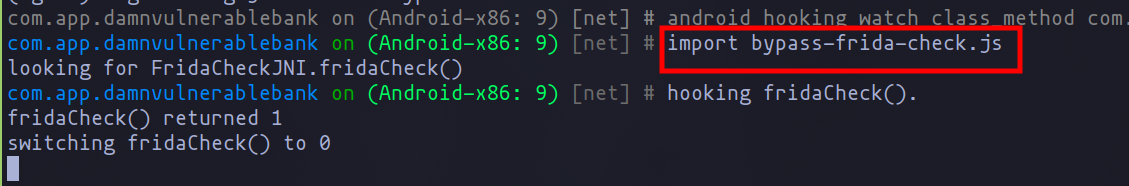
Script import
Application backend
The last part I wanted to discuss in this chapter is the configuration of the backend of the application to interact with the API. This is straightforward since you can build everything directly with Docker Compose. The only detail to keep in mind is the port configuration, to ensure it is not already in use (I had it occupied by Juice Shop).
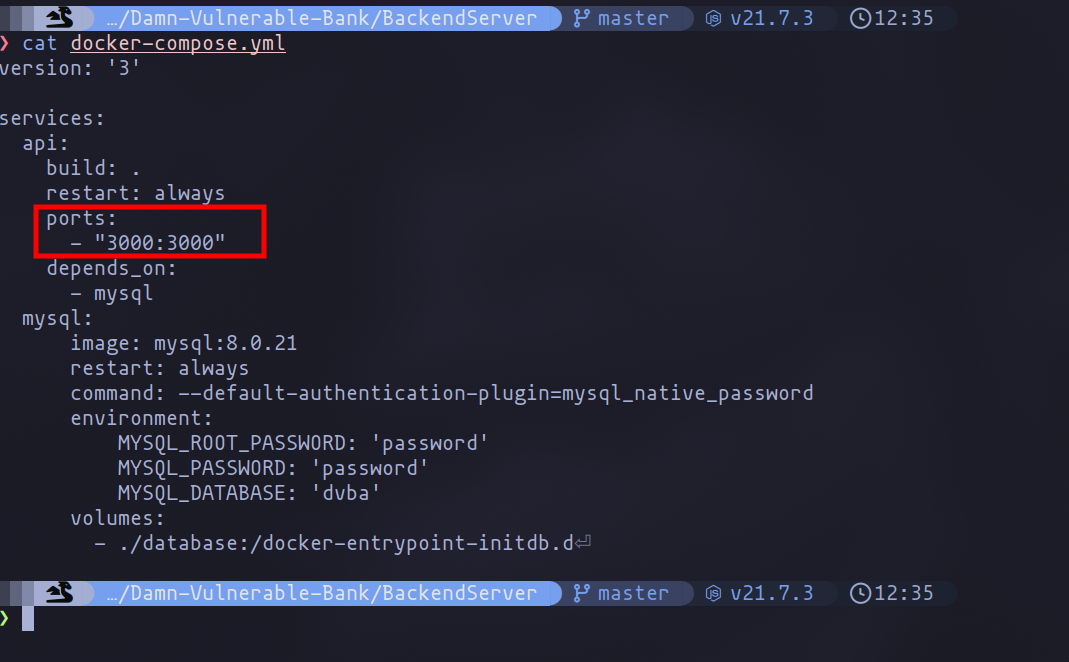
Docker compose file
Once you have verified and possibly adjusted the port configuration, you can deploy everything using the following command:
docker-compose up --build
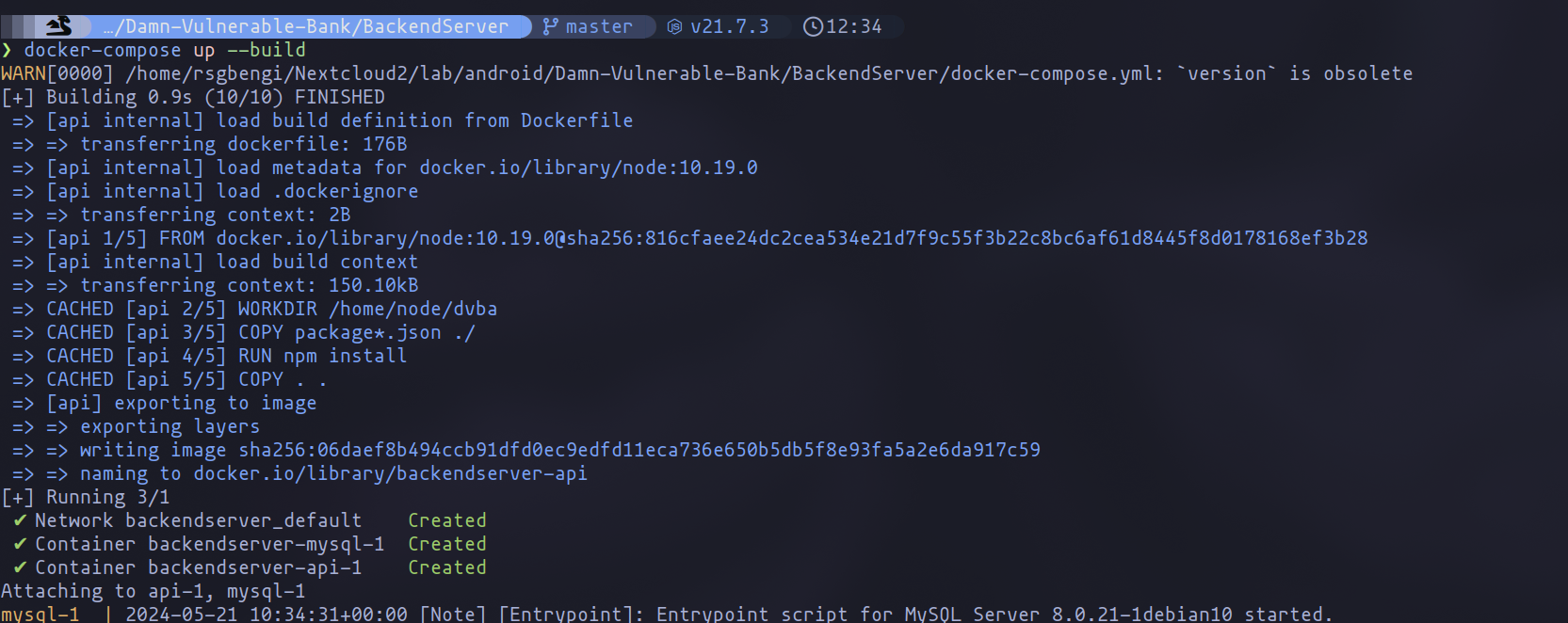
Docker build process
After setting up the application, navigate to the front-end and enter the API URL to check if everything is working correctly.
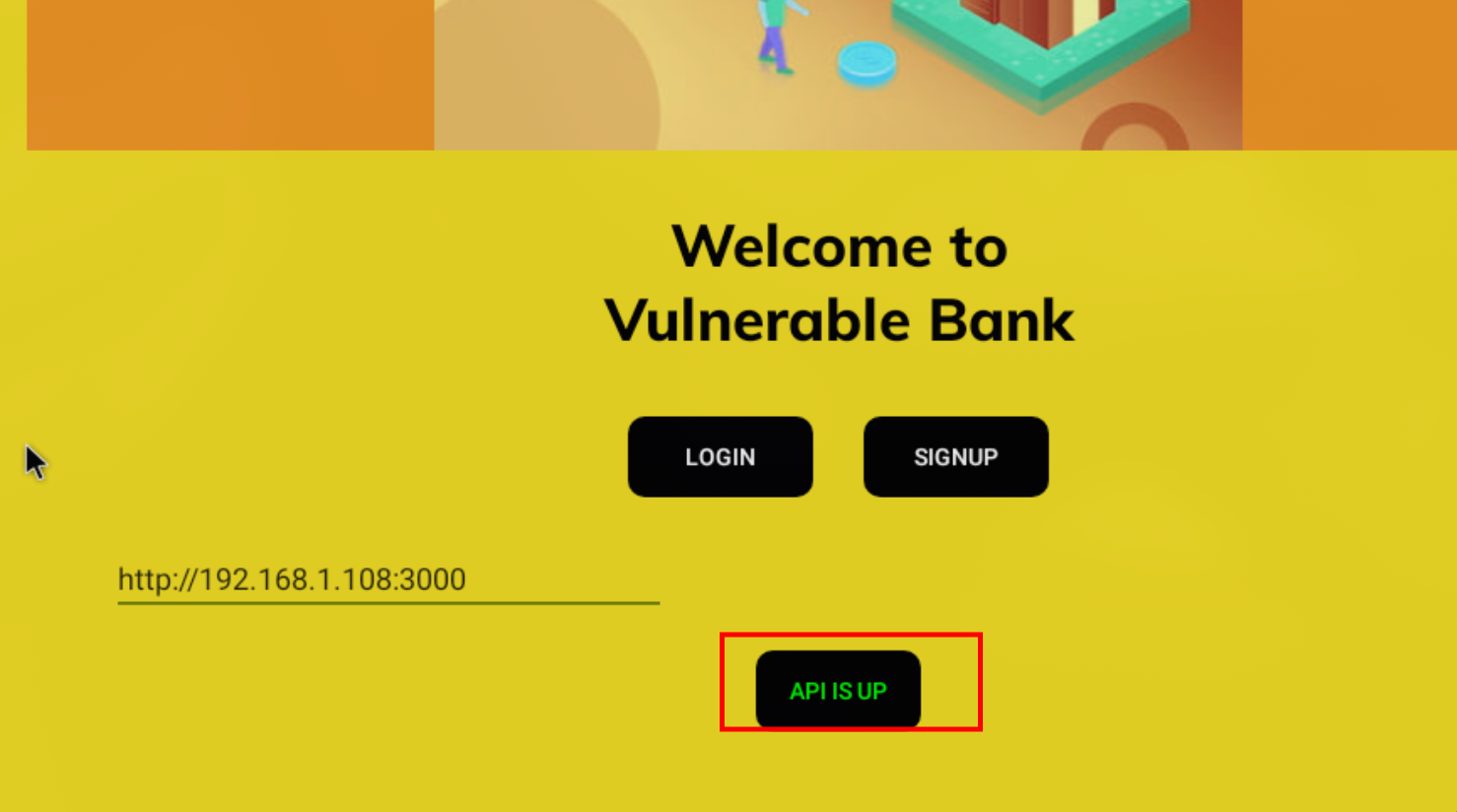
Confirmation that the API is working
Finally, create a user and try to log in to access all the functionalities of the application.
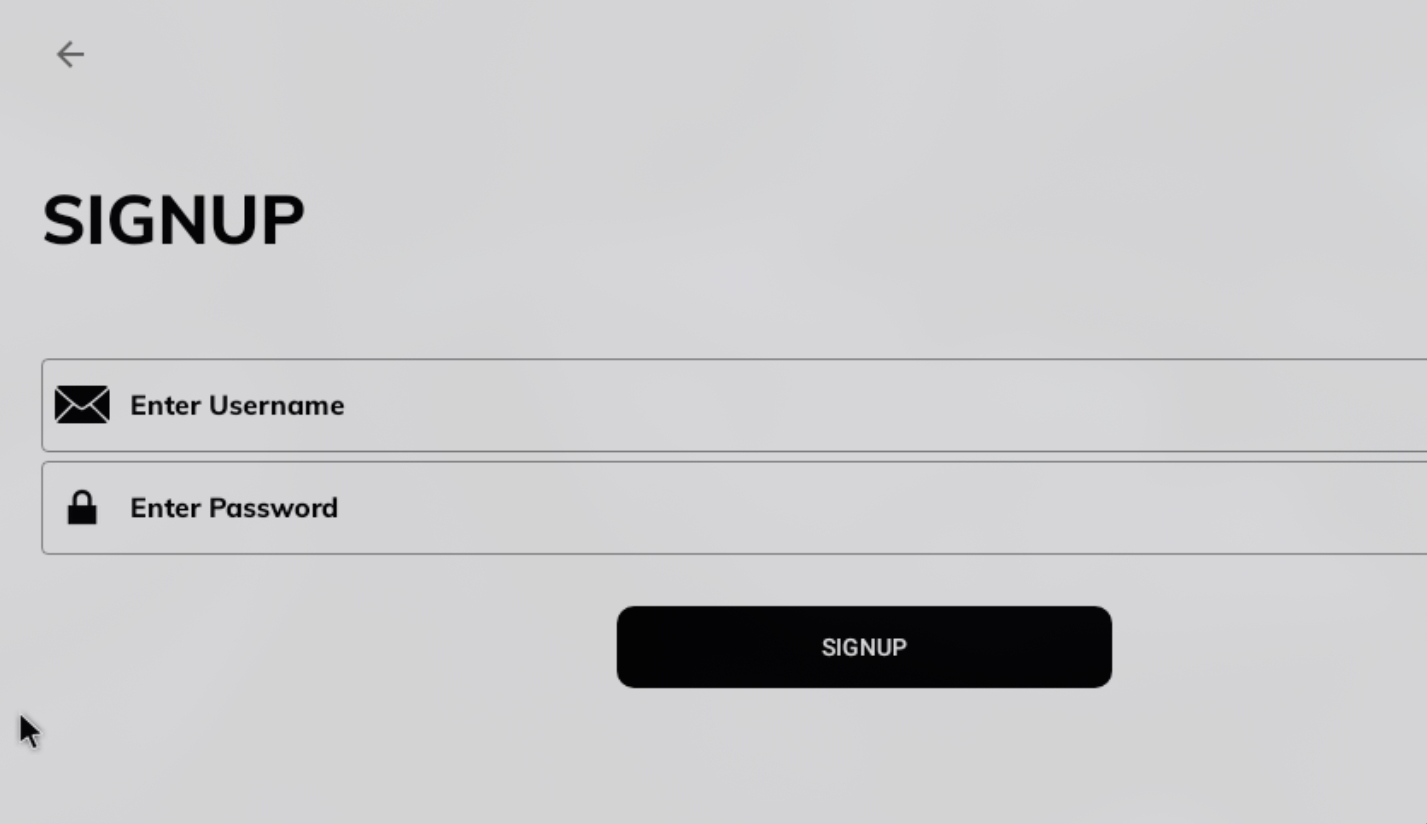
User registration
Application Portal
Conclusions
In this chapter, we have explored crucial techniques and tools for enhancing the penetration testing of Android applications. Here are the key takeaways:
- Patching an Application: We used patching to prevent the application from stopping when Frida is detected or when the device is used in an emulated environment, allowing for more in-depth analysis and vulnerability detection.
- Leveraging Objection: We introduced Objection as a user-friendly tool that simplifies the process of runtime application exploration and manipulation. Through practical examples, we learned how to manipulate objects and investigate methods within the application.
- Backend Configuration with Docker Compose: We covered the setup and configuration of the application’s backend using Docker Compose, enabling seamless interaction with the API. This ensures a complete and functional environment for conducting security assessments.
By mastering these techniques and tools, you are now better equipped to perform comprehensive and effective security testing on Android applications. These skills will enable you to uncover vulnerabilities, understand application behavior, and enhance overall security measures.
References
- Frida. Retrieved from https://frida.re
- Objection. Retrieved from https://github.com/sensepost/objection
- Android Security Testing. Retrieved from https://owasp.org/www-project-mobile-security-testing-guide/latest/Android\_Testing\_Guide
- Docker Compose Documentation. Retrieved from https://docs.docker.com/compose/
- Smali/Baksmali. Retrieved from https://github.com/JesusFreke/smali
- OWASP Mobile Security Project. Retrieved from https://owasp.org/www-project-mobile-security/
- Pentesting Android Apps with Frida. Retrieved from https://www.hackingarticles.in/pentesting-android-apps-using-frida/
- Juiceshop. Retrieved from https://owasp.org/www-project-juice-shop/
- Android Developers Documentation. Retrieved from https://developer.android.com/docs
- Practical Mobile Forensics. (2016). Authors: Heather Mahalik, Rohit Tamma, and Satish Bommisetty. Packt Publishing.
- TrustedSec. Android Hacking for Beginners. Retrieved from https://trustedsec.com/blog/android-hacking-for-beginners
Chapters

Previous chapter
Next chapter


💬 Comments Available
Drop your thoughts in the comments below! Found a bug or have feedback? Let me know.