Unveiling API Hacking: A Methodological Journey Through Recognition and Exploration
10 min read
January 7, 2024

Introduction
Welcome to a captivating journey into the realm of API hacking, where every line of code tells a story, and every vulnerability opens a door to vast unexplored territories. In this article, we’ll plunge into the intriguing world of crAPI, an application that challenges our auditing skills in a unique way. But before we dive deep into the intricacies of this fascinating universe, let’s ensure we have the right tools and our playground is set. Let’s configure our lab and get ready for the exhilarating art of hacking APIs!
Crafting the Ultimate Playground: Setting Up Your API Hacking Lab
Let’s delve into the intriguing realm of API hacking by setting up the ultimate playground: the crAPI application. The installation process is a breeze; just ensure you have Docker or Docker-compose on your machine and follow the official crAPI documentation at OWASP/crAPI.
crAPI/docs/setup.md at develop · OWASP/crAPI
If you’re sticking with the local setup, no worries; no adjustments are needed in the docker-compose.yml file. However, if you opt for a virtual machine setup (perhaps using Proxmox), a few tweaks are necessary. Navigate to the “ports” section and replace “127.0.0.1” with “0.0.0.0” to allow requests from all network interfaces. Check out the screenshots below for a sneak peek.
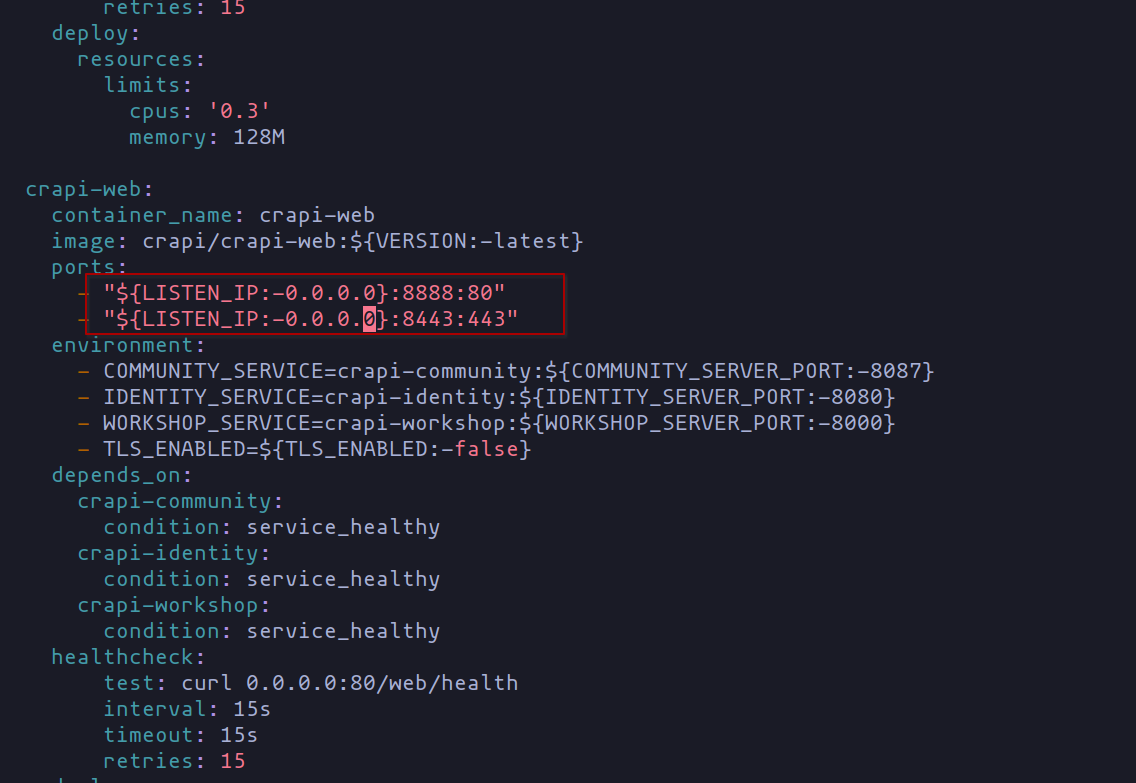
Configuration of docker-compose.yml
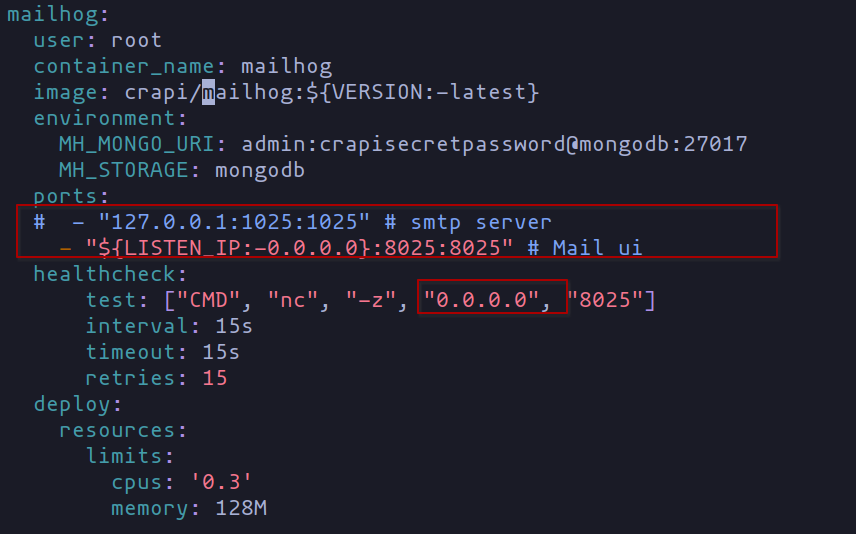
Change mailhog
With everything set up and the documentation at your fingertips, it’s showtime. Deploy the environment with a magical command:
docker-compose -f docker-compose.yml --compatibility up -d
**-f**: Picture this as the script for our Docker orchestra. We specify the composition file (docker-compose.yml), outlining how our containers should interact and play together.--compatibility: Think of this as the compatibility mode, ensuring smooth interactions between different versions of Docker. It’s like having a universal translator for our containerized symphony.up: This is the maestro’s command, telling Docker to bring our composition to life! It orchestrates the deployment of our containers, creating a harmonious ensemble of interconnected services.-d: Ah, the director’s cut! This flag stands for detached mode, meaning our containers will perform their virtuoso acts in the background, allowing us to enjoy the show without being bombarded by logs.
In essence, with this command, we’re telling Docker to follow our musical score (docker-compose.yml), ensuring compatibility among the performers, and then orchestrating a grand performance in the background. Bravo!
And just like that, you’re all set to explore the realm of API hacking!
How to Hack like a Pro: Navigating the Auditing Maze with OWASP and More
Let’s immerse ourselves in the world of auditing, but before we dive too deep, remember this crucial point—it’s not a random game. We need some details upfront, and that’s where the client comes in. They provide the scope (think target URL) and guide us on where to focus our hacking efforts (data filtering, injections, and the whole shebang).
Take our case, for instance. We’re dealing with the crAPI application (yes, chuckle at the name if you must). We have the URL, and our mission is to conquer the world of API hacking.
To navigate this labyrinth, we need a sherpa, and that’s where OWASP comes in. Picture them as the cool kids in cybersecurity, providing insights on testing and fortifying app security. Since our app dances with an API, we’re eyeing the top 10 vulnerabilities OWASP has identified in these bad boys.
OWASP API Security Project | OWASP Foundation
Here’s the golden nugget of wisdom: before you unleash your testing ninja skills on any app, bow down to OWASP. Memorize it, tattoo it on your arm—whatever suits your style.
But wait, there’s more! OWASP is like a treasure trove of hacking methodologies, tailored for every occasion you might encounter in your pentester life. Got a mobile app on your hands? They got you covered.
OWASP MASTG - OWASP Mobile Application Security
And if OWASP leaves you craving more, or you need a quick fix, there’s always Hacktricks, the Swiss Army knife of hacking wisdom. It’s got a bit of everything to tickle your fancy.
Now, these methodologies can feel like a buffet where you want to try everything, but hold your horses. Incorporate them into your toolkit bit by bit, like adding spices to your secret sauce. My goal here is to hand you a simple yet solid API hacking starter pack. We’re talking basics—what to peek at when an app’s got APIs. Once you’re comfy with the basics and sidestep the usual traps, you can level up your game.
Remember, when you’re starting out, you don’t have to be the Einstein of hacking. It’s a slow dance, a gradual journey. So, if an audit feels like you’re juggling too much, relax. This realm is vast, and you’re in it for the long haul. Learn, adapt, and don’t let the overwhelm sneak in. You got this! 🚀
Mastering Application Audits: A Survival Guide
Navigating an application audit requires a well-defined methodology to avoid drowning in complexity. I kick off the process by meticulously cataloging the application’s functionalities, ensuring a comprehensive understanding. This systematic approach is universally applicable, whether the application is tailored for Android, iOS, or web platforms.
To document and fortify this exploration, I create a dedicated ‘memory’—a repository of steps and tests for future reference. This strategic documentation proves invaluable, enabling me to recall specific details effortlessly, even months later. Utilizing tools like Obsidian, I capture detailed notes and screenshots, facilitating comprehensive recall.
Armed with a holistic, high-level overview, I adopt a structured testing approach—from addressing the most critical aspects to the less critical ones. This prioritization aligns with the type of application under examination, following the esteemed OWASP guidelines. The meticulous testing strategy ensures a robust evaluation, contributing to the overall effectiveness of the audit process.
Obsidian structure of a section
End-of-day rituals involve cross-referencing progress against a meticulously curated checklist. This step ensures that every crucial facet has been thoroughly examined, leaving no room for oversight. While generic templates are available on platforms like GitHub, I advocate for crafting a personalized checklist tailored to the unique nuances of the assessment at hand. This bespoke approach guarantees a more nuanced evaluation and aligns closely with the specific needs of the project.
It’s crucial to acknowledge that this process is a dynamic and continuous learning journey. The pursuit of excellence involves the ongoing refinement of strategies, emphasizing the importance of gradual improvement over time. Embrace the ethos of perpetual learning, and the iterative evolution of your methodology will undoubtedly yield more robust and effective results.
Exploration Unveiled: Navigating the Digital Maze
Embarking on our journey into application auditing, we plunge into the intriguing realm of crAPI testing. Our first port of call: the login interface. Here, we unleash the power of tools like ffuf or feroxbuster, conducting brute force tests to map directories and validate access without the need for credentials.
Portal login
The unraveled information is meticulously logged into our “memory bank” for future reviews, marking only the commencement of our thorough assessment.
ffuf -u "http://192.168.20.120:8888/FUZZ" -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -fs 2835
-u: This is where we specify the target URL, with “http://192.168.20.120:8888/FUZZ” acting as a placeholder for the word that will be tested in each iteration.**-w**: Think of this as the word arsenal! It’s where we define the list of words (in this case,/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt) that ffuf will use to launch its brute force attacks.-fs: Here, we set a size limit to filter responses. At 2835 bytes, it means ffuf will only show responses that are 2835 bytes or larger.
These nifty options empower ffuf to flex its muscles, systematically trying out different words from the list and sifting through responses based on their size. It’s like Sherlock Holmes combing through clues to uncover hidden paths or directories without the need for credentials. Quite the detective work, wouldn’t you say?
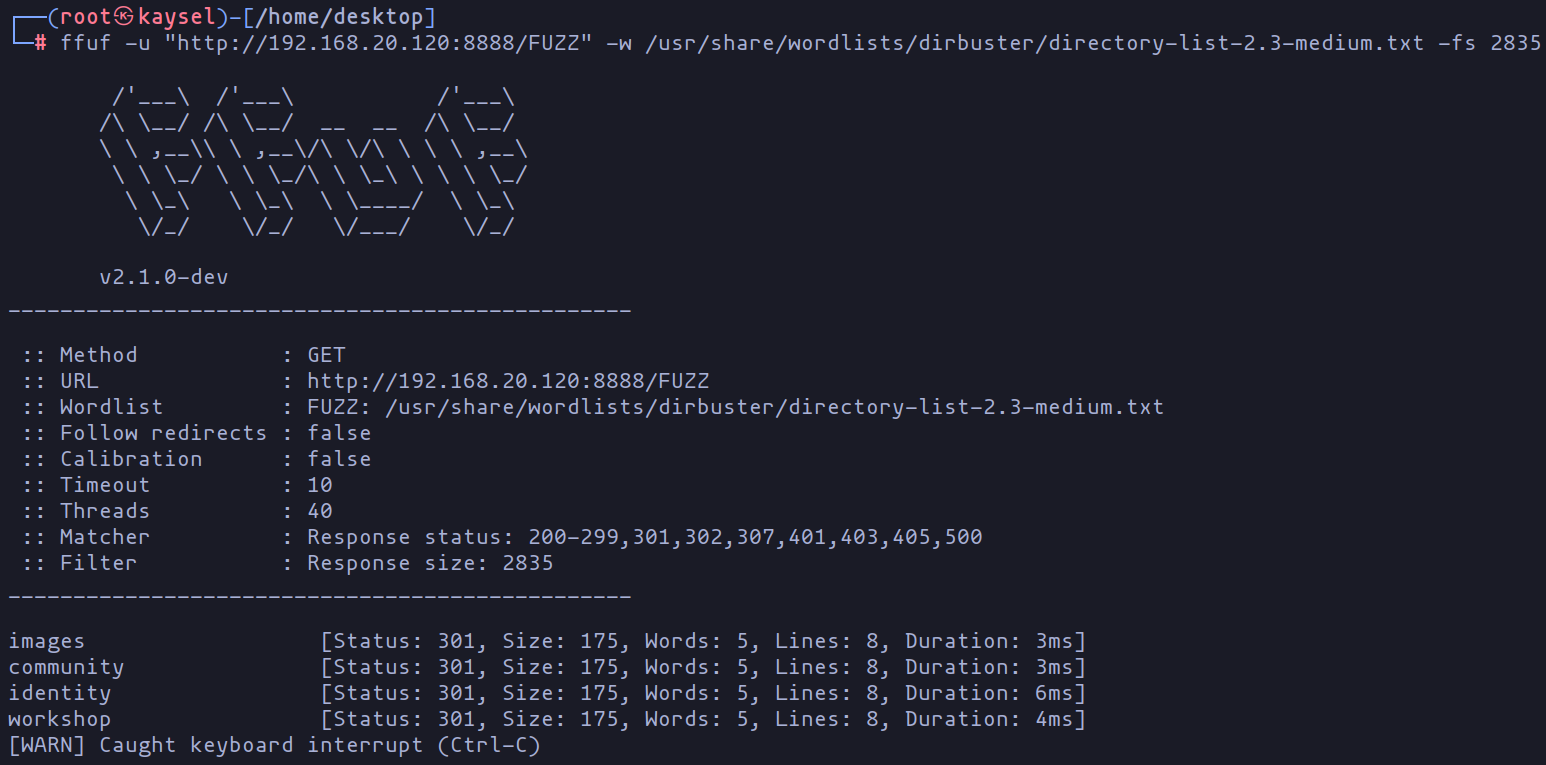
Ffuf results
User registration and initial glipse
Post-directory exploration, the next stride involves user registration to unlock the application’s functionalities.
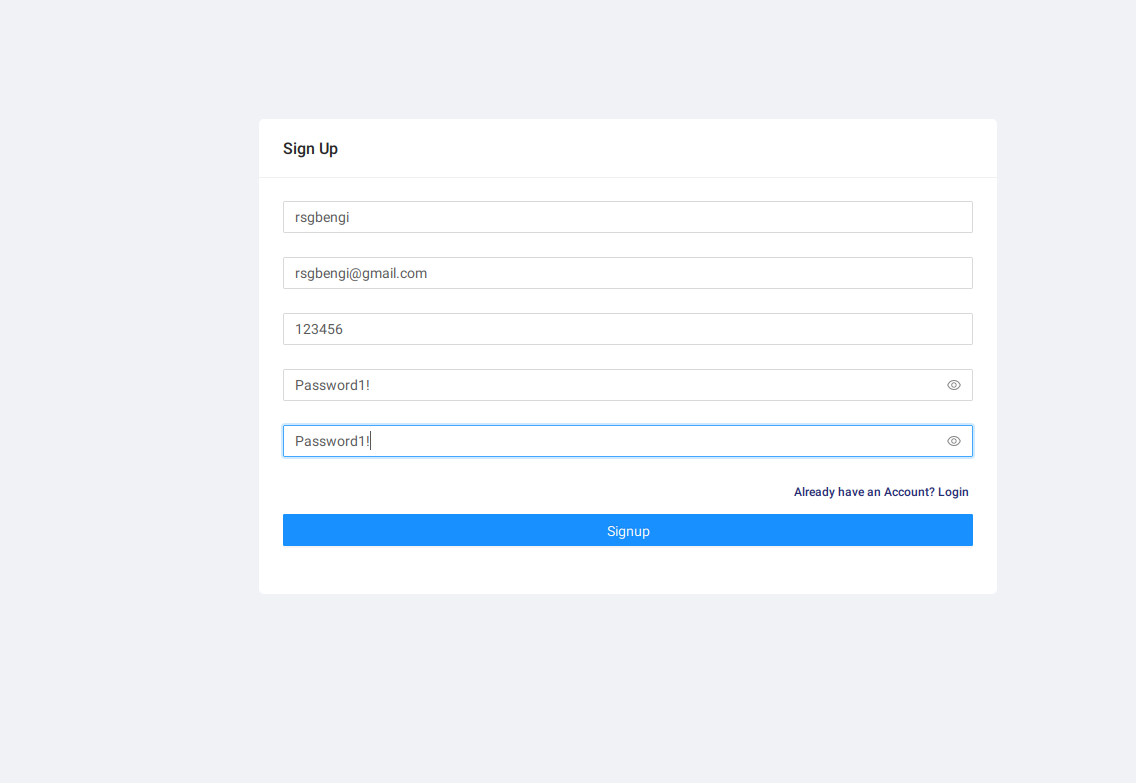
User registration
The payoff: distinct sections to explore, each revealing a facet of the digital landscape. A dashboard showcasing potential vehicle acquisitions, a store for procuring vehicle components, a community hub for user interactions, and a profile section encapsulating user characteristics.
Segmented Analysis
This segmentation allows us to deconstruct the seemingly vast application into manageable components, enabling a more focused testing approach. The identified sections for detailed scrutiny include:
- Login/Authentications Page
- Dashboard Information
- Component Purchase Area
- User Registration Area
- Community Area
- User Profile
Structuring the Test Memory
For effective documentation, our test memory aligns with these sections. As we delve into each area, pertinent details are recorded, encompassing functionality descriptions, operational processes, and thought-provoking questions. This meticulous documentation serves as a reference for the ongoing audit, ensuring a systematic and thorough examination of each facet.
By methodically covering these delineated areas, what initially appeared daunting is gradually deconstructed into comprehensible components, streamlining our testing process. The test memory becomes a dynamic repository, evolving with each audit iteration and fostering continuous improvement in our methodology.
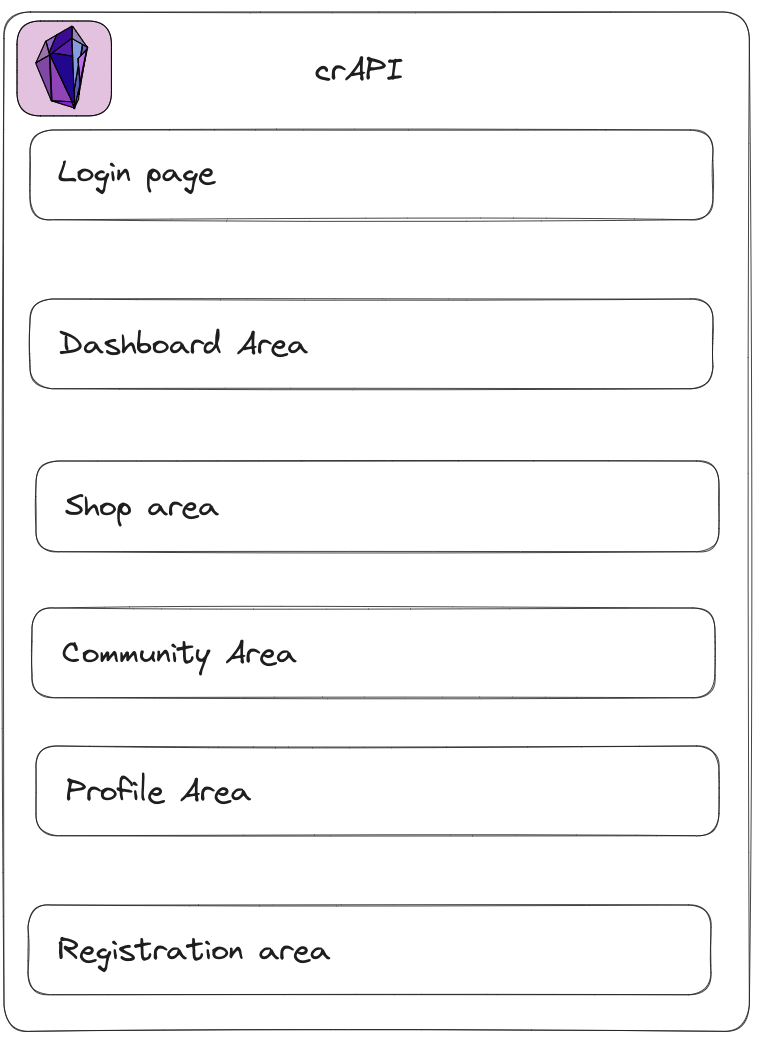
Structured memory
Navigating Each Section:
As we navigate through each of these sections, our approach involves capturing a detailed snapshot of the application’s landscape. This entails not just assessing functionalities but also delving into the intricacies of operations, prompting thoughtful questions, and encapsulating the essence of our exploration.
Functionality Descriptions:
Each section is a canvas on which the application paints a unique picture. We meticulously document the functionalities, offering a vivid description that encapsulates the purpose and potential impact.
Operational Insights:
Our scrutiny extends beyond the surface, unraveling the nuances of how different operations unfold within each area. This includes a step-by-step analysis, shedding light on the mechanics behind the user experience.
Thought-Provoking Questions:
In the pursuit of a comprehensive evaluation, we pose questions that serve as signposts for deeper inquiry. These questions not only assess current functionality but also stimulate reflection on potential improvements or vulnerabilities.
Continuous Iteration:
The documentation process is not a static endeavor. As we cover each area, our understanding evolves, prompting updates and refinements in our approach. It’s a dynamic journey of continuous improvement, mirroring the iterative nature of technology itself.
By weaving together descriptions, operational insights, and thought-provoking queries, our documentation becomes a rich narrative, providing not just a record of the application’s current state but a roadmap for its ongoing enhancement and fortification.
Conclusion
Up to this point, we’ve laid the foundation for our expedition into application auditing and API hacking. We’ve set up our lab, explored OWASP methodologies, and taken our initial steps in analyzing crAPI. But what happens when we face the most critical entry point: the login portal? How do we apply our skills specifically at this crucial juncture? In the next chapter, we’ll dive even deeper into the heart of the application, focusing on targeted tests for the login portal. Get ready to uncover how to unravel the hidden secrets behind each input field and strengthen crAPI’s security from its most vulnerable access point. Stay tuned as we unravel the next level of our API hacking adventure!
Chapters

Previous chapter
Next chapter


💬 Comments Available
Drop your thoughts in the comments below! Found a bug or have feedback? Let me know.