Harnessing the Power of Nuclei: A Guide to Advanced Vulnerability Scanning
13 min read
April 7, 2024

Introduction
In the ever-evolving landscape of cybersecurity, vulnerability scanners stand out as critical tools for protecting our digital environments. Among these essential tools, Nuclei emerges as a leading solution, characterized by its innovative approach to vulnerability detection. This guide aims to highlight the key features and functionalities of Nuclei, offering a clear roadmap for leveraging its capabilities:
- The Evolution of Digital Threats: As cybersecurity challenges become more complex, the need for advanced tools like Nuclei has never been more critical.
- Nuclei’s Distinction: Developed by ProjectDiscovery, Nuclei differentiates itself through a template-based, community-driven approach, enabling efficient and targeted vulnerability scans.
- Community-Curated Templates: At the heart of Nuclei’s success is its utilization of community-curated templates for detecting both known and “unknown” vulnerabilities, allowing for customizable and precise scans.
- Comprehensive Cybersecurity Solution: This guide provides a step-by-step exploration of Nuclei, from initial setup and template understanding to conducting first scans and analyzing results.
- Advanced Features and Applications: Delve into Nuclei’s advanced features, such as managing long-running scans and exploring fuzzing templates, to maximize its utility in your cybersecurity toolkit.
Join us as we delve into how Nuclei not only addresses today’s cybersecurity challenges but also equips us to face the threats of tomorrow. This journey through Nuclei’s functionalities will ensure you are well-equipped to enhance your digital defenses and maintain a proactive stance in the digital realm.
Methodology update
In this chapter, we will incorporate two critical enhancements to our methodology:
- Leveraging Vulnerability Scanners: Utilize vulnerability scanners to identify bugs that have been previously discovered in other web applications. This approach ensures that known vulnerabilities are not overlooked in your security assessments.
- Identifying Novel Web Vulnerabilities: Focus on the detection of new web vulnerabilities, specifically within GET request parameters, by employing fuzzing techniques. This proactive strategy aids in uncovering potential security flaws that have not yet been cataloged.
What Are Vulnerability Scanners?
In the vast and ever-evolving landscape of cybersecurity, one tool stands out as indispensable for fortifying our digital defenses: the vulnerability scanner. At its core, a vulnerability scanner is a specialized software designed to probe computer systems, networks, or applications for security weaknesses. These sophisticated tools play a critical role in the preemptive identification of vulnerabilities, allowing organizations and individuals to patch potential security breaches before they can be exploited by malicious actors.
The genesis of vulnerability scanners traces back to the early days of network computing, born out of the necessity to protect burgeoning digital infrastructures from emerging threats. Over the years, these scanners have evolved from simple, command-line interfaces to complex systems equipped with graphical user interfaces (GUIs), real-time analytics, and integrations with other cybersecurity tools.
There are several types of vulnerability scanners, each serving a distinct purpose:
- Network-based scanners focus on identifying vulnerabilities in networked devices and servers, scanning for open ports, and misconfigured firewalls.
- Web application scanners delve into web applications to find security flaws like SQL injection and cross-site scripting vulnerabilities.
- Wireless scanners are tailored to detect security issues within wireless networks, ensuring that Wi-Fi networks are secure and not prone to attacks.
- Database scanners aim to uncover vulnerabilities within databases, a critical component given the sensitive information they often hold.
The significance of vulnerability scanners goes beyond merely listing potential security flaws; they offer detailed insights into the severity of these vulnerabilities and provide recommendations for remediation. This proactive approach to security is a cornerstone of modern cybersecurity strategies, enabling organizations to stay one step ahead of potential threats.
As we delve deeper into the age of digital transformation, the role of vulnerability scanners will only grow in importance. They are not just tools but sentinels on the walls of our digital fortresses, guarding against the ceaseless tide of cyber threats. In this ongoing battle for cyber safety, understanding and leveraging vulnerability scanners is not just advisable; it’s imperative.
The importance of vulnerability scanners in our digital defense arsenal cannot be overstated. These tools scan our networks, systems, and applications, hunting for weaknesses that could be exploited by cyber adversaries. Among the myriad of options available in the cybersecurity landscape, one tool has risen to prominence for its unique approach and effectiveness: Nuclei.
What is Nuclei?
Nuclei stands at the forefront of vulnerability scanning technology, a testament to what can be achieved when innovation meets the pressing needs of cybersecurity. Developed by the visionary team at ProjectDiscovery, Nuclei is not merely another entry in the catalog of vulnerability scanners. It is a purpose-built tool designed to revolutionize the way we approach vulnerability detection and analysis.
Key Highlights of Nuclei:
- Template-based Scans: Nuclei distinguishes itself with its template-driven approach. This innovation allows users to conduct highly specific and customizable scans, focusing on the vulnerabilities that matter most to their organization’s security posture.
- Unmatched Speed and Efficiency: In the fast-paced world of cybersecurity, where threats evolve by the second, Nuclei’s ability to perform rapid, yet thorough scans is invaluable. It ensures that organizations can stay ahead of potential vulnerabilities, safeguarding their digital assets more effectively.
- A Flourishing Community: The strength of Nuclei lies not just in its technical capabilities, but also in the vibrant community that supports it. Security professionals from around the globe contribute to its ever-growing repository of templates, ensuring that Nuclei remains on the cutting edge of vulnerability detection.
- Seamless Integration: Understanding the importance of interoperability in cybersecurity, Nuclei is designed to integrate effortlessly with existing security tools and workflows. This makes it an indispensable addition to any security team’s toolkit, enhancing their capabilities without disrupting established processes.
Getting Started with Nuclei
Starting your adventure with Nuclei is straightforward, designed to empower both experienced and novice cybersecurity enthusiasts to bolster their defense mechanisms efficiently. This guide will walk you through the initial steps, focusing on program installation and the foundational concept of templates for vulnerability detection.
Installation
Installing Nuclei is a hassle-free process, accommodating various platforms. There are two main avenues for installation:
- Using Go: If you have Go installed on your system, Nuclei can be easily set up using package managers with a simple command. This method ensures that you’re always running the most current version of the software.
go install -v github.com/projectdiscovery/nuclei/v3/cmd/nuclei@latest
- Direct Download: For those without Go, the latest release of Nuclei can be directly downloaded from its GitHub repository. This option provides flexibility for users across different operating setups.
Before proceeding with the installation, verify that your system meets the necessary prerequisites for the chosen method. For the latest installation instructions and to choose the best option for your needs, visit the official Nuclei GitHub page: https://github.com/projectdiscovery/nuclei.
Understanding Nuclei Templates
At the core of Nuclei’s efficiency in detecting vulnerabilities are its templates. These templates, formatted in YAML or JSON, serve as the blueprint for scanning, defining specific conditions and patterns that Nuclei searches for in target applications.
- Template-Based Detection: By utilizing a collection of predefined templates, Nuclei can swiftly identify known vulnerabilities across a wide range of systems and applications. This method significantly reduces the time and complexity involved in setting up detailed scans.
- Customization and Community Support: The ability to understand and modify template structures allows for tailored vulnerability assessment. Additionally, the vibrant Nuclei community contributes to a growing repository of templates, ensuring the tool remains updated with the latest threat intelligence.
Exploring the template documentation available on Nuclei’s GitHub or diving into the community-curated templates will equip you with the knowledge to effectively harness the power of Nuclei in your security audits.
Using nuclei
In our journey through understanding vulnerability scanners, we’ve tackled theoretical aspects and delved into some intricate details of Nuclei. Now, it’s time to shift our focus towards practical applications, exploring essential use cases you’ll want to remember.
Launching Nuclei with the “-h” option unveils a plethora of settings, which might initially seem daunting. However, fret not; while many options fine-tune the tool’s behavior, we’ll concentrate on the fundamental features that are crucial for getting started.
Nuclei help command
Nuclei, a template-driven tool aimed at detecting previously identified vulnerabilities, benefits greatly from regular updates. To keep your toolkit sharp, use the update flag to refresh your templates, typically housed in the default directory:
~/nuclei-templates/
Nuclei update
Nuclei template directory
An example within this directory, such as:
~/nuclei-templates/http/technologies/angular-detect.yaml
demonstrates the plethora of templates for software version detection. Take the Angular detection template; its syntax, while straightforward, is a prime example of how these templates aim to identify specific attributes—in this case, “ng-version”—within the responses from targeted URLs.
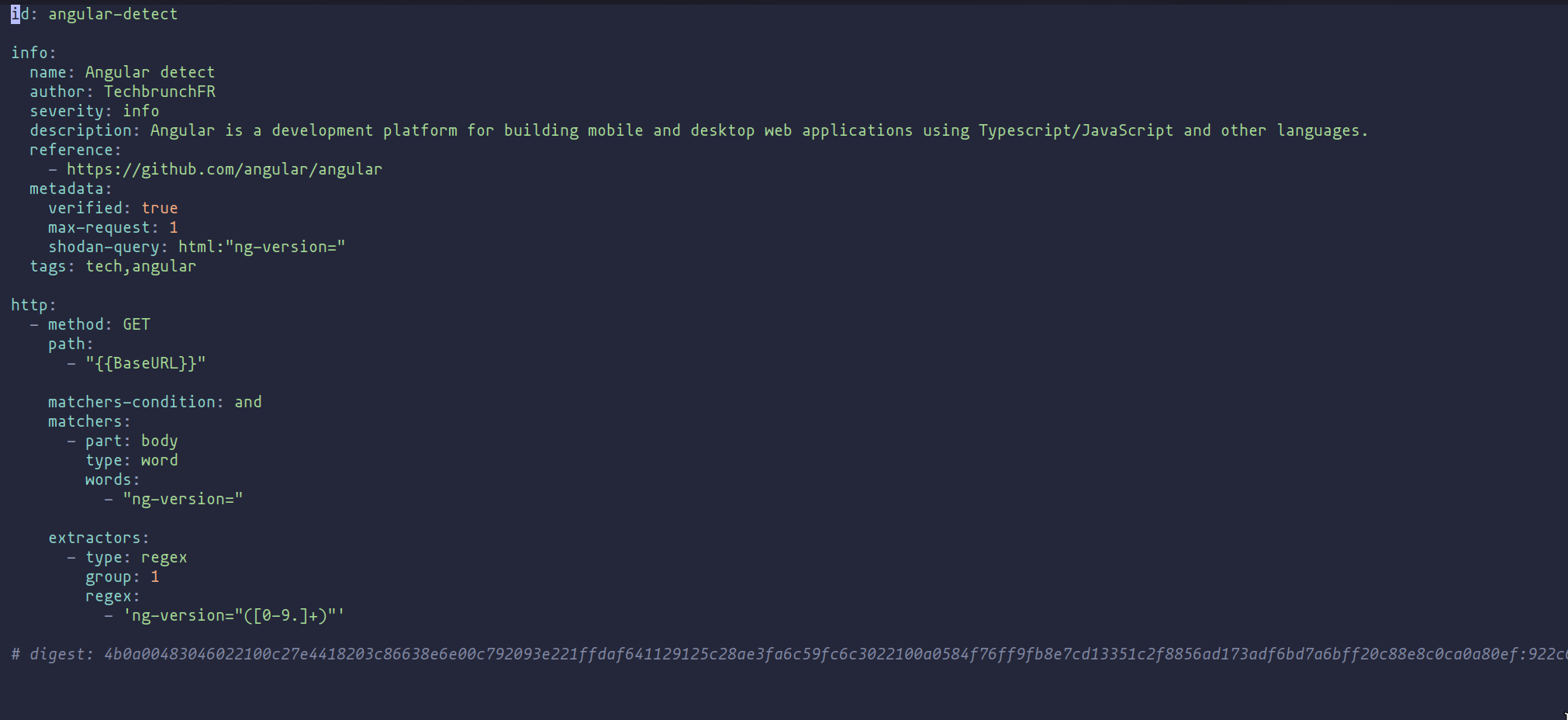
Angular detection template in YAML format
If you inspect pages like juice-shop, you’ll notice the “ng-version” attribute in action, demonstrating Angular’s presence.
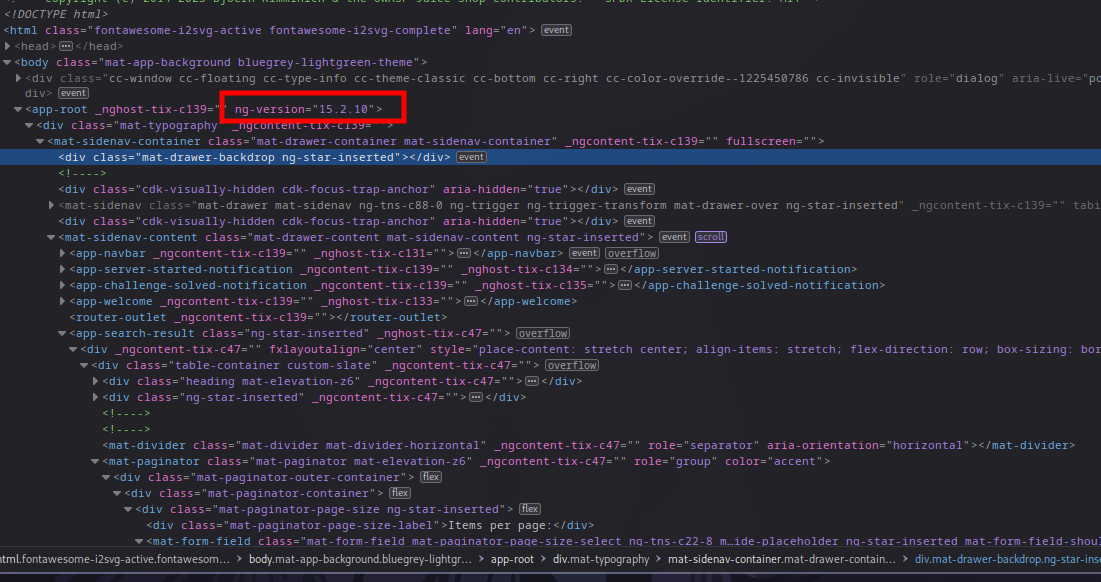
Version of angular in the response
After running Nuclei, you should find a detailed output, categorizing vulnerabilities by their criticality, with many classified as informational.
nuclei -u <url>
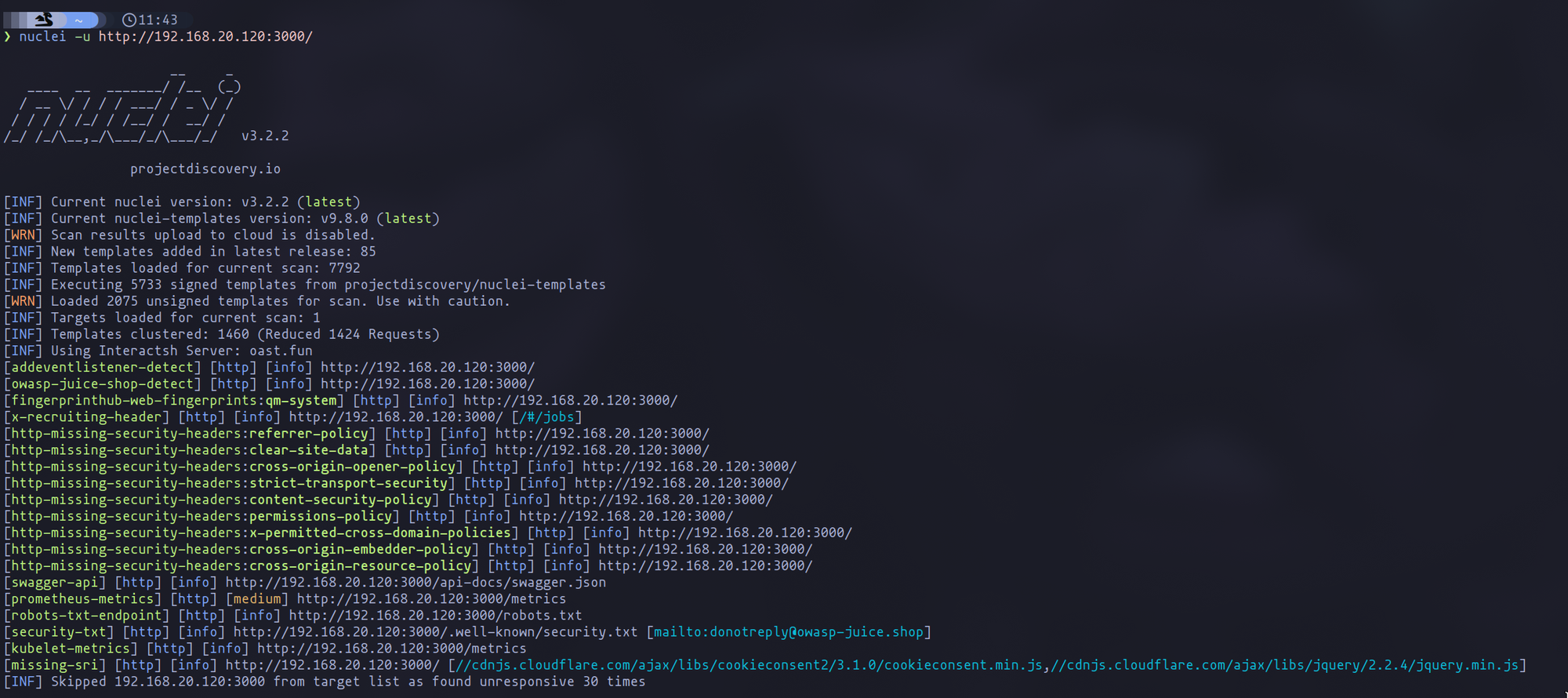
Nuclei execution
Nonetheless, you might find noteworthy findings, such as medium-risk application metrics or missing security headers—a different approach from what was discussed in our second chapter.
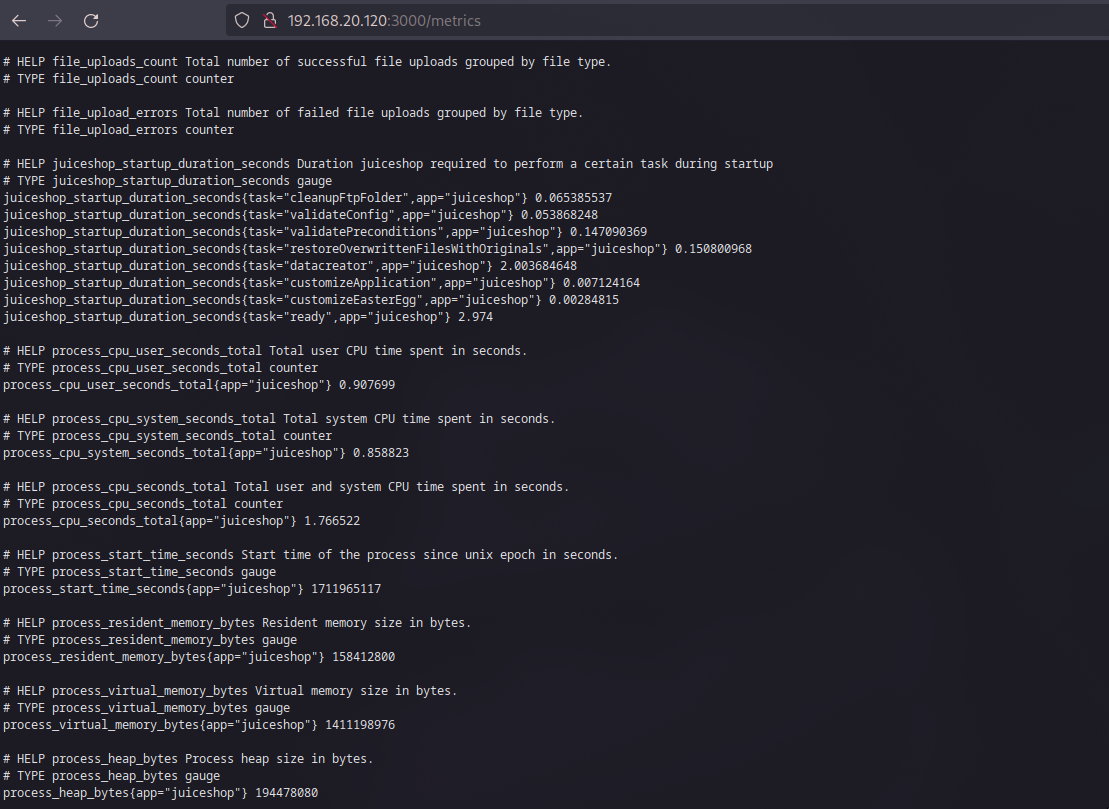
Application metrics
An intriguing observation might be the absence of Angular detection in your results. This occurs because Angular applications, as we’ve learned, require browser simulation to fully reveal the content of their responses. This can be achieved by running Nuclei with the “headless” flag, a crucial step for a comprehensive initial scan.
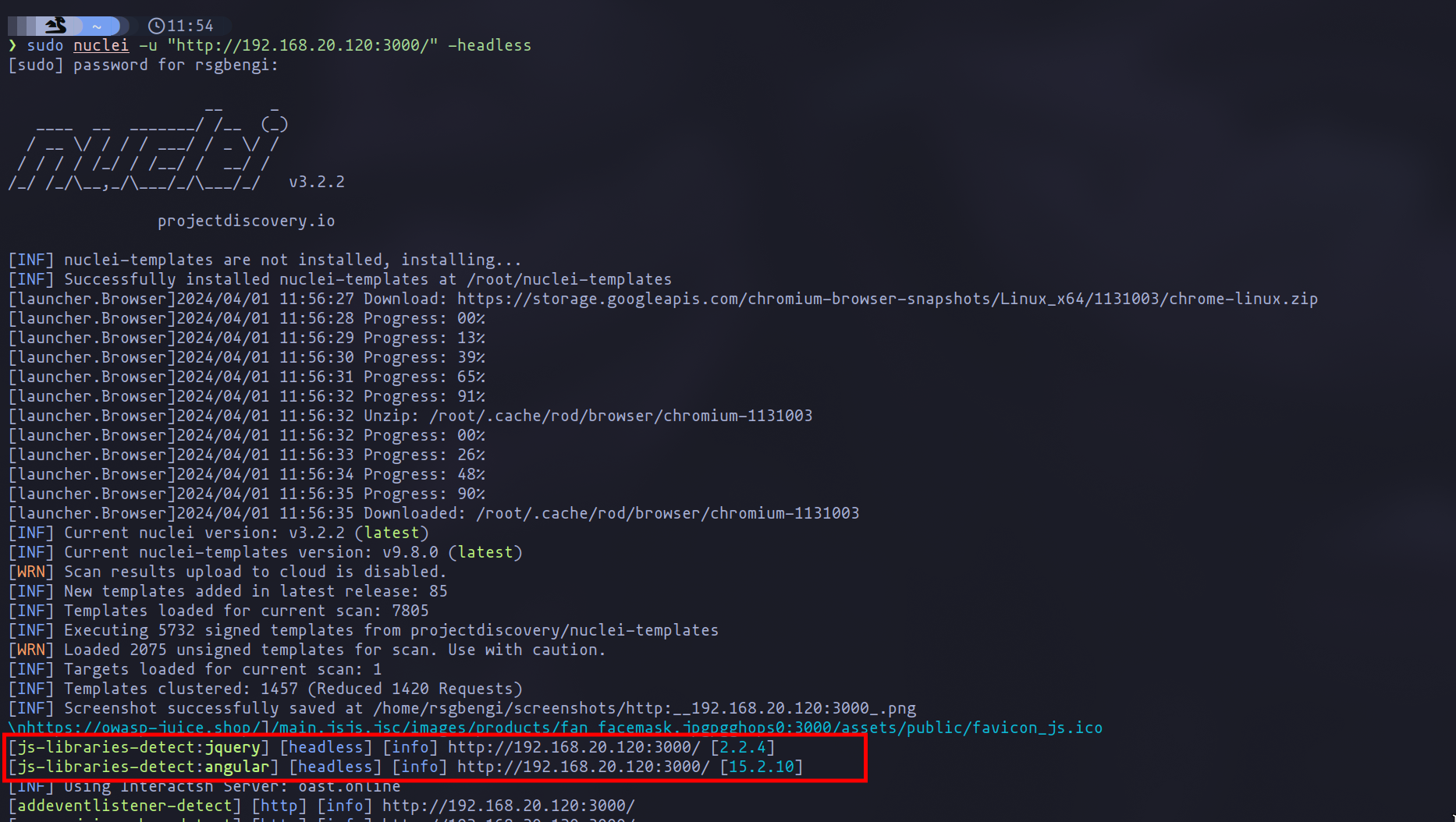
Headless execution
Nuclei offers numerous flags that tailor the scanning process to your needs, whether you’re adjusting the level of output detail or controlling the volume of requests. Notable options include:
- —severity: Filters templates by their severity level (info, low, medium, high, critical), enabling targeted testing based on vulnerability severity.
- —proxy: Routes Nuclei’s traffic through a specified proxy, useful for anonymizing scans, debugging, or scanning from specific locations. This flag supports HTTP, HTTPS, and SOCKS5 proxies.
- -tags: Allows the use of one or more tags to refine template selection based on vulnerability type, issue, or targeted system. For instance, to focus on SQL injection vulnerabilities, you might use
-tags sqli.
Exploring Advanced Nuclei Templates for Fuzzing
In our discussions so far, we’ve navigated through using Nuclei for detecting known vulnerabilities, invaluable for external penetration testing across numerous servers. However, when it comes to web application penetration testing, identifying application-specific vulnerabilities requires a different approach. This is where fuzzing templates come into play.
To leverage these fuzzing templates effectively, we’ll need to target GET requests at various endpoints with parameters. A practical way to gather such endpoints involves using proxies. By creating a plugin that logs URLs during your exploration of the application (in case of using mitmproxy), you can amass a significant list of potential targets.
mitmdump -s export_urls.txt
from mitmproxy import http
def request(flow: http.HTTPFlow) -> None:
# Abre el archivo cada vez que se captura una petición
with open("urls.txt", "a") as file:
# Escribe la URL de la petición capturada en el archivo y añade un salto de línea
file.write(flow.request.pretty_url + "\n")
This method enables the accumulation of URLs while investigating an application. Additionally, tools like Katana can be employed to directly collect parameters, offering a versatile approach to scanning application vulnerabilities.
katana -u "<url>" -f qurl -jc -headless -silent | nuclei
After gathering a sufficient list of endpoints, filter those with parameters for fuzzing. If you haven’t utilized Katana’s one-liner, you can still prepare your list for fuzzing as follows:
cat urls.txt | grep "192" | grep "?" | grep -v "socket" | sort -u > urls_to_fuzz.txt
nuclei -t fuzzing_templates/ -list urls_to_fuzz.txt -fuzz -headless
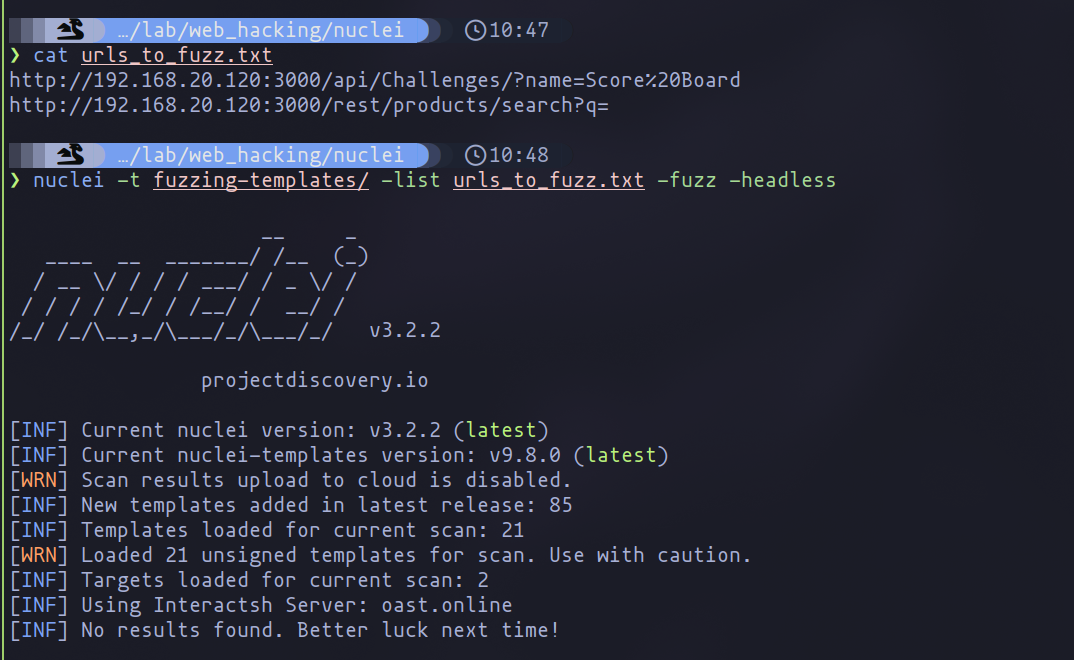
Fuzzing Execution
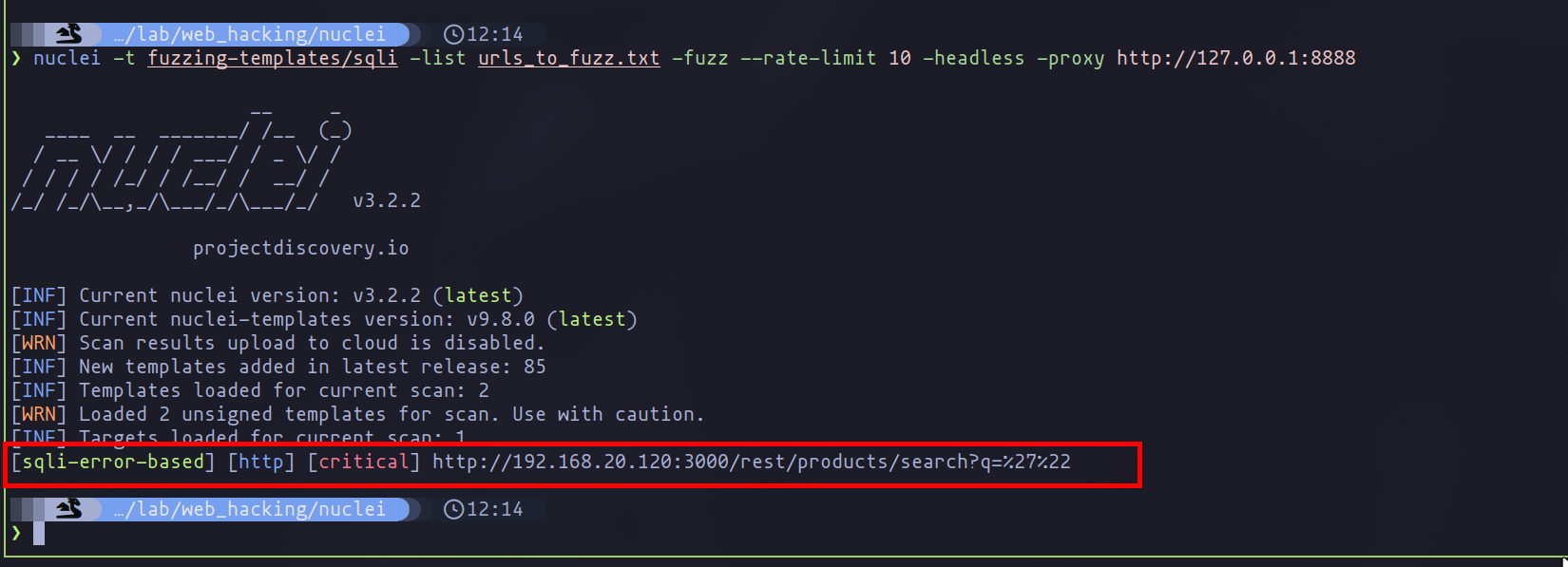
While initial runs may not yield results, this doesn’t imply the absence of vulnerabilities, such as SQL injection or DOM XSS. Employing Nuclei with a proxy to analyze responses can reveal errors indicative of vulnerabilities, such as SQLI errors, not captured by current templates due to the lack of specific error patterns.
nuclei -t fuzzing-templates/ -list urls_to_fuzz.txt -fuzz --rate-limit 10 -headless -proxy http://127.0.0.1:8888
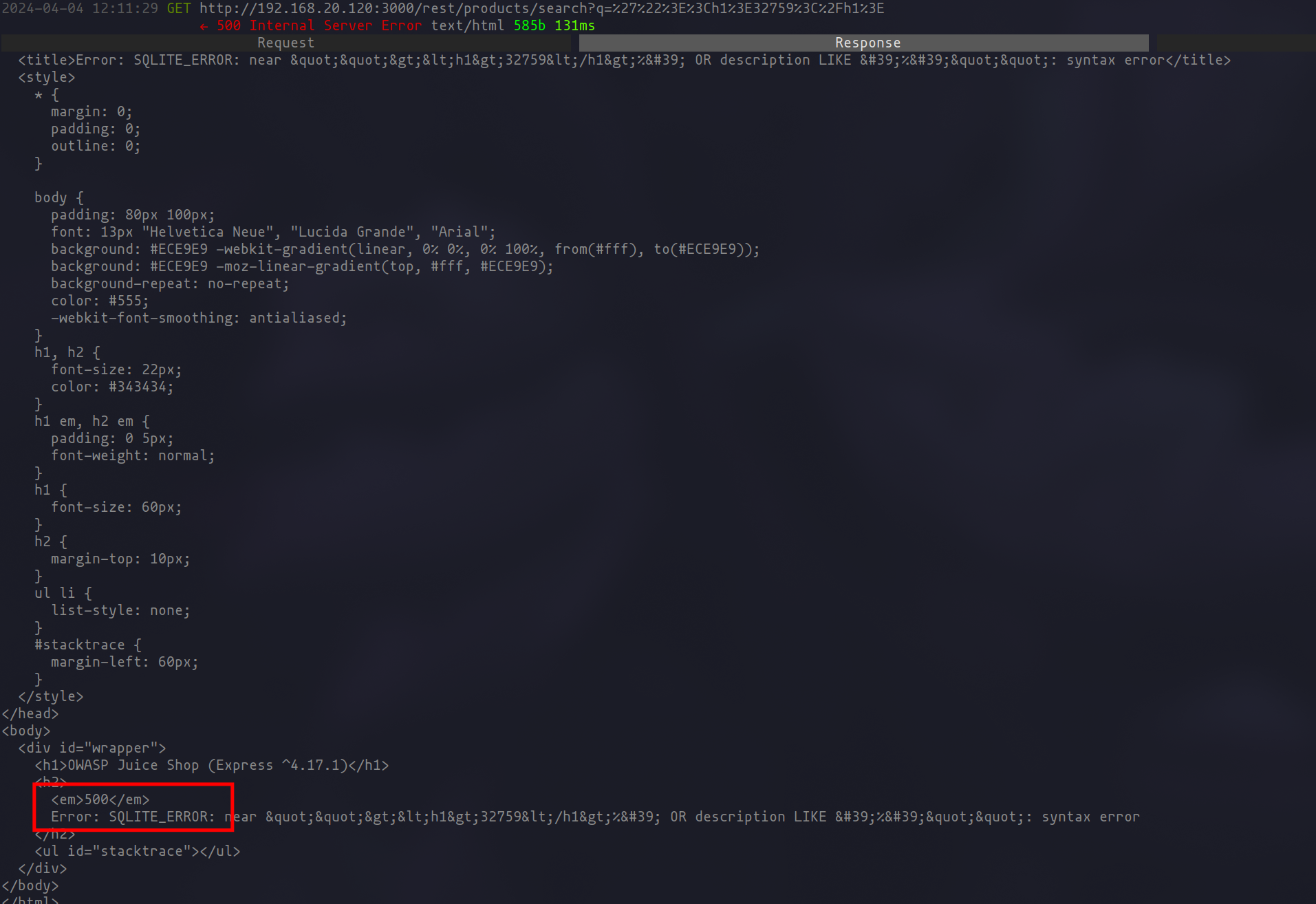
Response contains SQLite error
In cases where known errors aren’t detected by existing templates, customizing templates to include these patterns can enhance detection capabilities.
lab/web_hacking/nuclei/fuzzing-templates/sql
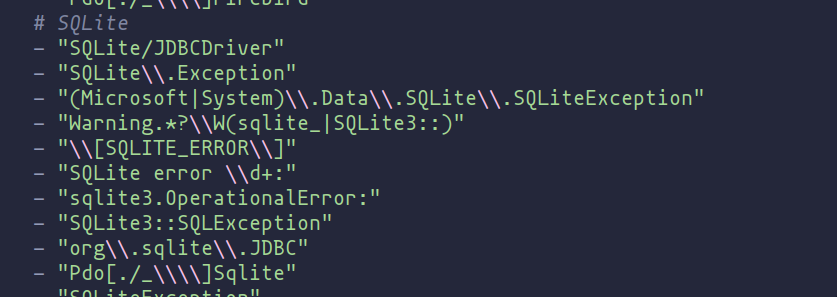
SQLite errors currently included
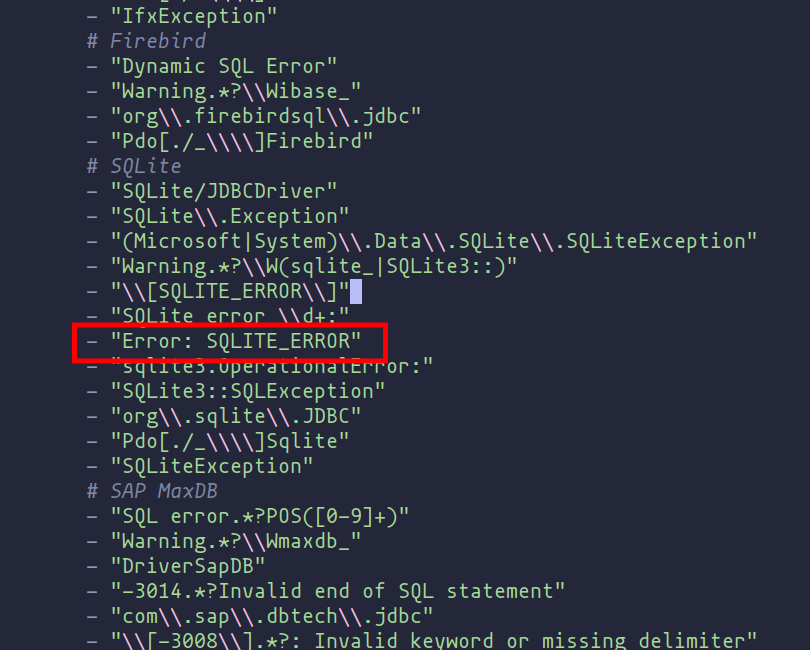
New error included
Detection of vulnerability
As we progress, we’ll delve deeper into the intricacies of the Nuclei template system, exploring how to craft a personalized vulnerability scanning engine that can identify a wider range of vulnerabilities, further enhancing our penetration testing toolkit.
Managing Long-Running Nuclei Scans with Save Points
In the realm of penetration testing, time is often of the essence. Nuclei, while powerful, can sometimes run lengthy scans that don’t neatly fit into the tight schedules of a pentesting assignment. Recognizing this challenge, Nuclei incorporates a valuable feature designed to accommodate the dynamic pacing of penetration tests: the ability to save and resume scan progress.
When you’re running a scan and need to pause—for instance, due to time constraints or the need to reallocate resources—simply interrupt the scan with Ctrl+C. This action triggers Nuclei to automatically generate a save file. This save file is crucial as it meticulously records the scan’s current state, ensuring no progress is lost.
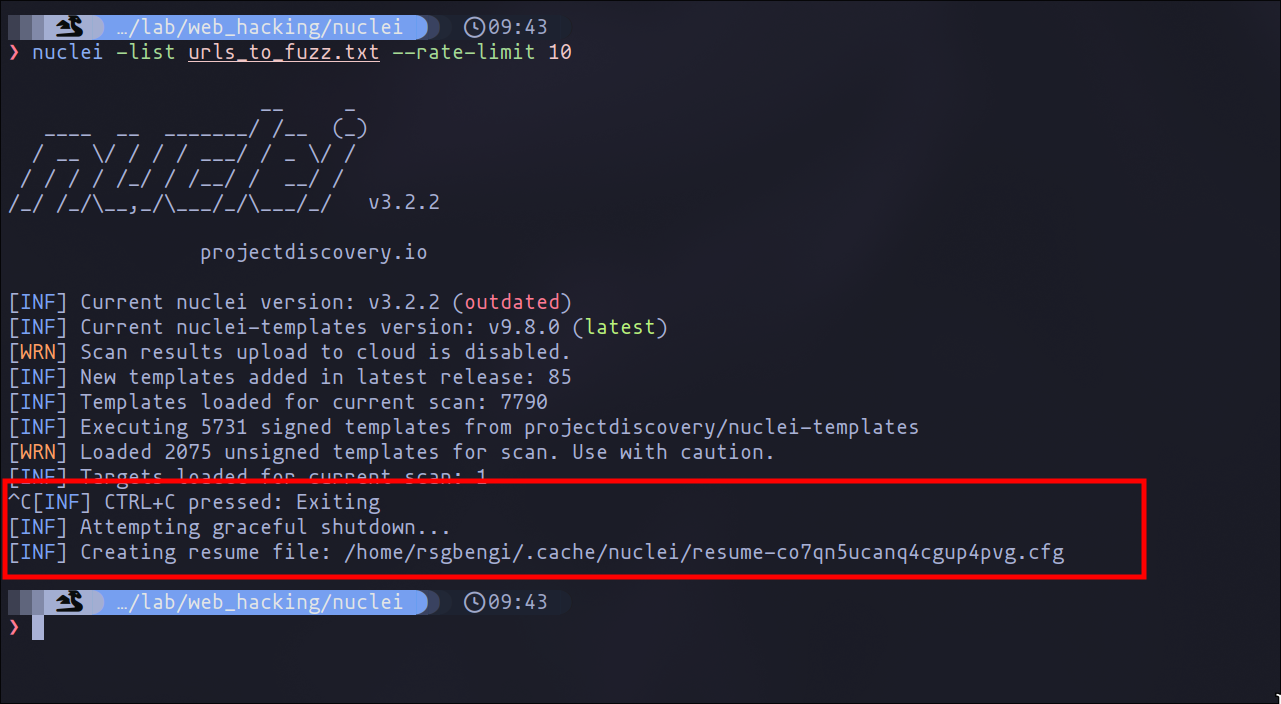
Stop the execution
The beauty of this functionality lies in its simplicity and the flexibility it offers to penetration testers. When you’re ready to resume the scan, you can use this save file to pick up exactly where you left off, ensuring a seamless continuation of your testing activities without the need to start from scratch.
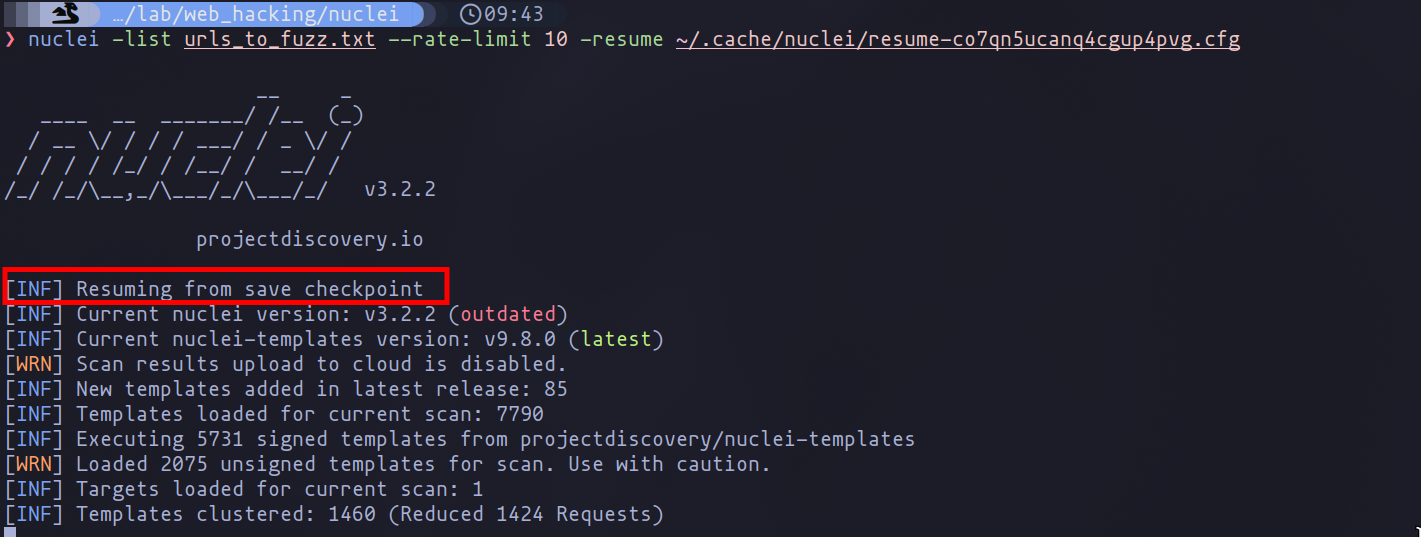
Execution from save point
Conclusions
In conclusion, Nuclei emerges as a pivotal tool in the cybersecurity landscape, offering a comprehensive, template-driven approach to vulnerability scanning. This guide highlights Nuclei’s unique position, underpinned by community-driven innovation and its capability to meet the nuanced demands of modern cybersecurity. As we delve into its functionalities, from basic installations to leveraging advanced features like fuzzing templates and managing long scans, it’s evident that Nuclei is more than just a tool; it’s an integral part of a proactive defense strategy against the ever-evolving cyber threats.
For those keen on deepening their understanding of Nuclei and maximizing its potential, the Project Discovery guide serves as an invaluable resource. It not only provides detailed instructions and insights into the tool’s extensive capabilities but also connects users with a community of cybersecurity professionals dedicated to refining and expanding Nuclei’s applications. Visiting the Project Discovery guide will equip you with the knowledge and skills to harness Nuclei’s full power, ensuring your digital environments are fortified against the challenges of tomorrow.
As we conclude, the importance of tools like Nuclei in safeguarding our digital frontiers cannot be overstated. In the ongoing battle for cybersecurity, knowledge, and preparedness are key. Nuclei, with its innovative approach and the support of a vibrant community, offers a beacon of hope, showcasing the potential of collaborative efforts in overcoming the cyber threats of the digital age.
Chapters

Previous chapter
Next chapter


💬 Comments Available
Drop your thoughts in the comments below! Found a bug or have feedback? Let me know.