Unveiling Shadows: Navigating the Risks of Unauthenticated API Access and Excessive Information Exposure
8 min read
February 16, 2024

Table of contents
Introduction
Welcome to the latest chapter in our dedicated API hacking series. Today, we embark on a detailed exploration of two pivotal vulnerabilities that present significant risks to API security: Unauthenticated API Access and Excessive Information Exposure. This chapter is designed to not only enhance your understanding of these vulnerabilities, but also to provide you with practical strategies for their identification and mitigation. Leveraging the power of tools like Burp Suite and Aquatone, we'll dive into real-world scenarios that bring these abstract concepts to life. As we dissect these vulnerabilities, our goal is to arm you with the knowledge and expertise necessary to fortify your applications against potential breaches. Prepare to deepen your insights into the critical aspects of API security, ensuring you're well-equipped to navigate the challenges of the digital age.
Unauthenticated API Access: Unveiling Hidden Entrances
Unauthenticated API access as a vulnerability refers to a security flaw in which APIs can be accessed without any form of authentication. This means that sensitive endpoints within an application's API are exposed to potential unauthorized use, allowing attackers to access or manipulate private data, execute unauthorized functions, or potentially gain further access to the system without needing to verify their identity.
This vulnerability arises from insufficient security measures during API development and deployment, where endpoints are not properly secured with authentication mechanisms. As we've seen in one of the chapters of our series, the application in question manages authentication using JSON Web Tokens (JWT). Despite JWT's potential for securing access, without rigorous implementation and checks, APIs remain vulnerable to unauthorized access, posing significant security risks.
The consequences of exploiting unauthenticated API access can be severe, ranging from data breaches and loss of sensitive information to system compromise and operational disruption. Attackers can use unauthenticated access to bypass security controls, elevate their privileges within a system, or launch further attacks against other parts of the network.
Practical Exploration: Unmasking Unauthenticated Access
To identify vulnerabilities of this kind, it's best to have thoroughly examined the entire application and gathered a substantial number of requests in Burp's history. Detecting such vulnerabilities entails testing each request without the JWT to determine if the same information can be accessed.
While scrutinizing requests in a small-scale application like crAPI may be manageable, the task becomes considerably more cumbersome in larger, real-world applications where the volume of requests is typically much higher. Thankfully, there are solutions available to automate parts of this process. One commonly used tool in conjunction with Burp is Autorize, known for its ease of use and efficiency in navigating through extensive request logs. If you're interested, you can explore its repository for further details.
On a different note, I've decided to take a different approach by leveraging a combination of other tools to enhance visualization. Allow me to introduce you to Aquatone. This tool is primarily tailored for external pentesting, generating concise reports with screenshots of discovered web pages for effortless visualization. However, it also proves to be quite effective for authorization testing, offering a convenient overview of vulnerable requests or endpoints.
You'll quickly grasp its utility. Here's the GitHub link for you to download and explore further.
To proceed, you'll need to copy all the URLs you've collected in Burp Suite:
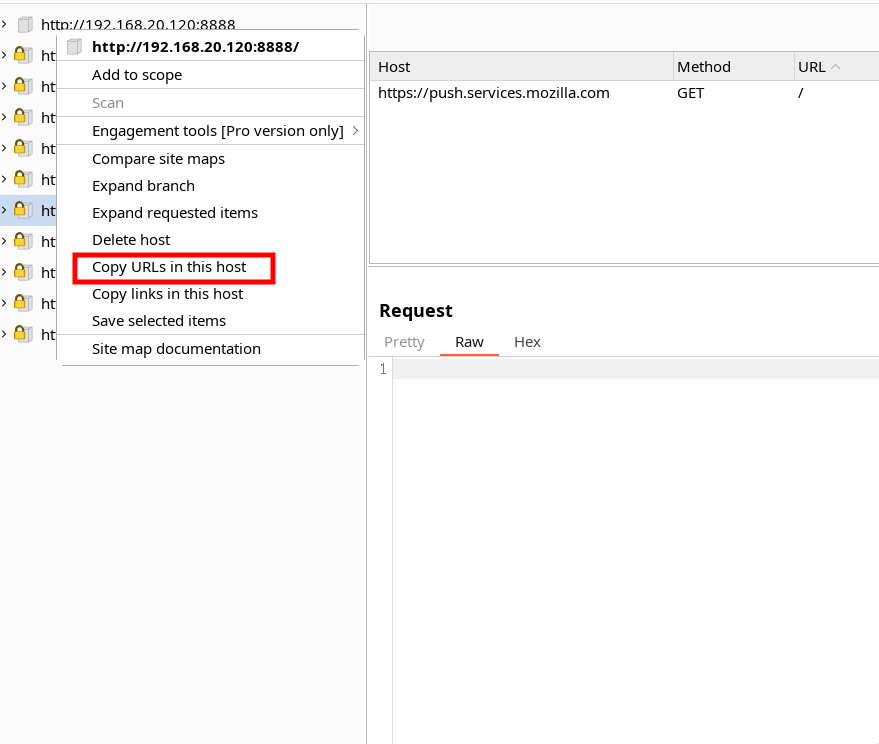
Once you've completed that step, we'll initiate Aquatone as follows:
cat ../endpoints.txt | aquatone
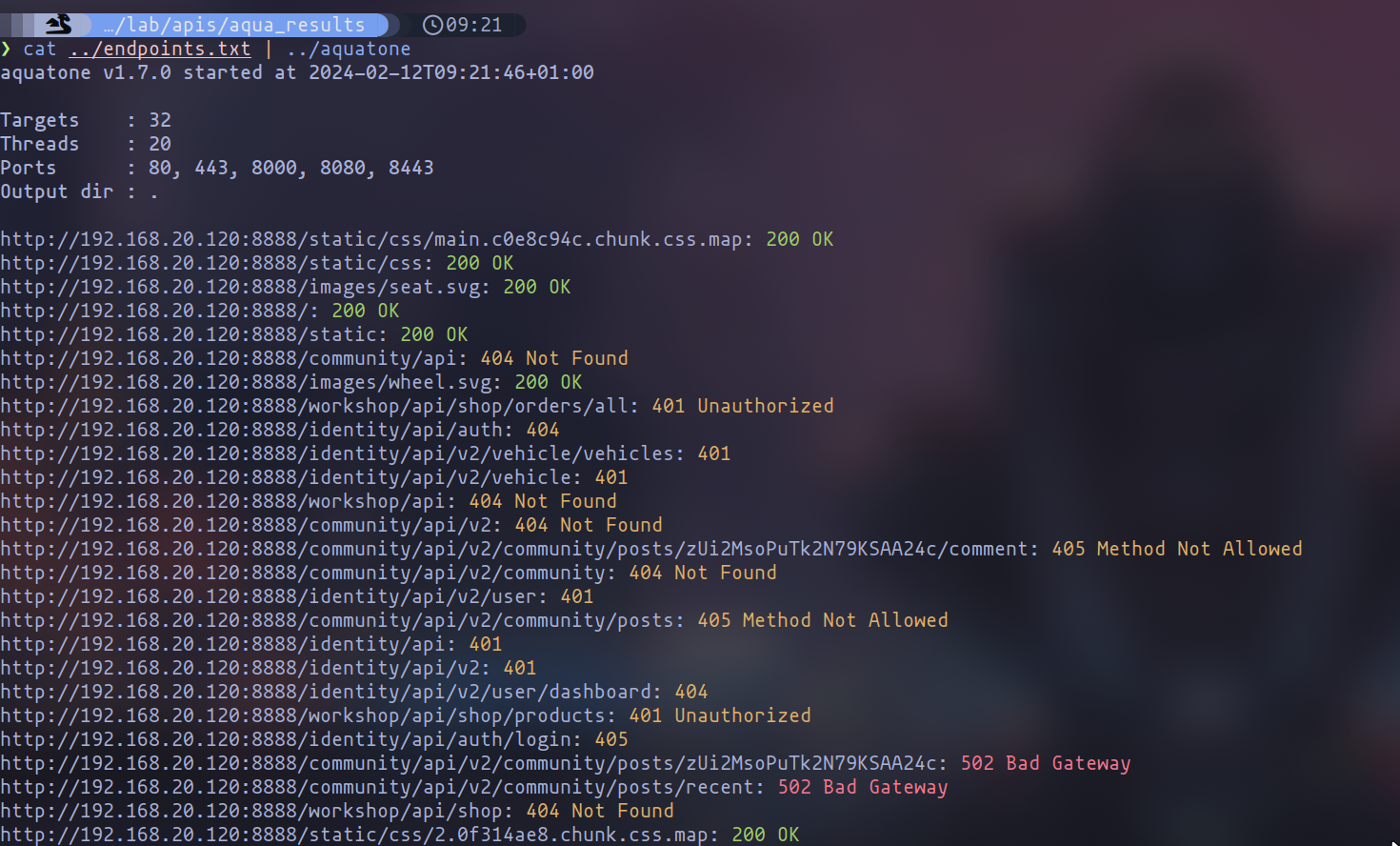
The execution should yield the following results, with our primary interest lying in "aquatone_report.html".
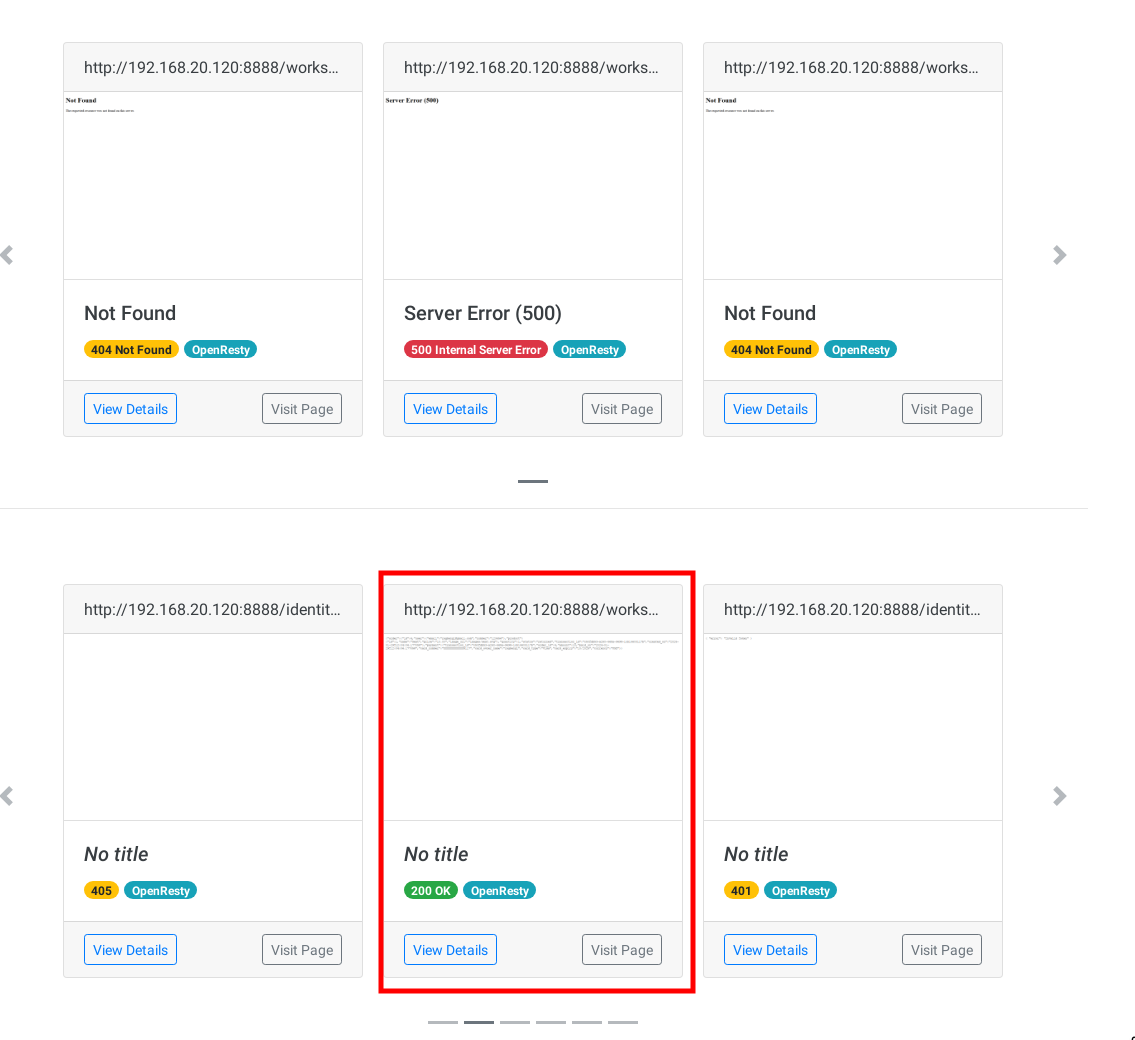
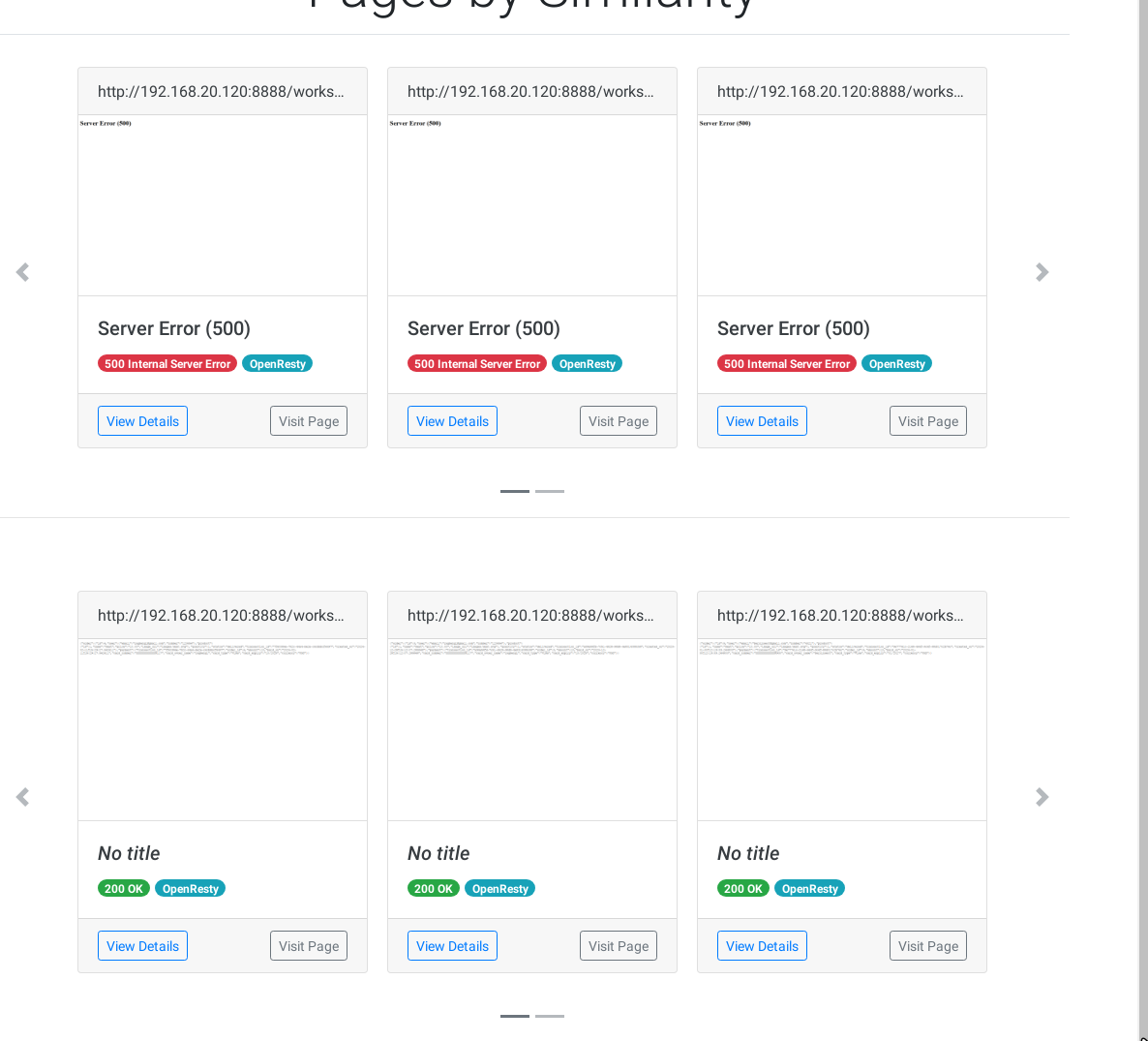
Accessing the report with Chromium, we'll be presented with all the results, allowing us to swiftly identify the endpoints of interest, thanks to Aquatone's categorization. In the image below, the highlighted endpoint stands out as particularly significant, revealing the outcome of a successful API request made without the inclusion of a JWT, thereby indicating a vulnerability:
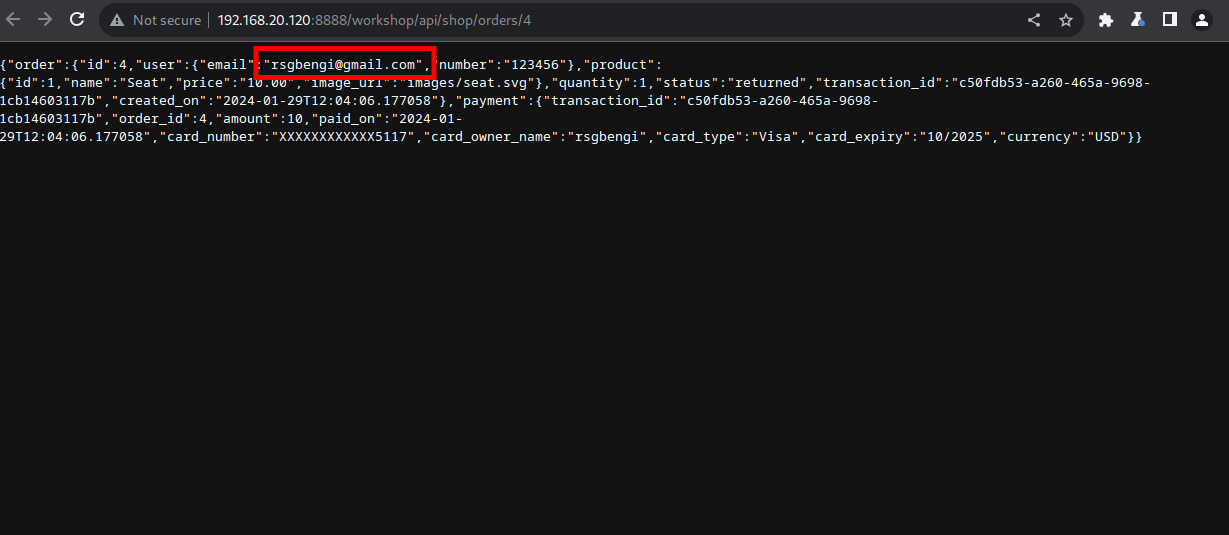
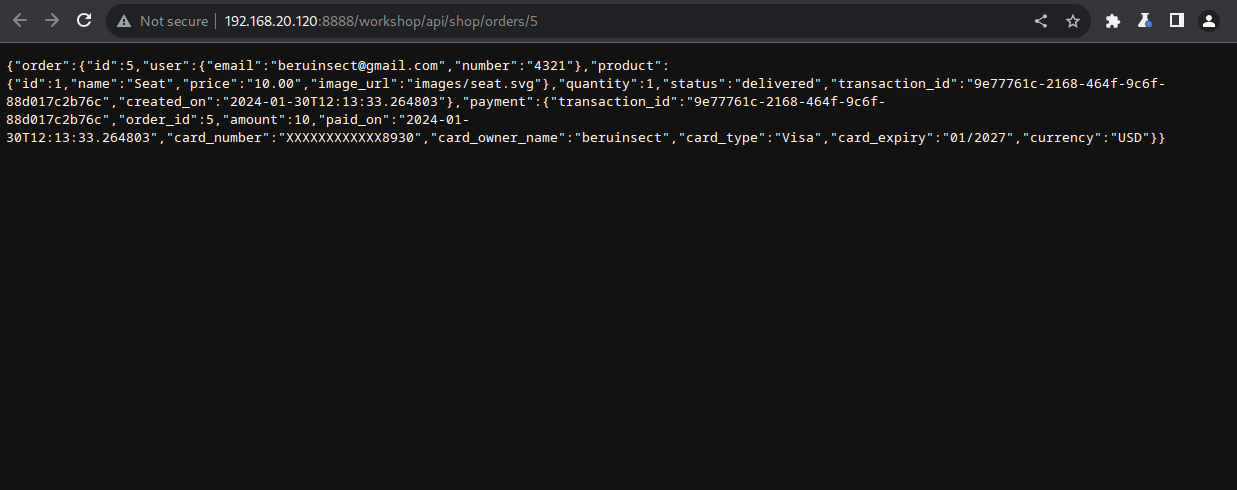
The vulnerable request pertains to viewing past purchases within the application. This can be verified by utilizing Burp Suite and accessing the functionality to view past purchases, as demonstrated in the following two images:
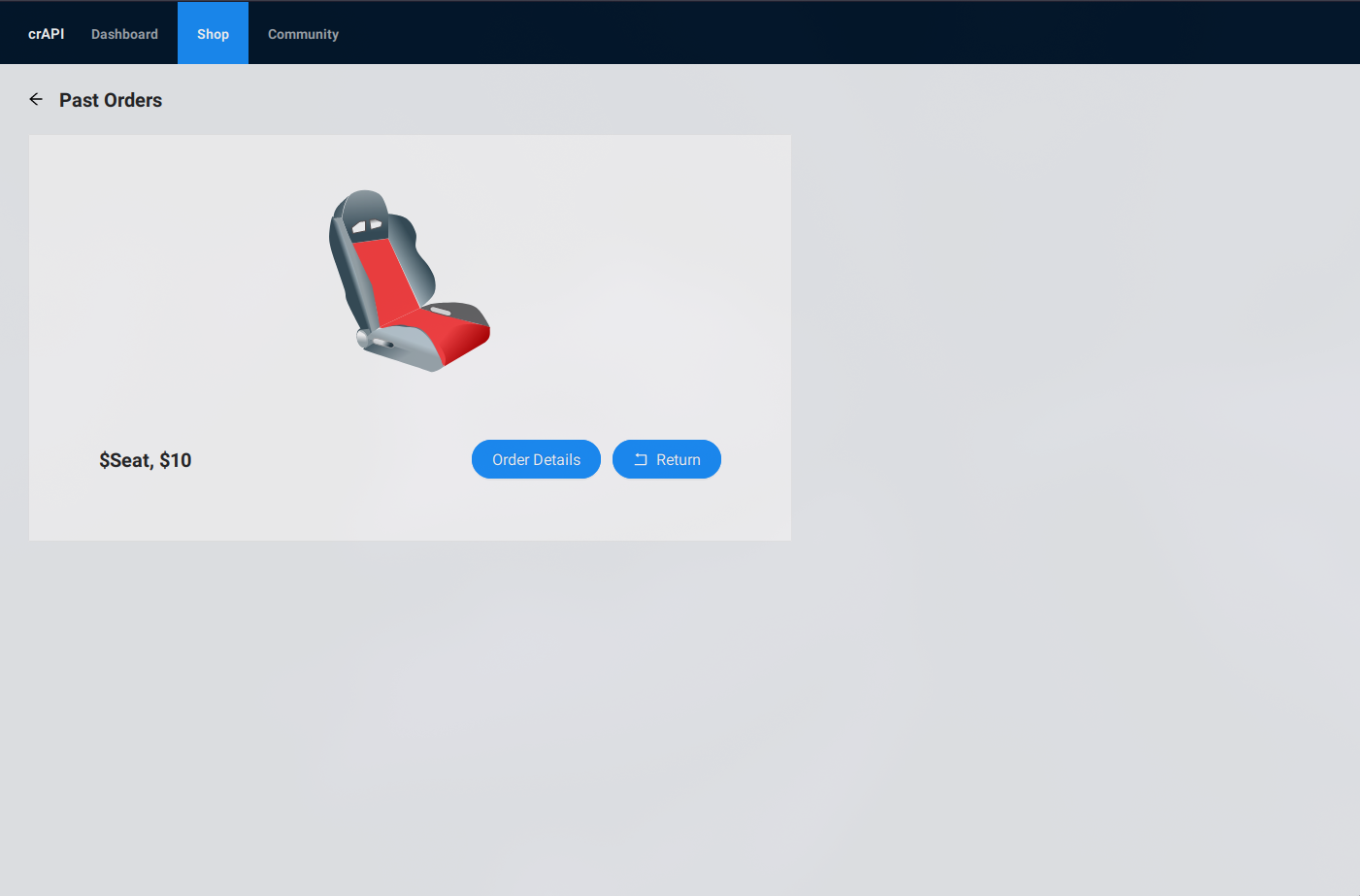
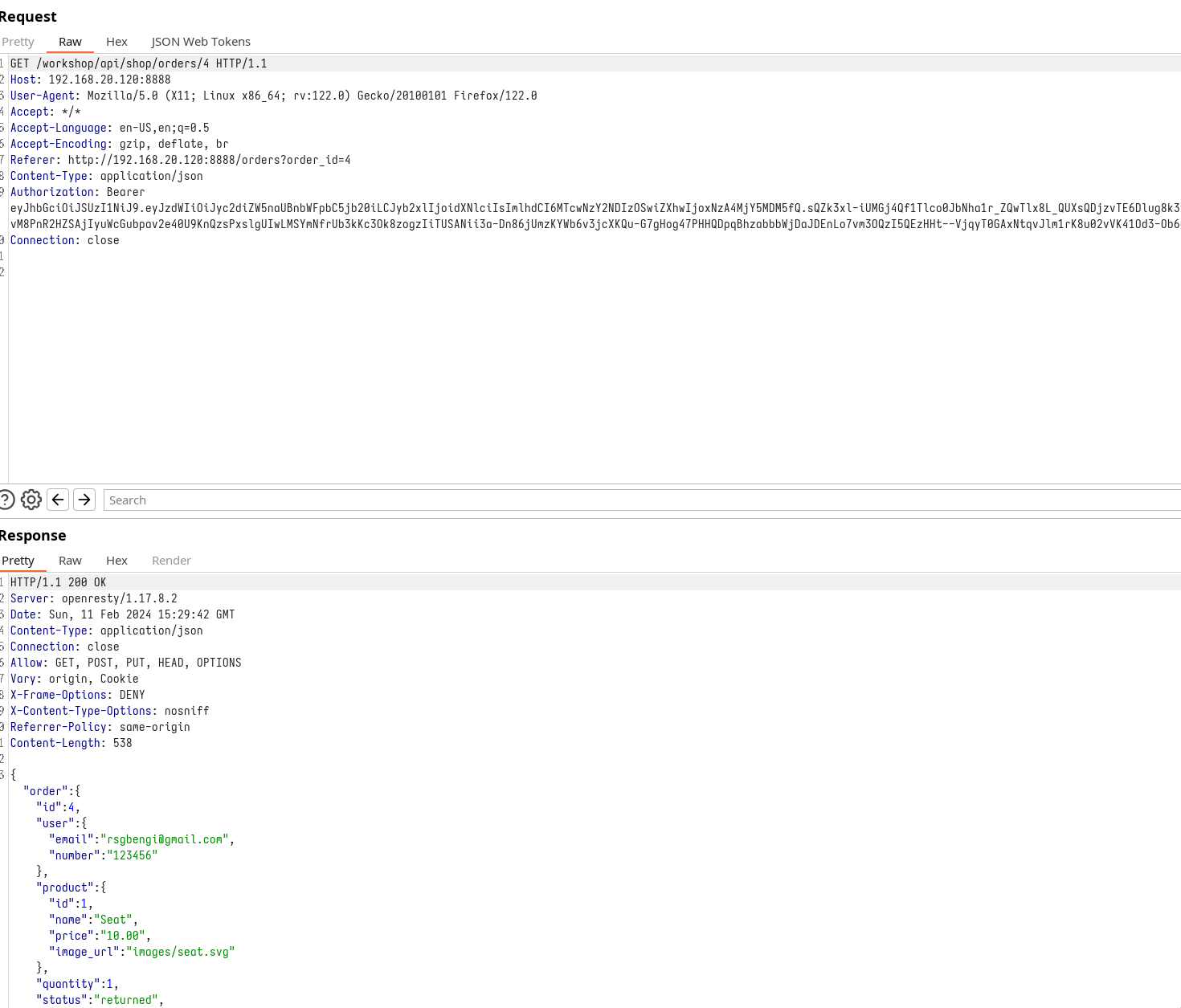
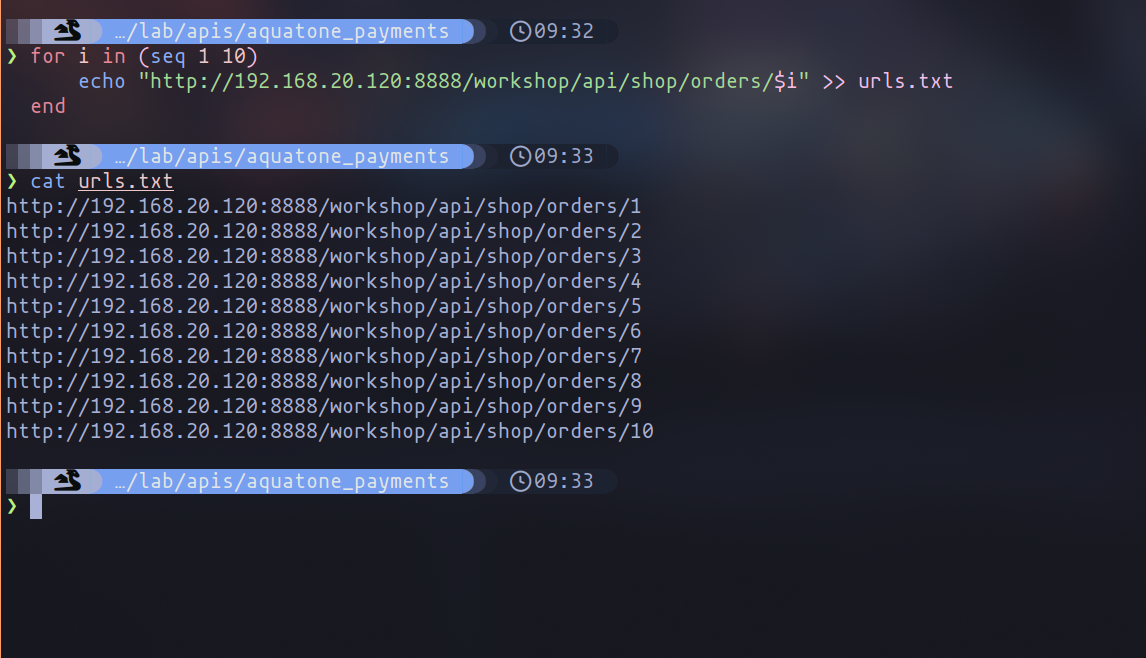
Acknowledging that this request is accessible without providing a JWT, we can endeavor to visualize past purchases of other users. To achieve this, we can utilize a file containing requests that modify the final ID, presuming it corresponds to different purchases made by users. In the following image, you can observe how I have inserted IDs ranging from 1 to 10 using the Fish shell.
for i in (seq 1 10)
echo "http://192.168.20.120:8888/workshop/api/shop/orders/$i" >> urls.txt
end
As depicted in the following image, in the second row, we observe the diverse responses from the API, enabling us to inspect past orders of other users, thereby demonstrating the vulnerability:
Excessive Information Exposure: Beyond the Surface of API Responses
Following our exploration of "Unauthenticated Access," a vulnerability that allows attackers to gain access to system functions or data without proper authentication, we delve into another critical but often overlooked risk: "Excessive Information Exposure."
"Excessive Information Exposure" occurs when an application inadvertently discloses more information than necessary, typically through its API responses. This can range from personal data to system details that could pave the way for further exploitation. Unlike Unauthenticated Access, which directly permits unauthorized entry into systems, Excessive Information Exposure is a subtler vulnerability resulting from a design oversight. This oversight leads to the unnecessary sharing of data, such as detailed error messages, API keys, and user information, that should be restricted or obfuscated.
The bridge between Unauthenticated Access and Excessive Information Exposure is of particular concern. While the former opens the door to unauthorized system interactions, the latter can provide the critical information needed to exploit those interactions more effectively. Together, they create a compounded security risk where the attacker, equipped with excess information, can navigate and manipulate the system with greater precision, potentially leading to identity theft, unauthorized access, and system compromise.
Mitigating these vulnerabilities requires a multifaceted approach. Starting with the principle of least privilege, especially in data sharing and system access, it's essential to implement rigorous data filtering, proper access controls, and continuous monitoring and auditing of both access patterns and data exposure.
Case Study: The Perils of Excessive Information Exposure
We've made considerable progress auditing nearly every part of our application. Yet, there's one segment we haven't thoroughly examined—the application's forum. Upon closer inspection, it becomes apparent that the forum hosts comments from three default users.
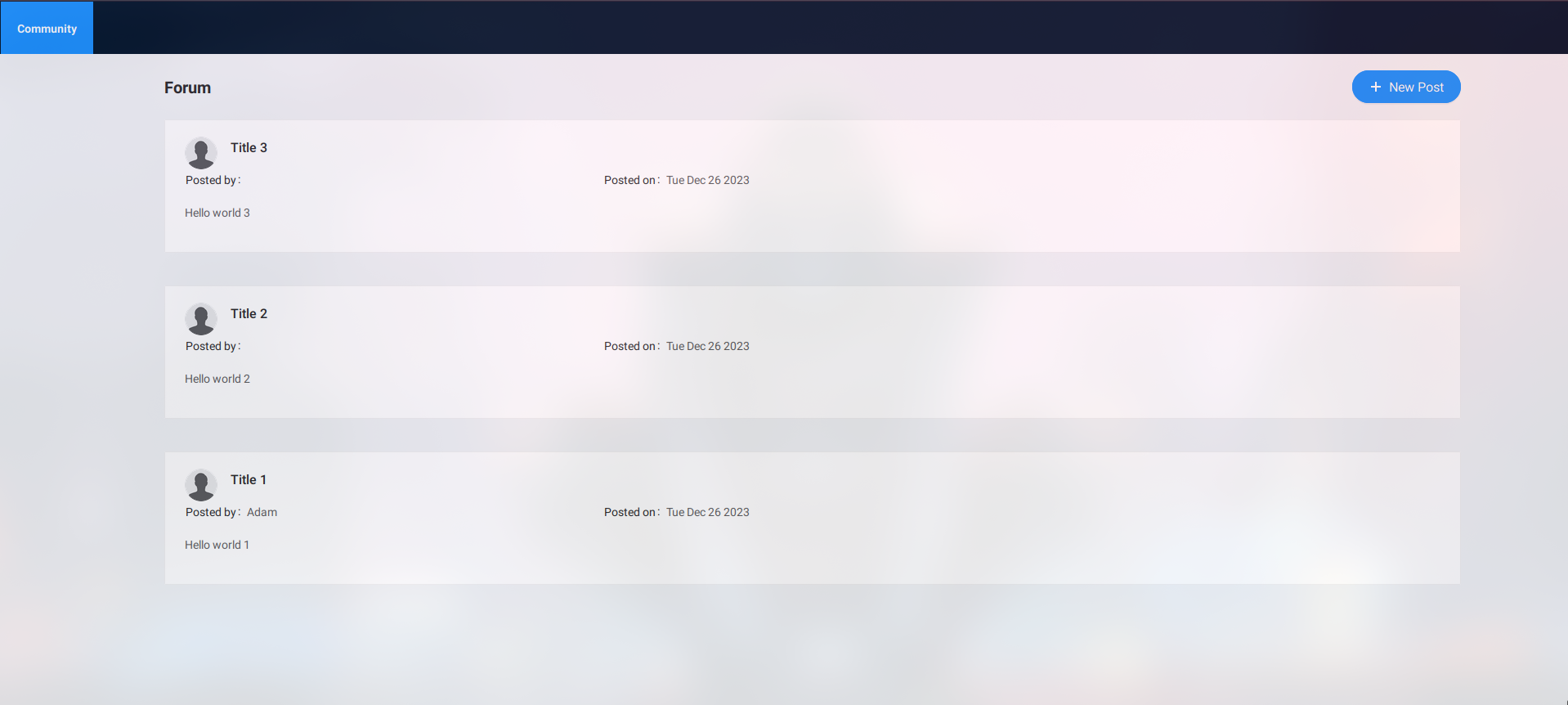
Delving into these comments offers an opportunity to test various inputs by replying to existing comments or creating new ones. Despite experimenting with numerous payloads aimed at triggering Cross-Site Scripting (XSS)—a vulnerability we'll explore in an upcoming series on web hacking—none have proven successful.

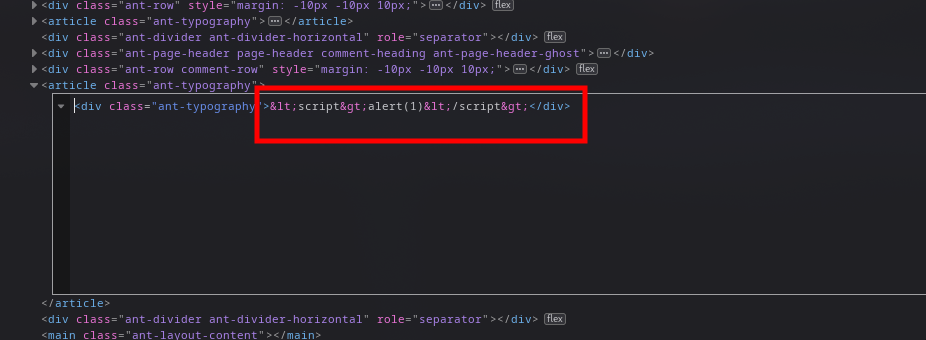
This lack of success indicates that the application effectively sanitizes user input, thwarting attempts at exploiting this potential vulnerability. However, a deeper investigation into the network requests made while interacting with the forum reveals a significant oversight: the exposure of other users' email addresses. Such information, which unnecessarily reveals more data than required for front-end operations, signals an Excessive Information Exposure vulnerability.
At first glance, this might not seem like a critical issue. Yet, when combined with previously identified vulnerabilities, such as flawed user authentication, this oversight could enable attackers to change the passwords of other users arbitrarily, bypassing the need to ascertain their email addresses.
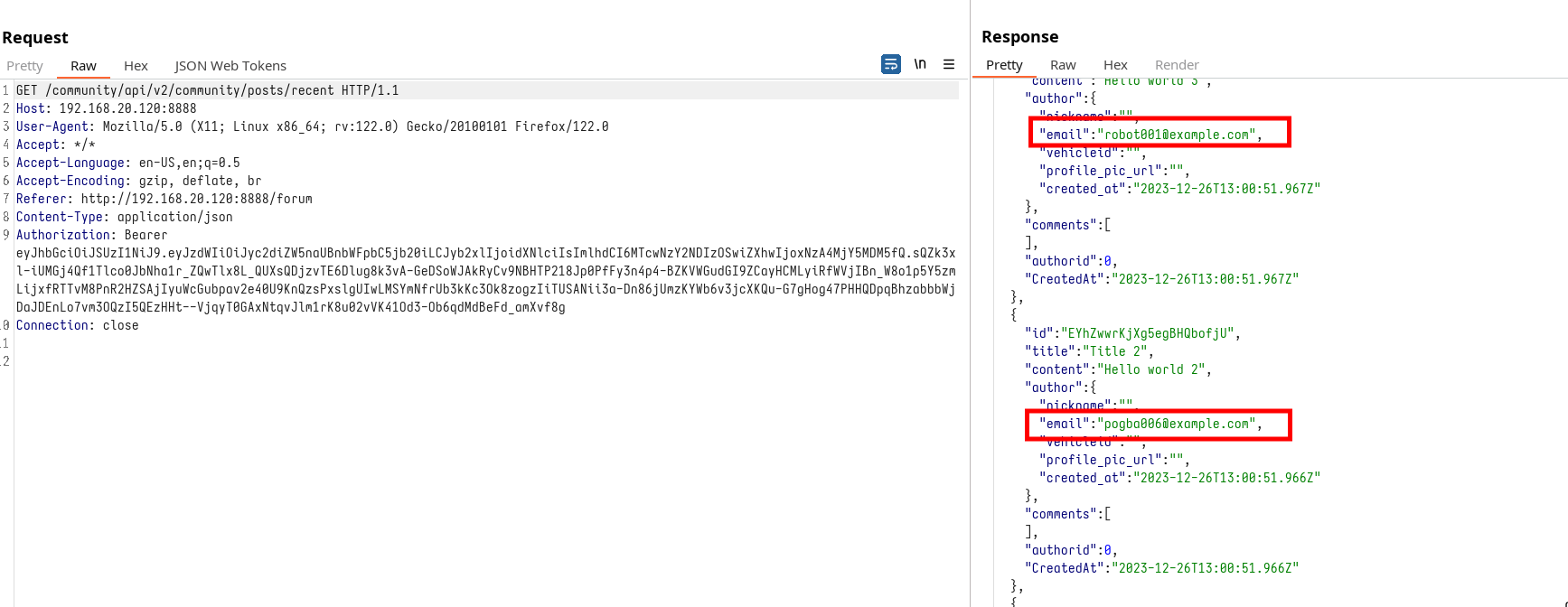
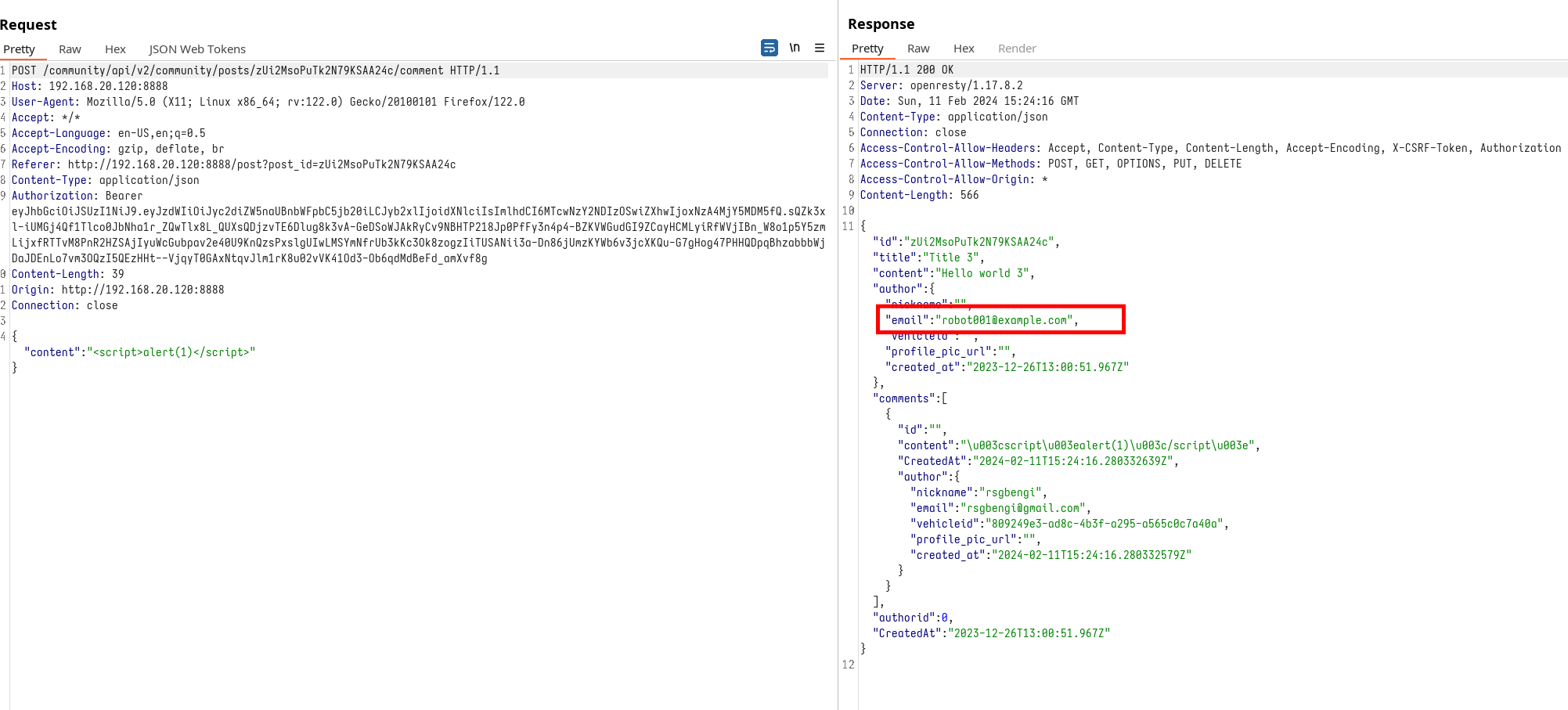
Conclusions
Our in-depth exploration of Unauthenticated API Access and Excessive Information Exposure vulnerabilities throughout this series has unveiled the intricate challenges and potential threats these weaknesses pose to data security and system functionality. The practical scenarios dissected, alongside the deployment of tools like Burp Suite and Aquatone, have shed light on the paramount importance of enforcing stringent security measures and adhering to the principle of least privilege within application ecosystems. These episodes have emphatically highlighted the critical need for robust authentication protocols, effective data filtering processes, and comprehensive access control measures to counteract the risks presented by these vulnerabilities.
Moreover, the adoption of continuous monitoring and auditing strategies stands out as a vital practice for the timely identification and rectification of security vulnerabilities. The interrelated nature of Unauthenticated API Access and Excessive Information Exposure underscores the necessity for a holistic cybersecurity approach. Addressing one area of vulnerability not only strengthens specific defenses but also bolsters the overall security posture against a spectrum of potential threats.
As we draw this chapter to a close, the enduring message is clear: the fight against cyber threats is a perpetual endeavor that requires unwavering diligence, innovative solutions, and a steadfast commitment to safeguarding our digital domains. This journey through the realms of Unauthenticated Access and Excessive Information Exposure serves as a poignant reminder of the ongoing need for comprehensive security strategies. These strategies are crucial in protecting sensitive data and preserving system integrity in an era where digital connectivity is ubiquitous. Let this series be a beacon, guiding us toward more secure and resilient digital infrastructures in our collective quest to navigate the complexities of the digital age.
Chapters

Previous chapter
Next chapter

