Slither: Your First Line of Defense in Smart Contract Security
12 min read
April 6, 2025

Introduction
Welcome back to my Web3 security series! If you’ve stuck around all the way to entry #17, you deserve a virtual high-five — either you’re genuinely fascinated by smart contract auditing, or you’ve invested too many hours to bail now. Either way, I’m glad you’re here!
By this point, you’ve probably encountered more require() statements than actual humans this week. Your dreams might feature reentrancy attacks, your lunch breaks are spent pondering frontrunning vulnerabilities, and you may have caught yourself whispering “msg.sender” in quiet moments. Don’t worry—we’re all a little weird here in security-land.
Today, I’m excited to introduce you to a tool that’s saved my sanity countless times: Slither. No, it’s not a reptile (though it does sniff out dangerous code-creatures with impressive accuracy). Developed by the brilliant minds at Trail of Bits, Slither is essentially a security scanner with superpowers—open source, extensively tested, and considerably less sweaty than actual steroids.
In this post, I’ll walk you through:
- What makes Slither tick under the hood (explained in human language, I promise)
- Why virtually every security professional I know keeps it in their toolbox
- How you can start using it today to catch bugs before they catch you
We’ll even roll up our sleeves with a practical example—because while theory is nice, watching Slither flag a potential exploit in real-time is downright satisfying.
So grab your favorite caffeinated beverage, make sure your terminal is ready, and let’s get slithering into the world of automated smart contract analysis! 🐍
What is Slither?
For those of us in the security trenches, hunting vulnerabilities across smart contracts day after day, Slither is essentially our reconnaissance tool of choice.
At its core, Slither is a static analysis framework that gives penetration testers and security auditors an immediate advantage when approaching a new smart contract codebase. Unlike many tools that simply generate noise, Slither provides actionable intelligence about the attack surface you’re dealing with.
When I’m approaching a new audit engagement with limited time (and let’s be honest, when aren’t we on a tight deadline?), Slither gives me that critical first look at what I’m dealing with. It’s like having satellite imagery before entering unfamiliar territory.
What makes Slither indispensable for security professionals:
- It maps the attack surface by identifying externally accessible functions, public state variables, and potential entry points for exploitation
- It flags high-value targets like privileged functions, self-destruct mechanisms, and direct ETH transfers that warrant immediate attention
- It traces execution paths through complex contract interactions, helping spot vulnerable flows that might otherwise take days to identify manually
- It detects common vulnerability patterns that experienced attackers will immediately target in production
I’ve lost count of how many times Slither has revealed critical vulnerability paths that weren’t immediately apparent from manual code review. Those subtle cross-contract interactions or state modifications after external calls that represent perfect exploitation opportunities? Slither excels at bringing these to light.
What particularly separates Slither from other security tools is its remarkably low false-positive rate. When Slither flags something as potentially dangerous, it’s almost always worth investigating. This precision is invaluable when you’re operating under audit time constraints and need to prioritize your efforts effectively.
Even for seasoned security professionals, Slither serves as an excellent starting point to orient yourself within complex systems. Rather than spending hours manually tracing inheritance hierarchies or mapping dependency structures, Slither gives you that information upfront, allowing you to focus your expertise on finding the non-obvious vulnerabilities that automated tools might miss.
In my pentesting toolkit, Slither is typically the first weapon I deploy – it helps me understand what I’m up against before I start crafting more targeted exploits.
How Does Slither Work?
Understanding how Slither analyzes smart contracts gives us a strategic advantage. Rather than just accepting its findings blindly, knowing its inner workings helps us leverage the tool more effectively and understand where to dig deeper.
At a high level, Slither operates like an advanced reconnaissance system for smart contract battlefields. Let me walk you through what’s happening under the hood when you point it at a codebase.
Phase 1: Building Intelligence Through Parsing
First, Slither uses the Solidity compiler frontend to generate an Abstract Syntax Tree (AST) of the target contract. This is essentially a structured representation of the code that makes it possible to analyze programmatically.
This initial parsing phase is critical because it extracts key tactical information:
- The complete inheritance hierarchy - crucial for understanding privilege escalation vectors
- Control flow graphs for every function - revealing all possible execution paths an attacker might follow
- Variable scopes and definitions - identifying potential storage collision attacks
What makes this parsing phase powerful is that Slither doesn’t just capture individual contract elements in isolation - it builds a comprehensive map of how everything interconnects.
Phase 2: Transforming into SlithIR for Deeper Analysis
The most powerful aspect of Slither comes next: it converts the parsed code into SlithIR, an intermediate representation specifically designed for security analysis.
This transformation is where Slither really differentiates itself from basic linting tools. SlithIR uses Static Single Assignment (SSA) form - a representation where each variable is defined exactly once. This is invaluable because it allows precise tracking of:
- Data flow paths - showing exactly how user input can propagate to sensitive operations
- State modifications - revealing where contract storage gets altered
- Cross-function dependencies - exposing how one vulnerable function might compromise others
The SSA form makes it significantly easier to detect subtle vulnerability patterns like reentrancy, where the sequence of state updates and external calls becomes critical.
Phase 3: Executing Specialized Detectors
Armed with this highly structured representation, Slither unleashes its arsenal of specialized vulnerability detectors - each designed to identify specific attack vectors:
- Taint analysis systematically traces user-controlled input through the application flow, flagging when it reaches sensitive operations like
selfdestructordelegatecall - Storage access pattern analysis identifies dangerous sequences like “read, external call, write” that often indicate reentrancy vulnerabilities
- Authorization analysis maps which addresses or roles can access which functions, exposing privilege issues
These detectors use graph-based algorithms to identify vulnerability patterns across the entire codebase, not just within individual functions or contracts.
Installation and First Steps
Setting up Slither properly is your first engagement in the smart contract security battlefield. As a penetration tester, you need reliable tools that integrate seamlessly into your workflow without becoming a distraction. Here’s how to get your Slither environment battle-ready.
The Arsenal: Prerequisites
Before deploying Slither, ensure your penetration testing environment has these essentials:
- Python 3.6+ - The runtime environment that powers Slither
- pip3 - Your package acquisition system
- Solidity compiler - Ideally with multiple versions available for testing against different compiler targets
For serious contract pentesting, I strongly recommend having multiple Solidity compiler versions accessible. Different projects compile with different versions, and compiler-specific bugs can sometimes be part of your attack vector. Check your current solc setup with:
solc --version
If you need to manage multiple compiler versions (and trust me, you will), install solc-select:
pip3 install solc-select
This gives you the ability to switch compiler versions on demand:
solc-select install 0.8.17
solc-select use 0.8.17
Deploying Slither
Now for Slither itself. Installation is straightforward, but pay attention to the output for any dependency warnings:
pip3 install slither-analyzer
Verify your deployment with:
slither --version
Pro tip: If you’re using Slither frequently across different client engagements, consider creating a dedicated virtual environment to avoid tool conflicts:
python3 -m venv slither-env
source slither-env/bin/activate
pip3 install slither-analyze
This isolation approach ensures your reconnaissance tooling remains stable regardless of other Python packages installed on your system.
Analyzing Your First Contract
Let’s analyze the contract we developed in entry #16 of this series, where we explored gas-related issues in Web3. You can run Slither on it with a simple command like:
slither src/contract.sol
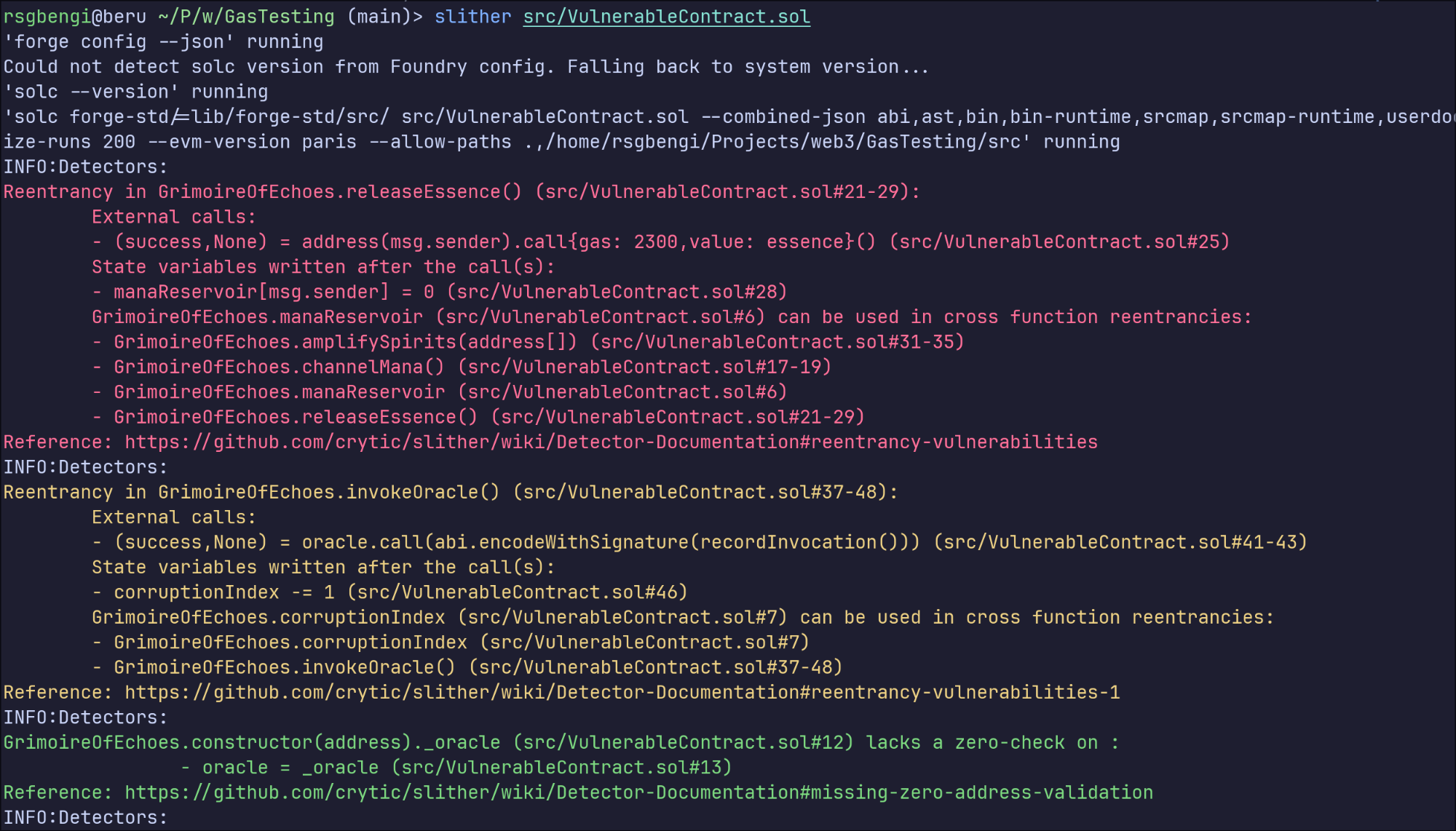
Running Slither for the first time
Once executed, Slither will output a detailed report directly in your terminal. For instance, running it on our gas-focused contract reveals potential reentrancy issues and unsafe external calls:
Here’s what Slither provides out of the box:
- Detected vulnerabilities
Reentrancy, shadowed variables, missing zero-address checks, and more. - Contract structure and inheritance
Including function relationships, modifier usage, and visibility. - Storage access patterns
For example, state variables modified after external calls — a common source of bugs. - Gas optimization tips
Such as identifying variables that could be marked asconstantorimmutable.
Even on a relatively simple contract, Slither surfaces a surprising amount of insight. The more complex the logic, the more valuable its output becomes — especially when used early in development or during security reviews.
Practice Example
Let’s examine a practical application of Slither against our target contract from last week. While Slither offers numerous advanced options, I’ll demonstrate the reconnaissance approaches that consistently deliver the highest value intelligence during my own contract penetration tests.
First, I’ll deploy Slither for an initial vulnerability scan:
slither .
This baseline scan reveals potential exploitation paths ranked by severity – from critical issues that warrant immediate attention to informational findings that might contribute to chained attacks.
Beyond this standard reconnaissance, I leverage two specialized intelligence-gathering commands:
slither . --print contract-summary
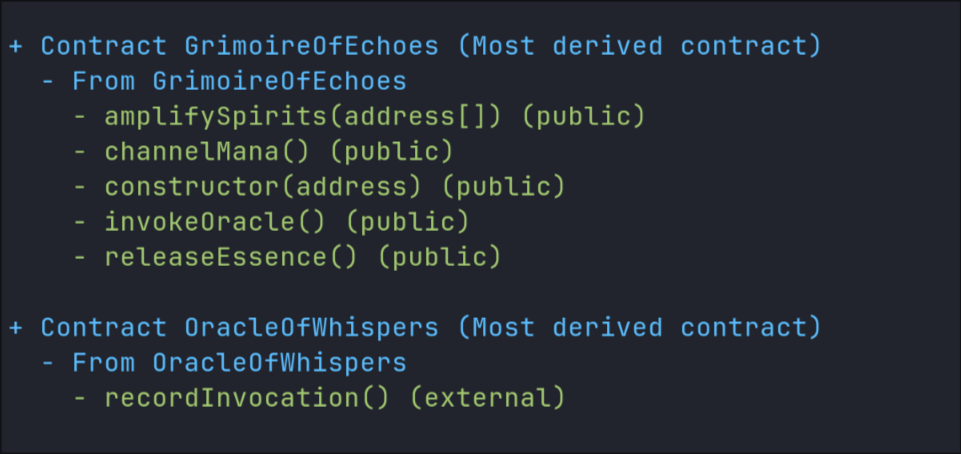
Basic recon
This generates a rapid overview of the target’s capabilities and structure – similar to mapping a facility’s floor plan before launching a physical penetration test.
Next, I map the permission structure to identify access control weaknesses:
slither . --print vars-and-auth
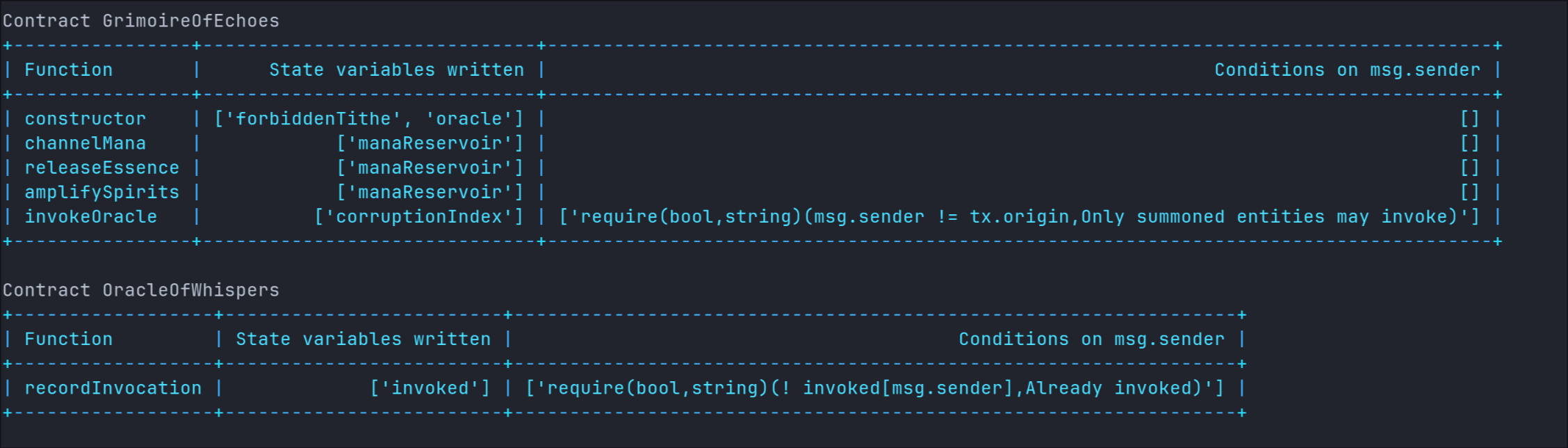
Auth recon
This shows me the permission structure - which functions can modify which variables, and who has access to what.
While command line tools are powerful, most of us work in code editors day-to-day. If you’re using Visual Studio Code like me, there are two extensions that will absolutely transform your auditing experience:
- Solidity Visual Developer
- Slither
Once you’ve installed these, open your project and click the “play” button in the Slither extension panel. After a few seconds, you’ll see all potential vulnerabilities displayed in a much more digestible format than the command line output.
What’s really cool is that you can click on any finding and VS Code will instantly jump to the exact line of code where Slither detected an issue. No more hunting through files!
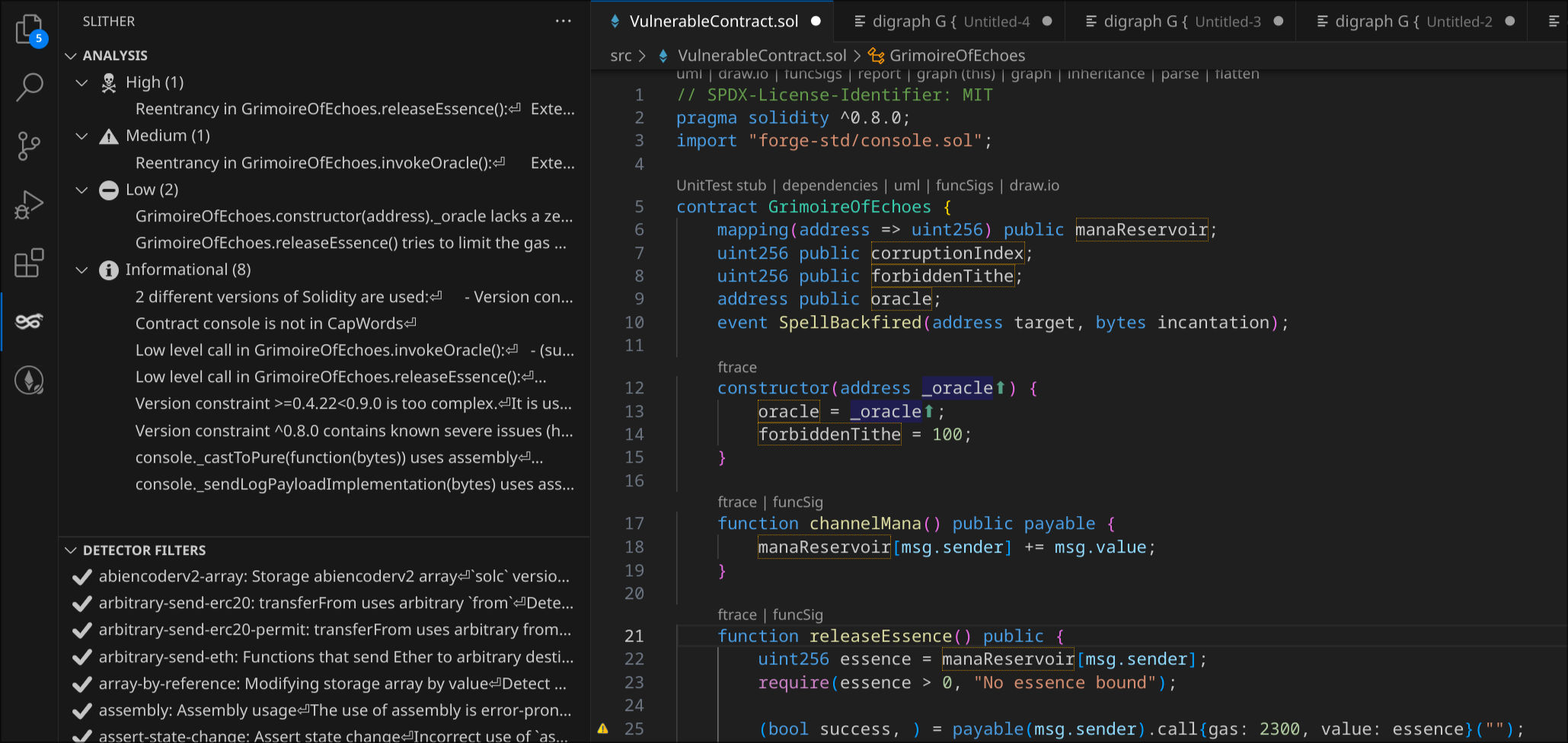
Slither in vscode
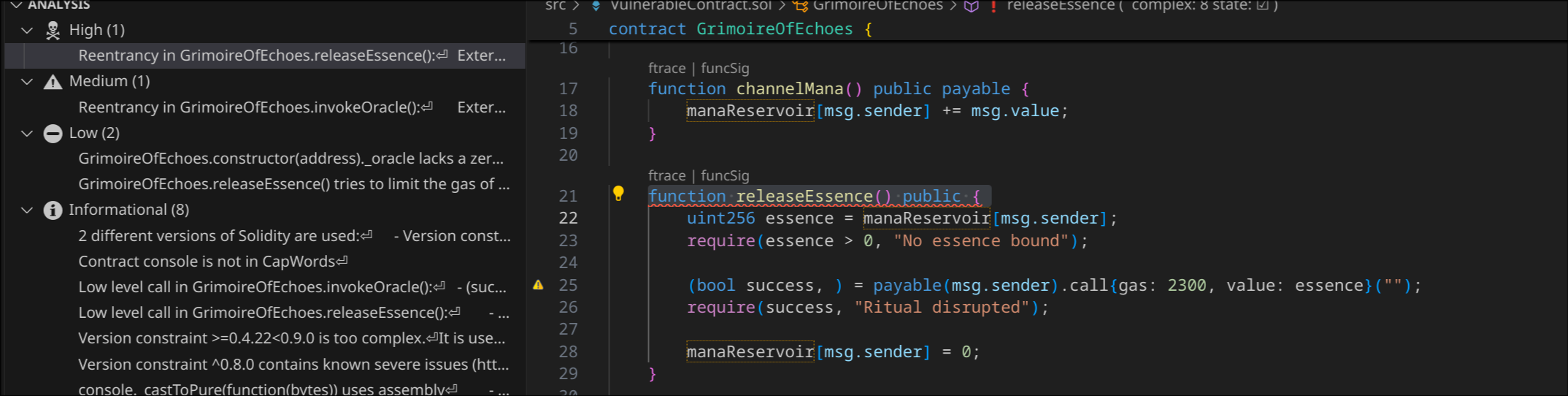
Jumping to the function
The Solidity Visual Developer extension lets you create audit annotations right in your code using the @audit keyword. For example:
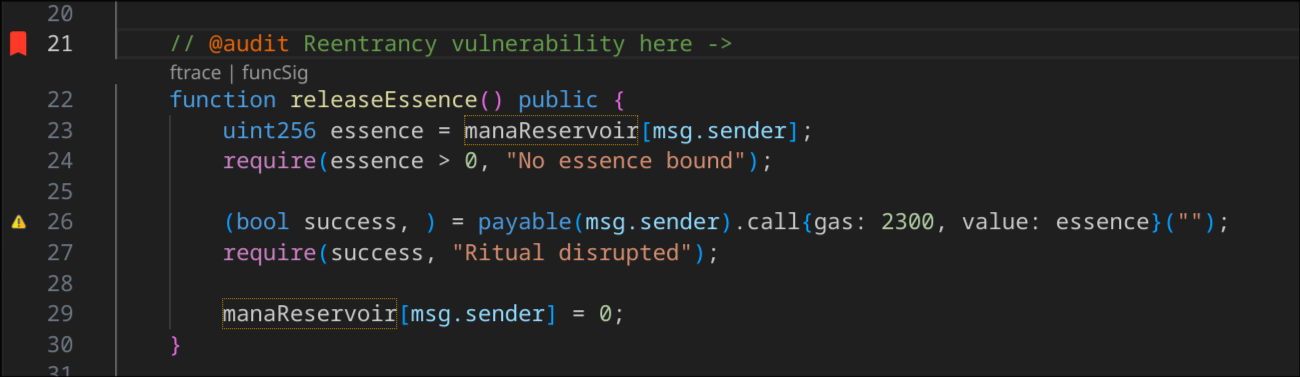
Using notation
This makes it incredibly easy to collect all your findings when it’s time to write up that final report, especially when you’re reviewing thousands of lines of code across multiple contracts.
One of my favorite features is the ability to generate interactive graphs that visualize contract structures and relationships. While our example is just a small contract, this becomes invaluable when dealing with complex systems.
You can see function call graphs, inheritance patterns, and storage access paths - all as interactive diagrams you can click through. It’s like having a map of the codebase that shows not just what exists, but how everything connects.
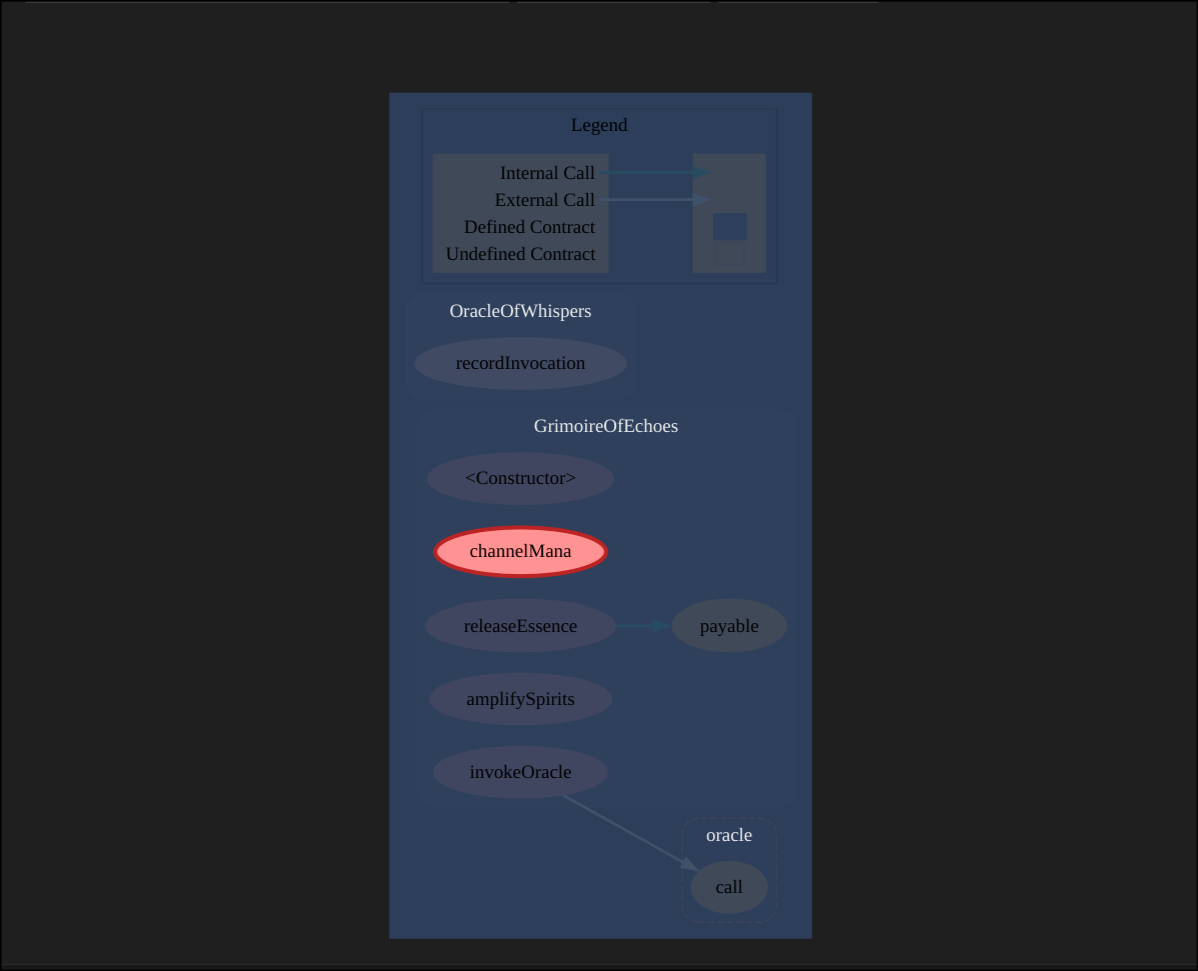
Graph representation
The extension offers several different visualization options, from straightforward inheritance trees to complex call graphs that show exactly how data flows through the system.
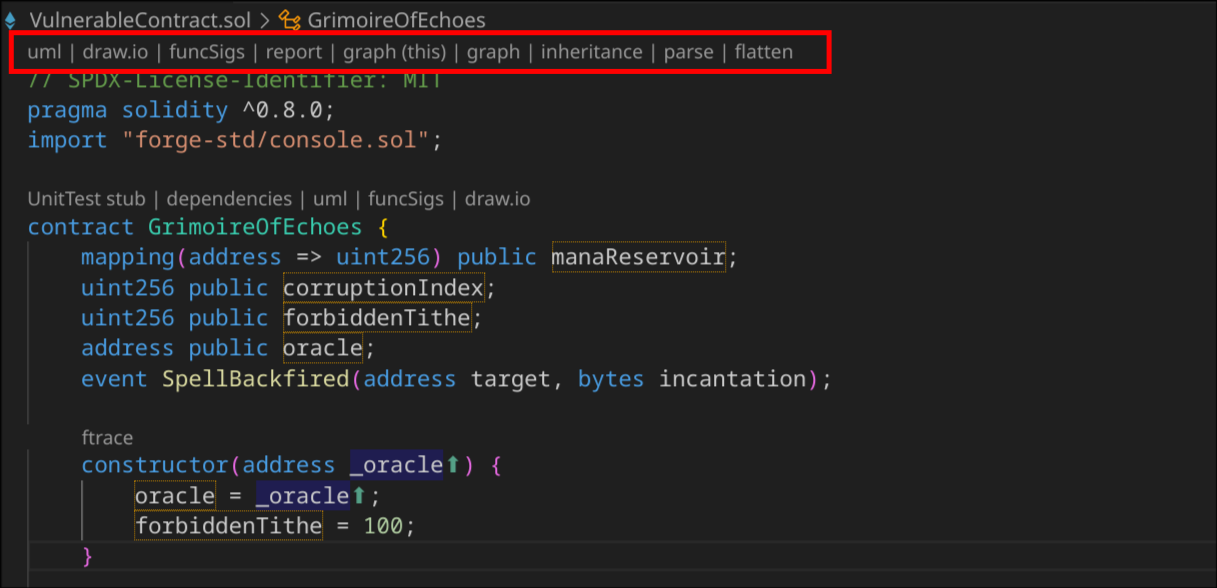
Different ways to represent information
Conclusions: Slithering Towards Web3 Security
And that’s where we’ll wrap up our introduction to Slither! As you can see, having a snake in your security toolkit isn’t always a bad idea (unless you’re in a Samuel L. Jackson movie, of course).
We’ve seen how Slither can become your best ally in detecting vulnerabilities before hackers find them and decide your smart contract is the ATM of the month. From static analysis to visualizations that would make a graphic designer weep, this tool has everything you need to sleep a little more soundly at night.
I’m leaving the article here because, honestly, it was getting a bit long (and I don’t want you needing extra coffee to finish reading it). Plus, my keyboard was starting to smoke and I don’t have the budget for a new one this month.
In the next article, we’ll dive into Slither’s API and see how we can program with it to create our own custom detectors. Because, let’s be honest, what’s more fun than writing code to analyze code? It’s like that scene from Inception, but with less Leonardo DiCaprio and more blockchain security.
Until then, keep your contracts clean and your variables initialized. Web3 security will thank you, and so will your digital wallet.
References
- Trail of Bits. “Slither Documentation: A Solidity Static Analysis Framework.” Available at: https://github.com/crytic/slither/wiki
- Juan Blanco. “Solidity Visual Developer Extension for VS Code.” Available at: https://marketplace.visualstudio.com/items?itemName=JuanBlanco.solidity
- Trail of Bits. “Slither VS Code Extension.” Available at: https://marketplace.visualstudio.com/items?itemName=trailofbits.slither-vscode
- Feist, J., Grieco, G., & Groce, A. “Slither: A Static Analysis Framework For Smart Contracts.” In 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB), 2019, 8–15. Available at: https://ieeexplore.ieee.org/document/8823898
- Ghaleb, A., & Pattabiraman, K. “How effective are smart contracts analysis tools?” In Proceedings of the 29th ACM SIGSOFT International Symposium on Software Testing and Analysis (ISSTA ’20), 2020, Virtual Event, USA, 11 páginas. Available at: https://doi.org/10.1145/3395363.3397385
Chapters

Previous chapter
Next chapter


💬 Comments Available
Drop your thoughts in the comments below! Found a bug or have feedback? Let me know.