User-Centric Pentesting: Unveiling Secrets with PowerView and PowerSploit
11 min read
March 31, 2023

Introduction: Delving Deeper into Active Directory for Penetration Testing
Welcome to another insightful chapter in our ongoing series focused on mastering penetration testing within Active Directory environments. As we delve deeper into this complex and critical aspect of network security, this chapter is designed to expand your understanding and skills in navigating Active Directory’s multifaceted landscape.
In this installment, we turn our attention to the intricate details that often make the difference between a surface-level understanding and a profound mastery of penetration testing. We will explore the nuances of user properties and secrets, understand the pivotal role of computer accounts, and dissect the strategic importance of groups within Active Directory.
Our journey will not only guide you through the process of identifying and analyzing key user accounts and their encrypted secrets but will also delve into the significant role of groups in privilege management. This chapter aims to provide you with the knowledge and tools necessary to navigate and exploit these systems more effectively, enhancing your capabilities as a cybersecurity professional.
Join me as we continue to unravel the complexities of Active Directory, paving the way for more advanced techniques and strategies in our series. Whether you’re a seasoned expert or just starting in the field, this chapter is set to enrich your understanding and approach to penetration testing in these ubiquitous and vital network environments.
evil-winrm -i 192.168.253.130 -u vaan -p 'Password1' -s powershellscripts/
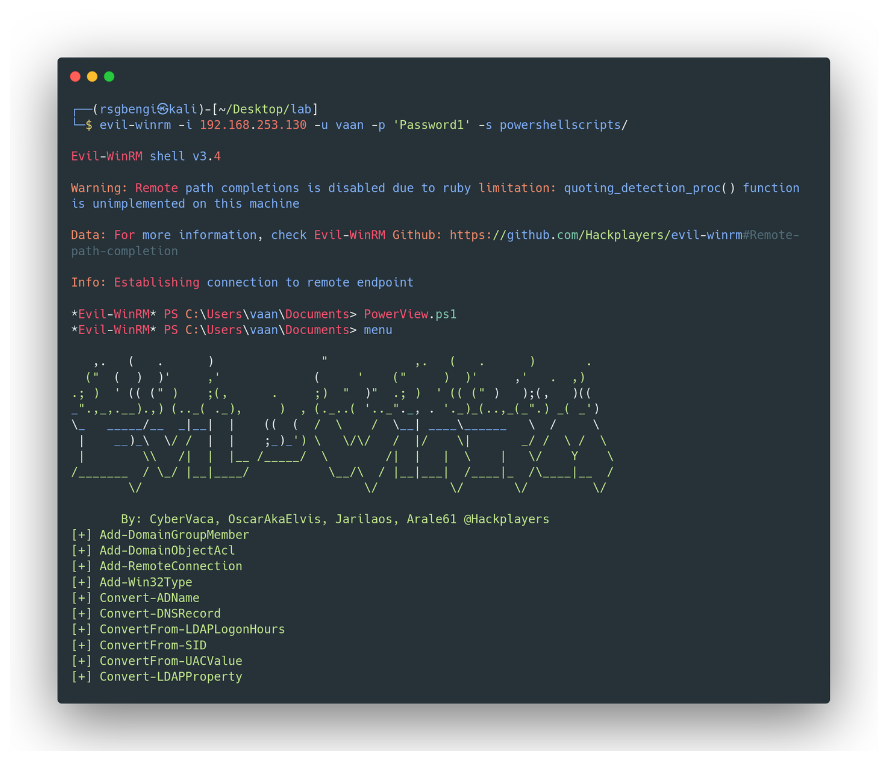
Command execution via evil-winrm
Join me as we dive into this exciting phase, where understanding the user landscape becomes key to mastering penetration testing in Active Directory environments.
Exploring User Properties in Active Directory for Penetration Testing
In the fascinating world of Active Directory penetration testing, knowing your way around user properties is like having a master key. With PowerView, part of the versatile PowerSploit framework, we unlock a treasure trove of information about users in the domain. Let’s dive into how this powerful tool can be your ally in uncovering critical user details.
Getting to Know Users with PowerView
- The Initial Command: The journey begins with
Get-NetUser. This simple yet potent command opens the door to an array of user properties, including the elusive Security Identifier (SID). Remember, the SID is a unique identifier, part domain, part user, and understanding it is like learning a secret language of Windows programs. - The Importance of ‘Distinguished Name’: The “distinguishedname” property is our map to the domain’s NTDS, guiding us through the maze of user queries.
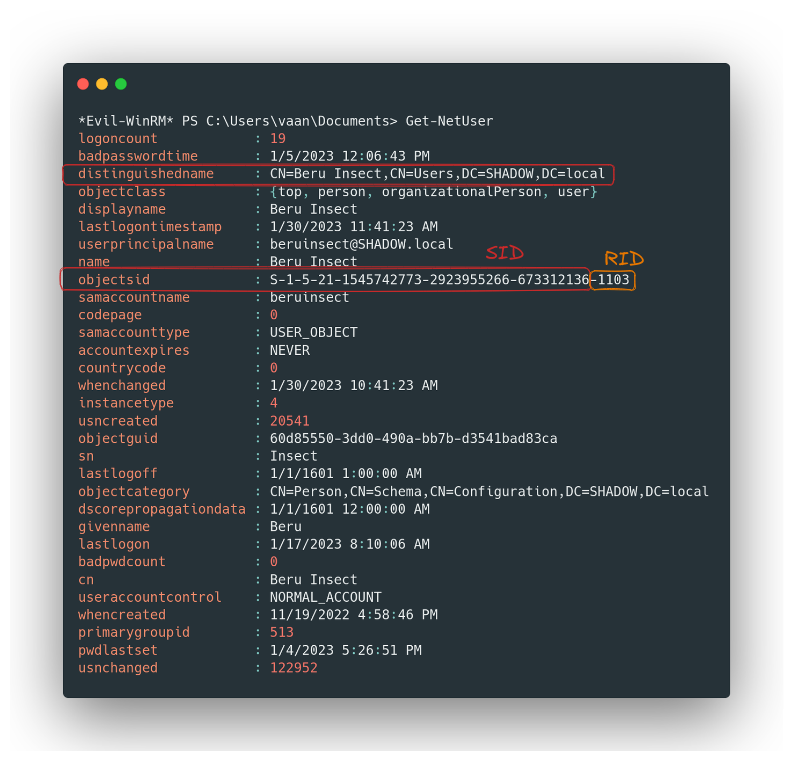
Getting users through powerview
Focusing Your Search
- Zooming In on Users: Need details about a specific user? Just ask PowerView:
Get-NetUser -Username <user>. - The User Roster: For a bird’s-eye view of all domain users, simply run
Get-NetUser | select cn. It’s like having the entire domain’s roll call at your fingertips.
Advanced User Reconnaissance
- Property-Based Filtering: Dive deeper with filters like
Get-NetUser -Properties pwdlastsetto get insights into password settings. - Unearthing Hidden Treasures in Descriptions: Often, user descriptions are gold mines, sometimes hiding passwords in plain sight. A command like
# Get-NetUser -Properties descriptioncan lead you to unexpected discoveries.
Streamlining Searches in Vast Domains
Hunting for Password Clues: In larger domains, where user lists are as vast as the ocean, use a more targeted approach to fish for potential passwords hidden in descriptions:
# Get-NetUser -Properties description
*Evil-WinRM* PS C:\Users\vaan\Documents> Get-NetUser -Properties description
description
-----------
Built-in account for administering the computer/domain
Built-in account for guest access to the computer/domain
Key Distribution Center Service Account
The password is Password1
<details>
<summary>My password is Password3</summary>
</details>
*Evil-WinRM* PS C:\Users\vaan\Documents> Get-NetUser -Properties description,cn | select-string "Pass"
@{cn=Beru Insect; description=The password is Password1}
@{cn=SQL Service; description=My password is Password3}
Bringing It to Life in a Lab
- Practical Application: To see these techniques in action, venture into a domain controller setup under Tools → Active Directory Users and Computers. It’s like setting up your own playground to experiment and see firsthand how these commands perform in a controlled environment.
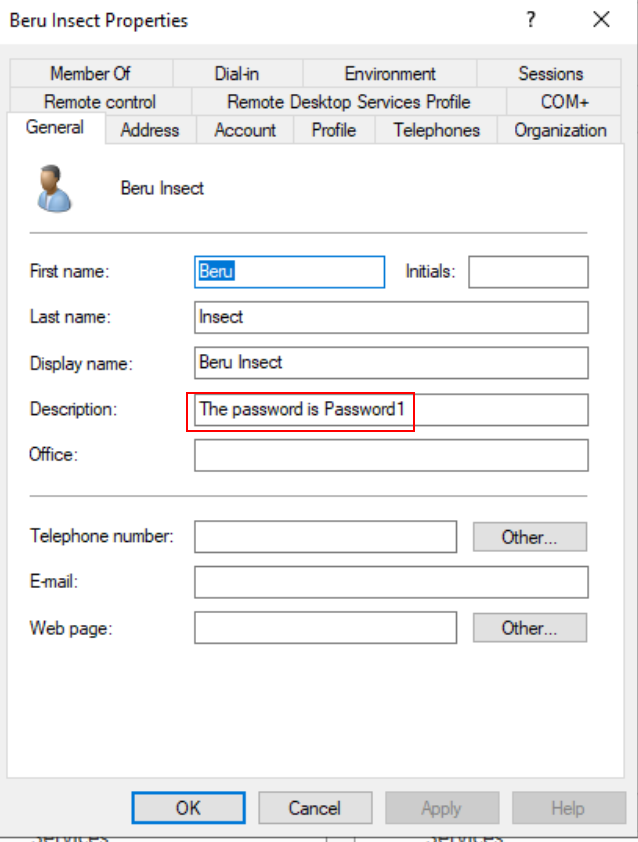
Description of a user
User Secrets: Deciphering the Storage Formats in Windows
In our journey through Active Directory penetration testing, understanding how user secrets are stored on Windows machines is a game-changer. Let’s dive deeper into the formats used for storing these secrets, shifting our focus from retrieval techniques to the actual structure and encryption of these credentials.
The Encryption Landscape: NT/LM Hashes and Kerberos Keys
- Beyond Plain Text: First off, it’s crucial to know that Windows doesn’t store user passwords in plain text. Instead, it encrypts them, primarily using “NT/LM hashes” and “Kerberos keys.”
- NT/LM Hashes Unveiled:
- Location: These hashes are found in the SAM (Security Accounts Manager) for local user credentials, and in the NTDS (NT Directory Services) for domain user credentials.
- NT Hash: This is the modern standard. It’s the encrypted form of the user password predominantly in use.
- LM Hash: An older, less secure format, not actively used since Windows Vista/Server 2008 due to its vulnerability to cracking. However, its presence persists in SAM and NTDS for backward compatibility with older Windows applications.
- Hash Example:
<username>:<rid>:<LM>:<NT>:::
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
LM: aad3b435b51404eeaad3b435b51404ee # Always the same value nowadays
<details>
<summary>NT: 31d6cfe0d16ae931b73c59d7e0c089c0</summary>
- Kerberos Keys:Function: These are derived from user passwords and are vital for authentication via the Kerberos protocol.Encryption Algorithms:AES 256 Key: The go-to for the AES256-CTS-HMAC-SHA1-96 algorithm, commonly used by Kerberos.AES 128 Key: Used with the AES128-CTS-HMAC-SHA1-96 algorithm.DES Key: Linked to the now-deprecated DES-CBC-MD5 algorithm.RC4 Key: Essentially the NT hash, employed by the RC4 HMAC algorithm.
Retrieving and Decrypting Credentials
- Techniques from Previous Chapters: To extract these credentials, we employ the methods discussed in earlier chapters of this series.
- Administrator Privileges: A key point to remember is that recovering these passwords requires administrator-level access.
UserAccountControl
Property of a user that should be taken into account, as it is important from a security point of view. Its flags are as follows:
- ACCOUNT_DISABLE: Account is disabled and cannot be used.
- DONT_REQUIRE_PREAUTH: The account doesn’t require Kerberos pre-authentication.
- NOT_DELEGATED: This account cannot be delegated through Kerberos delegation.
- TRUSTED_FOR_DELEGATION: Kerberos Unconstrained Delegation is enabled for this account and its services.
- TRUSTED_TO_AUTH_FOR_DELEGATION: The Kerberos S4USelf extension is enabled for this account and its services.
Zeroing in on Key Users for Effective Active Directory Penetration Testing
When you’re navigating the intricate maze of a real-world domain, the sheer number of users can be overwhelming. It’s like looking for a needle in a haystack. To help you zero in on the most impactful targets, here are some essential pointers to identify the key players in any domain.
Identifying the Power Players
- Spot the IT Gurus: Keep a sharp eye for users associated with IT. These folks often have the coveted administrative privileges – your golden ticket to broader access and control within the system.
- Target the Domain Overlord: The default domain administrator user is your ultimate target. Imagine having a master key to every door in the domain; that’s what compromising this account feels like.
- Don’t Overlook krbtgt: The krbtgt user account is like the silent guardian of user authentication, wielding the powerful NT and Kerberos keys. Understanding its role is crucial, especially as we delve deeper into Active Directory services in upcoming chapters.
Cutting Through the Clutter with PowerView
- Finding the Admins with Ease: To get straight to the admins, let PowerView be your guide. The
Invoke-EnumerateLocalAdmincommand is your searchlight, illuminating those with administrative powers amidst the sea of users.
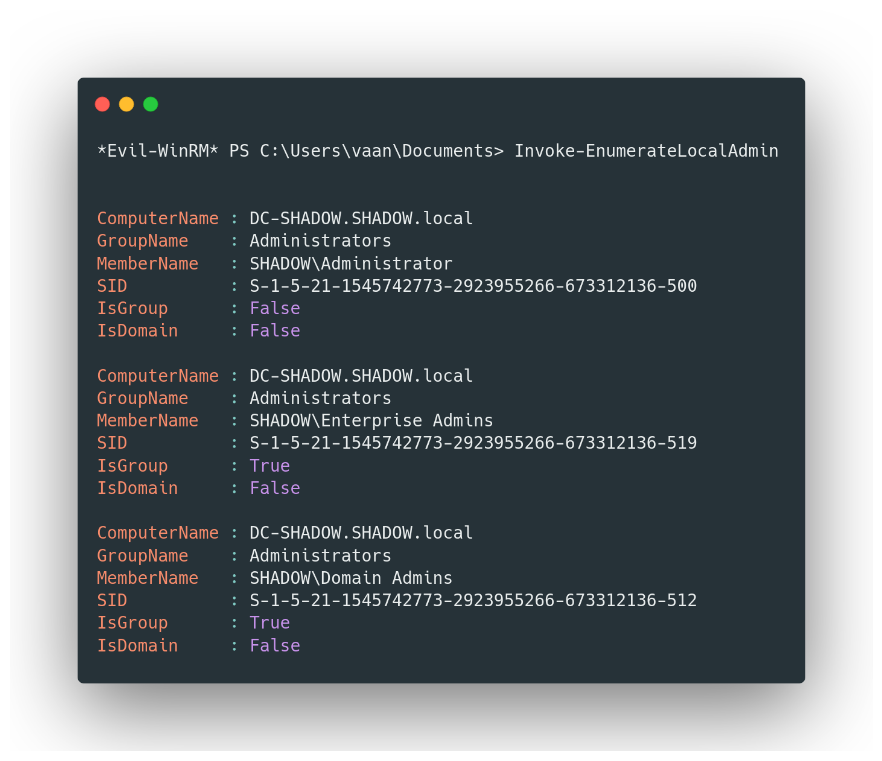
Existing administrators in the machine
Unveiling Computer Accounts in Active Directory
In the dynamic world of Active Directory, not only users but also computers have their unique accounts. These accounts are pivotal, as they play a crucial role in verifying the credentials of domain users attempting to log in. Identifying these computer accounts is quite straightforward – they’re the ones starting with a dollar sign followed by the computer’s hostname.
Exploring Computer Accounts
- Querying the NTDS: Want to take a peek at the different computers in the domain? It’s simple. By querying the domain database (NTDS), you can reveal the myriad of computer accounts that exist. Just use this command:
</details>
Get-ADObject -LDAPFilter "objectClass=User" -Properties SamAccountName | select SamAccountName
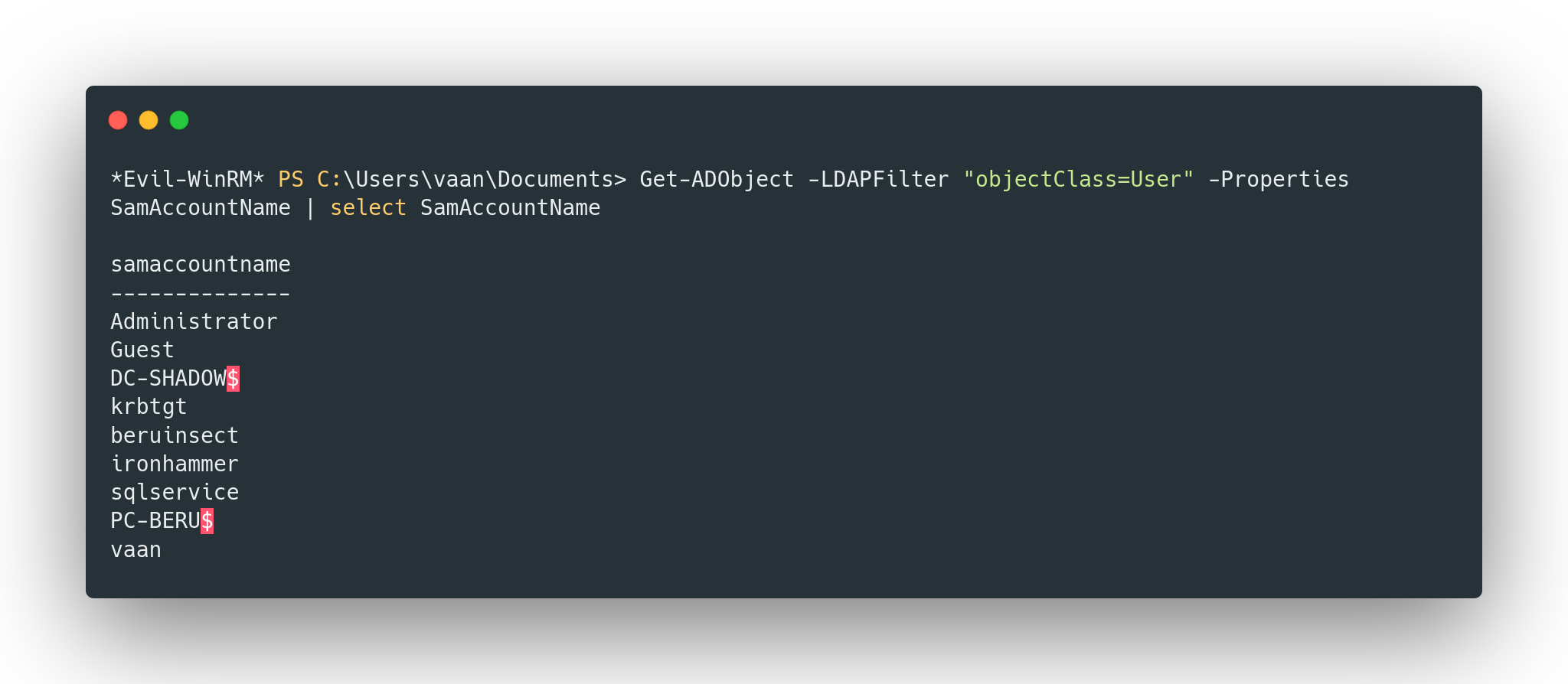
Sample of domain users where those ending with ”$” refer to computers.
PowerView to the Rescue: For a more targeted approach, especially if you’re a fan of PowerView, you can enumerate the computers in the domain with ease. The following command not only does the job but also returns the domain names, making your search even more efficient:
<details>
<summary>Get-NetComputer</summary>
Mastering Groups in Active Directory Penetration Testing
In the intricate ecosystem of Active Directory, ‘Groups’ is a powerful feature by Microsoft that simplifies the management of user privileges. Whether it’s granting or revoking access rights, groups allow administrators to perform these tasks efficiently, impacting multiple users simultaneously. Let’s explore how we can leverage this feature for effective penetration testing.
Harnessing the Power of Groups
- Discovering Domain Groups: To get a list of all the groups in the domain, the command is straightforward:
</details>
Get-ADGroup -Filter * | select SamAccountName
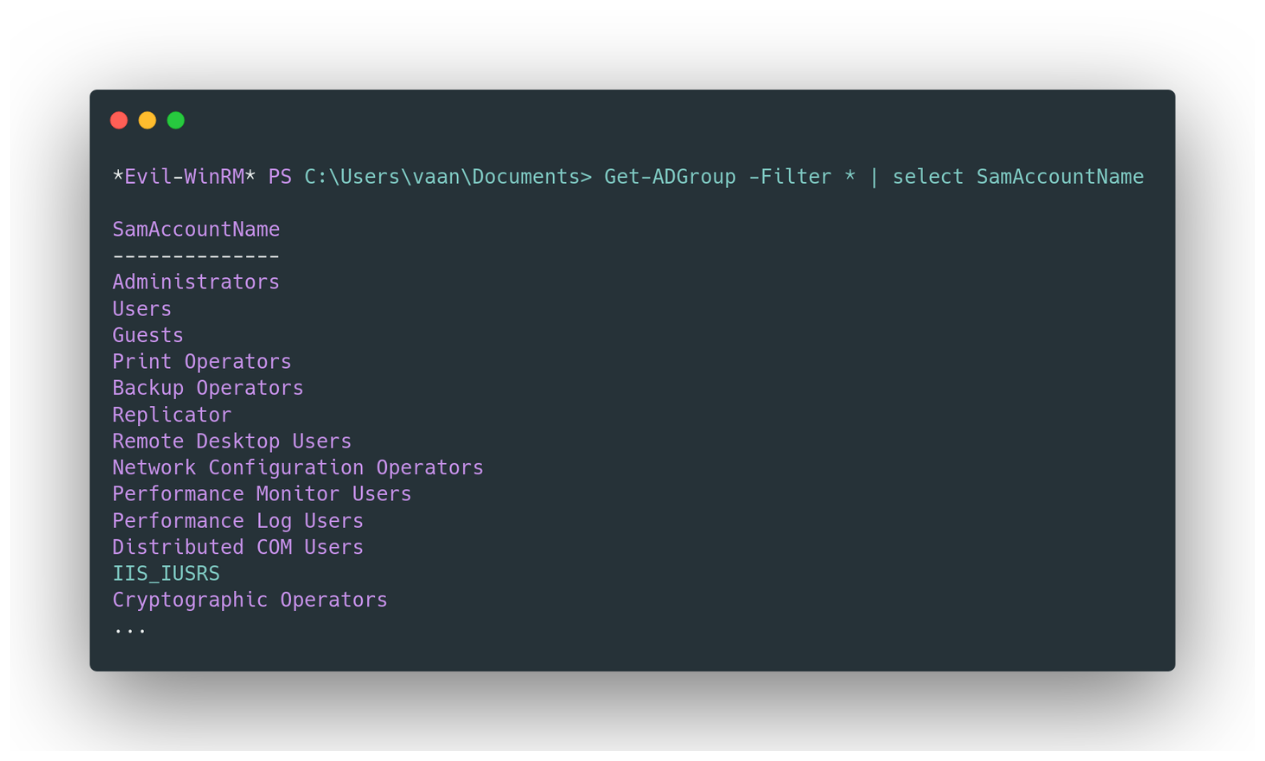
Existing groups in the domain
Using PowerView for Group Enumeration: PowerView offers an intuitive way to list the different groups in the domain:
<details>
<summary>Get-NetGroup </summary>
Focusing on Privileged Groups: To narrow down your search to groups with ‘admin’ in their names, which are often privileged, use:
</details>
Get-NetGroup *admin*
Identifying a User’s Groups: To find out the groups a specific user belongs to:
#Get-NetGroup -UserName <user>
*Evil-WinRM* PS C:\Users\vaan\Documents> Get-NetGroup -UserName vaan -Properties samaccountname
samaccountname
--------------
Denied RODC Password Replication Group
Domain Users
<details>
<summary>Domain Admins</summary>
Listing Users in a Specific Group: And to list all users within a particular group, such as ‘Domain Admins’:
</details>
Get-DomainGroupMember -Identity "Domain Admins" -Recurse
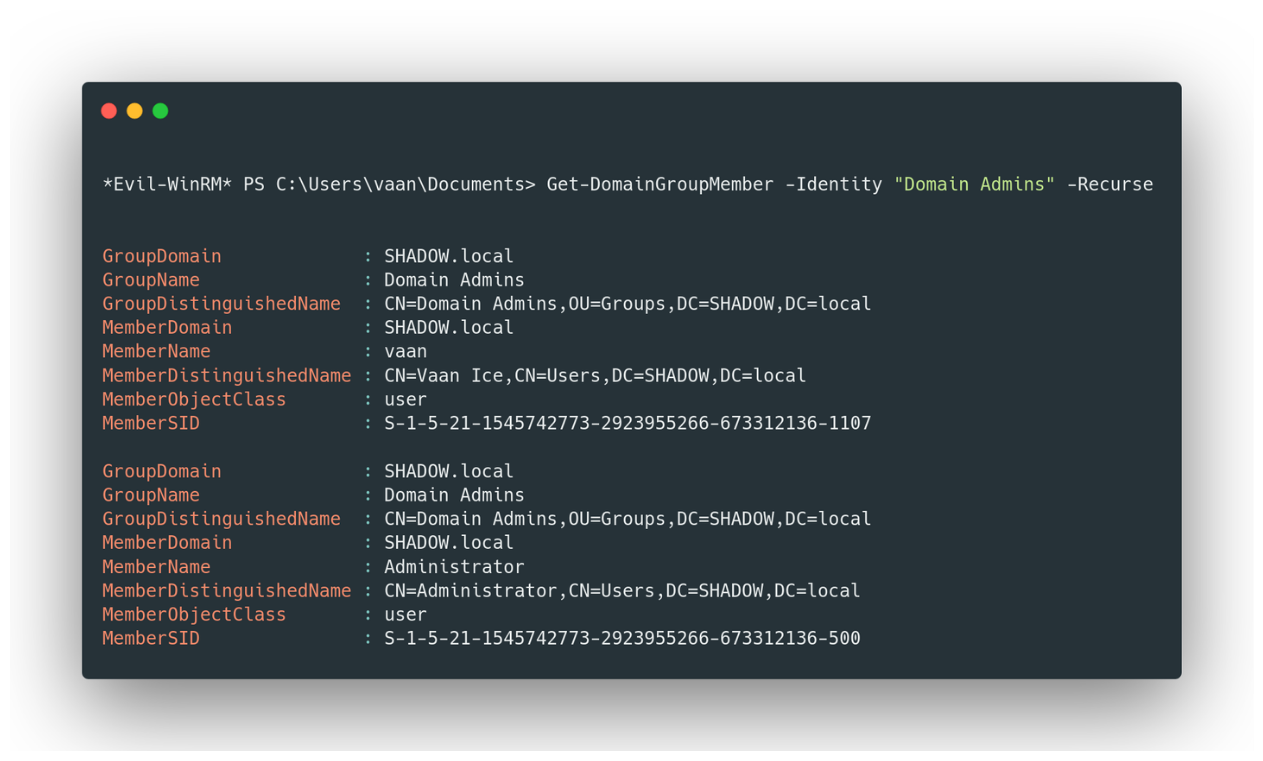
Sample of users belonging to the group “Domain Admins”
Important Groups to Note
Domain Admins, Local Administrators, and Administrators: These groups are particularly significant. Members of the ‘Domain Admins’ group, who are automatically part of the ‘Administrators’ group, have broad privileges across the domain. Compromising any user in this group could mean a total domain takeover. Similarly, the ‘Local Administrators’ group is key for gaining maximum privileges on a specific machine. This is due to Domain Admins being added to local machine administrator groups by default.
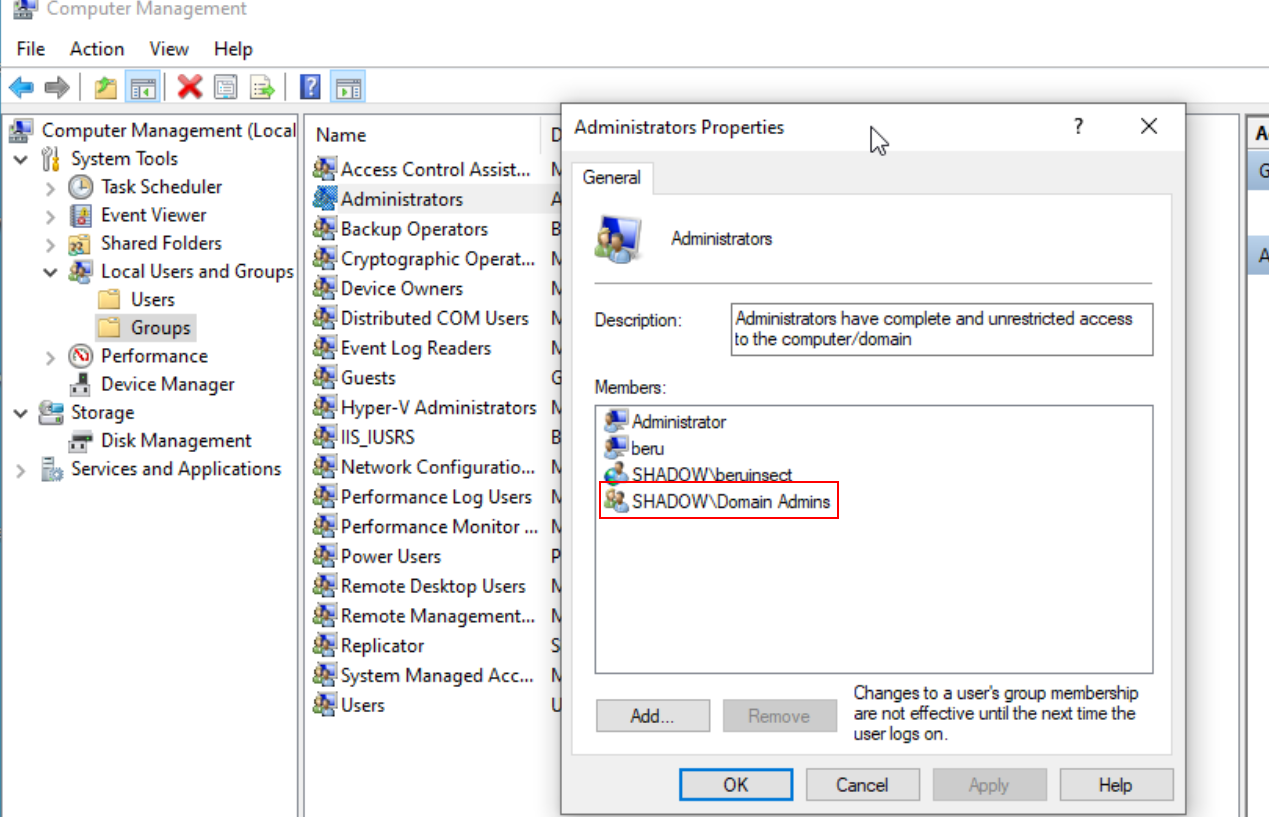
Users of groups belonging to the group of administrators of a computer
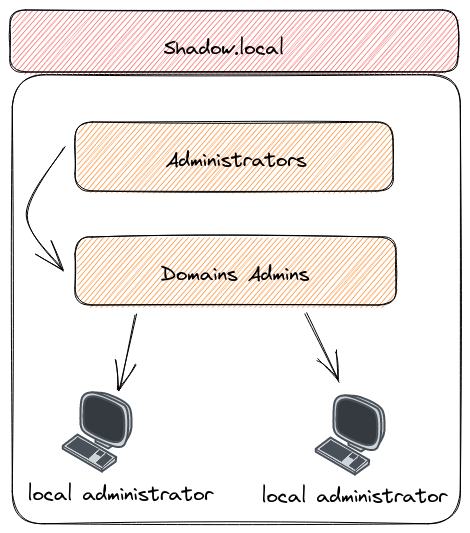
Groups with high privileges
Conclusion: Navigating the Complex Web of Active Directory in Penetration Testing
As we wrap up this chapter, we’ve traversed the intricate landscape of Active Directory, a cornerstone in the realm of network security and penetration testing. From the nuances of user properties and secrets to the strategic management of groups, our journey has equipped us with key insights and tools to navigate and exploit these systems effectively.
We’ve learned how to identify and analyze crucial user accounts, decrypting the secrets behind NT/LM hashes and Kerberos keys. We’ve also explored the significance of computer accounts, revealing their integral role in network security. Our deep dive into groups - the backbone of privilege management in Active Directory - has highlighted the importance of targeting specific user groups for a more efficient penetration testing strategy.
Understanding these elements of Active Directory is vital for anyone in the field of cybersecurity. It empowers us not only to identify vulnerabilities and potential attack vectors but also to think strategically about network security as a whole. As we continue this series, we will build upon this foundation, uncovering more advanced techniques and insights to enhance our skills in penetration testing and cybersecurity.
In the ever-evolving landscape of digital security, knowledge is power. And the insights gained in this chapter are invaluable tools in the arsenal of any cybersecurity professional, offering a guiding light through the complex, often daunting world of Active Directory penetration testing.
Resources
Active Directory Enumeration: PowerView - Hacking Articles
Chapters

Previous chapter
Next chapter


💬 Comments Available
Drop your thoughts in the comments below! Found a bug or have feedback? Let me know.