Web Application Hacking Fundamentals: Starting the Journey
9 min read
February 21, 2024

Introduction to the series
Welcome to the new series I’m embarking on, focused on hacking web applications. These applications are a common sight in penetration testing, especially for those just starting their journey in the field. From my experience, I’ve noticed a common challenge among newcomers: the overwhelming feeling of navigating through the methodology required for a web audit. There’s often confusion about whether they’re covering too much ground or if they’ve thoroughly completed their task, leading to a tangled process. This series aims to demystify the process for beginners, providing a clear path forward.
Moreover, we’re diving into how to audit web applications without the need for Burp Pro or any paid tools. We’ll leverage open-source tools, making this series a haven for those who prefer working directly from the terminal. That’s right, all you’ll need is a terminal and a browser to follow along.
However, it’s important to note that this series won’t cover every vulnerability out there. Instead, our focus will be on how to identify vulnerabilities and automate their detection. For those eager to delve deeper into specific techniques or vulnerabilities, I highly recommend Burp’s academy as a resource. It offers comprehensive coverage and dedicated labs for a wide range of vulnerabilities. Here is the link to Burp’s academy for further exploration:
Web Security Academy: Free Online Training from PortSwigger
This approach is designed to make web application auditing accessible and engaging, whether you’re just starting out or looking to refine your skills with open-source tools. Let’s embark on this journey together, armed with nothing but our terminals and a thirst for knowledge.
Level you will need
For this enlightening journey through web application hacking, there are three essential skills you’ll need to embark effectively:
- Proficiency with the Terminal and Linux Tools: The backbone of this series is the terminal. Every test and task we undertake will be executed within this environment, utilizing an array of Linux commands. A solid grasp of these commands and the ability to navigate the terminal environment with ease are imperative. For those who might feel less confident or are newcomers to the Linux world, don’t worry. In the resources section, I’ll provide a link to a complimentary course designed to get you up to speed.
- Basic Understanding of Web Vulnerabilities: While the series aims to guide you through identifying and exploiting vulnerabilities, a foundational knowledge of what these vulnerabilities are is crucial. We won’t delve into the minutiae of each vulnerability; instead, our focus will be on detection and exploitation techniques. Therefore, having some prior knowledge or experience in this area will be incredibly beneficial as we progress.
- Basic Programming Skills, Especially in Python: Automation and scripting will be key components of our hacking endeavors. Python, with its vast ecosystem and readability, will be our primary tool for extending the capabilities of other tools we’ll be using. Additionally, familiarity with Bash or similar scripting languages is necessary, as they will also play a significant role in our processes. A basic level of programming proficiency will enable you to follow along and engage fully with the series.
These prerequisites are designed to ensure that you can follow the series effectively and make the most out of the techniques and strategies we’ll explore. Remember, the resources section is there to support your learning journey, providing links and materials to bolster your skills where needed. Let’s gear up for an engaging and educational adventure into the world of web application hacking, leveraging the power of open-source tools and the command line.
Basic Tools diagrams
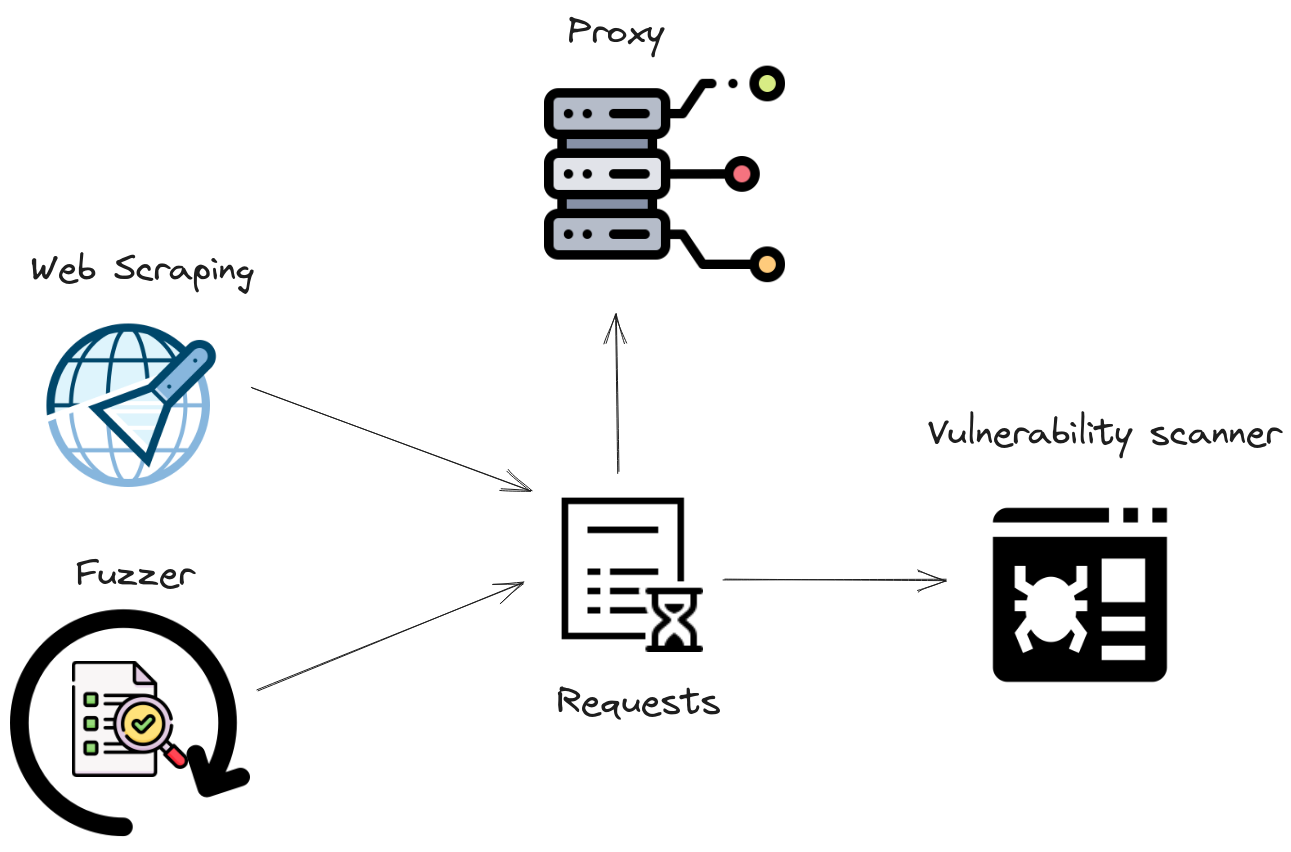
Kicking off my series on hacking web applications, let’s dive into the essential toolkit for conducting a comprehensive web penetration test. Instead of categorizing tools, I’ll focus on the specific activities and the types of tools needed for each. These activities are central to the pentesting process, and the tools I’ve selected are pivotal for executing these main activities in web application penetration testing:
- Information Gathering and Web Scraping: The first step in any web application penetration test is gathering as much information as possible about the target. Tools that automate the collection of URLs, endpoints, and other relevant data from the web application are crucial here. Instead of focusing on a single tool, I look for tools that can efficiently crawl a web application and compile a comprehensive list of resources.
- Fuzzing and Asset Discovery: Once I have a map of the application, the next step is to discover hidden or non-obvious assets, including directories, files, and functionalities not directly linked within the application. Fuzzing tools come into play here, helping me guess and identify these assets. My preference leans towards tools that can automate this process, offering customization options to fine-tune my fuzzing techniques.
- Interception and Request Manipulation with Proxies: A significant part of penetration testing involves intercepting and manipulating web requests. Proxies are indispensable for this purpose, allowing me to view, modify, and replay requests. I rely on proxies that offer advanced features like SSL interception, request modification, and automated testing capabilities.
- Vulnerability Scanning and Exploitation: Finally, identifying vulnerabilities and potential points of exploitation is the culmination of the testing process. Vulnerability scanners that can automate the detection of common vulnerabilities and provide actionable insights are a key part of my toolkit. However, I also value tools that allow for manual testing and exploration, as automation cannot catch every possible security issue.
Throughout this series, I’ll delve into how I use these tools in a real-world context, integrating them into my methodology to conduct thorough and effective web application penetration tests.
Laboratory
Setting up a practical lab environment is crucial for me to apply and refine the hacking techniques I discuss in this series. A lab provides a safe, legal, and controlled environment for me to practice my skills. That’s why I chose the OWASP Juice Shop project as my lab environment. OWASP Juice Shop is a deliberately insecure web application designed for training, educational purposes, and to test web application security tools and techniques.
Why OWASP Juice Shop?
OWASP Juice Shop encompasses a wide range of web vulnerabilities, making it an ideal choice for a hands-on learning environment. It covers the OWASP Top 10 vulnerabilities and beyond, offering me a comprehensive platform to practice attacks and testing strategies in real-time without any legal implications.
Setting Up Your Lab with Docker
Docker simplifies the process of deploying applications and their environments. To use OWASP Juice Shop as your lab, you first need to have Docker installed on your machine. Docker allows you to run applications in isolated environments called containers. Here’s a brief guide on setting up OWASP Juice Shop using Docker:
- Install Docker: If Docker isn’t already installed on your machine, you’ll need to install it. The process varies depending on your operating system, but for Ubuntu server machines, detailed instructions are provided in the link shared in the series.
- Pull OWASP Juice Shop Docker Image: Once Docker is installed, you can pull the OWASP Juice Shop image from Docker Hub. Open your terminal and execute the following command:bash
docker pull bkimminich/juice-shop
This command downloads the latest Juice Shop image to your local machine.
- Run OWASP Juice Shop: After pulling the image, run the following command to start the Juice Shop application:
docker run --rm -p 3000:3000 bkimminich/juice-shop
This command starts a Docker container with the Juice Shop application and maps its service port (3000) to the same port on your host machine. The --rm flag automatically removes the container when it’s stopped, ensuring that your setup remains clean.
Accessing OWASP Juice Shop
With the application running, you can access OWASP Juice Shop by navigating to http://localhost:3000 in your web browser. You’re now ready to begin practicing various web application hacking techniques in a realistic, yet secure and ethical environment.
Conclusions
As we conclude the inaugural chapter of this series on hacking web applications, it’s clear that we’re embarking on a journey that not only aims to demystify the complexities of web application penetration testing but also to arm you with the knowledge and tools needed to navigate this challenging yet rewarding field.
Throughout this first installment, we’ve laid the groundwork for what promises to be an in-depth exploration into the art and science of web application security. We’ve discussed the importance of understanding the methodology behind a web audit, the necessity of proficiency with terminal and Linux tools, and the foundational knowledge of web vulnerabilities and basic programming skills, particularly in Python.
The introduction of open-source tools and the setup of a practical lab environment using the OWASP Juice Shop project highlights our commitment to providing accessible and hands-on learning experiences. These tools and resources are not just meant to serve as a guide but as a companion in your journey towards becoming proficient in web application hacking.
By focusing on the essential activities of information gathering, fuzzing, interception, and vulnerability scanning, we’ve begun to peel back the layers of web application security. Each tool and technique introduced here is a stepping stone towards a deeper understanding and mastery of the field.
As we move forward, remember that this series is designed to evolve with you, whether you’re just starting out or looking to refine your existing skills. The journey into web application hacking is both broad and deep, and what we’ve covered in this first chapter is just the tip of the iceberg.
Looking ahead, we’ll dive deeper into each category of tools, exploring more advanced techniques, and tackling real-world challenges. The OWASP Juice Shop will serve as our sandbox, where theory meets practice, and where you’ll have the opportunity to apply what you’ve learned in a controlled environment.
I invite you to stay tuned for the next chapters, where we’ll continue to build upon the foundation laid here, exploring new vulnerabilities, sharpening our skills, and furthering our understanding of how to protect web applications from emerging threats.
This series is more than just a collection of articles; it’s a pathway to mastery in web application security. Thank you for joining me on this journey. Together, let’s continue to push the boundaries of what’s possible in the realm of web application hacking.
Resources
Challenge solutions · Pwning OWASP Juice Shop
Chapters
Next chapter


💬 Comments Available
Drop your thoughts in the comments below! Found a bug or have feedback? Let me know.