Active Directory Enumeration: Automated and Manual Techniques for Privilege Escalation
23 min read
October 23, 2023

Decoding Active Directory: From Enumeration to Escalation
Welcome to a new chapter in the world of Active Directory (AD) exploration! If you’ve been following our series, you’re already familiar with the basics of AD and the common attacks used for initial access in these environments. Now, we’re shifting gears to focus on methods of enumerating Active Directory once we have a foothold, coupled with strategies for privilege escalation.
Today’s journey dives into the realm of automatic enumeration with BloodHound, a tool that has become indispensable for its ability to unravel complex privilege relationships in AD environments. We’ll also walk through manual enumeration techniques, utilizing PowerView and windapsearch, for those instances where discretion and stealth are paramount.
This chapter is about striking the perfect balance: using advanced tools like BloodHound for comprehensive insights while also mastering the art of manual enumeration to minimize our digital footprint. Whether you’re part of a red team needing to move quietly or you’re just looking to expand your AD knowledge, this chapter will equip you with both the tools and the understanding necessary to navigate the multifaceted landscape of Active Directory.
So gear up, as we embark on this detailed journey to master the art of AD enumeration and leverage this knowledge for effective privilege escalation. Let’s get started!
Optimizing Active Directory Audits: Profound Insights with BloodHound, Sharphound, Python-Bloodhound, and RustHound
In the realm of Active Directory domain enumeration, BloodHound emerges as a pivotal tool, particularly for internal audits where network noise is a secondary concern. It functions like a navigational compass, pointing the way to privilege escalation within a domain. BloodHound, in essence, employs graph theory to uncover hidden relationships within an Active Directory or Azure environment, simplifying the visualization of complex attack paths. The installation of BloodHound is straightforward, following a basic tutorial available on Kali Linux’s website.
Once installed, accessing BloodHound is done through Neo4j credentials, leading to a user-friendly graphical interface.
Python-Bloodhound: Efficiently Enumerating Active Directory for Security Analysis
Setting up the graphical interface of BloodHound is just the initial step. The real power of BloodHound comes to the fore when it’s fed with comprehensive data from the target network. To gather this data, there are several effective tools at your disposal, each with its unique advantages.
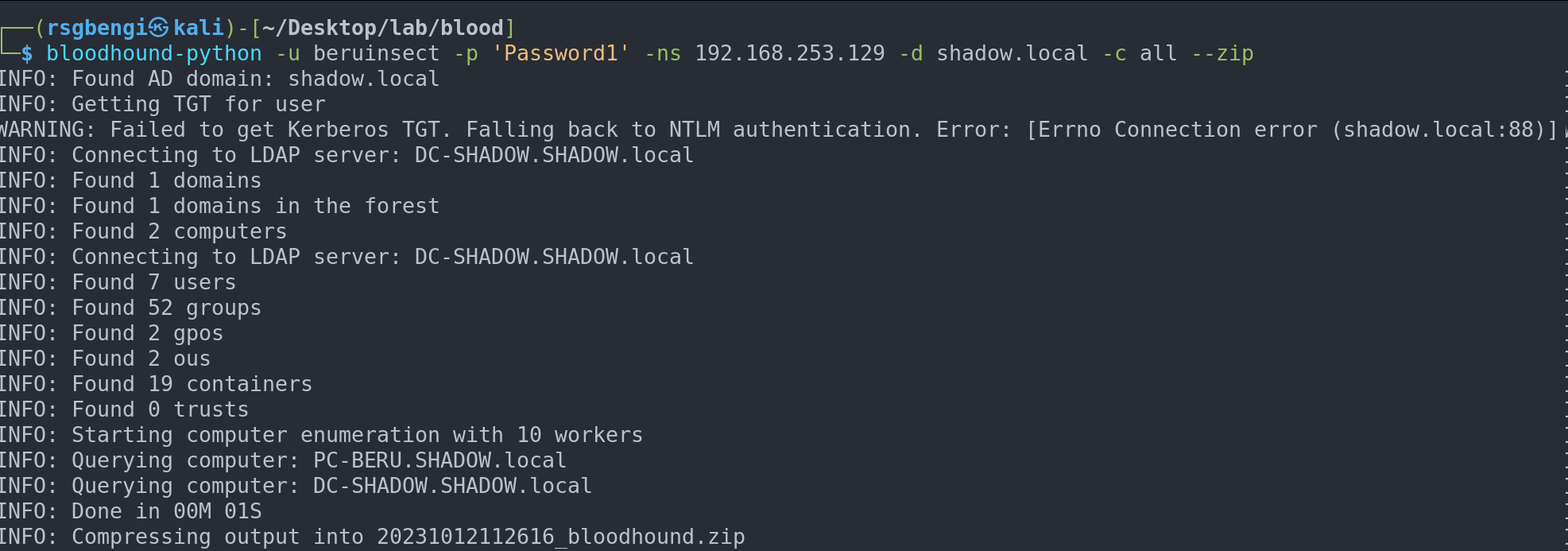
One of the most user-friendly options is “bloodhound-python”, which can be run directly from your Kali machine. This tool is designed to extract a wide array of data in an efficient manner. A typical command to gather extensive data using bloodhound-python looks something like this:
bloodhound-python -u beruinsect -p 'Password1' -ns 192.168.253.120 -d shadow.local -c all --zip In this command:
-u beruinsectand-p 'Password1'specify the username and password.-ns 192.168.253.120indicates the IP address of the name server.-d shadow.localspecifies the domain.-c alltells the tool to collect all types of data.--zipcompresses the collected data into a zip file for easy upload to BloodHound.
In scenarios where you’re using dynamic port forwarding, you might need to run bloodhound-python through proxychains to ensure it can communicate with the network. This would look something like:
proxychains bloodhound-python -u beruinsect -p 'Password1' -ns 192.168.253.120 -d shadow.local -c all --zip --dns-tcpRustHound: A Rapid Approach to Active Directory Data Collection
RustHound emerges as a compelling alternative for data collection in Active Directory environments, especially when speed is a critical factor. Although it might not boast the comprehensive feature set of bloodhound-python, RustHound compensates with its rapid data acquisition capabilities. What makes RustHound particularly intriguing is its knack for uncovering privilege escalation paths that might elude bloodhound-python.
This distinct edge in RustHound’s functionality can be a game-changer in certain scenarios. By offering different insights and potentially revealing unique escalation routes, RustHound adds another dimension to your enumeration strategy. It’s a testament to the fact that in the realm of network security and penetration testing, having a diverse toolkit can lead to more thorough and effective exploration of potential vulnerabilities.
Utilizing RustHound from Kali Linux can supplement the data gathered by other tools, providing a more rounded view of the network’s security posture. It’s an excellent example of how varied tools can complement each other, enhancing the overall effectiveness of your security analysis.
GitHub - NH-RED-TEAM/RustHound: Active Directory data collector for BloodHound written in Rust. 🦀
Sharphound: The Essential Binary Tool for In-Depth Active Directory Analysis
Sharphound stands as a prominent tool in the realm of Active Directory enumeration, widely recognized for its efficacy in data collection. However, its popularity comes with a caveat - it’s well-known to antivirus solutions. This recognition often leads to immediate detection and removal by antivirus programs, posing a significant challenge for its deployment.
To effectively utilize Sharphound in environments with active antivirus protection, one must employ evasion techniques to bypass these security measures. This could involve modifying the Sharphound binary to evade signature-based detection or using more sophisticated methods to cloak its activities.
The necessity to circumvent antivirus detection underscores the continuous cat-and-mouse game between security tools and protective measures. Sharphound’s effectiveness makes it a valuable asset for penetration testers and security analysts, but its conspicuous nature demands a higher level of stealth and creativity in its application.
For those interested in exploring Sharphound’s capabilities and integrating it into their security assessments, the official repository provides a wealth of information and resources. It serves as a starting point for understanding the tool’s functionality and potential applications in unraveling complex Active Directory environments.
GitHub - BloodHoundAD/SharpHound: C# Data Collector for BloodHound
Data Visualization with Bloodhound: Unraveling Active Directory’s Hidden Paths
After successfully gathering data using tools like bloodhound-python, RustHound, or SharpHound, the next critical step is to upload this data into BloodHound for analysis. This is a straightforward process. BloodHound provides an intuitive user interface, featuring a dedicated button for importing data.
You simply locate the button for uploading data, which is typically found on the BloodHound interface. Clicking this button will prompt you to select the data file you wish to upload. This file is often in a compressed format (like .zip), containing all the information gathered by your chosen data collection tool.
For instance, if you used bloodhound-python, your data file might be named something like ‘python-bloodhound.zip’. Select this file, and BloodHound will begin processing and integrating the data into its database. Once the upload is complete, BloodHound will display the newly imported data, ready for you to analyze. You can now explore various attack paths, identify potential vulnerabilities, and plan your approach for privilege escalation or other security assessments within the Active Directory environment.
Uploading data to BloodHound
.zip formed by python-bloodhound.zip
Once we’ve loaded the data into BloodHound, we embark on a journey of analytical possibilities. This powerful tool unfolds a variety of predefined paths for exploration. For instance, it effortlessly reveals users within the Active Directory who are susceptible to Kerberoasting. This feature is pivotal as it helps us pinpoint potential targets for elevating our privileges within the domain.
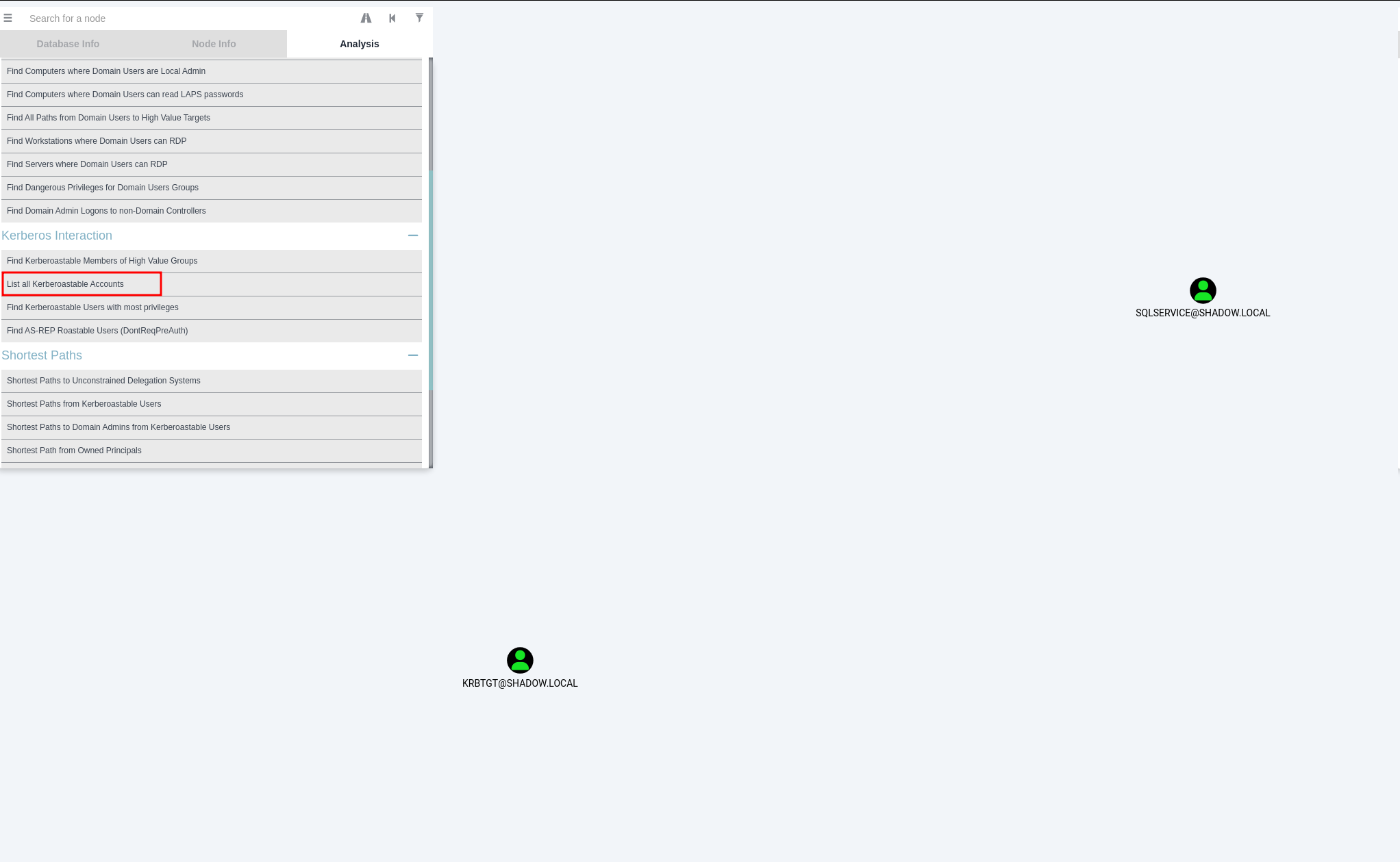
Users vulnerable to Kerberoast
But that’s just the beginning. BloodHound also guides us in finding the most direct and efficient route to the coveted position of a domain administrator. And if you’re contemplating executing a DCSync attack, BloodHound brilliantly illuminates various pathways to accomplish it successfully.
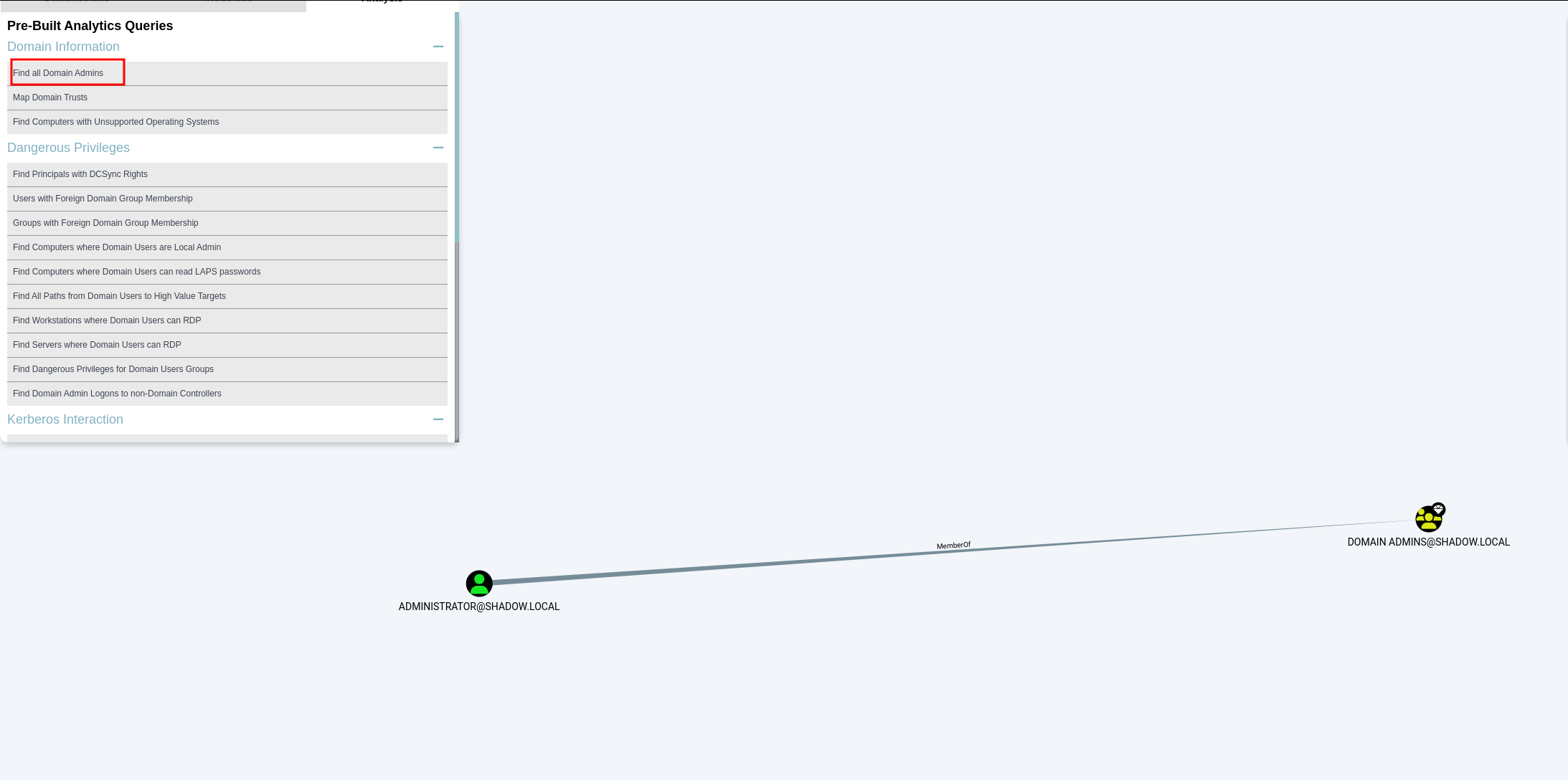
Shortest way to become a domain administrator
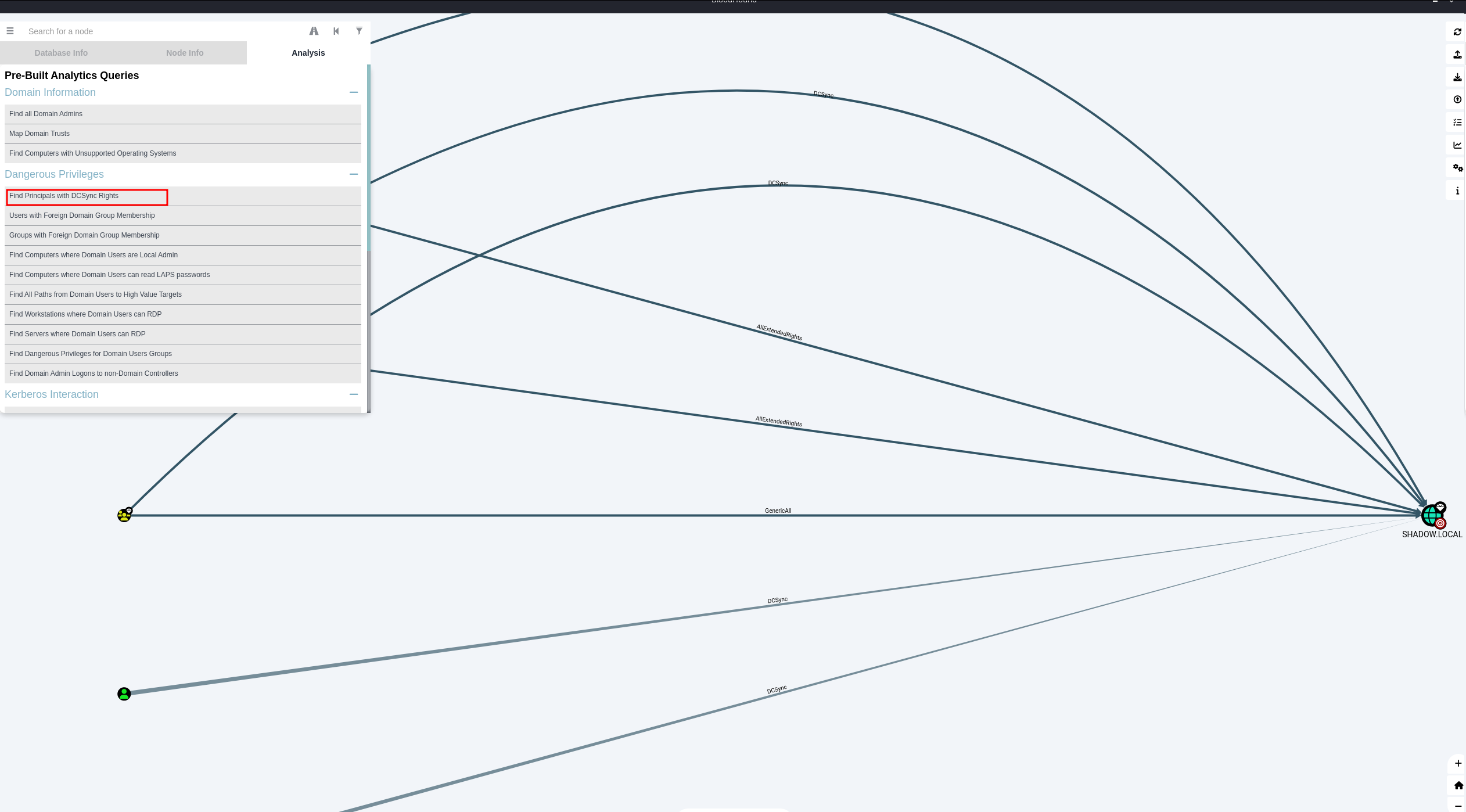
Possible ways to do dcsync
What’s truly captivating about BloodHound is its ability to provide detailed guidance on how to exploit specific configurations. A simple right-click on any graph link reveals necessary information for leveraging that particular setup. This level of detail is invaluable, especially when dealing with extended rights and other intricate aspects of Active Directory.
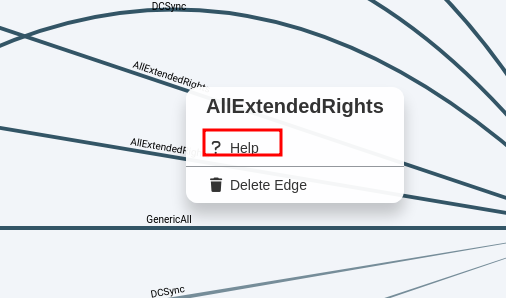
Edge help
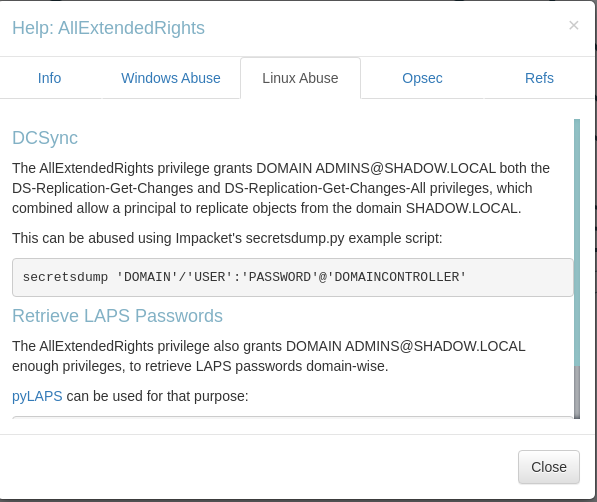
Path to escalate privilegesPath to escalate privileges
And if these predefined routes aren’t enough, BloodHound allows you to dive deeper. You can craft your own custom queries using the Cypher language, utilized in Neo4j. This means you can fine-tune your search to extract precisely the information you need. For example, if you’re interested in service accounts that might be vulnerable to Kerberoasting and contain ‘SQL’ in their names, BloodHound enables you to formulate a specific query for that.
Creation of own queries
Imagine you want to delve deeper into identifying service accounts potentially vulnerable to Kerberoasting and specifically those associated with ‘SQL’. BloodHound empowers you with the ability to create such targeted queries. Using its Cypher query language, you can pinpoint these accounts with precision.
Here’s how you can structure this specific query:
MATCH (u:User) WHERE ANY (x IN u.serviceprincipalnames WHERE toUpper(x) CONTAINS 'SQL')RETURN u
This query effectively scans through user accounts, focusing on service principal names. It filters out those containing ‘SQL’, providing a concise list of relevant targets. This level of detailed querying is a testament to BloodHound’s adaptability and depth, allowing you to tailor your investigation to your specific needs.
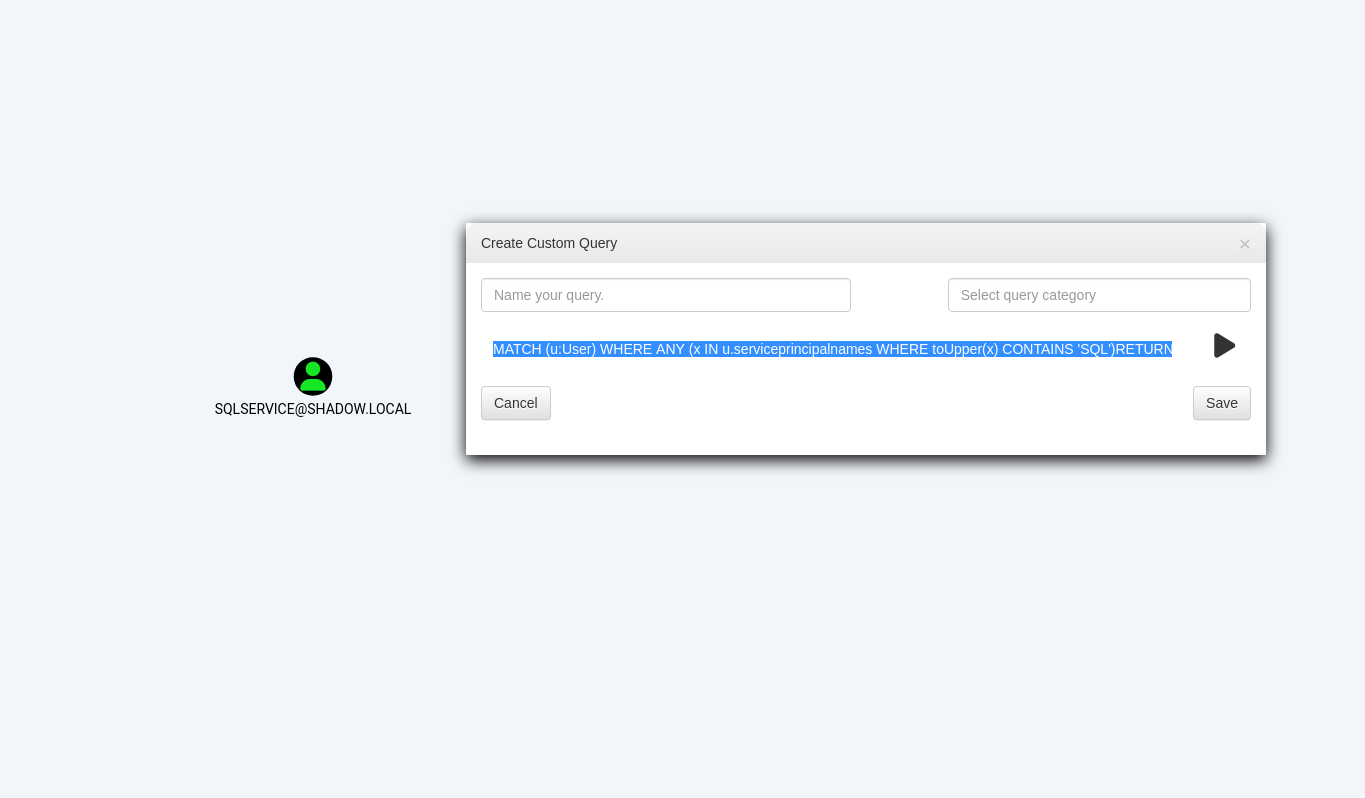
Query to show accounts vulnerable to Kerberoast and containing “SQL”.
Cypher’s syntax may be relatively straightforward, but it unlocks a world of possibilities when exploring Active Directory data. For those who wish to delve deeper, a comprehensive list of queries can be found in the BloodHound Cypher Cheatsheet. This resource is invaluable for both newcomers and seasoned professionals.
BloodHound utilizes Neo4j, a graph database, for its data structuring, and Cypher serves as the language for querying this complex information. Cypher might seem a bit intricate at first – it’s almost akin to crafting with ASCII art – but its potential for revealing critical insights in your data is immense.
The Cheatsheet provided at BloodHound Cypher Cheatsheet is more than just a guide; it’s a treasure trove of queries. It covers a wide range of scenarios and objectives, providing tailored queries for specific data extractions and insights. This resource is an essential tool for anyone looking to maximize their use of BloodHound, offering guidance and inspiration for diverse and effective data analysis
Mastering Manual Techniques: A Guide to In-Depth Active Directory Enumeration
Manual enumeration is a critical skill for Red teams aiming for stealth and minimal digital footprint. This process involves meticulously gathering information without triggering alarms. PowerView and evil-winrm are key tools in this task, allowing for in-depth exploration of Active Directory environments.
Another pivotal element in manual enumeration is LDAP (Lightweight Directory Access Protocol). It’s an efficient way to remotely query the domain database (NTDS) for valuable data on users, groups, and computers within a domain. For this purpose, windapsearch is an invaluable utility, offering a streamlined approach to LDAP queries.
It’s important to remember that these tools are just examples of what’s available for domain enumeration. The cyber security landscape is rich with alternatives like enum4linux and crackmapexec, each offering unique features and approaches. It’s worthwhile to experiment with these tools and discover which ones align best with your needs and preferences.
In manual enumeration, asking the right questions is as important as the tools you use. A well-structured approach, as outlined in the provided diagram, guides you through a thorough and effective enumeration process. It’s about piecing together the puzzle of a domain’s structure and vulnerabilities, one detail at a time.
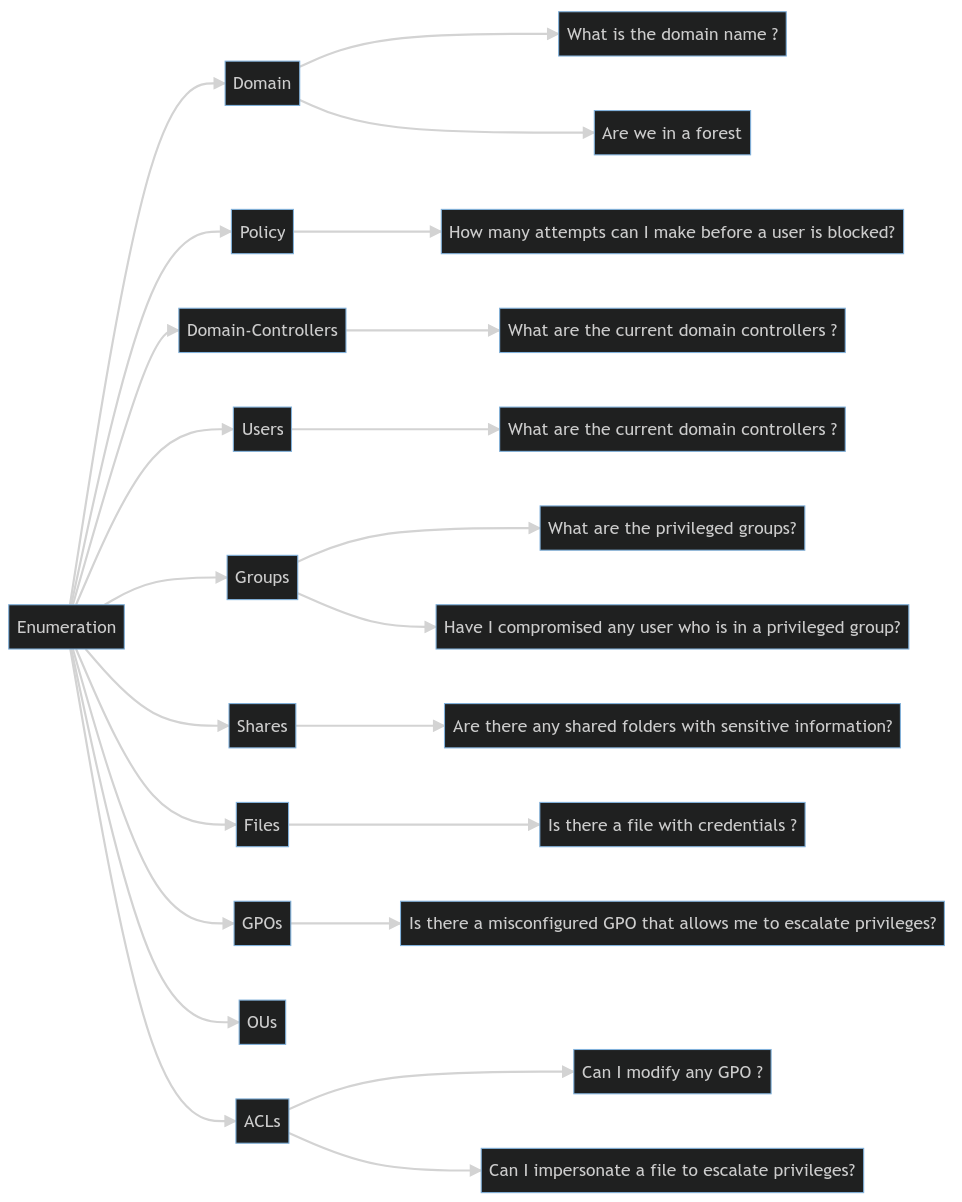
Diagram of questions we should answer from the domain
Effective Domain Management: Utilizing Evil-WinRM for Advanced Active Directory Enumeration
Evil-winrm, a potent tool in the arsenal of penetration testers, serves as a gateway to Windows Remote Management (WinRM). As explored in our previous discussions, particularly in chapter 5, this tool’s effectiveness in script execution is unparalleled.
To initiate, use the command: evil-winrm --ip <target-ip> -u <user> -p <password> -s <scripts_directory>. This launches a shell where specific scripts can be invoked, embedding their functions into the session’s memory. It’s a seamless process that amplifies your capabilities within the target environment.
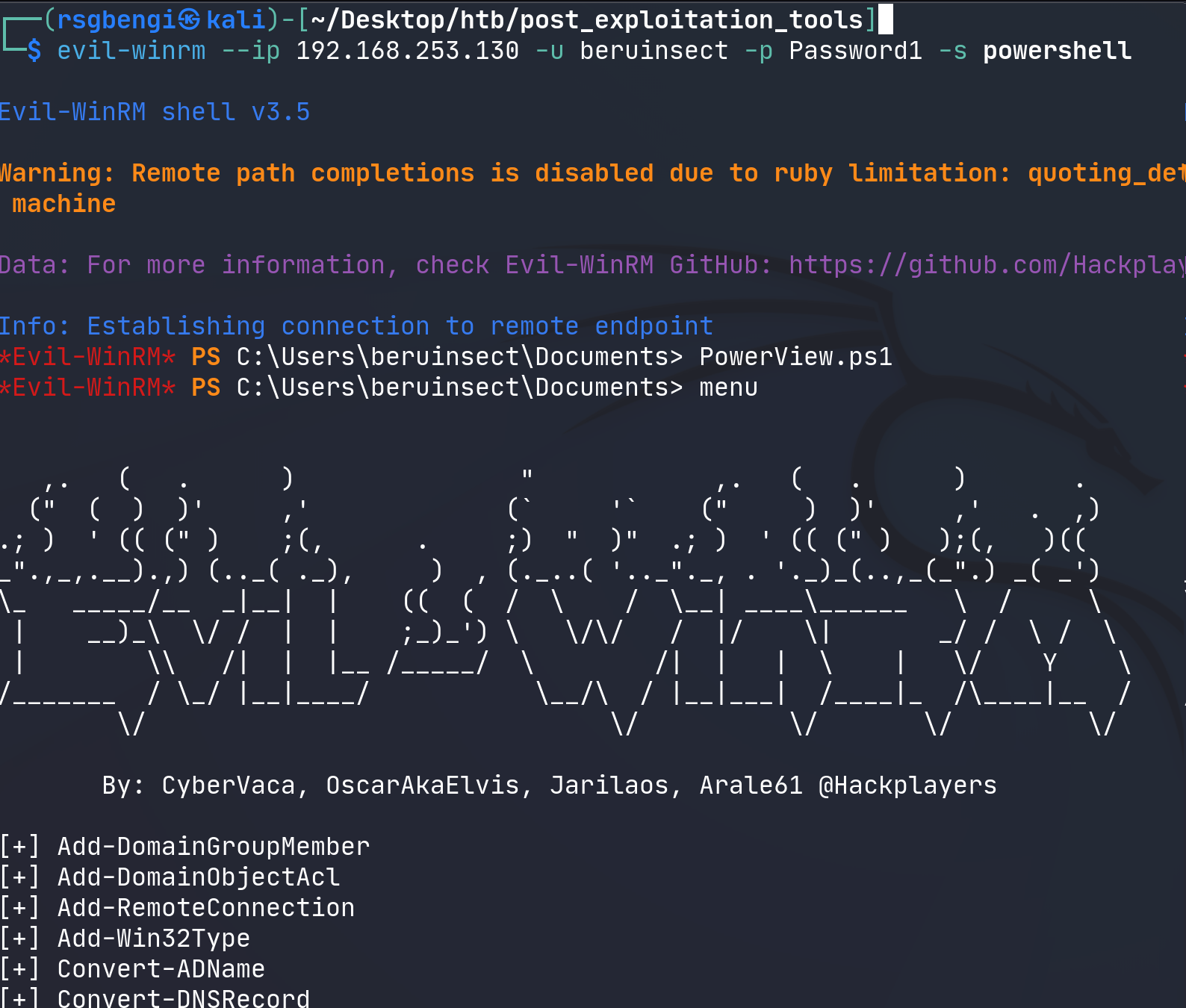
Running winrm with powerview
This article expands beyond our prior discussions, diving into the enumeration of Group Policy Objects (GPOs), Organizational Units (OUs), and Access Control Lists (ACLs). These elements, crucial in understanding the intricacies of Active Directory environments, were not covered in earlier articles. By integrating these concepts here, we aim to enrich your comprehension and operational capacity in these domains.
Unraveling the Domain Structure: Key Insights for Targeted Exploration
Diving into the domain structure is a crucial first step once we’ve established a shell in our target environment. Understanding the domain’s hierarchy, including its possible placement within a forest or its relationship with parent domains, lays the foundation for deeper exploration. This knowledge is pivotal in plotting a path for privilege escalation or identifying potential vulnerabilities.
To extract domain information, the Get-NetDomain function serves as our primary tool. This function reveals critical details about the domain’s structure and attributes.
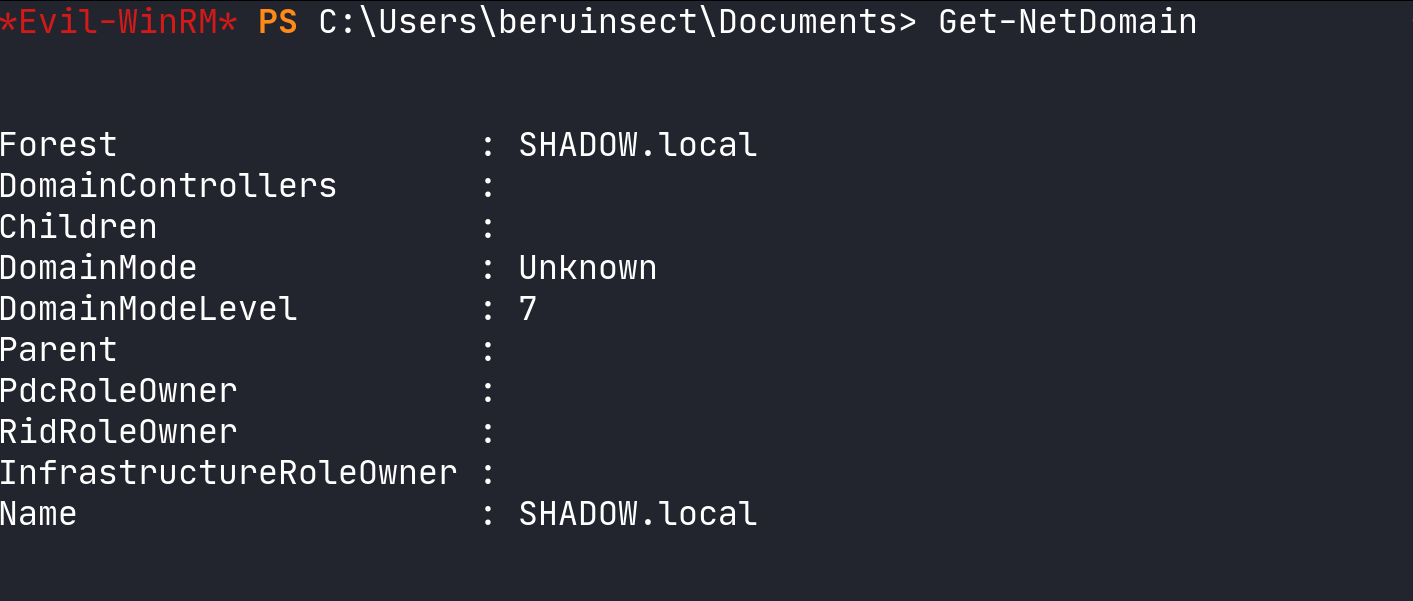
Domain information
Equally important is capturing the domain’s Security Identifier (SID) using Get-DomainSID. The SID, a unique identifier, plays a vital role in various advanced techniques, such as forging Golden Tickets, which can grant extensive access within the domain.
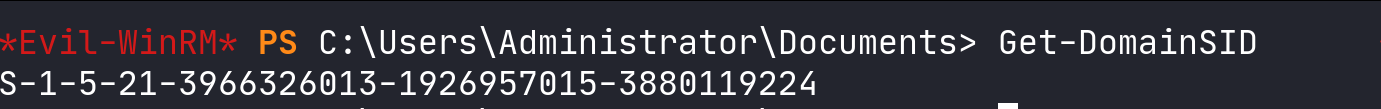
Domain SID
For a broader perspective, LDAP (Lightweight Directory Access Protocol) proves invaluable. Using windapsearch with the metadata module, we can obtain a comprehensive overview of the domain:
windapsearch --dc 192.168.253.129 -u [email protected] -p Password1 -m metadata
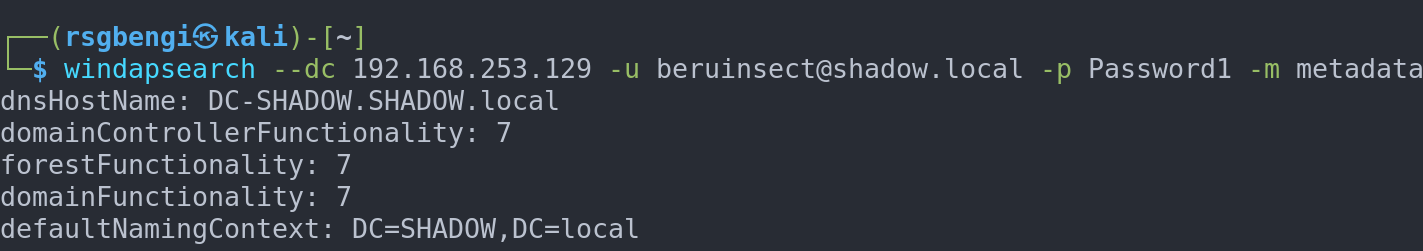
Domain Metadata
This command allows us to delve into the domain’s metadata, offering insights that might be overlooked by standard enumeration tools. Further, the flexibility of windapsearch is evident in its ability to filter results based on specific attributes, enhancing the efficiency and focus of our enumeration efforts.
Module help
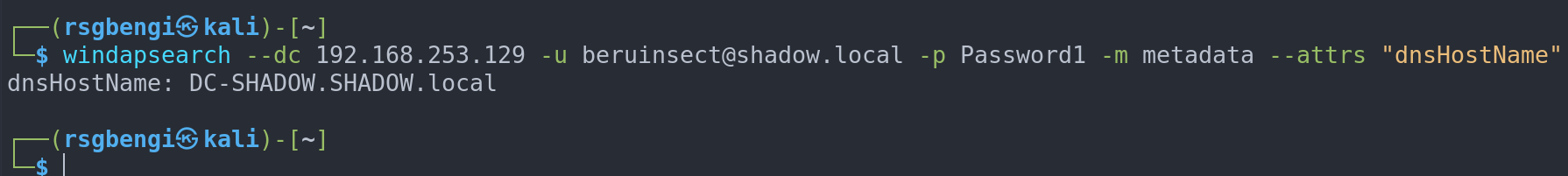
Use of “attrs”
Exploring Security Policies with PowerView
The password policy in an Active Directory domain is a critical aspect of security, and PowerView offers an efficient way to examine these policies. It’s particularly useful when considering brute force attacks, as a robust password policy can be a significant barrier against such attempts. With PowerView, we can gain detailed insights into these policies using the command:
(Get-DomainPolicy)."SystemAccess"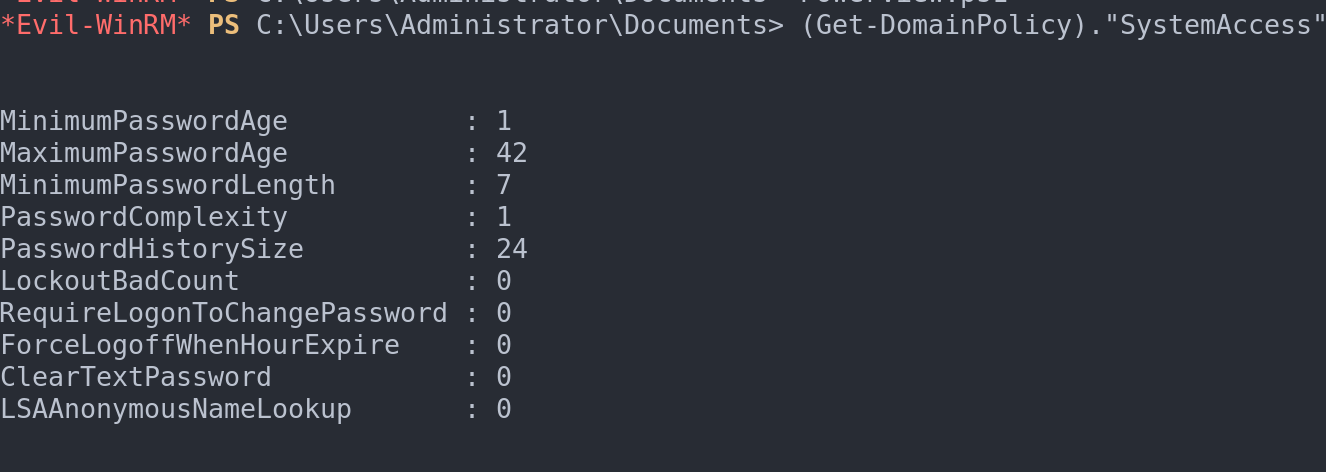
Moreover, PowerView enables us to access the configuration of Kerberos tickets, a key element in managing authentication in Active Directory. Understanding Kerberos configuration is essential as it can reveal vulnerabilities or key security practices. To check this configuration, we use:
(Get-DomainPolicy)."kerberospolicy"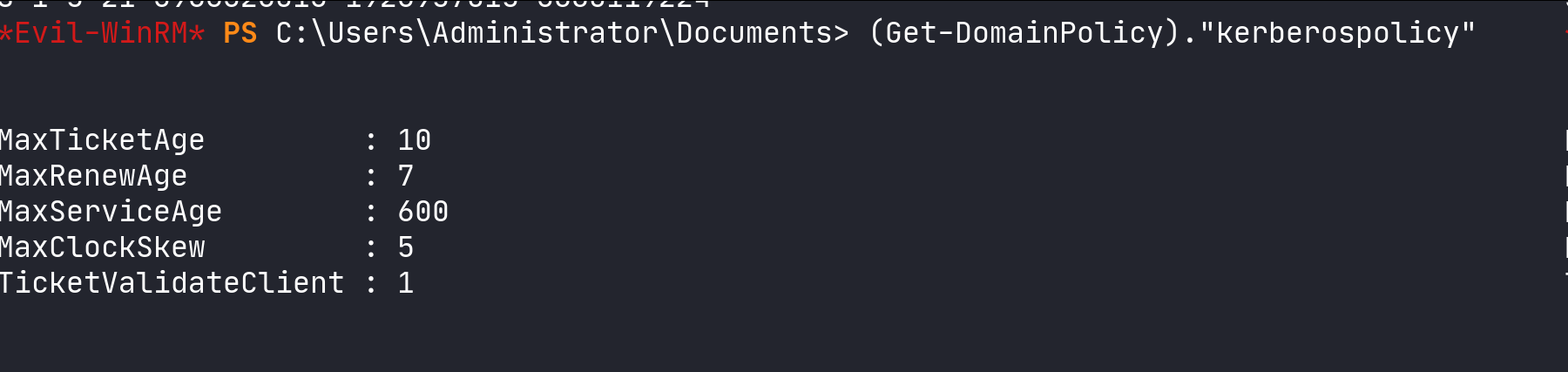
Kerberos policy
Uncovering Domain Controller Details with PowerView
In the realm of Active Directory, Domain Controllers play a pivotal role, and understanding their configuration is vital. PowerView offers a simple yet effective means to retrieve detailed information about these controllers. Crucial details such as the operating system version are particularly important as older versions might be susceptible to well-known vulnerabilities like EternalBlue. This information can be obtained using the command:
Get-DomainController 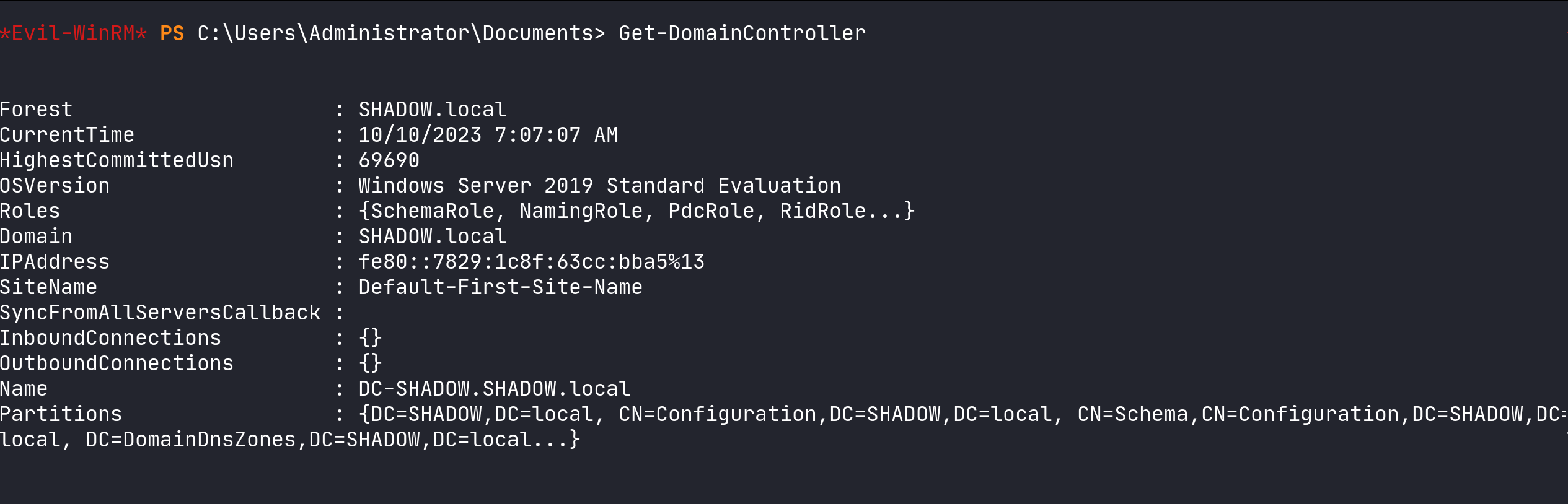
Obtain domain controller information
For environments with numerous domain controllers, where a concise overview is needed, PowerView allows us to streamline the output. By using the command below, we can focus on just the names of the controllers, providing a clear and succinct view:
Get-DomainController | select name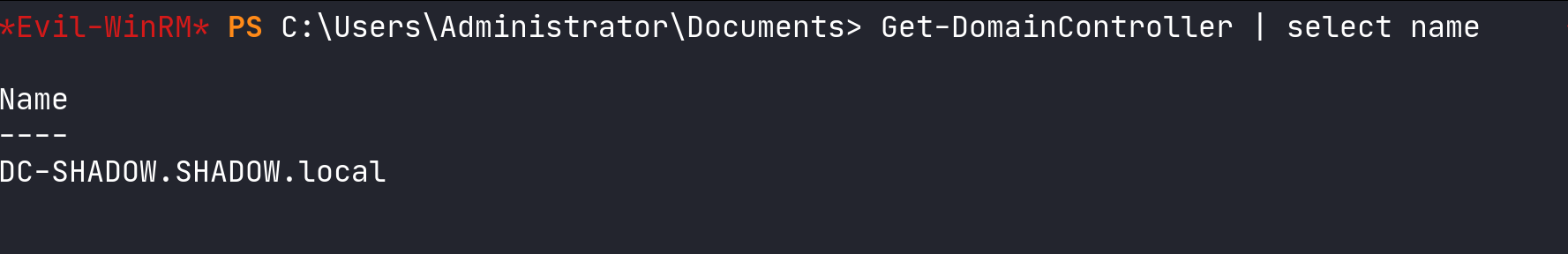
Filter for viewing domain controllers
Navigating Domain User Enumeration with PowerView and Windapsearch
Enumerating domain users is a critical step in understanding the landscape of an Active Directory environment. PowerView simplifies this process, offering commands that enable detailed insights into user accounts. The command Get-DomainUser can be employed to list all domain users, and for a more tailored output, the following command can be used:
<details>
<summary>Get-DomainUser </summary>
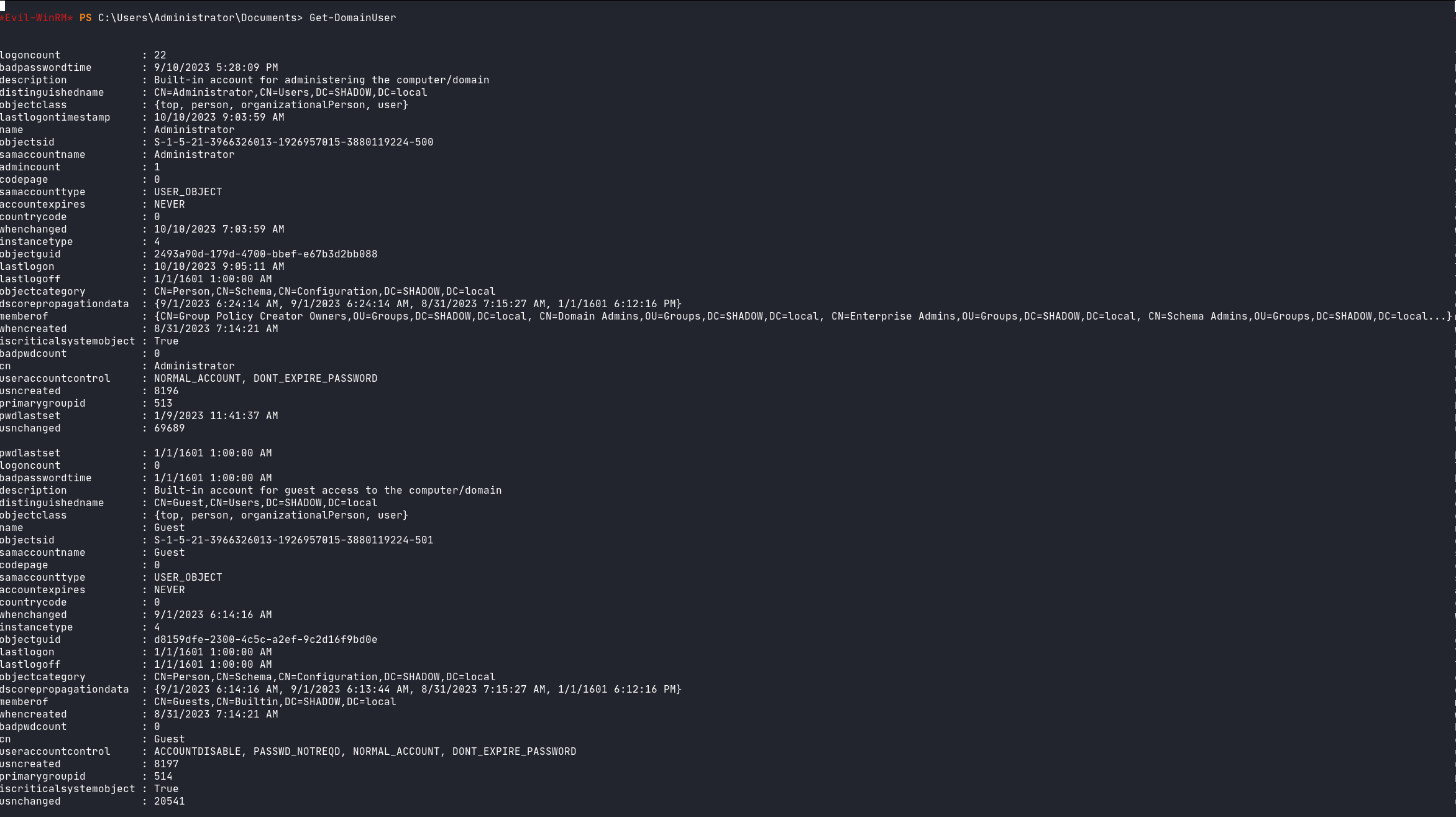
Get Domain users
</details>
Get-DomainUser | select cn,distinguishedname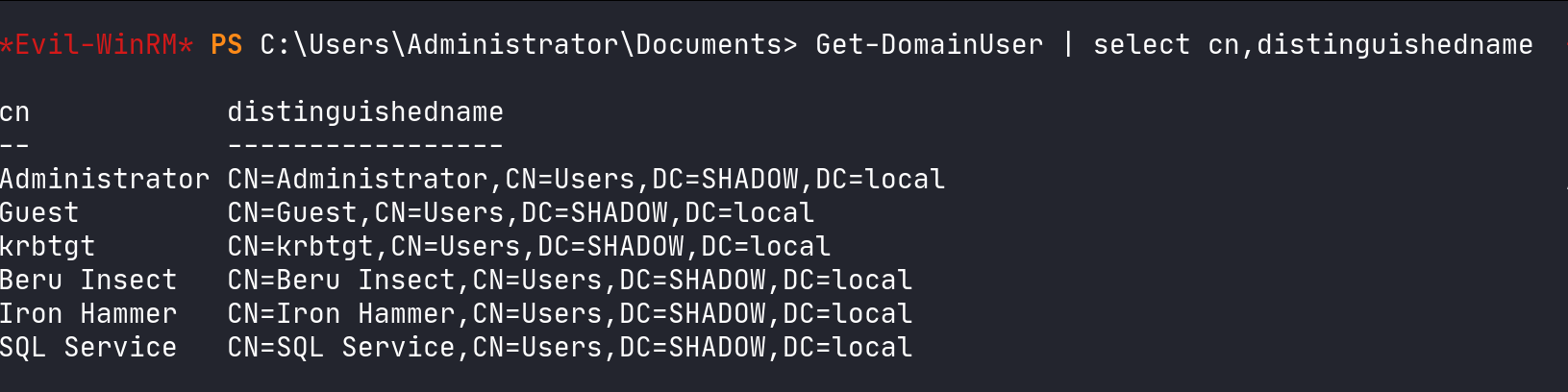
Filter user information
For an in-depth view of specific users, PowerView allows us to extract various properties such as creation dates, security identifiers (SIDs), and password policies:
Get-DomainUser -Identity <username>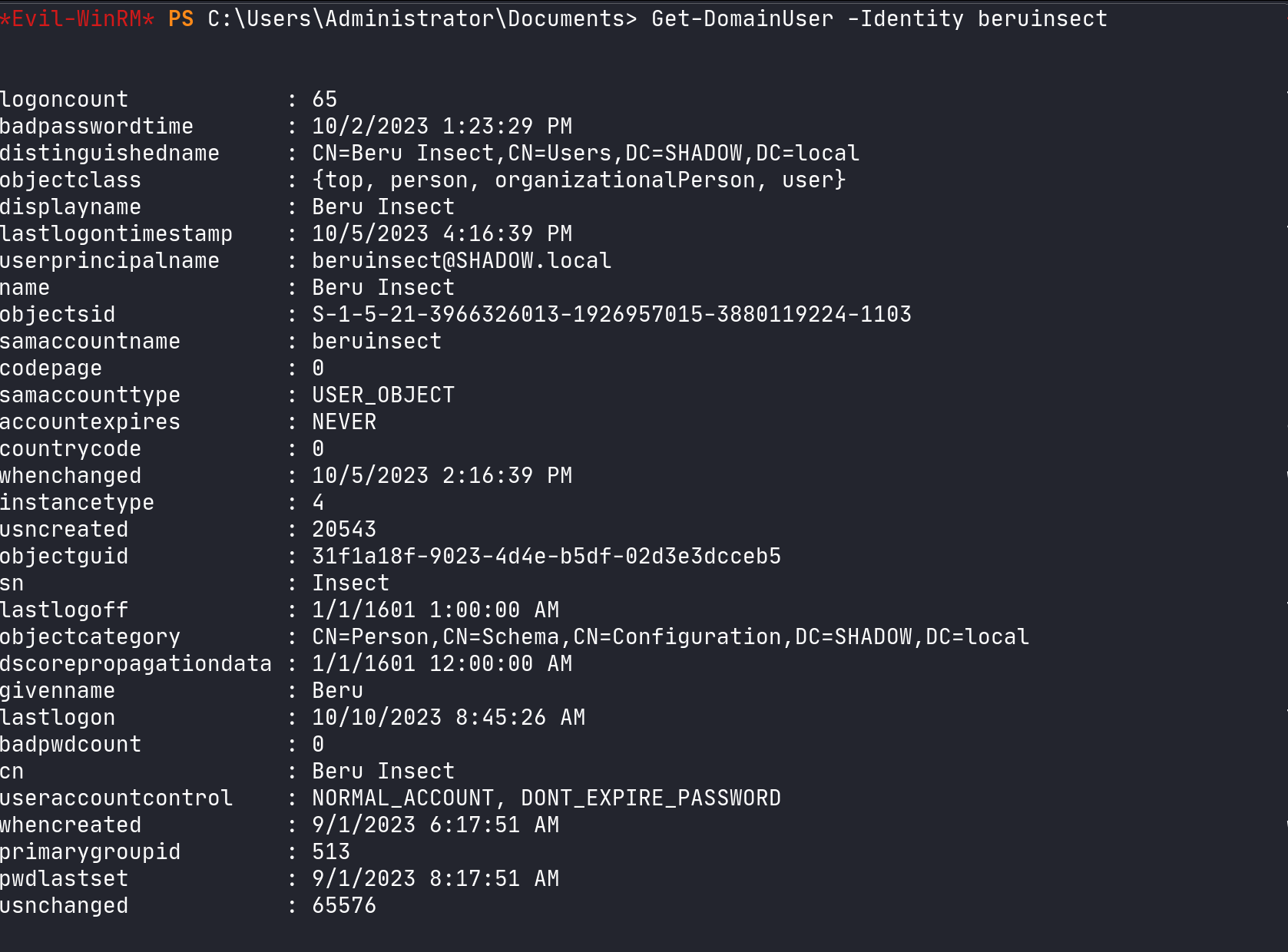
Filter by a a specific user
Get-DomainUser -Identity <username> -Properties DisplayName, MemberOf,objectsid,useraccountcontrol | Format-List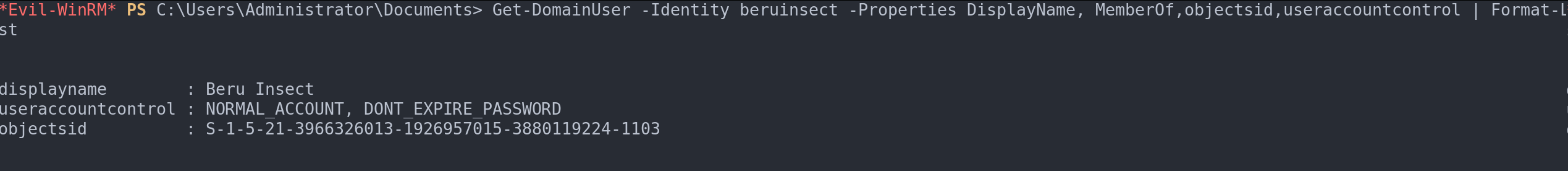
Filter information of interest
Windapsearch complements these PowerShell functionalities by enabling remote LDAP enumeration of domain users:
windapsearch --dc 192.168.253.129 -u [email protected] -p Password1 -m users
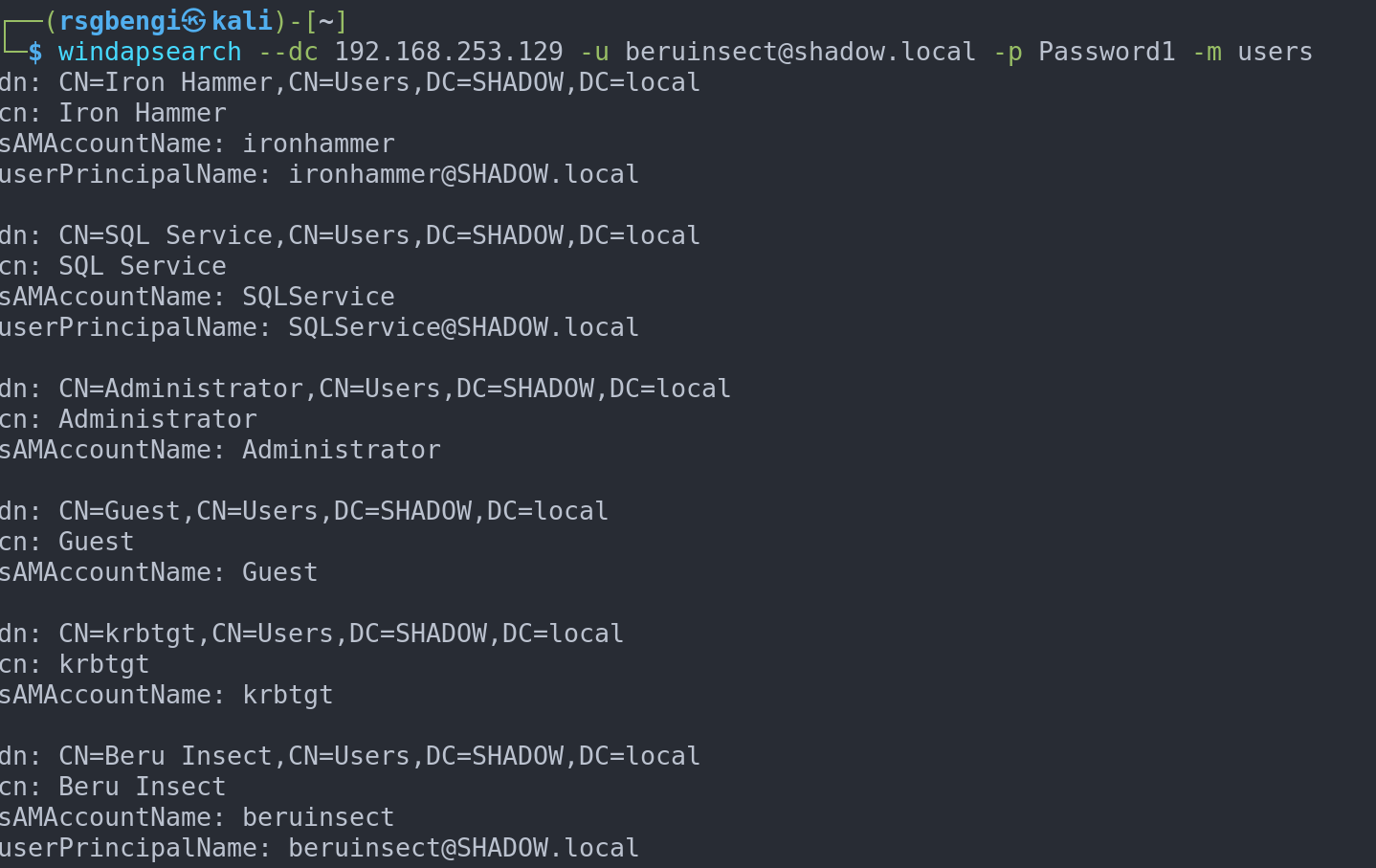
Obtaining all users
Moreover, Windapsearch is invaluable for identifying user accounts susceptible to Kerberoasting attacks:
windapsearch --dc 192.168.253.129 -u [email protected] -p Password1 -m
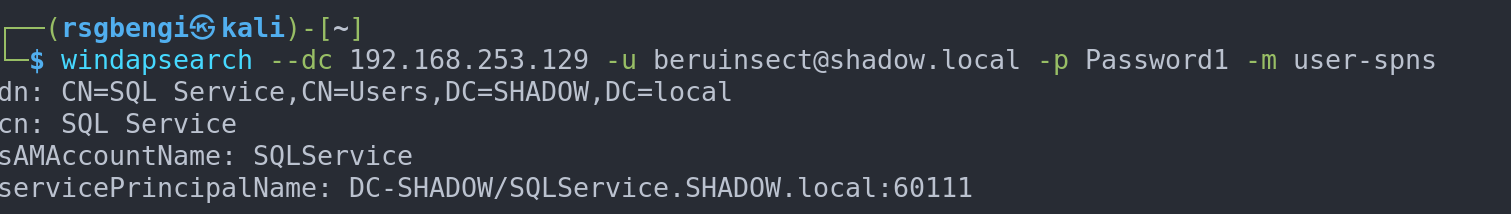
Obtaining users with service accounts
Exploring Domain Computers: PowerView and LDAP Approaches
Unveiling the landscape of domain computers is a crucial step in Active Directory enumeration. PowerView provides the means to not only list these computers but also delve into their operating systems, revealing potential vulnerabilities:
To list the computers visually:
Get-NetComputer| select name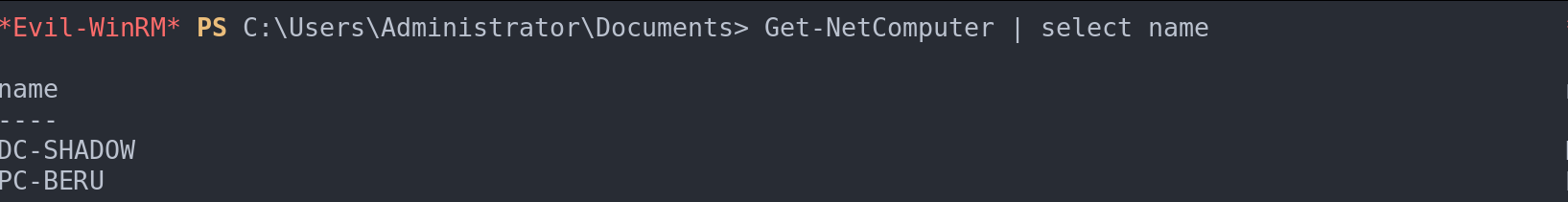
Filter computers
To identify computers running specific versions of Windows, such as Server 2016, PowerView offers a detailed command:
Get-NetComputer -OperatingSystem "*Server 2016*" | select name ,operatingsystem |Format-List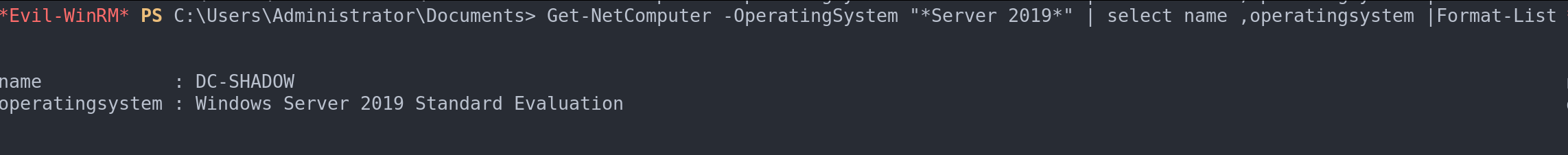
Filter by operating system
Complementing PowerView’s capabilities, LDAP queries through Windapsearch enable enumeration of domain computers, providing an alternative approach:
windapsearch --dc 192.168.253.129 -u [email protected] -p Password1 -m computers
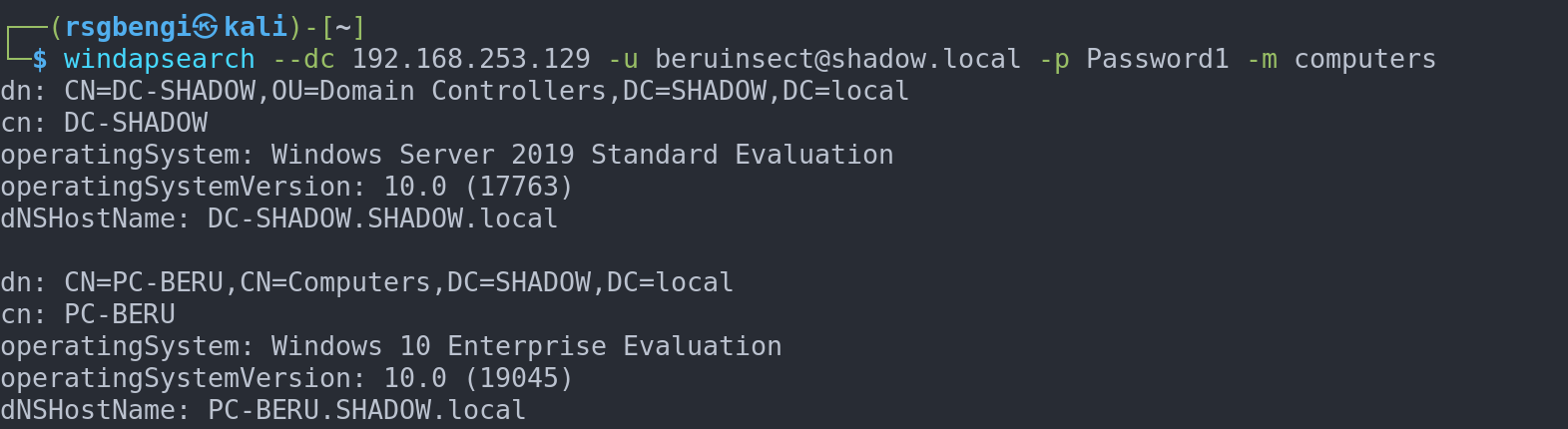
Getting machines from LDAP
Mastering Group Enumeration
Exploring group dynamics within Active Directory is pivotal for understanding privilege escalation avenues. In upcoming chapters, we’ll dive deeper into the intricacies of critical groups. For now, let’s focus on how to enumerate them effectively using PowerView and Windapsearch.
To get a comprehensive list of all available groups with PowerView:
Get-NetGroup | select name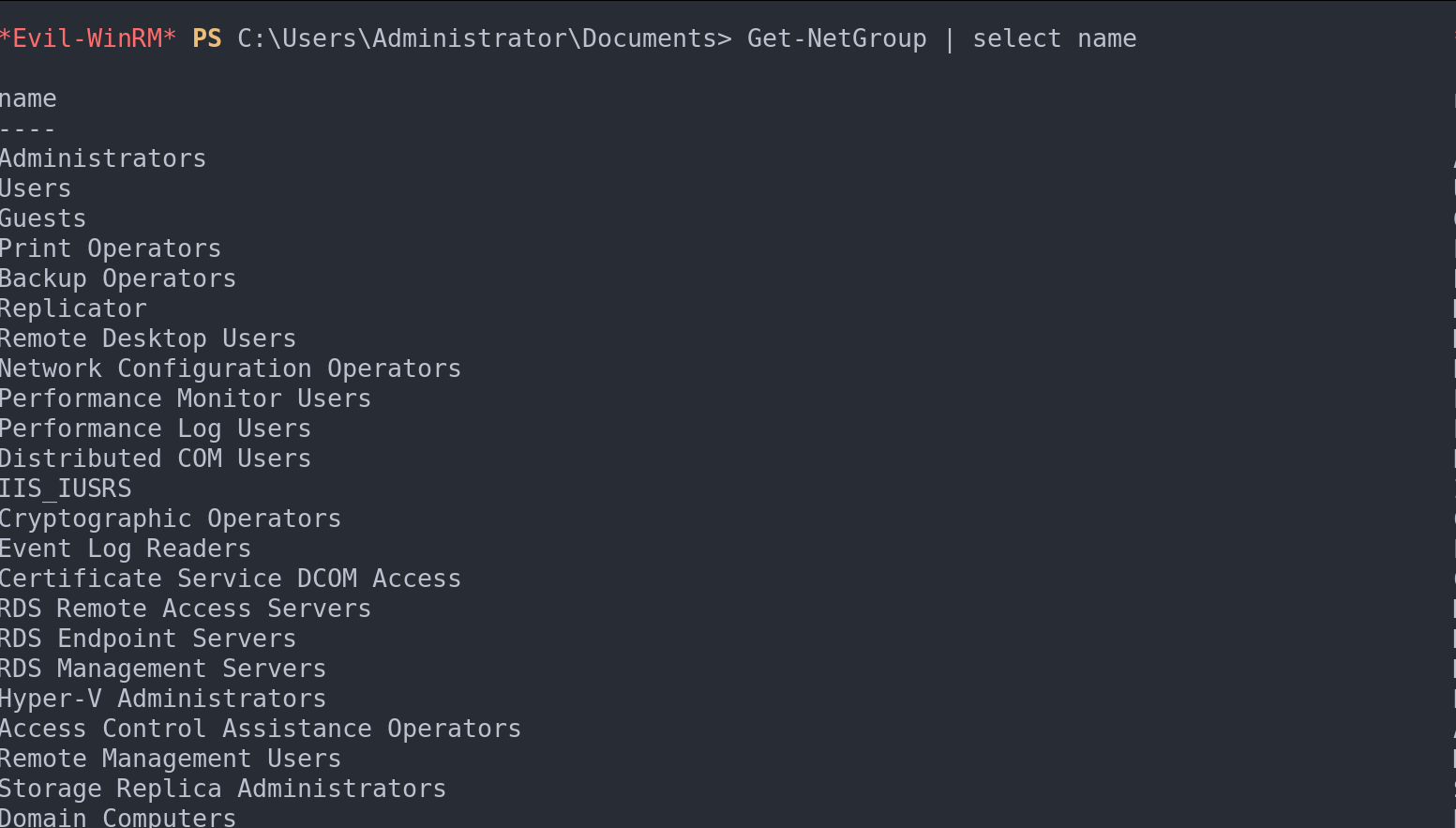
List domain groups
For specifics about a particular group, such as ‘Domain Admins’:
Get-NetGroup 'Domain Admins'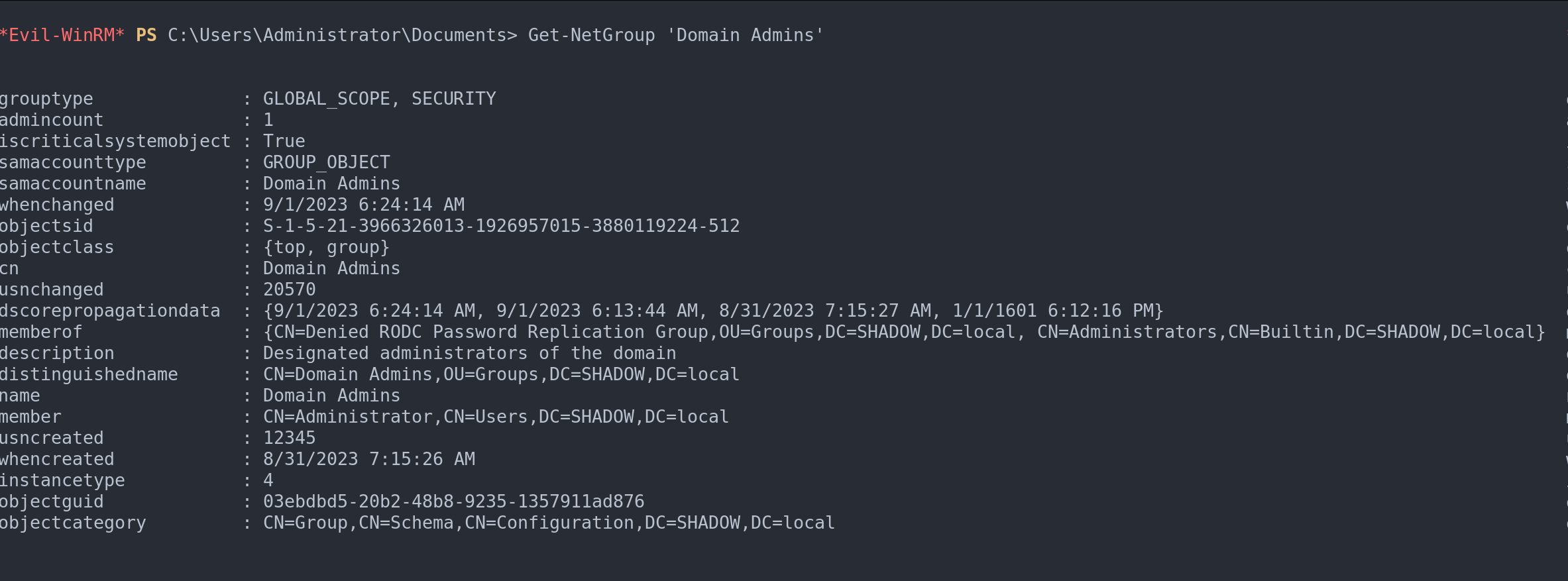
Filter by group
Using a wildcard, we can filter groups containing the term ‘admin’:
Get-NetGroup "*admin*"| select name 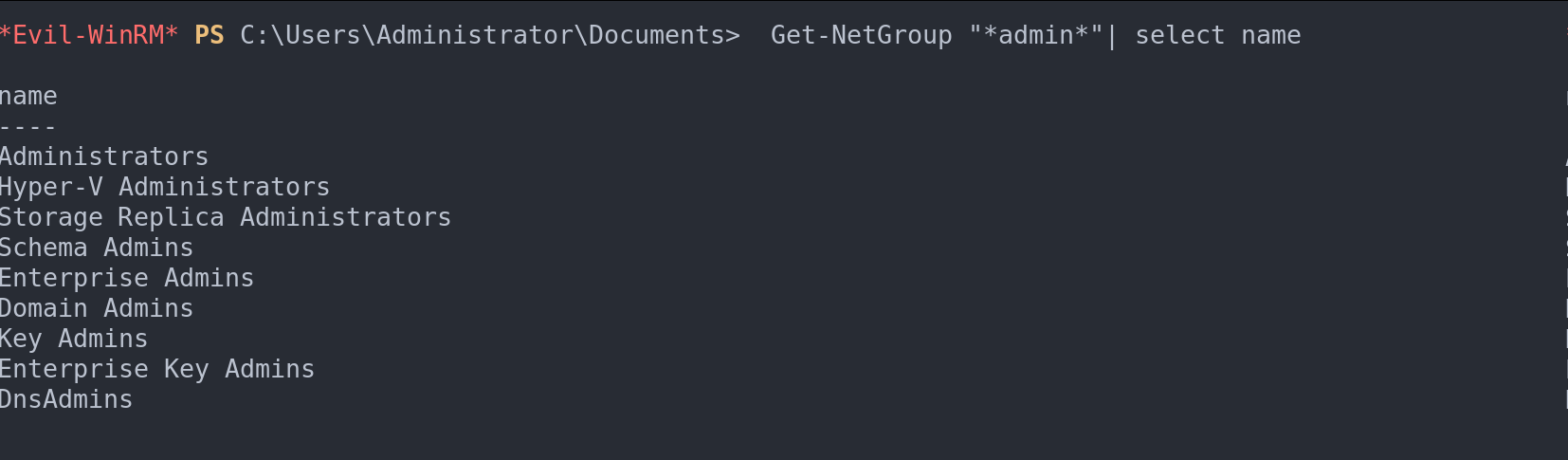
Filter by groups with the word admin
To uncover all members of a specific group like ‘Domain Admins’:
Get-NetGroupMember -MemberName "domain admins" -Recurse | select MemberName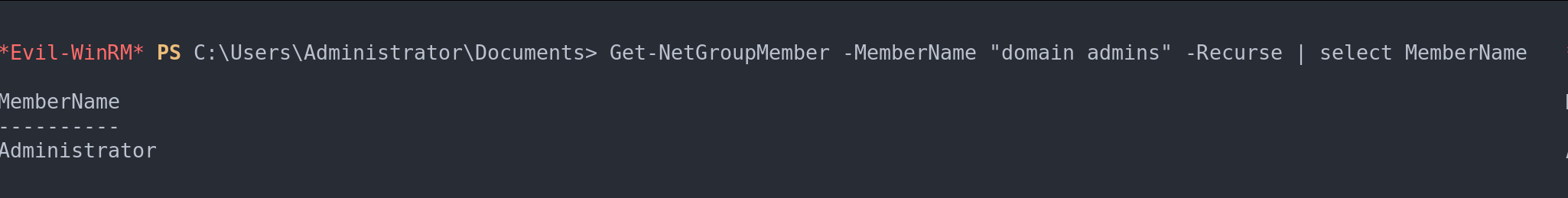
Filter by users who are administrators
To list all groups within the domain:
windapsearch --dc 192.168.253.129 -u [email protected] -p Password1 -m groups
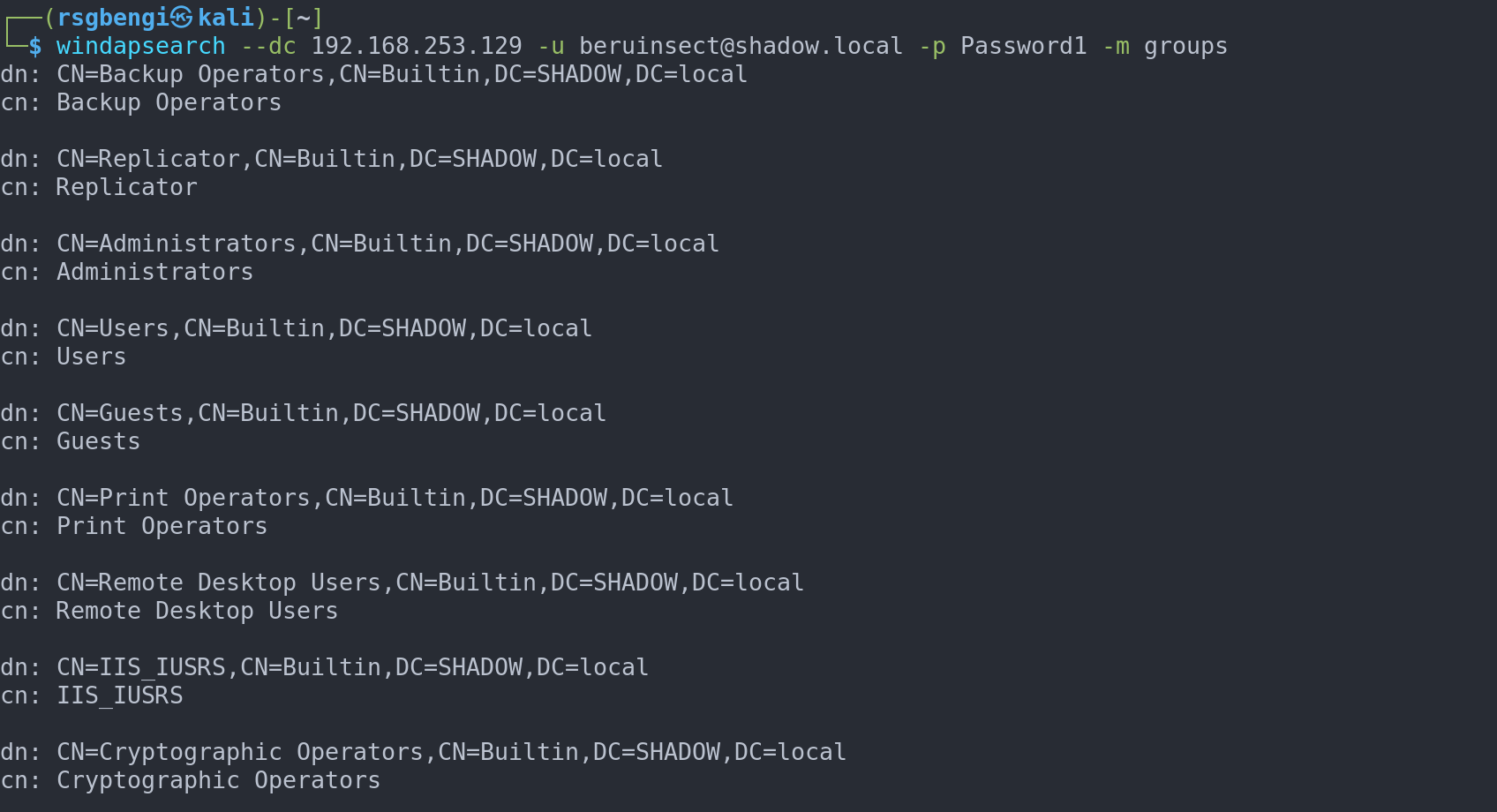
Obtaining groups through windapsearch
For a targeted approach to uncover members within the ‘Domain Admins’ group:
windapsearch --dc 192.168.253.129 -u [email protected] -p Password1 -m members --group "CN=Domain Admins,OU=Groups,DC=SHADOW,DC=local"
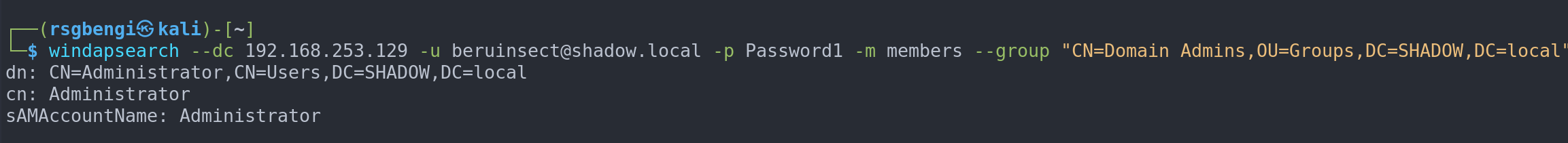
Filter by members of a specific group
Deciphering Local Group Dynamics in Windows Environments
Delving into the local group structure of Windows machines is a critical step in understanding the security and user management of a system. Here’s how we can methodically enumerate and analyze local groups and their members:
Listing Local Groups: To get an overview of all local groups present on a Windows machine, use the following PowerView command:
Get-NetLocalGroup | Select-Object GroupName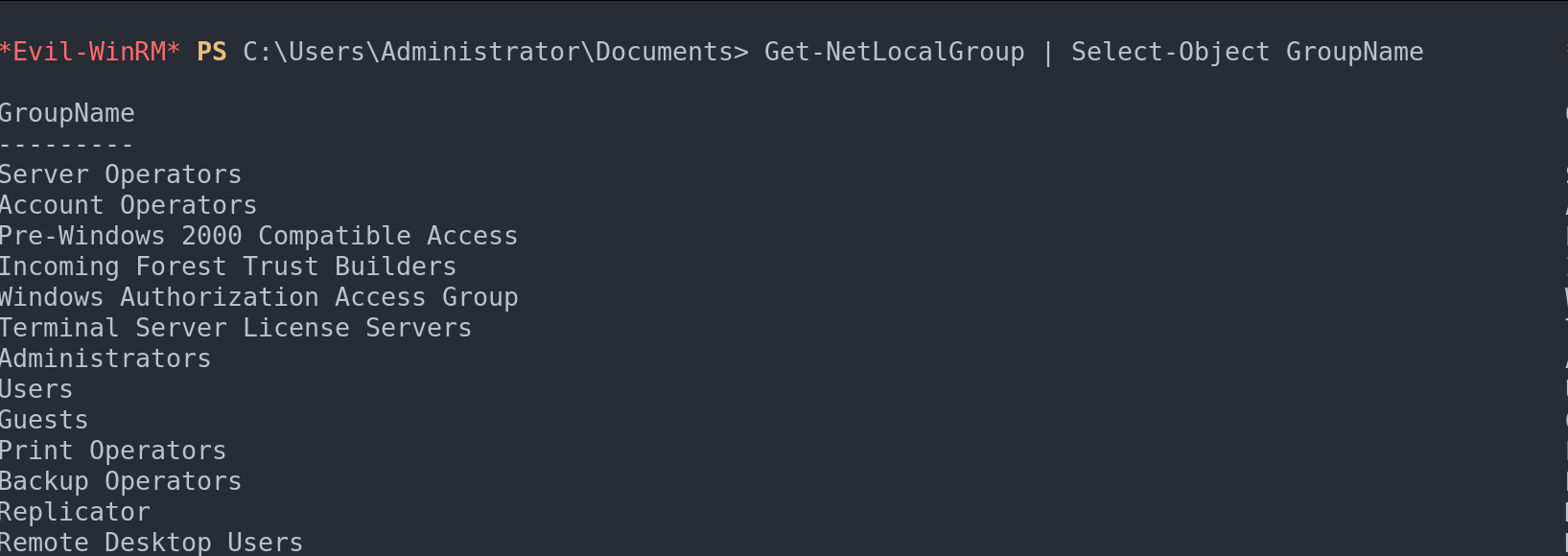
List local groups
Examining Group Members: To understand who belongs to a specific group, such as ‘Administrators’, use:
Get-NetLocalGroupMember -GroupName Administrators | Select-Object MemberName, IsGroup, IsDomainThis command provides insights into whether the members are users or groups and if they belong to the domain.
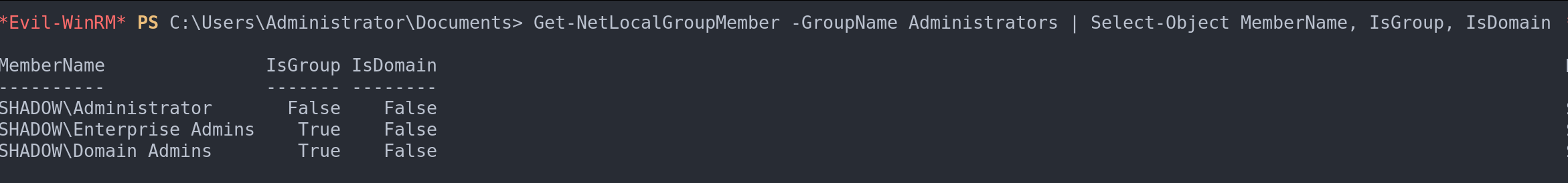
Members of a group
Investigating User’s Group Affiliations: To explore the groups a specific user is part of, use:
Get-NetGroup -UserName <"username">| select name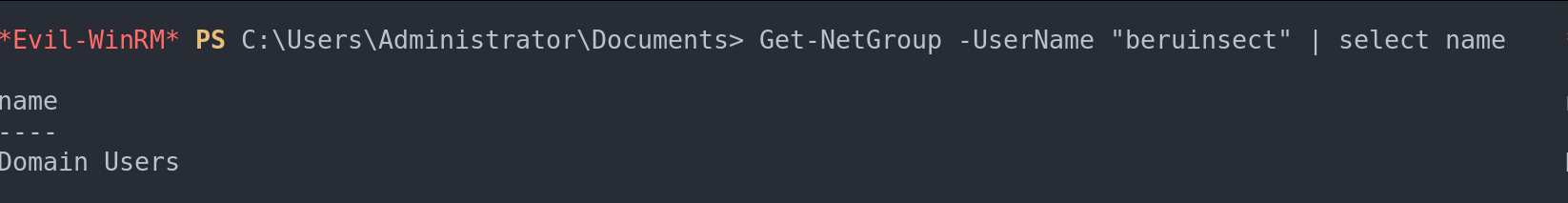
Local groups of a specific user
Uncovering Shared Network Resources: A Dive into NetShares
Exploring shared network folders is akin to uncovering hidden treasures within a network. These shares often contain sensitive information, crucial backups, and sometimes even forgotten data, ripe for examination. To embark on this exploration in Windows environments, we utilize a powerful tool in our arsenal:
Identifying Shared Folders: To list all shared network resources on a Windows machine, the following PowerView command becomes our key:
<details>
<summary>Get-NetShare</summary>
This command reveals all shared folders, providing a map to potentially valuable or sensitive resources within the network landscape.
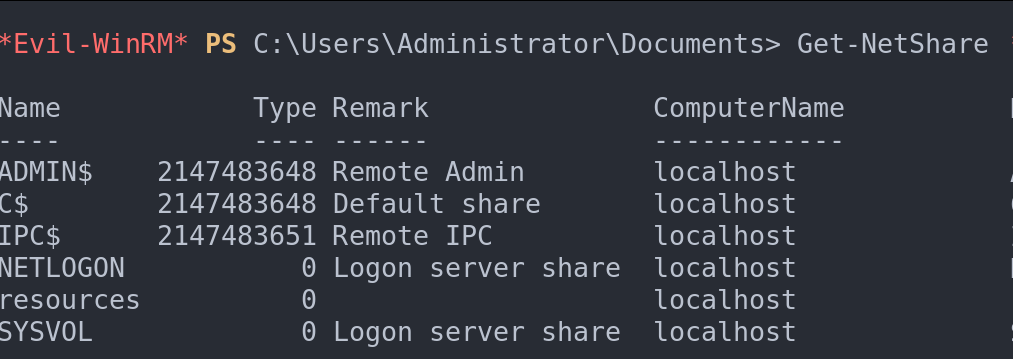
List of shared network folders on the machine
Sifting Through Files: The Hunt for Compromising Data
In the pursuit of critical information within a network, diving into the sea of files is essential. Among these files, some contain the keys to further access or pivotal data that could lead to compromising other machines. To embark on this digital treasure hunt, a powerful PowerShell script becomes our compass. Run this script in the C:\Users directory to unearth files of various formats that may hold valuable secrets:
</details>
Get-ChildItem -Include *.txt,*.pdf,*.xls,*.xlsx,*.doc,*.docx,*.kdbx,*.ini,*.log,*.xml,*.git* -File -Recurse -ErrorAction SilentlyContinue -Exclude desktop.ini
This script meticulously scans for a wide array of file types, from text documents to logs, uncovering potential repositories of sensitive information. It’s a methodical approach to sift through the digital layers, searching for those hidden gems – be it credentials, configuration files, or even inadvertently stored sensitive data. With each discovered file, we inch closer to understanding the network’s secrets and vulnerabilities.
Navigating Group Policies: A Key to Privilege Escalation
In the intricate maze of Active Directory, Group Policy Objects (GPOs) stand out as crucial elements for lateral movement and privilege escalation. Essentially, GPOs are collections of policy settings that orchestrate the behavior and access rights of users and computers within a Windows network. While we will delve deeper into their significance in upcoming chapters, it’s pivotal to grasp how to unearth these policy gems.
For starters, utilize PowerView’s capabilities to list GPOs with the following commands:
Get-NetGPOto list all GPOs.Get-NetGPO | select displaynamefor a focused view of GPO names.Find-GPOComputerAdmin –Computername <ComputerName>to pinpoint admin GPOs for specific computers.
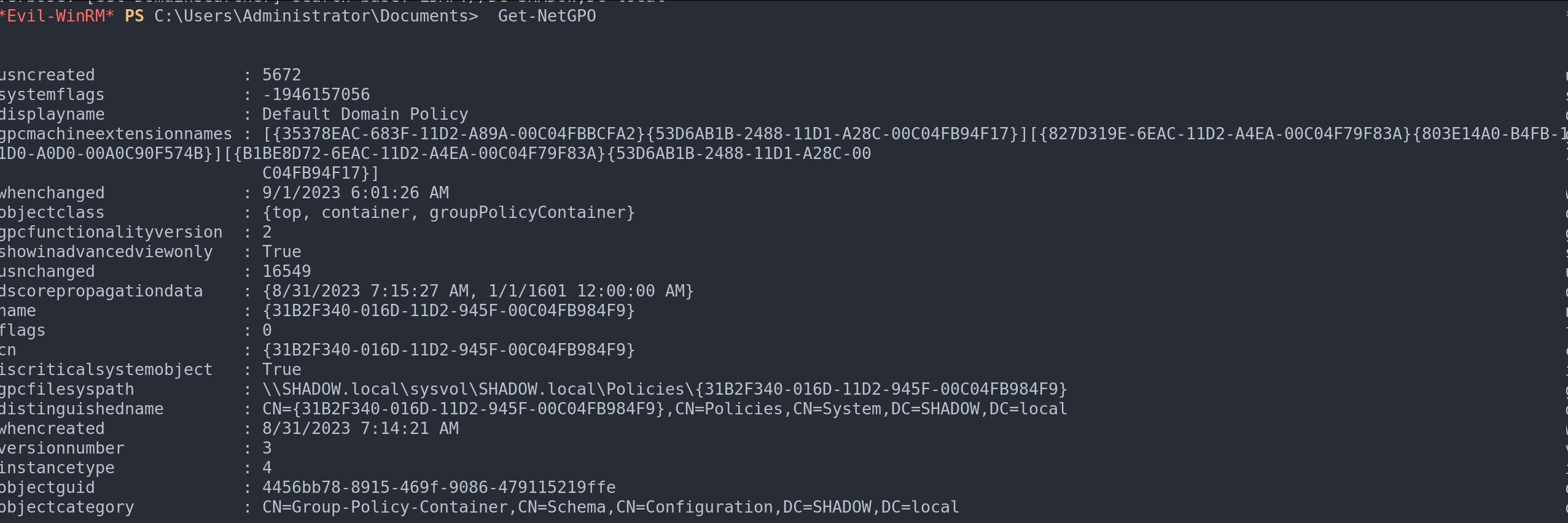
List all domain GPOs
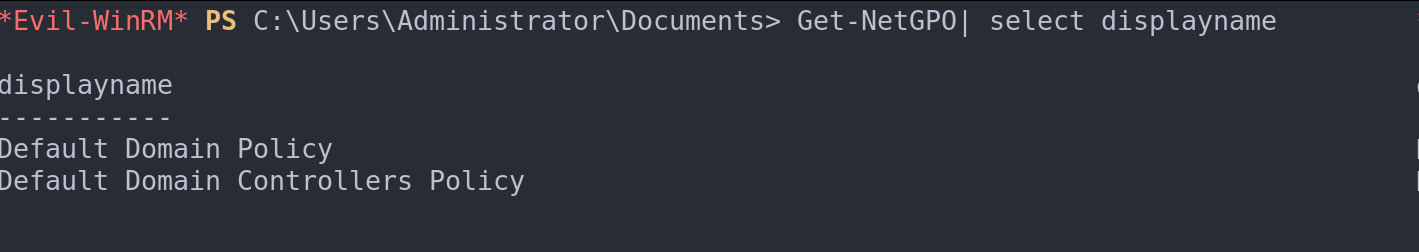
Filter by name
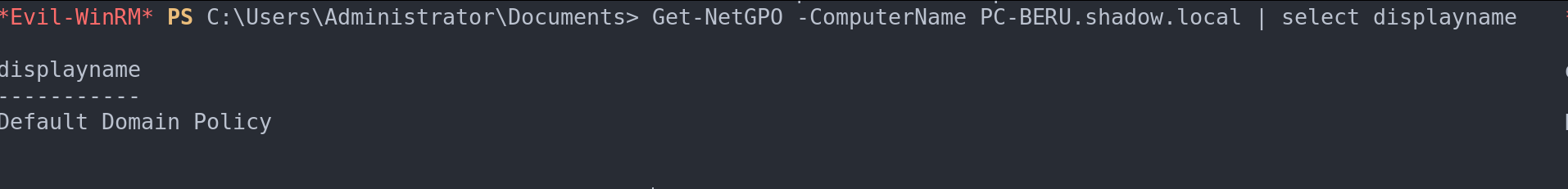
GPOs of a specific machine
Furthermore, to expand your search across the domain’s landscape, employ windapsearch with its gpos module:
windapsearch --dc 192.168.253.129 -u [email protected] -p Password1 -m gpos
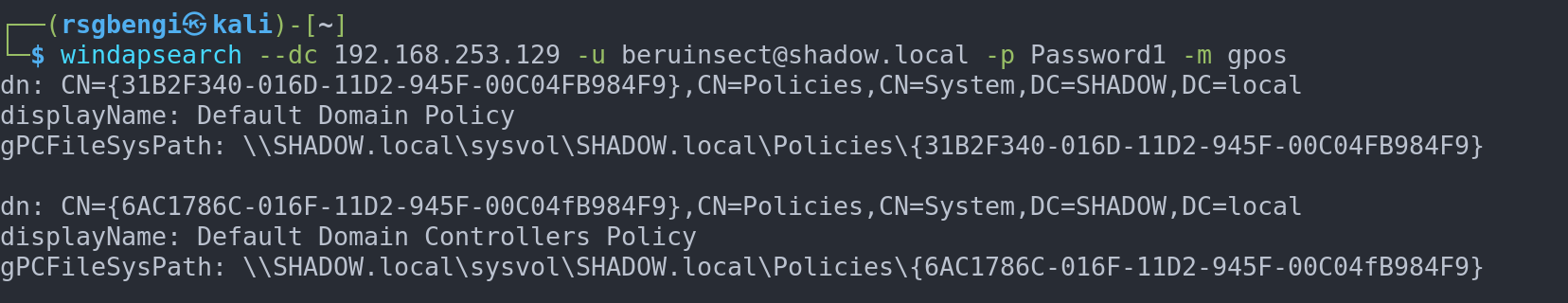
Unraveling Organizational Units: The Blueprint of Active Directory Structure
Picture Organizational Units (OUs) as the intricate compartments of a grand library within the Active Directory (AD) domain. These OUs serve as logical containers in Windows operating systems, methodically organizing and managing various network objects. Imagine them as shelves holding books (users), folders (groups), and gadgets (computers), each classified and arranged for optimal management and access.
Administrators typically harness OUs to implement a structured, hierarchical order in the AD landscape. This structure is not just for orderliness; it’s a strategic tool for applying targeted security policies to specific clusters of network objects. Just as a librarian categorizes books for easy access and to maintain a certain order, administrators use OUs to control and streamline the network environment.
To take a peek into this well-ordered world of OUs, the command Get-NetOU is your key. It’s like having a map that guides you through the various sections of this vast library, providing insights into how the AD domain is segmented and governed. In upcoming discussions, we’ll delve deeper into the interplay between OUs and Group Policy Objects (GPOs), unraveling how they collectively sculpt the security and operational framework of the AD domain.
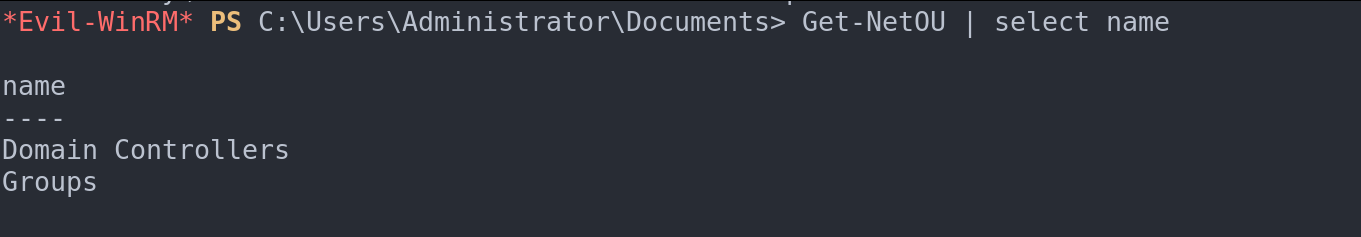
Obtaining OUs
Deciphering ACLs: The Gatekeepers of Network Security
Access Control Lists (ACLs) are akin to the intricate security protocols of a high-tech facility. They are sets of rules integral to managing access rights in operating systems, file systems, and network environments. ACLs dictate who gets to access, modify, delete, or perform specific actions on a resource, much like a security guard determines who enters a building.
In the realm of Active Directory (AD), understanding and managing ACLs are crucial for maintaining robust network security. PowerView, a versatile tool in our arsenal, allows us to inspect ACLs associated with different groups. For example, using Get-ObjectAcl -SamAccountName "<group>" -ResolveGUIDs, we can unveil the list of ACLs tied to a particular group, uncovering the security permissions vested in it.
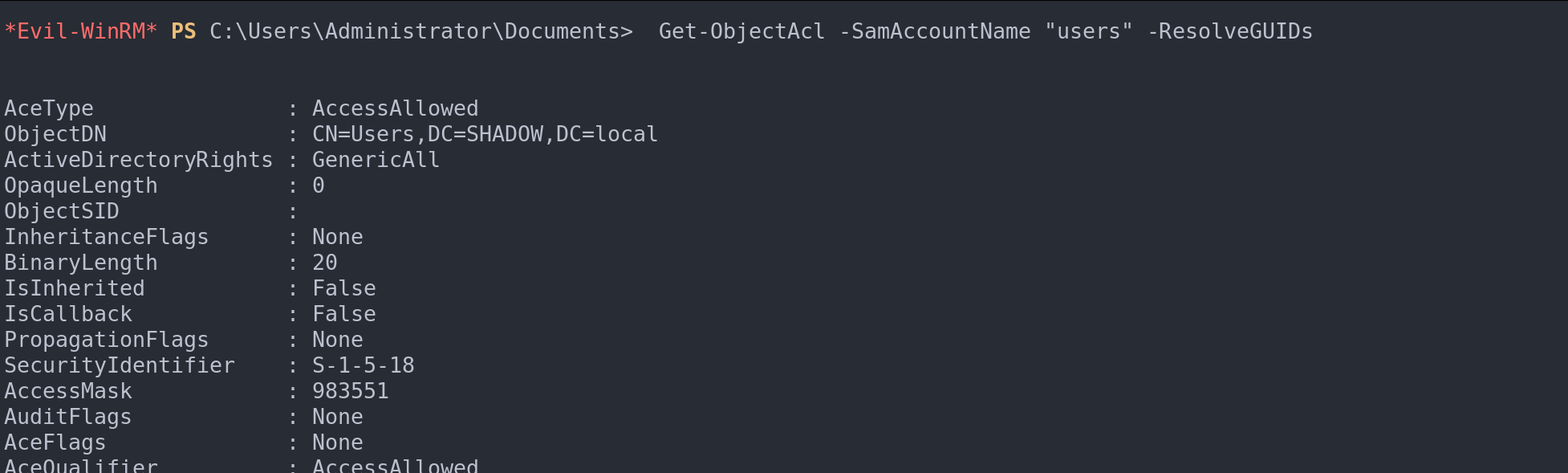
ACLs of a given group
Moreover, determining whether a user can alter a group policy becomes straightforward with Get-NetGPO | %{Get-ObjectAcl -ResolveGUIDs -Name $_.Name}. This capability is vital in auditing and securing group policy settings.
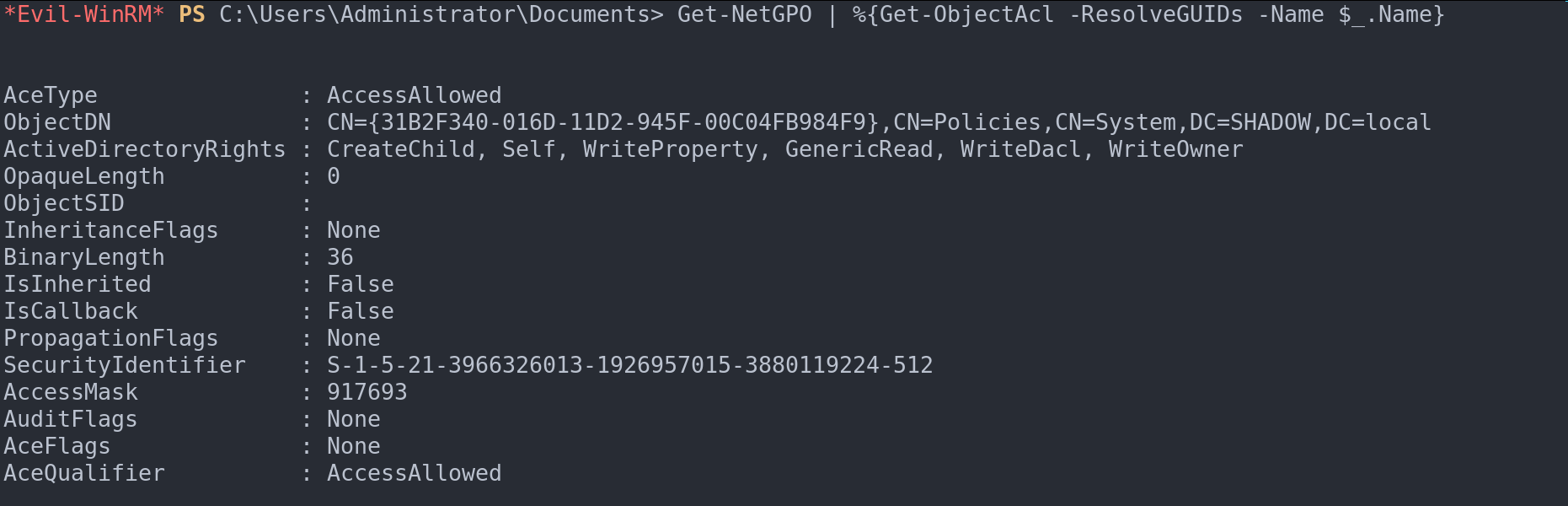
See if we can modify a group policy
To dig deeper and find ACLs of particular interest or potential vulnerabilities, Invoke-ACLScanner -ResolveGUIDs is our go-to command. It scans and highlights ACLs that might be exploitable for privilege escalation or unauthorized access.
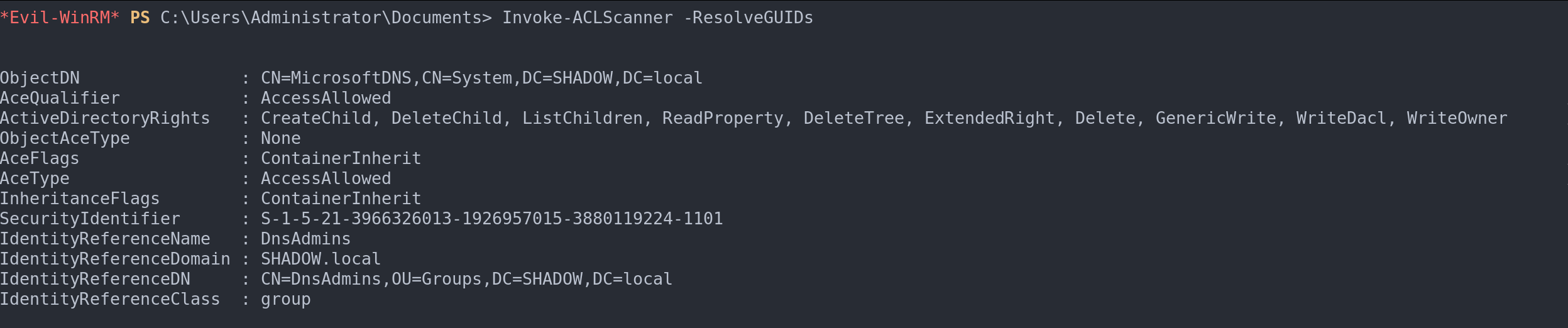
Finding interesting ACLs
Investigating ACLs linked to a specific user is also a breeze with Get-DomainObjectAcl -Identity <user> -ResolveGUIDs. This function is particularly useful when assessing the access rights and permissions of a user within the AD environment.
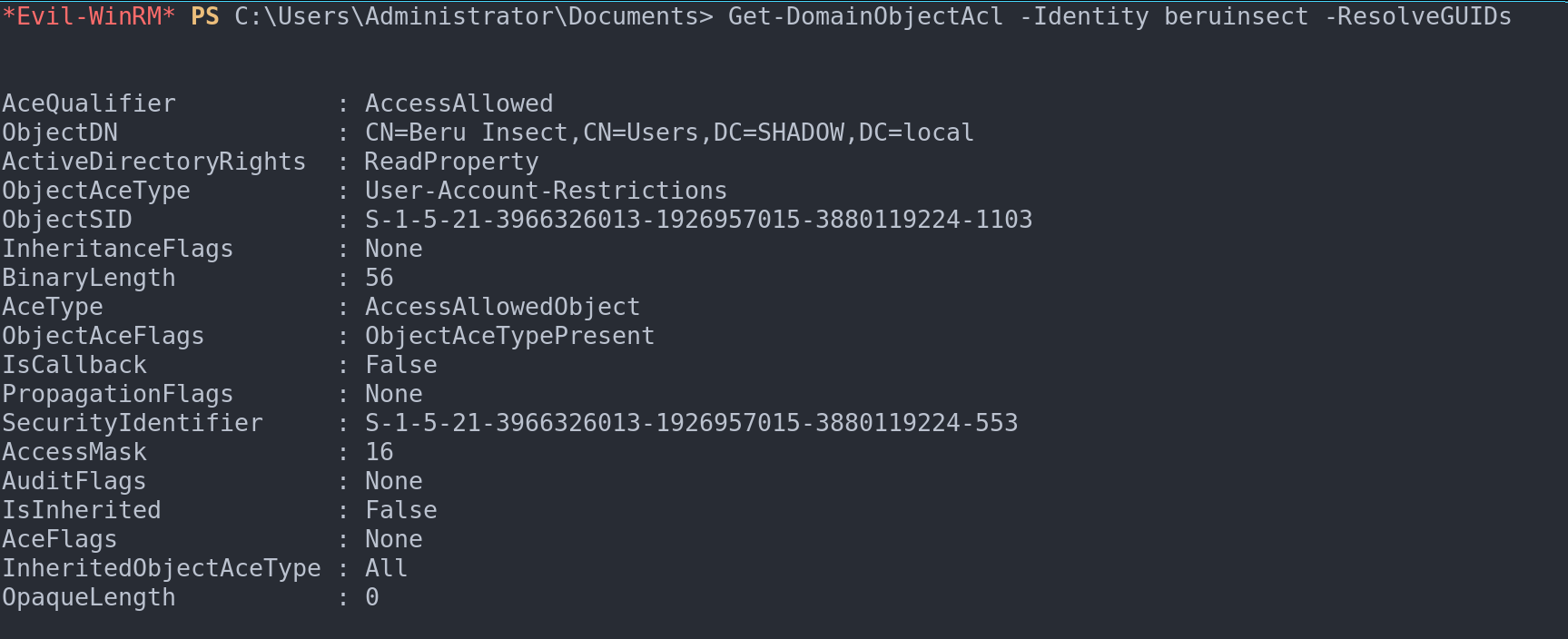
Obtain access control lists for a given usero
Lastly, to inspect ACLs applied to a specific folder or file, Get-PathAcl -Path "\\10.0.0.2\Users" comes in handy. This helps in understanding the access control set on shared network folders or sensitive files, a crucial aspect of data security.
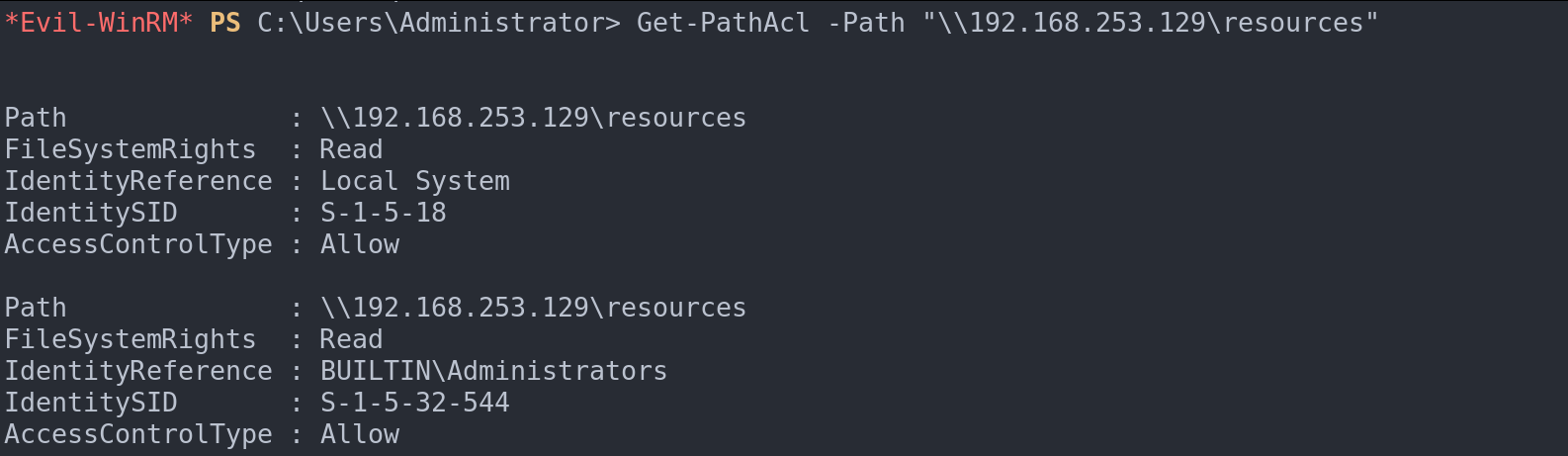
Access control lists against a given path
Navigating the Maze of Active Directory: A Comprehensive Wrap-Up
In this explorative journey, we’ve delved deep into the intricacies of Active Directory enumeration, both through automated means like BloodHound and manual methods utilizing tools like PowerView and windapsearch. We’ve seen how BloodHound, with its graph theory prowess, serves as a compass, guiding us through the complex labyrinth of privilege relationships and revealing paths to escalate our privileges within the domain.
Simultaneously, we embraced the subtler art of manual enumeration, vital in scenarios demanding stealth, using tools like PowerView and windapsearch. This method, though more labor-intensive, equips us with the finesse to operate undetected, a crucial skill in red team operations.
Our exploration didn’t just stop at gathering information; we learned to interpret and utilize it. From scrutinizing domain controllers and user accounts to dissecting groups, policies, and ACLs, we gained insights into the myriad ways each component of an Active Directory environment interacts and influences the other.
As we navigated through this complex network of information and permissions, we uncovered various facets of domain security, from GPOs and OUs to the finer details of local group enumerations and network shares. Each element we encountered and understood brought us closer to mastering the domain environment, teaching us not just how to extract information but also how to use it effectively.
In essence, this chapter has been a comprehensive guide, empowering us with the knowledge and tools to perform thorough and effective Active Directory enumerations. Whether you’re a budding cybersecurity enthusiast or a seasoned professional, the insights and techniques covered here are invaluable assets in your quest to understand and secure Active Directory environments.
Tips of the article
We have given enumeration with powerview and windapsearch, however, how can we enumerate domain users with crackmapex and enum4linux ?
crackmapexec smb targets.txt -u <user> -p <pass> --users
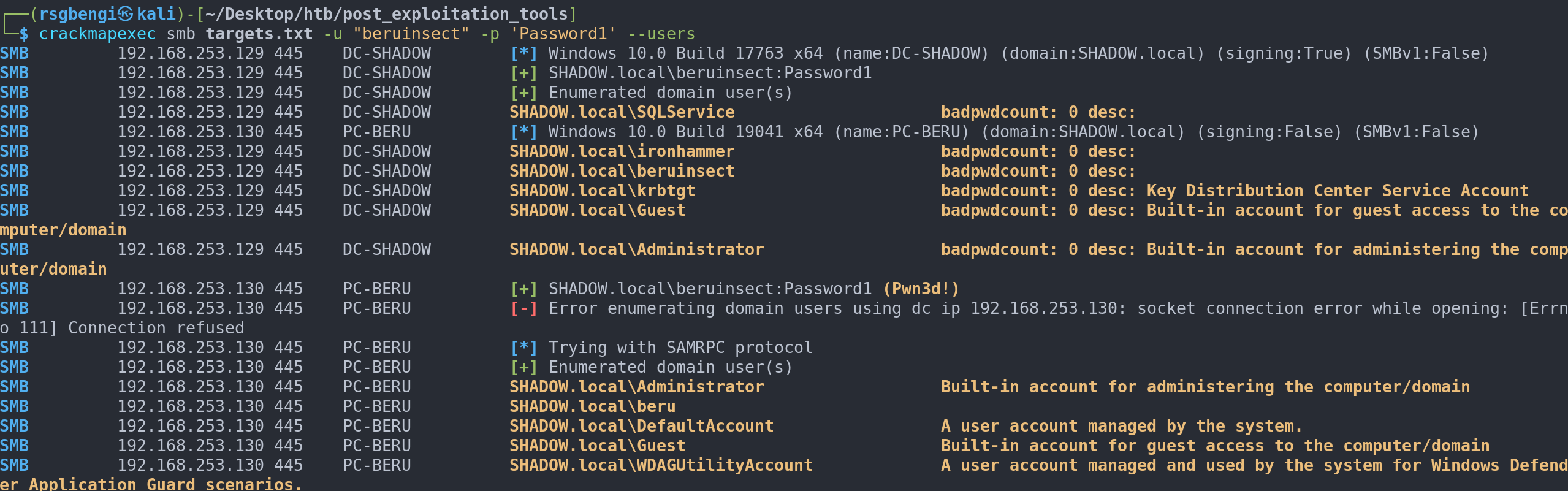
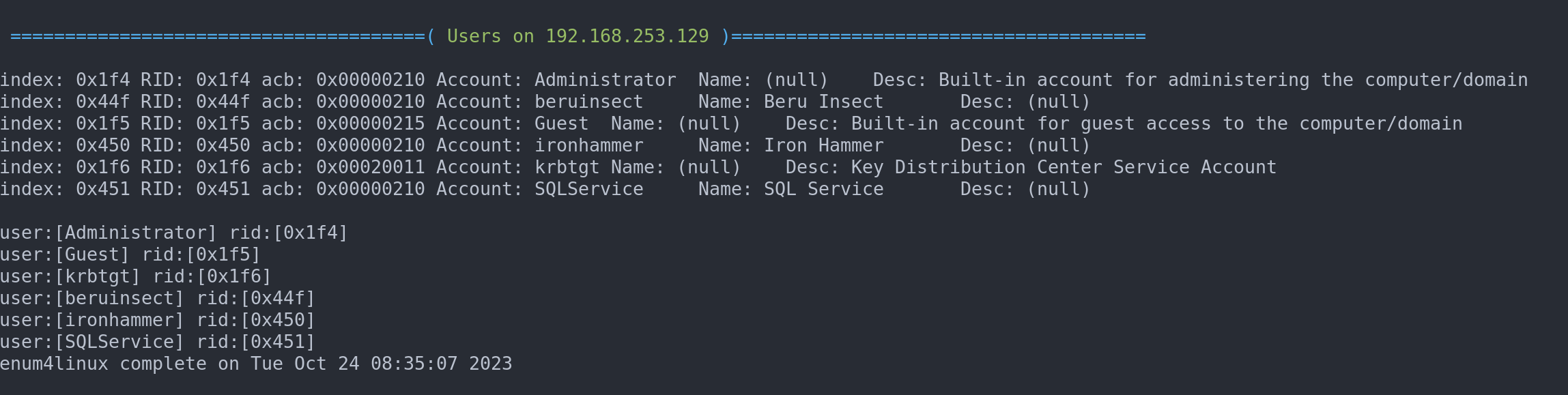
enum4linux -u <user> -p <password> -U <ip>
Following the above, how can I list the network shared folders ? and the password policy ?
To list shares:
crackmapexec smb <targets> -u <user> -p <password> --shares
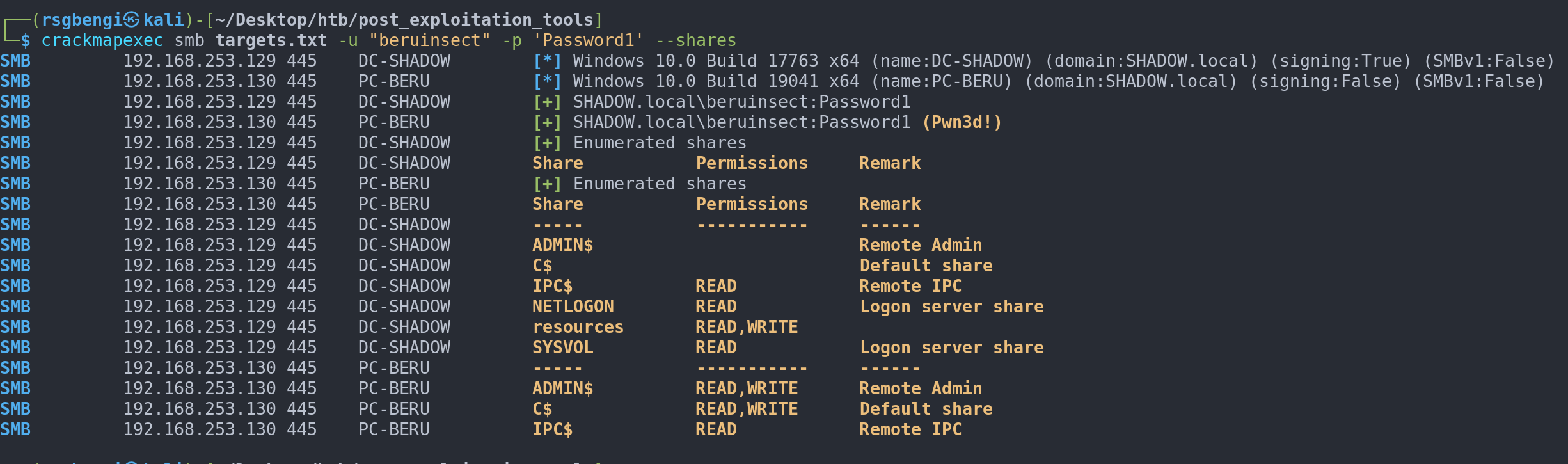
enum4linux -u <user> -p <password> -S <ip>
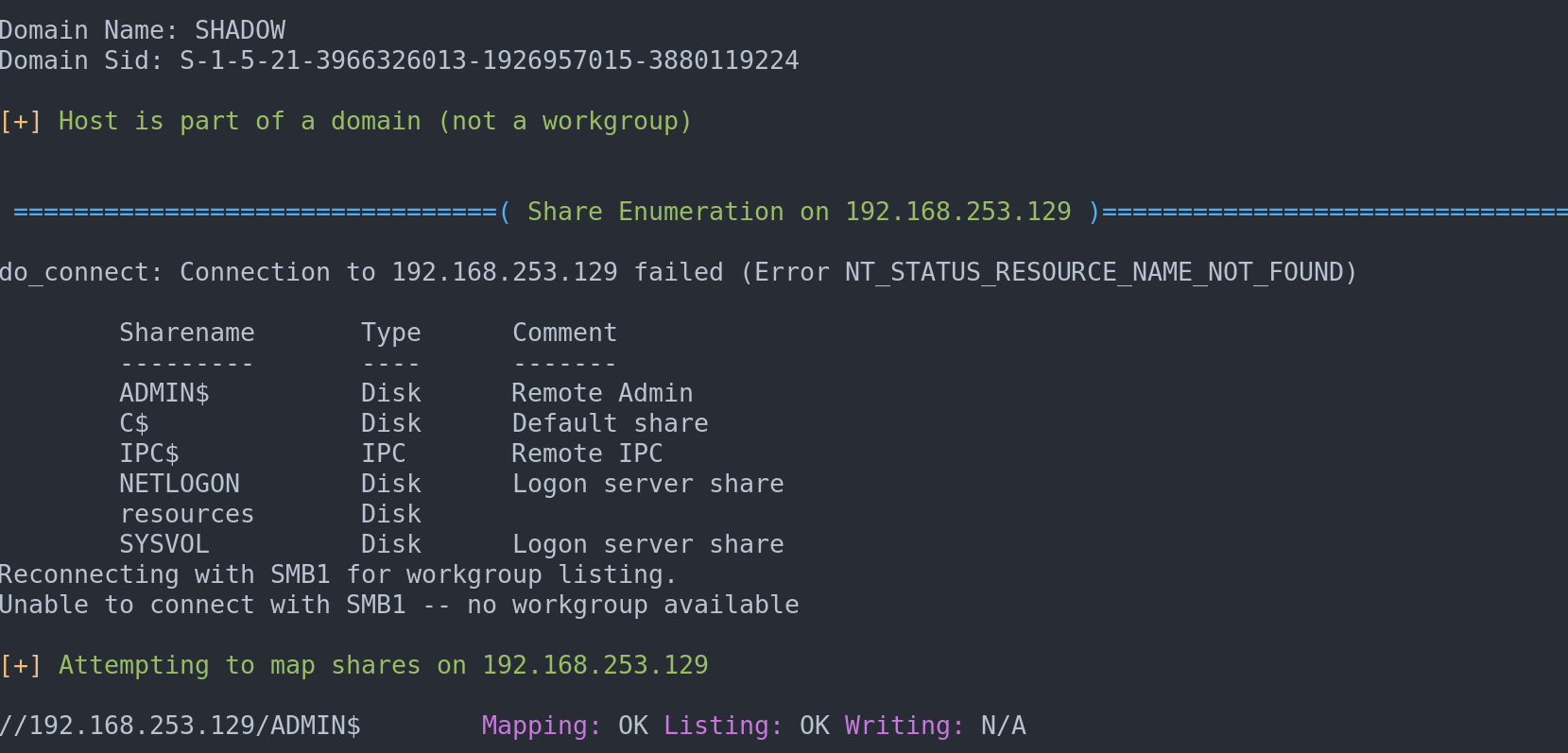
To enumerate the password policy:
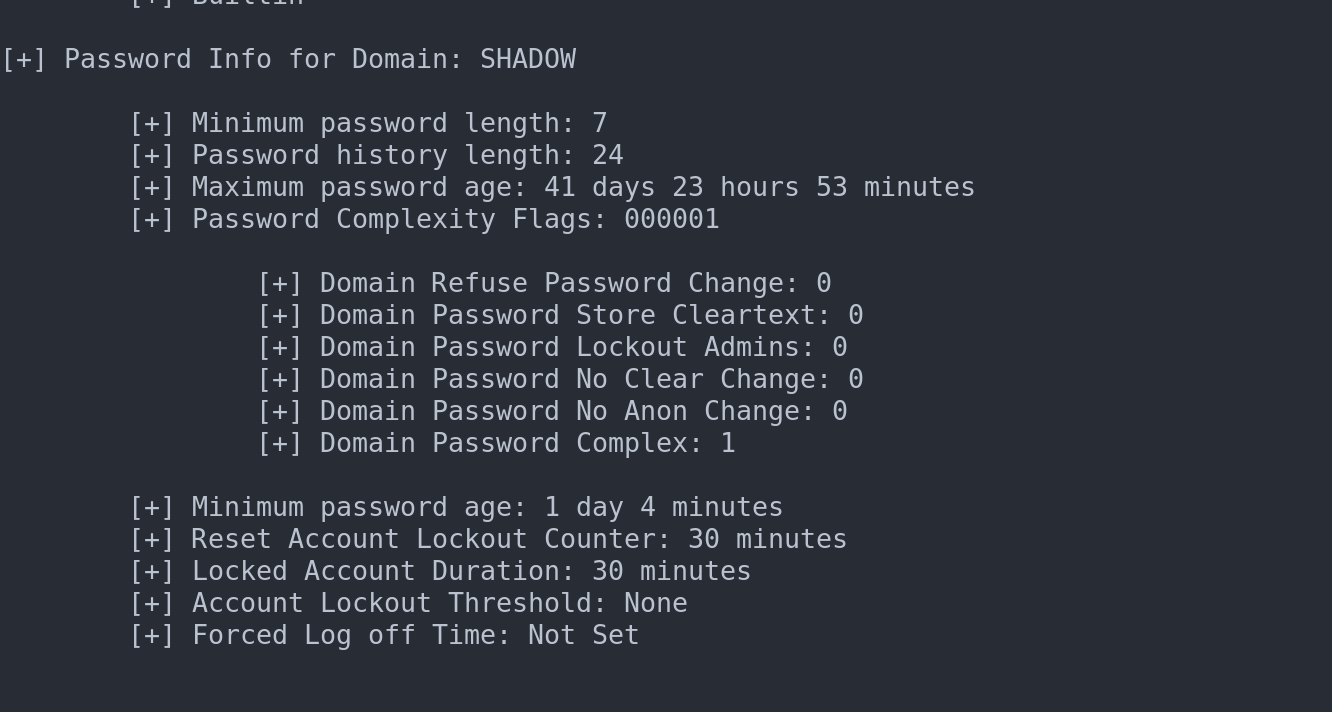
crackmapexec smb <targets> -u <user> -p <pass> --pass-pol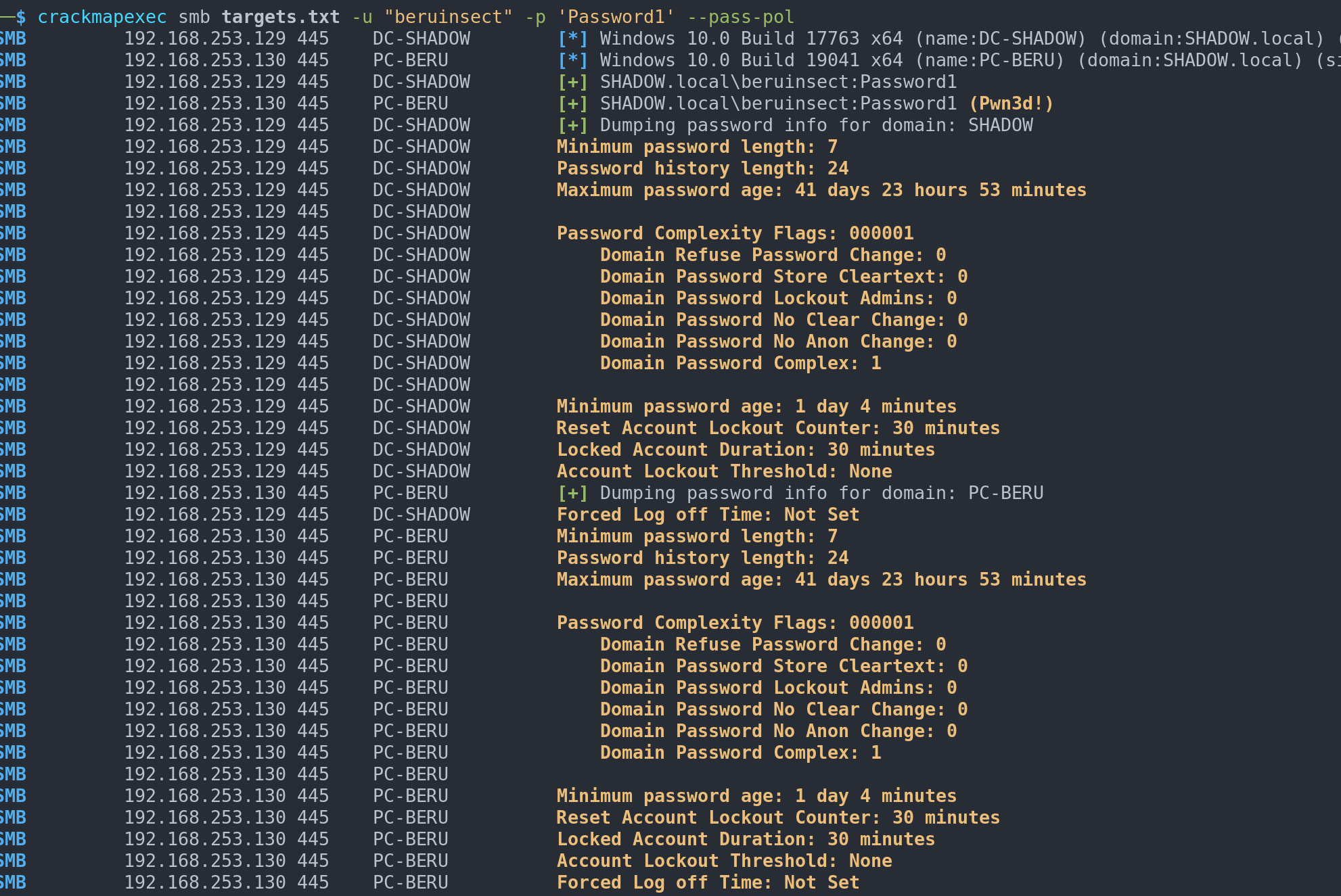
enum4linux -u <user> -p <password> -P <ip>
What can i use bloodhound for and when should i not use it ?
I can use it when I’m doing internal infrastructure pentesting or ctf as the noise it generates is not really crucial. However, in an exercise where I have to be quiet, I will have to avoid it, otherwise I will be detected quickly.
Resources
Active Directory Domain Enumeration Part-1 With Powerview
Active Directory Enumeration - Pentest Everything
Chapters

Previous chapter
Next chapter


💬 Comments Available
Drop your thoughts in the comments below! Found a bug or have feedback? Let me know.